July 6, 2011 in Russia
This “previously confidential list of people and organizations found to be involved in laundering money and funding terrorism” was presented by Rossiyskaya Gazeta, the Russian-government owned newspaper. It was originally compiled by the Russian Ministry of Justice. A rough, Google translation is also presented [in brackets] alongside the headings in Russian.
Организации и физические лица, включенные в перечень на основании подпунктов 1 – 3 пункта 2.1 статьи 6 Федерального закона от 7 августа 2001 г. N 115-ФЗ “О противодействии легализации (отмыванию) доходов, полученных преступным путем, и финансированию терроризма”
[Organizations and individuals included in the list by virtue of subsections 1 – 3 of paragraph 2.1 of Article 6 of the Federal Law of 7 August 2001 N 115-FZ “On Combating Legalization (Laundering) of Proceeds from Crime and Terrorist Financing”]
Организации [Organizations]
1. АЛЬ-КАИДА В СТРАНАХ ИСЛАМСКОГО МАГРИБА (ПРЕЖНЕЕ НАЗВАНИЕ САЛАФИСТСКАЯ ГРУППА ПРОПОВЕДИ И ДЖИХАДА)*.
2. АСБАТ АЛЬ-АНСАР*.
3. БАЗА (АЛЬ-КАИДА)*.
4. БРАТЬЯ-МУСУЛЬМАНЕ (АЛЬ-ИХВАН АЛЬ-МУСЛИМУН)*.
5. ВЫСШИЙ ВОЕННЫЙ МАДЖЛИСУЛЬ ШУРА ОБЪЕДИНЕННЫХ СИЛ МОДЖАХЕДОВ КАВКАЗА*.
6. ГРУППА ДЖАМААТ МУВАХИДОВ.
7. ДВИЖЕНИЕ ТАЛИБАН*.
8. ДЖУНД АШ-ШАМ*.
9. ДОМ ДВУХ СВЯТЫХ (АЛЬ-ХАРАМЕЙН)*.
10. ИМАРАТ КАВКАЗ (КАВКАЗСКИЙ ЭМИРАТ)*.
11. ИСЛАМСКАЯ ГРУППА (АЛЬ-ГАМАА АЛЬ-ИСЛАМИЯ)*.
12. ИСЛАМСКАЯ ГРУППА (ДЖАМААТ-И-ИСЛАМИ)*.
13. ИСЛАМСКАЯ ПАРТИЯ ТУРКЕСТАНА (бывшее ИСЛАМСКОЕ ДВИЖЕНИЕ УЗБЕКИСТАНА)*.
14. ИСЛАМСКИЙ ДЖИХАД-ДЖАМААТ МОДЖАХЕДОВ*.
15. КАБАРДИНО-БАЛКАРСКАЯ РЕГИОНАЛЬНАЯ ОБЩЕСТВЕННАЯ ОРГАНИЗАЦИЯ СОВЕТ СТАРЕЙШИН БАЛКАРСКОГО НАРОДА КБР; ИНН: 0721013951; Рег.номер: 1060700000118; г. Нальчик Кабардино-Балкарская Республика, пр. Ленина, д. 7 “а”, офис 110.
16. КОНГРЕСС НАРОДОВ ИЧКЕРИИ И ДАГЕСТАНА*.
17. ЛАШКАР-И-ТАЙБА*.
18. МЕЖДУНАРОДНАЯ РЕЛИГИОЗНАЯ ОРГАНИЗАЦИЯ НУРДЖУЛАР.
19. МЕЖДУНАРОДНОЕ ОБЩЕСТВЕННОЕ ОБЪЕДИНЕНИЕ НАЦИОНАЛ-СОЦИАЛИСТИЧЕСКОЕ ОБЩЕСТВО (НСО, НС).
20. МЕЖДУНАРОДНОЕ РЕЛИГИОЗНОЕ ОБЪЕДИНЕНИЕ АТ-ТАКФИР ВАЛЬ-ХИДЖРА.
21. МЕЖДУНАРОДНОЕ РЕЛИГИОЗНОЕ ОБЪЕДИНЕНИЕ ТАБЛИГИ ДЖАМААТ.
22. МЕЖРЕГИОНАЛЬНАЯ ОБЩЕСТВЕННАЯ ОРГАНИЗАЦИЯ ДВИЖЕНИЕ ПРОТИВ НЕЛЕГАЛЬНОЙ ИММИГРАЦИИ.
23. МЕЖРЕГИОНАЛЬНАЯ ОБЩЕСТВЕННАЯ ОРГАНИЗАЦИЯ НАЦИОНАЛ-БОЛЬШЕВИСТСКАЯ ПАРТИЯ.
24. МЕЖРЕГИОНАЛЬНОЕ ОБЩЕСТВЕННОЕ ДВИЖЕНИЕ АРМИЯ ВОЛИ НАРОДА.
25. МЕЖРЕГИОНАЛЬНОЕ ОБЩЕСТВЕННОЕ ОБЪЕДИНЕНИЕ ДУХОВНО-РОДОВАЯ ДЕРЖАВА РУСЬ.
26. МЕЖРЕГИОНАЛЬНОЕ ОБЩЕСТВЕННОЕ ОБЪЕДИНЕНИЕ ФОРМАТ-18.
27. МЕСТНАЯ ОРГАНИЗАЦИЯ ГОРОДА КРАСНОДАРА ПИТ БУЛЬ (PIT BULL); г. Краснодар, ул. Гудимы, д. 32, кв. 99.
28. МЕСТНАЯ РЕЛИГИОЗНАЯ ОРГАНИЗАЦИЯ АСГАРДСКАЯ СЛАВЯНСКАЯ ОБЩИНА ДУХОВНОГО УПРАВЛЕНИЯ АСГАРДСКОЙ ВЕСИ БЕЛОВОДЬЯ ДРЕВНЕРУССКОЙ ИНГЛИИСТИЧЕСКОЙ ЦЕРКВИ ПРАВОСЛАВНЫХ СТАРОВЕРОВ-ИНГЛИНГОВ; г. Омск; г.Омск, ул.Ивана Воронкова, 29-а.
29. МЕСТНАЯ РЕЛИГИОЗНАЯ ОРГАНИЗАЦИЯ СВИДЕТЕЛИ ИЕГОВЫ ТАГАНРОГ.
30. МЕСТНАЯ РЕЛИГИОЗНАЯ ОРГАНИЗАЦИЯ СЛАВЯНСКАЯ ОБЩИНА КАПИЩА ВЕДЫ ПЕРУНА ДУХОВНОГО УПРАВЛЕНИЯ АСГАРДСКОЙ ВЕСИ БЕЛОВОДЬЯ ДРЕВНЕРУССКОЙ ИНГЛИИСТИЧЕСКОЙ ЦЕРКВИ ПРАВОСЛАВНЫХ СТАРОВЕРОВ-ИНГЛИНГОВ; г. Омск; г.Омск, ул.Ивана Воронкова, 29-а.
31. МОСКОВСКАЯ ГОРОДСКАЯ ОРГАНИЗАЦИЯ МЕЖРЕГИОНАЛЬНОГО ОБЩЕСТВЕННОГО ДВИЖЕНИЯ СЛАВЯНСКИЙ СОЮЗ.
32. ОБЩЕСТВЕННОЕ НЕЗАРЕГИСТРИРОВАННОЕ ОБЪЕДИНЕНИЕ ГРУППА РАДА ЗЕМЛИ КУБАНСКОЙ ДУХОВНО РОДОВОЙ ДЕРЖАВЫ РУСЬ; г. Краснодар, ул. Коммунаров, д. 221.
33. ОБЩЕСТВЕННОЕ ОБЪЕДИНЕНИЕ АХТУБИНСКОЕ НАРОДНОЕ ДВИЖЕНИЕ К БОГОДЕРЖАВИЮ.
34. ОБЩЕСТВЕННОЕ ОБЪЕДИНЕНИЕ КУЗБАССКАЯ ОБЩЕСТВЕННАЯ ОРГАНИЗАЦИЯ СЛАВЯНСКИЙ МИР.
35. ОБЩЕСТВЕННОЕ ОБЪЕДИНЕНИЕ ОМСКАЯ ОРГАНИЗАЦИЯ ОБЩЕСТВЕННОГО ПОЛИТИЧЕСКОГО ДВИЖЕНИЯ РУССКОЕ НАЦИОНАЛЬНОЕ ЕДИНСТВО.
36. ОБЩЕСТВО ВОЗРОЖДЕНИЯ ИСЛАМСКОГО НАСЛЕДИЯ (ДЖАМИЯТ ИХЬЯ АТ-ТУРАЗ АЛЬ-ИСЛАМИ)*.
37. ОБЩЕСТВО СОЦИАЛЬНЫХ РЕФОРМ (ДЖАМИЯТ АЛЬ-ИСЛАХ АЛЬ-ИДЖТИМАИ)*.
38. ОБЪЕДИНЕННЫЙ ВИЛАЙАТ КАБАРДЫ, БАЛКАРИИ И КАРАЧАЯ.
39. ПАРТИЯ ИСЛАМСКОГО ОСВОБОЖДЕНИЯ (ХИЗБ УТ-ТАХРИР АЛЬ-ИСЛАМИ)*.
40. ПРИМОРСКАЯ РЕГИОНАЛЬНАЯ ПРАВОЗАЩИТНАЯ ОБЩЕСТВЕННАЯ ОРГАНИЗАЦИЯ СОЮЗ СЛАВЯН; ИНН: 2540087611; Рег. номер: 1082500000318; 690019, г. Владивосток, ул. Алеутская, д. 45А, офис 120.
41. РЕГИОНАЛЬНОЕ ОБЩЕСТВЕННОЕ ОБЪЕДИНЕНИЕ НАЦИОНАЛ-СОЦИАЛИСТИЧЕСКАЯ РАБОЧАЯ ПАРТИЯ РОССИИ (НСРПР).
42. РЕЛИГИОЗНАЯ ГРУППА БЛАГОРОДНЫЙ ОРДЕН ДЬЯВОЛА.
43. РЕЛИГИОЗНАЯ ГРУППА КРАСНОДАРСКАЯ ПРАВОСЛАВНАЯ СЛАВЯНСКАЯ ОБЩИНА “ВЕК РА” (ВЕДИЧЕСКОЙ КУЛЬТУРЫ РОССИЙСКИХ АРИЕВ) СКИФСКОЙ ВЕСИ РАССЕНИИ.
44. РЕЛИГИОЗНАЯ ОРГАНИЗАЦИЯ МУЖСКАЯ ДУХОВНАЯ СЕМИНАРИЯ ДУХОВНОЕ УЧРЕЖДЕНИЕ ПРОФЕССИОНАЛЬНОГО РЕЛИГИОЗНОГО ОБРАЗОВАНИЯ ДРЕВНЕРУССКОЙ ИНГЛИИСТИЧЕСКОЙ ЦЕРКВИ ПРАВОСЛАВНЫХ СТАРОВЕРОВ-ИНГЛИНГОВ; г. Омск; г. Омск, ул. Ивана Воронкова, 29-а.
45. РЯЗАНСКАЯ ГОРОДСКАЯ ОБЩЕСТВЕННАЯ ПАТРИОТИЧЕСКАЯ ОРГАНИЗАЦИЯ РУССКОЕ НАЦИОНАЛЬНОЕ ЕДИНСТВО.
46. СВЯЩЕННАЯ ВОЙНА (АЛЬ-ДЖИХАД ИЛИ ЕГИПЕТСКИЙ ИСЛАМСКИЙ ДЖИХАД)*.
Физические лица [Individuals]
1. АБАЕВ АЛИХАН АБДИЕВИЧ*, 19.12.1986 г.р., с. Сельментаузе Веденского района ЧИАССР.
2. АБАЕВ АСЛАНБЕК БАУДИНОВИЧ*, 29.05.1983 г.р., г. Грозный ЧИАССР.
3. АБАКАРОВ МАГОМЕД ГАСАНОВИЧ*, 12.07.1983 г.р., ст. Бороздиновская Шелковского района ЧИАССР.
4. АБАСИЛОВ МАГОМЕД ПАХРУДИНОВИЧ*, 27.02.1972 г.р., с. Стальское Кизилюртовского района Республики Дагестан.
5. АБДЕЛЬ АЗИЗ МАХАММЕД АБДЕЛЬ ВАХАТ*, 07.09.1959 г.р., г. Мосул, Ирак.
6. АБДРАХМАНОВ АДЛАН АМСАДОВИЧ*, 03.07.1975 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
7. АБДУЛАЕВ ПАТАХ МАГОМЕДОВИЧ*, 18.02.1973 г.р., с. Гимры Унцукульского района Республики Дагестан.
8. АБДУЛАЕВ ШАМИЛЬ ХАРОНОВИЧ*, 18.01.1980 г.р., с. Уч-Арал Талды-Курганской области Казахской ССР.
9. АБДУЛВАГАБОВ РУСЛАН КАЗБЕКОВИЧ*, 09.05.1978 г.р., ст. Каргалинская Шелковского района ЧИАССР.
10. АБДУЛВАГАПОВ САЙД-МАГОМЕД АБУТАЛИПОВИЧ*, 31.07.1980 г.р., с. Шаами-Юрт ЧИАССР.
11. АБДУЛВАХАБОВ РУСЛАН МИЦИЕВИЧ*, 29.01.1980 г.р., с. Закан-Юрт Ачхой-Мартановского района ЧИАССР.
12. АБДУЛКАДЫРОВ АБДУЛКАДЫР ГАДЖИЕВИЧ*, 07.09.1959 г.р., с. Кудали Гунибского района Республики Дагестан.
13. АБДУЛКАДЫРОВ РУСЛАН РАМЗАНОВИЧ*, 23.07.1980 г.р., с. Урус-Мартан Урус-Мартановского района Чеченской Республики.
14. АБДУЛКАДЫРОВ ШАМСУДИ САЙТХУСЕЙНОВИЧ*, 06.03.1981 г.р., с. Яшкуль Яшкульского района Калмыцкой АССР.
15. АБДУЛКАРИМОВ МАГОМЕД УСМАНОВИЧ*, 21.01.1974 г.р., с. Муцалаул Хасавюртовского района Республики Дагестан.
16. АБДУЛЛАЕВ АДАМ МОЛДИЕВИЧ (АБДУЛАЕВ АДАМ МОЛДИЕВИЧ)*, 20.05.1985 г.р., с. Алхан-Юрт Урус-Мартановского района ЧИАССР (20.05.1985 г.р., с. Алхан-Юрт Урус-Мартановского района ЧИАССР).
17. АБДУЛМАЖИДОВ АХМАД ДЕНИЕВИЧ*, 25.10.1981 г.р., с. Алхан-Юрт Урус-Мартановского района ЧИАССР.
18. АБДУЛХАДЖИЕВ ЗЕЛИМХАН ЗАНДИЕВИЧ*, 31.07.1975 г.р., г. Грозный ЧИАССР.
19. АБДУРАЗАКОВ АБДУРАЗАК МАГОМЕДОВИЧ*, 22.01.1961 г.р., г. Буйнакск Республики Дагестан.
20. АБДУРАЗАКОВ МУРАД САЛИМОВИЧ*, 23.11.1968 г.р., с. Хоточ Гунибского района Республики Дагестан.
21. АБДУРАХМАНОВ АСЛАМБЕК САЙХАНОВИЧ*, 21.06.1975 г.р., с. Курчалой ЧИАССР.
22. АБДУРАХМАНОВ ТУРПАЛ АЛИ ИЗМУТДИНОВИЧ*, 04.11.1966 г.р., с. Замьяны Астраханской обл.
23. АБДУРАХМАНОВ ШАМИЛЬ ХАНСОЛТАЕВИЧ*, 15.11.1990 г.р., с. Байтарки Ножай-Юртовского района ЧИАССР.
24. АБДУРАШИДОВ МОХМАТСЕЛАХ АБДУЛВАХИДОВИЧ*, 14.08.1965 г.р., с. Кошкельды Гудермесского района Чеченской Республики.
25. АБЖАВАТОВ АРТУР АБАКАРОВИЧ*, 26.11.1983 г.р., г. Махачкала Республики Дагестан.
26. АБСАЛИМОВ РУСТАМ САПИРОВИЧ*, 28.08.1976 г.р., г. Махачкала Республики Дагестан.
27. АБУБАКАРОВ ИЛЬЯС АХМЕТОВИЧ*, 24.10.1984 г.р., г. Грозный Чеченской Республики.
28. АБУБАКАРОВ ИЛЬЯС МУСАЕВИЧ*, 14.09.1979 г.р., с. Мескер-Юрт Шалинского р-на ЧИАССР.
29. АБУБАКАРОВ ЛЕМА ДЕНИСОЛТАНОВИЧ*, 10.05.1974 г.р., с. Ахкинчу-Борзой Ножай-Юртовского района ЧИАССР.
30. АБУБАКАРОВ РИЗАВДИ СУЛТАНОВИЧ*, 29.11.1982 г.р., п. Чограйский Арзгирского района Ставропольского края.
31. АБУБАКАРОВ РИЗВАН СУЛТАНОВИЧ*, 17.01.1977 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
32. АБУБАКАРОВ РУСЛАН САЛАУДИНОВИЧ*, 14.09.1965 г.р., г. Токмак Киргизской АССР.
33. АБУБАКАРОВ РУСЛАНБЕК БУСАНИЕВИЧ*, 27.05.1979 г.р., с. Знаменское Надтеречного района ЧИАССР.
34. АБУБАКАРОВ САИДХАСАН НАЖМУДИЕВИЧ*, 09.06.1981 г.р., с. Шали Шалинского района ЧИАССР.
35. АБУБАКАРОВ САЙД-ХАМЗАТ АДАМОВИЧ*, 02.01.1979 г.р., с. Дуба-Юрт Шалинского района ЧИАССР.
36. АБУЕВ САИД МУСАЕВИЧ*, 08.05.1973 г.р., г. Тимер-Тау Карагалинской области Республики Казахстан.
37. АБУЕВ ХАСАН АБУСУЛТАНОВИЧ*, 21.12.1963 г.р., с. Тевзан Веденского р-на ЧИАССР.
38. АБУХАНОВ АЛИК ШАХИДОВИЧ*, 31.08.1960 г.р., с. Махкеты Введенского района ЧИАССР.
39. АВДАДАЕВ РУСТАМ ХАМЗАТОВИЧ*, 20.02.1979 г.р., с. Гойское Урус-Мартановского района ЧИАССР.
40. АГАЕВ ТАХИР ХАЛАДОВИЧ*, 08.08.1977 г.р., с. Байтарки Ножай-Юртовского района ЧИАССР.
41. АГАМИРЗАЕВ АБДУЛХАМИД МУТАЛИПОВИЧ*, 16.05.1985 г.р., с. Советское Советского района ЧИАССР.
42. АГАМИРЗАЕВ АРТУР МУТАЛИПОВИЧ*, 26.07.1981 г.р., с. Нохч-Келой Советского района ЧИАССР.
43. АГУЕВ МАГОМЕД-ЭМИ МОВЛАЕВИЧ*, 09.07.1986 г.р., с. Новые Атаги Шалинского района ЧИАССР.
44. АГУЕВ МОВЛИД МАМАЕВИЧ*, 29.07.1970 г.р., с. Мескеты Ножай-Юртовского района ЧИАССР.
45. АДАЕВ ЕВГЕНИЙ АБУЯЗИТОВИЧ*, 12.03.1984 г.р., х. Овчинников Дубовского р-на Ростовской обл.
46. АДАЕВ ЗЕЛИМХАН ВАЛЕРЬЕВИЧ*, 24.03.1974 г.р., с. Ножай-Юрт Ножай-Юртовского района ЧИАССР.
47. АДАМОВ АБУДАРДЫ МАГАМЕДОВИЧ*, 25.07.1973 г.р., с. Арбузинка Балкашинского р-на Целиноградской области Республики Казахстан.
48. АДАМОВ МАЙРБЕК МАГОМЕДОВИЧ*, 07.04.1957 г.р., с. Чулактау Джамбульской области Казахской ССР.
49. АДЖИНИЯЗОВ КАЙТАРБИ СЕЙДАЛИЕВИЧ*, 22.12.1974 г.р., с. Тукуй-Мектеб Нефтекумского района Ставропольского края.
50. АДИЛЬГЕРЕЕВ ИСМАИЛ АБДУЛАЕВИЧ*, 24.04.1970 г.р., г. Буйнакск Республики Дагестан.
51. АДУЕВ РАМЗАН АЛАУДИНОВИЧ*, 27.09.1983 г.р., г. Грозный ЧИАССР.
52. АЖГЕЛЬДИЕВ ЭНВЕР МАГОМЕДОВИЧ*, 10.09.1983 г.р., а. Кизыл-Юрт Хабезского района Ставропольского края.
53. АЗИЕВ АЛИХАН МОВЛАЕВИЧ*, 31.07.1982 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
54. АЗИЕВ ИМРАН ЛЕЧИЕВИЧ*, 01.06.1973 г.р., с. Старая Сунжа Грозненского р-на ЧИАССР.
55. АЗИЕВ РИЗВАН ЛЕЧИЕВИЧ*, 21.03.1979 г.р., с. Старая Сунжа Грозненского района (возможно г. Грозный) ЧИАССР.
56. АЗИЕВ САИД-АХМЕД МУХИДОВИЧ*, 20.12.1977 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
57. АЗИЕВ ХАЖМУРАД ЯКУБОВИЧ*, 29.09.1968 г.р., с. Автуры Шалинского района ЧИАССР.
58. АЗИЕВ ХАМЗАТ БАДРУДИНОВИЧ*, 14.09.1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
59. АЗИЕВ ХАРОН ЛЕЧИЕВИЧ*, 15.01.1975 г.р., с. Совяжа-Юрт Грозненского района ЧИАССР.
60. АЗИЕВ ШАМХАН МУХИДОВИЧ*, 10.08.1979 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
61. АЗИЕВ ЮНУС ЛЕЧИЕВИЧ*, 08.09.1981 г.р., с. Советское Советского района ЧИАССР.
62. АЗИЗОВ АЛЕКСЕЙ АЛЫМЖАНОВИЧ*, 10.11.1982 г.р., с. Никольское Гатчинского района Ленинградской области.
63. АЗИМОВ АНЗОР ЗИЯУДИНОВИЧ*, 14.09.1982 г.р., с. Ушкалой Советского района ЧИАССР.
64. АЙБАЗОВ ОТАРИЙ АЛИЕВИЧ*, 26.05.1971 г.р., ст. Сторожевая Зеленчукского района Ставропольского края.
65. АЙБАЗОВ РАШИД ХАСАНОВИЧ*, 15.02.1980 г.р., г. Усть-Джегута Карачаево-Черкесской Республики.
66. АЙГУМОВ СУЛЕЙМАН САЙД-ХАСАНОВИЧ*, 27.01.1981 г.р., с. Побединское ЧИАССР.
67. АЙДАЕВ ИБРАГИМ ГОГЛАЕВИЧ*, 15.11.1977 г.р., г. Грозный ЧИАССР.
68. АЙДАМИРОВ ВАХИТ КАЧАЕВИЧ*, 22.11.1964 г.р., с. Агишбатой Веденского района ЧИАССР.
69. АЙСУМОВ ЗАУРБЕК АСЛАМБЕКОВИЧ*, 24.09.1990 г.р., с. Шали Шалинского района ЧИАССР.
70. АЙТАЕВ АЛИ САЛМАНОВИЧ*, 16.11.1973 г.р., с. Киров-Юрт Введенского района ЧИАССР.
71. АЙТАМИРОВ ЗЕЛИМХАН ИСЛАМХАНОВИЧ*, 10.01.1964 г.р., с. Татай-Хутор Ножай-Юртовского района ЧИАССР.
72. АЙТУКАЕВ АЛИБЕК ЮНУСОВИЧ*, 24.01.1979 г.р., с. Хамавюрт Хасавюртовского района ДАССР.
73. АЙТУКАЕВ МЯХЬДИ МОВСАЕВИЧ*, 23.10.1984 г.р., ст. Дубовская Шелковского района Чеченской Республики.
74. АКАВОВ ЗАУР ГУСЕЙНОВИЧ*, 11.08.1973 г.р., г. Махачкала ДАССР.
75. АКАЕВ СУПЬЯН ХАСУЕВИЧ*, 04.03.1976 г.р., с. Катыр-Юрт Ачхой-Мартановского района ЧИАССР.
76. АКБУЛАТОВ АСЛАН САЛМАНОВИЧ*, 15.05.1972 г.р., с. Побединское Грозненского района ЧИАССР.
77. АКИЕВ АДАМ АЮБОВИЧ*, 01.07.1955 г.р., с. Джатсай Ильичевского района Ю-Казахстанской области.
78. АКИШИН ВИТАЛИЙ НИКОЛАЕВИЧ*, 07.05.1969 г.р., г. Дятьково Брянской области.
79. АЛАЕВ АСЛАН САЙДАХМАДОВИЧ*, 13.06.1978 г.р., с. Нижний Герзель Гудермесского района ЧИАССР.
80. АЛАЕВ ХАСАИН АБДУЛХАНОВИЧ*, 15.05.1976 г.р., с. Нижний Герзель Гудермесского района ЧИАССР.
81. АЛАРХАНОВ МАГОМЕД ЭДАМОВИЧ*, 05.11.1973 г.р., с. Суворов-Юрт Гудермесского района ЧИАССР.
82. АЛАУДИНОВ АЛАШ АЛЬВИЕВИЧ*, 07.03.1960 г.р., Чири-Юрт Шалинского района ЧИАССР.
83. АЛДАМОВ АЛИХАН ЛЕЧИЕВИЧ*, 05.10.1977 г.р., с. Советское Советского района ЧИАССР.
84. АЛДАМОВ АСЛАН ЛЕЧАЕВИЧ*, 24.07.1976 г.р., с. Золотуха Актюбинского района Астраханской области.
85. АЛДАНОВ ХАБИБ МАГОМЕДОВИЧ*, 13.09.1975 г.р., с. Верхний Дженгутай Буйнакского района ДАССР.
86. АЛЕКПЕРОВ МУСА НУХБАБАЕВИЧ*, 15.03.1972 г.р., с. Побегайловка Минераловодского района Ставропольского края.
87. АЛЕКСАНДРОВ НИКОЛАЙ ГЕННАДЬЕВИЧ*, 09.11.1982 г.р., г. Новочебоксарск Чувашской Республики.
88. АЛЕКСЕЙЧИК СЕРГЕЙ АЛЕКСАНДРОВИЧ*, 18.04.1978 г.р., г. Чимкент Республики Казахстан.
89. АЛЕРОЕВ ИБРАГИМ ХУСЕНОВИЧ*, 19.06.1976 г.р., с. Пседах Малгобекского района ЧИАССР.
90. АЛЕРОЕВ ХАЛИД СУЛТАНОВИЧ*, 03.02.1974 г.р., с. Пседах Малгобекского района Республики Ингушетия.
91. АЛИ СОЙТЕКИНОГЛЫ*, 10.02.1977 г.р., Карасу, Турция.
92. АЛИБАЕВ МАРСЕЛЬ УРАЛОВИЧ*, 09.07.1974 г.р., п. Уфимский Хайбуллинского района Республики Башкортостан.
93. АЛИБИЕВ РАМАЗАН ИЛЬМАТИЕВИЧ*, 21.08.1976 г.р., с. Эдиссия Курского района Ставропольского края.
94. АЛИДИБИРОВ ЗАГИДГАДЖИ МАГОМЕДОВИЧ*, 20.12.1960 г.р., с. Алак Ботлихского района Республики Дагестан.
95. АЛИЕВ АБДУЛЛА УВАЙСОВИЧ*, 28.01.1984 г.р., с. Билихуль Джувалинского района Джамбульской области КазССР.
96. АЛИЕВ АСЛАН БАЛАУДИНОВИЧ*, 08.01.1987 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
97. АЛИЕВ АСЛАН ЮНУСОВИЧ*, 07.10.1981 г.р., г. Грозный ЧИАССР.
98. АЛИЕВ БАУДИН РУСЛАНОВИЧ*, 15.02.1983 г.р., с. Ачхой-Мартан ЧИАССР.
99. АЛИЕВ ИСА ХУСЕЙНОВИЧ*, 24.04.1987 г.р., с.Золотуха Ахтубинского района Астраханской области.
100. АЛИЕВ РУСЛАН БОРИСОВИЧ*, 02.01.1974 г.р., г. Малгобек Республики Ингушетия.
101. АЛИЕВ СУЛТАН ВАХАЕВИЧ*, 05.01.1959 г.р., с. Алхазурово Урус-Мартановского района ЧИАССР.
102. АЛИЕВ ТИМУРЛАН АЙГУНОВИЧ*, 04.12.1964 г.р., г. Буйнакск Республики Дагестан.
103. АЛИЕВ ХУСАЙН АБДУЛРЕШИДОВИЧ*, 24.12.1979 г.р., с. Ножай-Юрт Ножай-Юртовского района Чеченской Республики.
104. АЛИЛОВ ОМАР МАГОМЕДОВИЧ*, 20.07.1962 г.р., с. Вихли Кулинского района Республики Дагестан.
105. АЛИЛОВА СОФИЯ МАГОМЕДОВНА*, 10.03.1986 г.р., с. Кули Кулинского р-на Республики Дагестан.
106. АЛИСУЛТАНОВ ВАХИТ АЛИХАДЖИЕВИЧ*, 24.12.1984 г.р., с. Курчалой ЧИАССР.
107. АЛИСУЛТАНОВ РАШИД ТАГИРОВИЧ*, 03.09.1982 г.р., с. Чонтаул Кизилюртовского района Республики Дагестан.
108. АЛИСУЛТАНОВ САЙХАН АЛИХАНОВИЧ*, 16.10.1988 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
109. АЛИСХАНОВ АСЛАН ВАХАЕВИЧ*, 10.08.1981 г.р., ст. Вознесеновская Малгобекского района ЧИАССР.
110. АЛИХАДЖИЕВ АСЛАН МОВЛАЕВИЧ*, 10.01.1982 г.р., с. Зоны Шатойского района Чеченской Республики.
111. АЛИХАДЖИЕВ ИСА ШАМИЛЕВИЧ*, 14.09.1978 г.р., с. Автуры Шалинского района Чеченской Республики.
112. АЛИХАНОВ АБИЛЬ АЗИМОВИЧ*, 22.10.1989 г.р., пос. Заволжский Палласовского района Волгоградской области.
113. АЛИХАНОВ БЕСЛАН ЗИНУЛБЕКОВИЧ*, 06.02.1984 г.р., с. Сержень-Юрт Шалинского района ЧИАССР.
114. АЛСОЛТАНОВ МУСА ОЛХАЗУРОВИЧ*, 06.10.1983 г.р., поселок Татал Юстинского района Калмыкской АССР.
115. АЛХАЗУРОВ ГАЙИРБЕК КАРИМОВИЧ*, 07.12.1977 г.р., ст. Курдюковская Шелковского района Чечено-Ингушской АССР.
116. АЛХАНОВ МАГОМЕД ХАСАНОВИЧ*, 24.10.1982 г.р., с. Надтеречное, Надтеречного р-на ЧИАССР.
117. АЛХАНОВ ОМАР АБУБАКАРОВИЧ*, 08.01.1977 г.р., г. Грозный ЧИАССР.
118. АЛХАНОВ РУСЛАН ГУМАХАЕВИЧ*, 15.09.1969 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
119. АЛХОТОВ АРТЕМ ЯКУБОВИЧ*, 17.11.1983 г.р., с. Байтарки Ножай-Юртовского района ЧИАССР.
120. АЛЬ-ЖУНАЙДИ АММАР МАХМУД*, 01.05.1975 г.р., г. Хеврон, Палестина.
121. АЛЬБУКАЕВ АНЗОР ДУКВАХОВИЧ*, 08.09.1984 г.р., с. Валерик Ачхой-Мартановского района ЧИАССР.
122. АЛЬДАГИР АМИН БУТРОС*, 27.04.1964 г.р., г. Хама Сирийской Арабской Республики.
123. АЛЬМУРЗАЕВ АЛИ АЛИЕВИЧ*, 09.07.1958 г.р., г. Караганда КазССР.
124. АЛЬМУРЗИЕВ АЛАУДИН ОСМАНОВИЧ*, 14.08.1980 г.р., г. Нальчик Кабардино-Балкарской АССР.
125. АМАГОВ РУСЛАН МУХМАТСАНИЕВИЧ*, 25.01.1978 г.р., ст. Орджоникидзевская Сунженского района ЧИАССР.
126. АМАЕВ МУХМАД МАЛИКОВИЧ*, 10.04.1978 г.р., с. Новотерское Наурского района ЧИАССР.
127. АМАЕВ РИЗВАН РАМЗАНОВИЧ*, 25.06.1972 г.р., г. Аргун ЧИАССР.
128. АМАЕВ ШАРПУДИН ЛЕЧИЕВИЧ*, 20.08.1958 г.р., с. Гехи Урус-Мартановского района ЧИАССР.
129. АМАНКАЕВ АЛИМХАН КАЙТЕРБИЕВИЧ*, 08.01.1977 г.р., с. Токуй-Мектеб Ногайского района Республики Дагестан.
130. АМРИЕВ ЗУРАБ СУЛУМБЕКОВИЧ*, 15.05.1981 г.р., г. Грозный ЧИАССР.
131. АНАСОВ САИДБЕК КУРБАНОВИЧ*, 15.12.1981 г.р., с. Энгель-Юрт Гудермесского района ЧИАССР.
132. АНДРЕЕВ АНДРЕЙ АЛЕКСАНДРОВИЧ*, 24.10.1984 г.р., станица Смоленская Северского р-на Краснодарского края.
133. АНДРЕЕВ РОМАН ВЛАДИМИРОВИЧ*, 24.07.1960 г.р., г. Гатчина Ленинградской области.
134. АНЧИН АЛЕКСАНДР АРКАДЬЕВИЧ*, 26.07.1982 г.р., п. Удачный Мирнинского района Якутской АССР.
135. АПАЕВ ЮНУС АХМЕДОВИЧ*, 06.10.1986 г.р., с. Валерик Ачхой-Мартановского района ЧИАССР.
136. АРАХОВ АРКАДИЙ АЛИКОВИЧ*, 11.11.1976 г.р., г. Елгава Латвийской ССР.
137. АРСАЕВ АНЗОР АСАНОВИЧ*, 04.02.1980 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
138. АРСАЕВ ИБРАГИМ ВИСИРПАШАЕВИЧ*, 02.11.1979 г.р., г. Хасавюрт ДАССР.
139. АРСАЕВ МАСХУД ЮНАДИЕВИЧ*, 04.12.1974 г.р., с. Мескеты Ножай-Юртовского района ЧИАССР.
140. АРСАМАКОВ ШАМИЛЬ ВАХИДОВИЧ (ВАХИТОВИЧ)*, 21.11.1978 г.р., с. Ведучи Сунженского района ЧИАССР.
141. АРСАМИКОВ АЛИХАН АБДУЛАЕВИЧ*, 14.04.1984 г.р., с. Шали Шалинского района Чеченской Республики.
142. АРСАМИКОВ АНЗОР САЛАУДИНОВИЧ*, 08.08.1983 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
143. АРСАМИКОВ РУСТАМ САЛАУДИНОВИЧ*, 16.11.1978 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
144. АРСАМИРЗУЕВ ЗЕЛИМХАН АЕЛЬЕВИЧ*, 08.10.1984 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
145. АРСАНОВ ВИСХАН ИСАЕВИЧ*, 20.02.1988 г.р., с. Курчалой Шалинского района ЧИАССР.
146. АРСАНОВ РУСЛАН ИСАЕВИЧ*, 25.12.1977 г.р., с. Курчалой Шалинского района ЧИАССР.
147. АРСАНУКАЕВ ЗУБАЙРА ЭЛИЕВИЧ*, 17.03.1987 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
148. АРСАНУКАЕВ МОВСАР ХАСАНОВИЧ*, 01.07.1978 г.р., г. Аргун ЧИАССР.
149. АРСАНУКАЕВ МУСЛИМ ВАХАЕВИЧ*, 24.10.1975 г.р., с. Побединское Грозненского района Чеченской Республики.
150. АРСАНУКАЕВ УМАЛТ МУСАЕВИЧ*, 19.01.1973 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
151. АРСАХАНОВ ХАСАН АХМЕТОВИЧ*, 30.12.1988 г.р., с. Хамби-Ирзи Ачхой-Мартановского района ЧИАССР.
152. АРСЕЛЬГОВ МУХАМЕД-АЛИ ЮСУПОВИЧ*, 09.05.1976 г.р., с. Насыр-Корт Назрановского района ЧИАССР.
153. АРСЛАНБЕКОВ АЛЬБЕРТ АРСЛАНБЕКОВИЧ*, 15.11.1978 г.р., п. Дубки гор. Кизилюрт Республики Дагестан.
154. АРСЛАНОВ ЮСУП АБДУРАХМАНОВИЧ*, 08.08.1968 г.р., с. Карамахи Буйнакского района Республики Дагестан.
155. АРСНУКАЕВ РУСЛАН ВАХАЕВИЧ*, 14.10.1976 г.р., с. Катар-Юрт Ачхой-Мартановского района ЧИАССР.
156. АРСТЕМИРОВ РАСУЛ ШЕДИТОВИЧ*, 24.04.1982 г.р., с. Киров-Юрт Веденского района ЧИАССР.
157. АРХАГОВ РУСТАМ РУСЛАНОВИЧ*, 26.05.1983 г.р., аул Кара-Паго Прикубанского района Карачаево-Черкесской Республики.
158. АРЦАЕВ ИБРАГИМ ВИСИРПАШАЕВИЧ*, 02.11.1979 г.р., г. Хасавюрт Республики Дагестан.
159. АРЦУЕВ АХМЕД АБДУЛАЕВИЧ (АРЦУЕВ АРТУР АБДУЛАЕВИЧ)*, 08.07.1979 г.р., с. Ново-Шарой Ачхой-Мартановского района ЧИАССР (08.07.1979 г.р., с. Ново-Шарой Ачхой-Мартановского района ЧИАССР).
160. АСЕЛЬДЕРОВ МАГОМЕД ГУСЕНОВИЧ*, 18.06.1979 г.р., с.Карамахи Буйнакского района Республики Дагестан.
161. АСЕЛЬДЕРОВ ЮСУП ГУСЕЙНОВИЧ*, 24.03.1974 г.р., с.Карамахи Буйнакского района Республики Дагестан.
162. АСЛАМБЕКОВ СУЛТАН МУМАДИЕВИЧ*, 24.11.1975 г.р., с. Агишты Веденского района ЧИАССР.
163. АСЛАМКАДИРОВ БОРЗ-АЛИ ЭЛЬМАНОВИЧ*, 07.07.1971 г.р., с. Агишбатой Чеченской Республики.
164. АСЛАНБЕКОВ МАГАДЫ СУЛТАНОВИЧ*, 09.12.1974 г.р., с. Ачхой-Мартан ЧИАССР.
165. АСЛАНБЕКОВ РУСЛАН МУХТАРОВИЧ*, 23.07.1983 г.р., с. Дубовское Дубовского района Ростовской области.
166. АСТАМИРОВ АСЛАН РАМЗАНОВИЧ*, 02.04.1977 г.р., г. Грозный ЧИАССР.
167. АСТАМИРОВ ИЛЕС ИСАЕВИЧ*, 05.01.1975 г.р., г. Грозный Чечено-Ингушской АССР.
168. АСУХАНОВ СОСЛАН АБУБАКАРОВИЧ*, 25.03.1984 г.р., г. Аргун ЧИАССР.
169. АСХАБАЛИЕВ ШАМИЛЬ МАГОМЕДОВИЧ*, 10.07.1975 г.р., г. Махачкала Республики Дагестан.
170. АСХАБОВ АДАМ ГЕБЕРТУЕВИЧ*, 23.02.1984 г.р., х. Фомин Заветинского района Ростовской области.
171. АСХАБОВ АДАМ ИСАЕВИЧ*, 07.02.1977 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
172. АСХАБОВ РУСЛАН ДАЙДАЛОВИЧ*, 27.08.1968 г.р., с. Майколь Кустанаевской области КССР.
173. АТАБИЕВ РАШИД ХАСАНОВИЧ*, 21.07.1980 г.р., г. Усть-Джегута Ставропольского края КЧАО.
174. АТАЕВ КАЗБЕК МАГОМЕДОВИЧ*, 31.01.1978 г.р., г. Малгобеке ЧИАССР.
175. АТГИРИЕВ ТУРПАЛАЛИ АЛАУДИНОВИЧ*, 08.05.1969 г.р., с. Аллерой Шалинского района ЧИАССР.
176. АТНАЗОВ САИД-ХУСЕЙН МАГОМЕДОВИЧ*, 20.12.1981 г.р., г. Грозный ЧИАССР.
177. АТСАЛАМОВ ЮНАДИ АДАМОВИЧ*, 28.09.1978 г.р., с. Вярды Советского района ЧИАССР.
178. АТУЕВ ИСЛАМ ИМХАДЖИЕВИЧ*, 28.07.1976 г.р., г. Аргун ЧИАССР.
179. АУШЕВ МАГОМЕД МУССИЕВИЧ*, 16.09.1978 г.р., г. Грозный ЧИАССР.
180. АХАЕВ ЭЛЬБЕК ЛУЛУЕВИЧ*, 01.04.1963 г.р., с. Ца-Ведено Веденского района Чеченской Республики.
181. АХМАДОВ АЛЬВИ АБДУЛБЕКОВИЧ*, 31.10.1978 г.р., с. Старая Сунжа Грозненского района ЧИАССР.
182. АХМАДОВ РИЗВАН ЛЕЧАЕВИЧ*, 20.04.1977 г.р., с. Кулары Грозненского района ЧИАССР.
183. АХМАДОВ РУСЛАН ИСРАИЛОВИЧ*, 08.12.1966 г.р., с. Исти-Су Гудермесского района ЧИАССР.
184. АХМАДОВ ХАВАЖИ ХАСАНОВИЧ*, 29.12.1978 г.р., с. Мескер-Юрт Шалинского района ЧИАССР.
185. АХМАДОВ ХАСАМБЕК САЙД-АРБИЕВИЧ*, 12.03.1975 г.р., с. Батурино Чапаевского района Уральской области.
186. АХМАДОВ ХАСАН САЛАУДЫНОВИЧ*, 21.03.1977 г.р., с. Гойты Урус-Мартановского района Чеченской Республики.
187. АХМАДХАНОВ ЗАЙНДИ УМАРОВИЧ*, 22.07.1948 г.р., Джамбульская область Республики Казахстан.
188. АХМАДХАНОВ ТИМУР ШЕЙХ-АХМЕДОВИЧ*, 24.09.1975 г.р., г. Гудермес Чеченской Республики.
189. АХМАТОВ РУСЛАН ИМРАНОВИЧ*, 09.01.1971 г.р., п. Горагорск Надтеречного района ЧИАССР.
190. АХМЕДОВ СУЛТАН АЛИЕВИЧ*, 17.11.1981 г.р., с. Замай-Юрт Ножай-Юртовского района ЧИАССР.
191. АХМЕДОВ ШАВКАТ РАВИЛЬЕВИЧ*, 22.09.1985 г.р., п. Бустон Матчинского района Ленинабадской обл. Таджикской ССР.
192. АХМЕРХАДЖИЕВ АЮБ ТИМИРХАДЖИЕВИЧ*, 24.06.1971 г.р., ст. Гребенская Шелковского района ЧИАССР.
193. АХМЕТСАФИН МУСА ШАРИФОВИЧ*, 10.05.1977 г.р., г. Белорецк.
194. АЦАЕВ АДАМ ТАУСОВИЧ*, 15.10.1975 г.р., пос. Краснокунский Краснокунского района Павлодарской области.
195. АШАХАНОВ КАХИМ ИСРАПИЛОВИЧ*, 24.12.1984 г.р., ст. Наурская Наурского района ЧИАССР.
196. АШАХАНОВ РУСЛАН САЙПАЕВИЧ*, 30.10.1972 г.р., с. Самашки Ачхой-Мартановского р-на Чеченской Республики.
197. АШИКОВ ШАМИЛЬ БАГАВДИНОВИЧ*, 25.08.1971 г.р., с. Гуниб Гунибского района Республики Дагестан.
198. АЮБОВ ИМАЛИ ВИСАРХАДЖИЕВИЧ*, 22.06.1978 г.р., пос. Новогрозненский Гудермесского района ЧИАССР.
199. БАДАЕВ АНЗОР МАГОМЕДОВИЧ*, 29.05.1985 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
200. БАДАШЕВ АЛХАЗУР ШАМИЛЬЕВИЧ*, 24.07.1975 г.р., г. Грозный ЧИАССР.
201. БАДУЕВ САЙДМАГОМЕД ХУСЕЙНОВИЧ*, 19.05.1986 г.р., с. Урус-Мартан ЧИАССР.
202. БАДУРГОВ ЗЕЛИМХАН МАГОМЕДОВИЧ*, 10.06.1982 г.р., Ачхой-Мартановский район ЧИАССР.
203. БАЗАЕВ ШЕМИЛЬ ЖАМЛЕЙНОВИЧ*, 24.02.1976 г.р., г. Шали ЧИАССР.
204. БАЗУЕВ УМАР УЛЬБИЕВИЧ*, 27.01.1977 г.р., г. Эмба Мугаджарского района Казахской ССР.
205. БАЗУРКАЕВ АСЛАНБЕК ВАХАЕВИЧ*, 15.03.1975 г.р., с. Исти-Су Гудермесского района ЧИАССР.
206. БАЗУРКАЕВ СУЛТАН АБДУЛАЕВИЧ*, 06.01.1963 г.р., с. Баматюрт Хасавюртовского района Республики Дагестан.
207. БАЙДАРОВ ШАМХАН ХАВАЖЕВИЧ*, 16.10.1977 г.р., г. Грозный ЧИАССР.
208. БАЙДУЛАЕВ АНЗОР АЛХАЕВИЧ*, 29.10.1987 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
209. БАЙДУЛАЕВ ДОККА АЛХАЕВИЧ*, 17.05.1980 г.р., с. Алхан-Кала Грозненского р-на ЧИАССР.
210. БАЙДУЛАЕВ КАЗБЕК ДЖАЛАУДИНОВИЧ*, 23.09.1988 г.р., хутор Страховский Новоанинского района Волгоградской области.
211. БАЙЗУРКАЕВ АРТУР АБУЕВИЧ*, 05.12.1981 г.р., г. Новый Узень Мангышлакской области КазССР.
212. БАЙМУРАТОВ АРИБИЙ АБДУЛЛАЕВИЧ*, 26.01.1987 г.р., с. Борагангечу Хасавюртовского района ДАССР.
213. БАЙМУРЗАЕВ УМАР АЛИЕВИЧ*, 02.04.1983 г.р., с. Макажой Веденского района ЧИАССР.
214. БАЙРАМУКОВ МУРАТБИ АЙГУФОВИЧ*, 08.06.1976 г.р., ст. Сторожевая Зеленчукского района Карачаево-Черкесской Республики.
215. БАЙСАГУРОВ АБДУЛАХИ ШАРИПОВИЧ*, 27.10.1986 г.р., с. Курчалой Шалинского района ЧИАССР.
216. БАЙСАЕВ УМАР ДАУДОВИЧ*, 24.04.1977 г.р., х. Мокро-Соленый Цимлянского района Ростовской обл.
217. БАЙСИЕВ ИСЛАМ ХАМАДОВИЧ*, 21.10.1991 г.р., с. Хаттуни Веденского района Чеченской Республики.
218. БАЙСУЕВ МАХДИ МУСАЕВИЧ*, 25.10.1978 г.р., с. Энгель-Юрт Гудермесского района ЧИАССР.
219. БАЙСУРОВ КАЗБЕК АБУХОЕВИЧ*, 21.06.1980 г.р., с. Курчалой ЧИАССР.
220. БАЙТАЕВ БЕСЛАН ХУСАИНОВИЧ*, 19.10.1975 г.р., с. Самашки Ачхой-Мартановского р-на ЧИАССР.
221. БАЙТАЛАЕВ МУСЛОВ ХАЙДАРОВИЧ*, 06.05.1985 г.р., с. Дарго Веденского района ЧИАССР.
222. БАЙТУКАЕВ АНЗОР ЗАЙНДИЕВИЧ*, 12.06.1980 г.р., с. Мескер-Юрт ЧИАССР.
223. БАЙЧОРОВ АРСЕН АХМАТОВИЧ*, 08.01.1984 г.р., г. Карачаевск Карачаево-Черкесской Республики.
224. БАКАЕВ АХДАН БАУДОВИЧ*, 06.10.1980 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
225. БАКАЕВ ИДРИС САЙДАЕВИЧ*, 23.02.1971 г.р., ст. Наурская Наурского района ЧИАССР.
226. БАКАЕВ МАГДАН БАУДИНОВИЧ*, 09.11.1970 г.р., с. Энбексий-Карабулакский Алакульского р-на Талды-Курганской обл.
227. БАКАЛОВ МАГОМЕД ХАСАНОВИЧ*, 19.09.1979 г.р., с. Н.Атаги Шалинского района ЧИАССР.
228. БАКАШЕВ ДЖАМБУЛАТ ДЕНИЛБЕКОВИЧ*, 24.07.1984 г.р., с. Ведено Веденского района ЧИАССР.
229. БАКИЕВ ШАМИЛЬ АХМАТОВИЧ*, 06.10.1981 г.р., с. Маловодное Энбекшиказахского района Алма-Атинской области Казахской ССР.
230. БАЛАЕВ ТАМИРЛАН ТУРУЕВИЧ*, 02.10.1970 г.р., с. Харачой Веденского района ЧИАССР.
231. БАЛАНТАЕВ ВЛАДИМИР АЛЕКСАНДРОВИЧ*, 22.06.1973 г.р., г. Кемерово.
232. БАЛТИЕВ УМАЛТ ДЖАМЛАЙЛОВИЧ*, 26.11.1983 г.р., с. Шали Шалинского района Чеченской Республики.
233. БАЛУЕВ ИСМАИЛ ИСХАКОВИЧ*, 16.12.1974 г.р., г. Нальчик, с. Хасанья Кабардино-Балкарской Республики.
234. БАНТАЕВ АРБИ ХОЖ-БАУДИНОВИЧ*, 28.08.1981 г.р., с. Комсомольское Гудермесского района ЧИАССР.
235. БАРАКАЕВ ШАРАБДИН САМОВДИНОВИЧ*, 16.09.1973 г.р., с. Брагуны Гудермесского района ЧИАССР.
236. БАРАХАЕВ ХАМИТ АХИЯДОВИЧ*, 28.03.1954 г.р., г. Караганда Казахской ССР.
237. БАРАХОЕВ ИССА АХЪЯДОВИЧ*, 20.06.1968 г.р., с. Сурхахи Республики Ингушетия.
238. БАРЗАКОВ МАГОМЕД МАХМУДОВИЧ*, 13.05.1966 г.р., с. Мескиты Ножай-Юртовского района ЧИАССР.
239. БАРЗИГОВ ЛЕЧИ АХЪЯДОВИЧ*, 08.07.1979 г.р., с. Далготой Шалинского района ЧИАССР.
240. БАРКИНХОЕВ АБУБУКАР ХАДЖИБИКАРОВИЧ*, 24.08.1982 г.р., с. Сурхахи Назрановского района ЧИАССР.
241. БАРКИНХОЕВ РУСЛАН ЗЕЛИМХАНОВИЧ*, 21.06.1984 г.р., г. Есиль Есильского района Тургайской области Казахской ССР.
242. БАСАЕВ АЛХАЗУР САЛМАНОВИЧ*, 17.07.1962 г.р., с. Мартан-Чу Урус-Мартановского района ЧИАССР.
243. БАСАЕВ АЛЬВИ МУСАЕВИЧ*, 25.09.1968 г.р., с. Мартан-Чу Урус-Мартановского района ЧИАССР.
244. БАСАЕВ ВИС-АЛИ ХОЖАХМЕДОВИЧ*, 29.10.1972 г.р., с. Грушевое Урус-Мартановского района ЧИАССР.
245. БАСХАНОВ ИСЛАМ МУРТАНОВИЧ*, 19.11.1980 г.р., с. Побединское Грозненского района ЧИАССР.
246. БАСХАНОВ РУСТАМ МАХАМЕДОВИЧ*, 21.06.1984 г.р., с. Новое Солкушино Наурского района ЧИАССР.
247. БАТАГОВ МАГМЕД АРБИЕВИЧ*, 03.08.1981 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
248. БАТАЕВ АСЛАН ЛОМ-АЛИЕВИЧ*, 19.09.1984 г.р., с. Урус-Мартан ЧИАССР.
249. БАТАЕВ АХМЕД РАХМАНОВИЧ*, 15.04.1982 г.р., с. Урус-Мартан ЧИАССР.
250. БАТАЕВ ВИСИТ НУРДИЕВИЧ*, 03.11.1985 г.р., г. Аргун Чеченской Республики.
251. БАТАЕВ РУСЛАН ХОЖАЕВИЧ*, 29.03.1970 г.р., ст. Сары-Су Шелковского района ЧИАССР.
252. БАТАЕВ ТУРКО САЛМАНОВИЧ*, 20.12.1986 г.р., г. Грозный ЧИАССР.
253. БАТАЕВ УМАР ИСАЕВИЧ*, 17.08.1981 г.р., с. Ачхой-Мартановского района ЧИАССР.
254. БАТАКОВ ВАХИТ СУПЬЯНОВИЧ*, 03.08.1973 г.р., с. Брагуны Гудермесского района ЧИАССР.
255. БАТАЛОВ АЛИХАН СУЛТАНОВИЧ*, 05.08.1979 г.р., с. Серноводск Сунженского района ЧИАССР.
256. БАТАЛОВ АСЛАМБЕК ХАСЕЙНОВИЧ*, 11.03.1968 г.р., г. Аргун Шалинского р-на Чеченской Республики.
257. БАТАЛОВ ИДРИС ЭМАЛИЕВИЧ*, 24.06.1981 г.р., с. Джалка Гудермесского района ЧИАССР.
258. БАТАЛОВ РУСТАМ МАГОМЕДОВИЧ*, 25.05.1972 г.р., г. Южно-Сухокумск Республики Дагестан.
259. БАТАЛОВ ХАМЗАТ ЗАЙНДИЕВИЧ*, 31.03.1981 г.р., с. Серноводск Сунженского района ЧИАССР.
260. БАТУКАЕВ САЙДБЕК СИДИКОВИЧ*, 22.04.1987 г.р., с. Ведено Веденского района ЧИАССР.
261. БАТЧАЕВ АЛИМ СУЛЕЙМАНОВИЧ*, 07.08.1972 г.р., ст. Сторожевая Зеленочукского района Карачаево-Черкесской Республики.
262. БАТЫРОВ БАТЫР ГАДЖИЕВИЧ*, 02.01.1947 г.р., с. Карамахи Буйнакского района Республики Дагестан.
263. БАТЫРОВ СУЛЕЙМАН ГАДЖИЕВИЧ*, 21.06.1963 г.р., с. Карамахи Буйнакского района Республики Дагестан.
264. БАХАЕВ АХМЕД РАМЗАНОВИЧ*, 22.09.1975 г.р., г. Грозный Чеченской Республики.
265. БАХАЕВ РОМАН МАХМУДОВИЧ*, 24.05.1976 г.р., с. Серноводск ЧИАССР.
266. БАХАЕВ ХАМЗАТ ХАРОНОВИЧ*, 15.09.1976 г.р., х. Фомин Заветинского района Ростовской области.
267. БАХАРЧИЕВ МАГОМЕД САИДСЕЛИМОВИЧ*, 19.11.1972 г.р., с. Серноводск Сунженского района ЧИАССР.
268. БАХАРЧИЕВ РУСЛАН САЙДАМИНОВИЧ*, 24.02.1978 г.р., село Промысловка Лимановского р-на Астраханской обл.
269. БАХВАЛОВ АЛЕКСЕЙ ЕВГЕНЬЕВИЧ*, 17.09.1975 г.р., г. Ленинград.
270. БАХТИЕВ АСЛАН МУСАЕВИЧ*, 13.09.1976 г.р., с. Альтиево Назрановского района ЧИАССР.
271. БАЦАЕВ АБДУЛСАЙД ЖАПАРОВИЧ*, 23.04.1966 г.р., с. Зандак Ножай-Юртовского района ЧИАССР.
272. БАЦИЕВ ДАУД ДОККАЕВИЧ*, 13.05.1983 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
273. БАЦИЕВ ИСЛАМ САЙДАХМАТОВИЧ*, 20.10.1977 г.р., г. Хасавюрт ДАССР.
274. БАЦИЕВ РУСЛАН АНАТОЛЬЕВИЧ*, 23.03.1978 г.р., г. Хасавюрт Республики Дагестан.
275. БАЧАЕВ ИСЛАМ ИСАЕВИЧ*, 21.11.1983 г.р., с. Серноводск Сунженского района ЧИАССР.
276. БАЧАЕВ МУСА УСМАНОВИЧ*, 05.03.1983 г.р., с. Старая Сунжа Грозненского района ЧИАССР.
277. БАЧАЕВ МУСЛИМ ИСАЕВИЧ*, 19.12.1977 г.р., с. Серноводск Сунженского района ЧИАССР.
278. БАЧИГОВ АКРАМАН ХАРУНОВИЧ*, 04.04.1986 г.р., с. Цаца Светлояровского района Волгоградской области.
279. БАШЕЛУТСКОВ ДАВИД ВАГАРШАКОВИЧ*, 17.01.1991 г.р., село Ахалкалаки Ахалкалакского района Республики Грузия.
280. БАШИРОВ БИСЛАН ВАХАЕВИЧ*, 31.01.1982 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
281. БАШТАРОВ АДАМ МУСАЕВИЧ*, 08.02.1984 г.р., г. Грозный ЧИАССР.
282. БЕГЕЛЬДИЕВ ТАХИР ХАЙРЕТДИНОВИЧ*, 05.11.1974 г.р., с. Кара-Тюбе Нефтекумского района Ставропольского края.
283. БЕГИТОВ АСЛАНБЕК СОСЛАНБЕКОВИЧ*, 01.06.1965 г.р., с. Хал-Калой Советского района ЧИАССР.
284. БЕЙДУЛЛАЕВ ЗАУР ТЕМРАЗОВИЧ*, 27.02.1985 г.р., г. Махачкала ДАССР.
285. БЕКАЕВ КАЗБЕК ШАМСУДИЕВИЧ*, 24.01.1979 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
286. БЕКМУРЗАЕВ РАСАМБЕК СУЛЕЙМАНОВИЧ*, 17.09.1980 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
287. БЕКОВ ИССА УВАЙСОВИЧ*, 27.10.1972 г.р., с. Верхние Ачалуки Малгобекского района ЧИАССР.
288. БЕКСУЛТАНОВ МОВСАР ВАХАЕВИЧ*, 09.11.1983 г.р., г. Грозный ЧИАССР.
289. БЕКСУЛТАНОВ РУСЛАН ВАХАЕВИЧ*, 30.01.1983 г.р., с. Мирный Курского района Ставропольской области.
290. БЕЛАШЕВ ВЛАДИМИР ИЛЬИЧ*, 30.07.1961 г.р., г. Кунгур Пермской области.
291. БЕЛИЕВ РУСЛАН ХУМАЙДОВИЧ*, 12.12.1979 г.р., г. Хасавюрт ДАССР.
292. БЕЛКИН ДМИТРИЙ НИКОЛАЕВИЧ*, 27.01.1976 г.р., п. Шишино Топкинского р-на Кемеровской области.
293. БЕЛОВ АЛЕКСАНДР ВАСИЛЬЕВИЧ*, 08.07.1979 г.р., г. Зеленодольск Республики Татарстан.
294. БЕЛОЗЕРОВ АЛЕКСЕЙ ВИКТОРОВИЧ*, 26.03.1980 г.р., с. Красный Городок Сергиевского района Самарской области.
295. БЕРГОЕВ СУЛИМ АБДУЛАЕВИЧ*, 16.08.1975 г.р., с. Катыр-Юрт Ачхой-Мартановского района ЧИАССР.
296. БЕРИЕВ АСЛАНБЕК МАКШЕРИПОВИЧ*, 26.05.1974 г.р., ст. Ильиноская Грозненского района ЧИАССР.
297. БЕРСАНОВ ЛЕММА МУСАЕВИЧ*, 18.08.1985 г.р., г. Грозный ЧИАССР.
298. БЕРСАНОВ ЛОМ-АЛИ ЛОМАЕВИЧ*, 02.02.1982 г.р., с. Алхан-Кала Грозненского района ЧИАССР.
299. БЕРСАНОВ ЛОМ-АЛИ МУСАЕВИЧ*, 18.08.1985 г.р., г. Грозный ЧИАССР.
300. БЕРСАНОВ САИД-ХУСЕЙН МУСАЕВИЧ*, 01.05.1977 г.р., с. Дуба-Юрт Шалинского района Чеченской Республики.
301. БЕТАЛМИРЗАЕВ АСЛАН МОВЛАДОВИЧ*, 08.06.1975 г.р., совхоз “Коммунизм” Амангельдинского района Тургайкой обл. КазССР.
302. БЕТЕРГИРАЕВ ЗАУР ХИЗИРОВИЧ*, 28.05.1981 г.р., с. Шали ЧИАССР.
303. БЕЦИЕВ ХАСАН ЭМИЕВИЧ*, 03.04.1976 г.р., с. Ведено Веденского района Чеченской Республики.
304. БИБУЛАТОВ БАДРУДИ ШАХАЕВИЧ*, 07.12.1972 г.р., с. Элистанжи Веденского района ЧИАССР.
305. БИБУЛАТОВ САЙХАН АЛГАЗИРОВИЧ*, 21.07.1982 г.р., с. Ачхой-Мартан ЧИАССР.
306. БИДАГОВ РУСЛАН МАГОМЕДОВИЧ*, 17.06.1978 г.р., с. Карамахи Буйнакского района Республики Дагестан.
307. БИДЖИЕВ ХАЗРЕТ РАКАЕВИЧ*, 06.07.1960 г.р., пос. Красноводский Республики Казахстан.
308. БИДИЕВ ЯКУБ АХМЕДОВИЧ*, 30.09.1979 г.р., с. Дышне-Ведено Веденского района ЧИАССР. Возможно 1970 г.р.
309. БИКАЕВ АДАМ КЮРАЕВИЧ*, 08.05.1978 г.р., с. Алхан-Кала ЧИАССР.
310. БИКТИМИРОВ РУСЛАН САЛАВАТОВИЧ*, 14.07.1975 г.р., д. Ялчикаево Кумертауского района Республики Башкортостан.
311. БИЛАЛОВ КАЗБЕК ИСАЕВИЧ*, 10.04.1982 г.р., с. Согунты Ножай-Юртовского района ЧИАССР.
312. БИЛЬТАЕВ ХАСАН ДУКВАЕВИЧ*, 27.05.1983 г.р., с. Валерик Ачхой-Мартановского района ЧИАССР.
313. БИНИНИ ДЖОН (САУДАНИ ЕСЕФ САИДОВИЧ)*, 01.09.1975 г.р., г. Лондон (Великобритания) (18.09.1969 г.р., г. Константин (Алжир)).
314. БИССАМИРОВ ШАМИЛЬ ВАХАЕВИЧ*, 03.12.1976 г.р., с. Кошкельды Гудермесского района ЧИАССР.
315. БИТАЕВ СУЛИМ РУСЛАНОВИЧ*, 10.02.1981 г.р., г. Грозный ЧИАССР.
316. БИТИЕВ АЛИХАН ШАМИЛЬЕВИЧ*, 13.12.1976 г.р., с. Черный Яр Черноярского района Астраханской области.
317. БИТИЕВ АСЛАН ШАМХАНОВИЧ*, 14.06.1969 г.р., с. Верхний Наур Надтеречного р-на Чеченской Республики.
318. БИТИЕВ ЗЕЛИМХАН ШАМИЛЬЕВИЧ*, 29.04.1979 г.р., пос. Большой Царын Октябрьского района Калмыкской АССР.
319. БИХАЕВ АНАРБЕК АХМЕДОВИЧ*, 16.09.1962 г.р., г. Аргун ЧИАССР.
320. БЛОХИН АЛЕКСАНДР ЮРЬЕВИЧ*, 06.12.1980 г.р., д. Горушки Яранского района Кировской области.
321. БОГАТЫРЕВ ИСА АБУЯЗИТОВИЧ*, 28.09.1991 г.р., г. Грозный ЧИАССР.
322. БОДРОВ МИХАИЛ АЛЕКСАНДРОВИЧ*, 27.03.1985 г.р., д. Верховая Рыбинского района Красноярского края.
323. БОЛТУКАЕВ МЕХДИН УМАРПАШАЕВИЧ*, 26.02.1990 г.р., с. Аллерой Ножай-Юртовского района ЧИАССР.
324. БОПАЕВ ШАМХАН ЮСАЕВИЧ*, 23.05.1980 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
325. БОРИСОВ АНДРЕЙ ИВАНОВИЧ*, 26.03.1968 г.р., Тюменская область.
326. БОСТАНОВ АСЛАН РУСЛАНОВИЧ*, 29.01.1980 г.р., г. Карачевск КЧАО.
327. БОСТАНОВ МАРАТ ИСЛАМОВИЧ*, 05.02.1964 г.р., с. Кызыл-Покун Малокарачаевского р-на КЧАО.
328. БОТАЕВ СУЛТАН ШАМСУДИНОВИЧ*, 23.04.1982 г.р., с. Чонтаул Кизилюртовского района Республики Дагестан (23.04.1982 г.р., г. Хасавюрт Республики Дагестан).
329. БУГАЕВ АЛЬБЕК САЛИЕВИЧ*, 06.02.1978 г.р., г. Урус-Мартан Урус-Мартановского района ЧИАССР.
330. БУГАЕВ КЮРИ ЛЕЧИЕВИЧ*, 16.08.1973 г.р., г. Гудермес ЧИАССР.
331. БУГАЕВ РАИДИН ЯМУДИНОВИЧ*, 29.05.1978 г.р., г. Махачкала Республики Дагестан.
332. БУЛАХ ВИТАЛИЙ ЕВГЕНЬЕВИЧ*, 20.07.1963 г.р., г. Армавир Краснодарского края.
333. БУРМАСОВ СЕРГЕЙ ПАВЛОВИЧ*, 10.06.1983 г.р., п. Санболи Амурского района Хабаровского края.
334. БУРЧАЛОВ КАМИЛЬ МАГОМЕДОВИЧ*, 16.08.1959 г.р., г. Бухара Узбекской ССР.
335. БУСЫРЕВ СЕРГЕЙ НИКОЛАЕВИЧ*, 30.09.1970 г.р., г. Ленинград.
336. БУШТУРОВ ТУРПАЛБЕК ШААЕВИЧ*, 15.03.1955 г.р., с. Бегень Баскарагайского района Павлодарской области.
337. БУШУЕВ ЗУРАБ НЕДИРСУЛТАНОВИЧ*, 18.09.1979 г.р., с. Ножай-Юрт Ножай-Юртовского района ЧИАССР.
338. ВАКУЕВ МАРАТ САЛАМБЕКОВИЧ*, 27.03.1976 г.р., г. Аргун ЧИАССР.
339. ВАЛИТОВ МАРС МАРАТОВИЧ*, 14.12.1967 г.р., г. Уфа Республики Башкортостан.
340. ВАЛИТОВ РАИЛЬ РАМИЛЕВИЧ*, 04.04.1981 г.р., г. Туймазы Республики Башкортостан.
341. ВАНГАШЕВ СУЛИМ МУСАЕВИЧ*, 10.12.1975 г.р., с. Катыр-Юрт Ачхой-Мартановского района ЧИАССР.
342. ВАРАЕВ МАЙРБЕК ВИЙСАЕВИЧ*, 01.07.1975 г.р., п. Яшкуль Яшкульского района Калмыцкой АССР.
343. ВАРЛАКОВ АЛЕКСАНДР АЛЕКСАНДРОВИЧ*, 21.04.1971 г.р., г. Свердловск.
344. ВАХАЕВ АРБИ ХУСЕЙНОВИЧ*, 11.11.1976 г.р., г. Грозный Чеченской Республики.
345. ВАХАЕВ МАГДАН ХОЗАЕВИЧ*, 11.06.1986 г.р., с. Урус-Мартан ЧИАССР.
346. ВАХАЕВ ТИМУР ДАДАШЕВИЧ*, 25.05.1976 г.р., г. Грозный Чеченской Республики.
347. ВАХИДОВ ВАХИД ШАМХАНОВИЧ*, 14.03.1976 г.р., с. Урус-Мартан Урус-Мартановского р-на ЧИАССР.
348. ВАЦАНАЕВ МУХАММЕД-ШЕРИП МАГОМЕДОВИЧ*, 19.07.1969 г.р., с. Дышне-Ведено Веденского района ЧИАССР.
349. ВАШАЕВ АБУБАКАР СУЛТАНОВИЧ*, 20.06.1965 г.р., с. Автуры Шалинского района ЧИАССР.
350. ВАШАЕВ ЗЕЛИМХАН СУЛТАНОВИЧ*, 10.10.1969 г.р., с. Автуры Шалинского района ЧИАССР.
351. ВЕДЕРНИКОВ ВЛАДИМИР АЛЕКСАНДРОВИЧ*, 30.01.1984 г.р., Чистопольского района Республики Татарстан.
352. ВЕЗЕРХАНОВ АСЛАНБЕК ВАХИДОВИЧ*, 25.08.1978 г.р., с. Кургалой Шалинского района ЧИАССР.
353. ВИДАЕВ ХИЗАР ЛОМЭЛЬЕВИЧ*, 18.11.1987 г.р., с. Урус-Мартан ЧИАССР.
354. ВИСАЕВ АПТИ УВАЙСОВИЧ*, 01.05.1985 г.р., г. Грозный ЧИАССР.
355. ВИСАИТОВ АДАМ АЛИЕВИЧ*, 30.01.1957 г.р., с. Джусалы Кармакчинского района Кзыл-Ординской области Казахской ССР.
356. ВИСАИТОВ АСЛАН МОВЛДИЕВИЧ*, 27.02.1974 г.р., с. Серноводск Сунженского района ЧИАССР.
357. ВИСИХАНОВ РУСЛАН ЗИНАУДИНОВИЧ*, 04.12.1979 г.р., с. Елтай Индерского района Гурьевской области Казахской ССР.
358. ВИСЛОГУЗОВ ДМИТРИЙ СЕРГЕЕВИЧ*, 20.09.1980 г.р., г. Бийск Алтайского края.
359. ВИТУШЕВ УМАР ЗАЙНАЛОВИЧ*, 17.10.1977 г.р., с. Новый Шарой Ачхой-Мартановского района ЧИАССР.
360. ВИЧИГОВ РУСТАМ РУСЛАНОВИЧ*, 14.12.1982 г.р., с. Ачхой-Мартан ЧИАССР.
361. ВИШНЯКОВ АРТУР ВЛАДИМИРОВИЧ*, 30.10.1987 г.р., п. Шексна Вологодской области.
362. ВЛАДОВСКИЙ МИХАИЛ АЛЕКСАНДРОВИЧ*, 23.03.1983 г.р., г. Грозный Чеченской Республики.
363. ВЛАСОВ ВЛАДИМИР СЕРГЕЕВИЧ*, 29.07.1956 г.р., г. Москва.
364. ВОРОНОВ ДМИТРИЙ ВИКТОРОВИЧ*, 26.09.1969 г.р., г. Грозный Чеченская Республика.
365. ВЫШЕГУРОВ МАГОМЕД УМАРОВИЧ*, 04.08.1972 г.р., г. Орджоникидзе СОАССР.
366. ГАБАЕВ ИСЛАМ РУСЛАНОВИЧ*, 19.01.1989 г.р., с. Ведено Веденского района ЧИАССР.
367. ГАБДРАХМАНОВ РИНАТ РИФОВИЧ*, 24.12.1968 г.р., г. Уфа Республики Башкортостан.
368. ГАБДУЛХАКОВ ДАНИЛ ЛЯБИБОВИЧ*, 18.05.1982 г.р., г. Усинск Республики Коми.
369. ГАДАЕВ АНЗОР АБДУЛБЕКОВИЧ*, 04.10.1983 г.р., с. Мескер-Юрт Шалинского района ЧИАССР.
370. ГАДАЕВ МАГОМЕД КАЗБЕКОВИЧ*, 06.11.1984 г.р., с. Закан-Юрт Ачхой-Мартановского района ЧИАССР.
371. ГАДАМУРОВ АЛИХАН АДАМОВИЧ*, 21.08.1985 г.р., с. Косиновка Обоянского района Курской области.
372. ГАДЖИАКАЕВ МАГОМАДЗАГИР УМАКАЕВИЧ*, 07.01.1975 г.р., с. Доргели Карабудахкентского района ДАССР.
373. ГАДЖИБАГОМЕДОВ МУСА ГАДЖИБАГОМЕДОВИЧ*, 28.02.1972 г.р., с. Карамахи Буйнакского района ДАССР.
374. ГАДЖИЕВ МАГОМЕД АБДУСАЛИМОВИЧ*, 18.10.1968 г.р., г. Избербаше ДАССР.
375. ГАДЖИЕВ ХАБИБ САИДБЕГОВИЧ*, 10.12.1966 г.р., с. Хвайни-Кунда Цумадинского района Республики Дагестан.
376. ГАЗИЕВ БИСЛАН ХАРОНОВИЧ*, 17.08.1977 г.р., с. Катыр-Юрт Ачхой-Мартановского района ЧИАССР.
377. ГАЗИЕВ ЗАУРБЕК МАСХУДОВИЧ*, 15.04.1981 г.р., с. Пролетарское Грозненского района ЧИАССР.
378. ГАЗИЕВ КАЗБЕК РАМЗАНОВИЧ*, 24.12.1972 г.р., с. Дышне-Ведено Веденского района ЧИАССР.
379. ГАЗИЗОВ ИЛЬЯС АХМЕТХАФИЗОВИЧ*, 16.03.1960 г.р., п. Лесхоз Сабинского района Республики Татарстан.
380. ГАИРБЕКОВ ГАЗИМАГОМЕД ГАИРБЕКОВИЧ*, 26.07.1977 г.р., с. Кванада Цумадинского района Республики Дагестан.
381. ГАИРБЕКОВ МАГОМЕД ГАИРБЕКОВИЧ*, 06.02.1976 г.р., с. Кванада Цумадинского района Республики Дагестан.
382. ГАЙГЕРАЕВ УМАР МАГОМЕДОВИЧ*, 08.01.1983 г.р., с. Ачхой-Мартан ЧИАССР.
383. ГАЙТАМИРОВ АДАМ АЛИЕВИЧ*, 19.08.1976 г.р., с. Шаро-Аргун Шатойского района Чеченской Республики.
384. ГАЙТУКАЕВ ДЖАМАЛАЙ ИСАЕВИЧ*, 03.02.1979 г.р., с. Ленинское Ерментауского р-на Целиноградской обл. КазССР.
385. ГАЙХАНОВ МУСА МИНКАИЛОВИЧ*, 26.03.1953 г.р., п. Кадамжай Фрунзенского района Ошской области КиргССР.
386. ГАКАЕВ МАГОМЕД-ХУСЕЙН УМАРОВИЧ*, 18.05.1977 г.р., г. Грозный ЧИАССР.
387. ГАКАЕВ РОМАН ДЖАНДАРОВИЧ*, 01.10.1978 г.р., ст. Червленая Шелковского района ЧИАССР.
388. ГАМАДАЕВ ГАМЗАТ ЗАЛИМХАНОВИЧ*, 12.08.1980 г.р., с. Новолакское Новолакского района Республики Дагестан.
389. ГАМАДАЕВ ГИЛАНИ ЗАЛИМХАНОВИЧ*, 19.12.1978 г.р., с. Новолакское Новолакского района Республики Дагестан.
390. ГАМАДАЕВ ЗАЛИМХАН МАГОМЕДОВИЧ*, 20.08.1936 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
391. ГАМАЕВ АСЛАНБЕК ОСМАНОВИЧ*, 30.01.1978 г.р., с. Новые-Атаги ЧИАССР.
392. ГАМАЕВ ИСА МАЙРБЕКОВИЧ*, 04.11.1978 г.р., с. Ушкалой ЧИАССР.
393. ГАМИДОВ МАГОМЕДРАСУЛ МЕДЖИДОВИЧ*, 01.03.1952 г.р., с. Карамахи Буйнакского района ДАССР.
394. ГАНАЕВ ИСРАПИЛ АДАМОВИЧ*, 30.01.1987 г.р., с. Мескер-Юрт Шалинского района ЧИАССР.
395. ГАНАТОВ ХАМЗАТ ДАУДОВИЧ*, 17.09.1967 г.р., с. Ведучи Советского района ЧИАССР.
396. ГАНИЕВ РУСТАМ СУЛУМБЕКОВИЧ*, 01.12.1979 г.р., с. Чемульга Сунженского района ЧИАССР.
397. ГАНИШИВ АБДУЛГАНИ ЮСУПОВИЧ*, 05.01.1988 г.р., г. Грозный Чеченской Республики.
398. ГАПАРХОЕВ ИССА МАКШАРИПОВИЧ*, 28.09.1974 г.р., ст. Орджоникидзевская Сунженского района ЧИАССР.
399. ГАПАРХОЕВ МАЙРБЕК МАГОМЕДОВИЧ*, 12.08.1984 г.р., г. Назрань ЧИАССР.
400. ГАПОНОВ МАКСИМ АЛЕКСАНДРОВИЧ*, 06.06.1973 г.р., г. Ташкент Республики Узбекистан.
401. ГАСТЕМИРОВ РОМАН МАГОМЕДОВИЧ*, 10.03.1979 г.р., г. Грозный ЧИАССР.
402. ГАСТИЕВ ИСЛАМ ИБРАГИМОВИЧ*, 03.02.1984 г.р., с. Ведено Веденского района ЧИАССР.
403. ГАТИЕВ НАРИМАН ХИЗИРИЕВИЧ*, 07.01.1967 г.р., с. Османюрт Хасавюртовского района ДАССР.
404. ГАЦАЕВ РАМЗАН САЙД-БЕКОВИЧ*, 15.07.1989 г.р., с. Захино Пушко-Горского района Псковской области.
405. ГАЯНОВ БУЛАТ МАРСОВИЧ*, 24.07.1972 г.р., г. Туймазы Республики Башкортостан.
406. ГАЯНОВ САЛАВАТ МАРСОВИЧ*, 15.08.1976 г.р., г. Туймазы Республики Башкортостан.
407. ГЕЗИХАДЖИЕВ ХАМЗАТ МАХЧАЕВИЧ*, 18.07.1969 г.р., с. Мескеты Ножай-Юртовского района ЧИАССР.
408. ГЕРИМСУЛТАНОВ АСЛАН БЕДИЕВИЧ*, 02.11.1975 г.р., ст. Гребенская Шелковского района ЧИАССР.
409. ГЕРИХАНОВ МУСЛИМ МУСАЕВИЧ*, 27.09.1974 г.р., г. Аргун ЧИАССР.
410. ГИГИЕВ ЛЕЧИ БАУДИНОВИЧ*, 08.06.1954 г.р., г. Текели Талды-Курганской области Казахской ССР.
411. ГИМРАНОВ РУСТАМ РАВИЛОВИЧ*, 04.05.1987 г.р., р.п. Нижняя Мактама Альметьевского района ТАССР.
412. ГИНАЕВ АСЛАМБЕК ЖУНАЙДОВИЧ*, 31.12.1976 г.р., ст. Калиновская Наурского района ЧИАССР.
413. ГИНАЕВ ТИМУР МУРАТОВИЧ*, 20.05.1984 г.р., с. Ведено Веденского района ЧИАССР.
414. ГЛЕБОВ КОНСТАНТИН ВИКТОРОВИЧ*, 26.04.1979 г.р., г. Владивосток.
415. ГОЙДЕНКО РУСЛАН АЛЕКСАНДРОВИЧ*, 04.09.1977 г.
416. ГОЙЛАБИЕВ САЛВАДИ НУРАДИЕВИЧ*, 29.03.1987 г.р., с. Байтарки Ножай-Юртовского района ЧИАССР.
417. ГОЛОВНЕВ ЕВГЕНИЙ НИКОЛАЕВИЧ*, 14.05.1989 г.р., г. Красноярск.
418. ГОЛОДОК СЕРГЕЙ АЛЕКСАНДРОВИЧ*, 02.04.1962 г.р., д. Гальки Крупского р-на Минской обл. Республики Беларусь.
419. ГОРЧАКОВ ВАДИМ МИХАЙЛОВИЧ*, 27.06.1985 г.р., г. Одинцово Московской обл.
420. ГОЧИЯЕВ РАМАЗАН ХАНАФИЕВИЧ*, 08.12.1965 г.р., ст. Сторожевая Зеленчукского района Карачаево-Черкесской Республики.
421. ГРИЦКЕВИЧ НИКОЛАЙ ПАВЛОВИЧ*, 20.12.1959 г.р., г. Лунинец Брестской области.
422. ГУБАРЕВ ПАВЕЛ АЛЕКСЕЕВИЧ*, 19.02.1987 г.р., г. Омск.
423. ГУБКИН ИГОРЬ ВЛАДИМИРОВИЧ*, 25.01.1964 г.р., г. Благовещенск Амурской области.
424. ГУДАЕВ АЛИХАН ИМРАНОВИЧ*, 01.03.1981 г.р., с. Советское Приозерного р-на Калмыцкой АССР.
425. ГУДКОВ АЛЕКСЕЙ ГЕНАДЬЕВИЧ*, 05.01.1978 г.р., пос. Могойтуй Агинско-Бурятского АО Читинской области.
426. ГУМАРОВ РАВИЛЬ ШАФИЕВИЧ*, 22.11.1962 г.р., г. Кушва Свердловской области.
427. ГУМЕРОВ ИЛЬГАМ ШАКИРОВИЧ*, 16.03.1966 г.р., д. Чувашский Брод Алькеевского р-н Республики Татарстан.
428. ГУПОЛОВИЧ АЛЕКСАНДР ИВАНОВИЧ*, 17.02.1966 г.р., г. Донецк Ростовской области.
429. ГУЦИЕВ РИЗВАН МАГДАНОВИЧ*, 11.09.1966 г.р., с. Серноводск Сунженского района ЧИАССР.
430. ГУЧИГОВ РУСТАМ ВАХАЕВИЧ*, 03.11.1977 г.р., г. Урус-Мартан Урус-Мартановского района ЧИАССР.
431. ДАДАЕВ АМАЙ ДАУТОВИЧ*, 30.01.1989 г.р., ст. Наурская Наурского района ЧИАССР.
432. ДАДАЕВ ИЛЬМАН ИМРАНОВИЧ*, 26.02.1984 г.р., с. Ачхой-Мартан ЧИАССР.
433. ДАДАЕВ ЛЕЧА СУЛТАНОВИЧ*, 21.02.1982 г.р., г. Грозный ЧИАССР.
434. ДАДАЕВ МУСА УСМАНОВИЧ*, 20.09.1981 г.р., с. Надтеречное Надтеречного р-на ЧИАССР.
435. ДАДАЕВ РАСУЛ АРБИЕВИЧ*, 16.05.1985 г.р., с. Березовка Нелидовского района Калининской области.
436. ДАДАЕВ РУСЛАН МАГОМЕДОВИЧ*, 30.10.1969 г.р., с. Алхазурово Урус-Мартановского района ЧИАССР.
437. ДАДАЕВ ХАЗИР ЛЕЧИЕВИЧ*, 01.07.1968 г.р., с. Шали Шалинского р-на ЧИАССР.
438. ДАДАШЕВА АСЕТ МОВЛАГАДИНОВНА*, 03.04.1963 г.р., с. Дачу-Борзой Грозненского р-на ЧИАССР.
439. ДАЕВ АХЪЯД АСХАБОВИЧ*, 04.08.1982 г.р., г. Урус-Мартан ЧИАССР.
440. ДАЙДАЕВ ДЖАМИЛЬ ШАМСОЛТОВИЧ*, 27.07.1982 г.р., с. Урус-Мартан ЧИАССР.
441. ДАЙЗИЕВ МАГОМЕДШАПИ ЮСУПОВИЧ*, 24.05.1959 г.р., с. Карамахи Буйнарского района ДАССР.
442. ДАКАЕВ АХМЕД ИЗРАИЛОВИЧ*, 22.07.1980 г.р., с. Энгель-Юрт Гудермесского района ЧИАССР.
443. ДАКАЕВ СУЛЕЙМАН СЕБЕРОВИЧ*, 18.08.1976 г.р., с. Ленинское Наурского района ЧИАССР.
444. ДАКАЕВ ЮСУП АХЯТОВИЧ*, 20.02.1990 г.р., с. Ремонтное Ростовской области.
445. ДАКАШЕВ РУСТАМ УЗГЕНБАЕВИЧ*, 01.11.1980 г.р., г. Аргун ЧИАССР.
446. ДАЛЬЦАЕВ МУСА ТАТИЕВИЧ*, 02.04.1958 г.р., с. Новотерское Наурского р-на ЧИАССР.
447. ДАМАЕВ РУСТАМ РИЗВАНОВИЧ*, 28.02.1984 г.р., с. Урус-Мартан ЧИАССР.
448. ДАМХАЕВ УСАМА МУСАЕВИЧ*, 25.12.1977 г.р., с. Ведено Веденского района ЧИАССР.
449. ДАНАШЕВ РАМЗАН АБУЯЗИТОВИЧ*, 08.10.1971 г.р., с. Ведено Введенского района ЧИАССР.
450. ДАНДАЕВ АРБИ ХАМЗАТОВИЧ*, 01.02.1974 г.р., г. Грозный ЧИАССР.
451. ДАНДАЕВ ИСА МУМАДИЕВИЧ*, 17.04.1973 г.р., с. Дуба-Юрт ЧИАССР.
452. ДАНДАЕВ МАГОМЕД АДЛАНОВИЧ*, 22.05.1980 г.р., г. Урус-Мартан ЧИАССР.
453. ДАРАЕВ РАМЗАН ДАЛХАДОВИЧ*, 08.01.1963 г.р., с. Герменчук Шалинского района ЧИАССР.
454. ДАСАЕВ ТИМУР МОВЛИДОВИЧ*, 07.12.1979 г.р., с. Ачхой-Мартан ЧИАССР. Возможно 1974 г.р.
455. ДАТАГАЕВ АЛИ ХУСАИНОВИЧ*, 17.06.1980 г.р., с. Курчалой Шалинского района ЧИАССР.
456. ДАУДОВ АХМЕД ХОЖБАУДЫЕВИЧ*, 09.11.1979 г.р., с. Курчалой Шалинского района ЧИАССР.
457. ДАУДОВ МАХМУД АЛАУДИЕВИЧ*, 24.06.1984 г.р., г. Грозный ЧИАССР.
458. ДАУДОВ РУСЛАН САИДСАЛАХАНОВИЧ*, 24.12.1970 г.р., с. Дуба-Юрт Шалинского района ЧИАССР.
459. ДАУДОВ САЛАМБЕК СУЛТАНОВИЧ*, 19.02.1974 г.р., с. Шали Шалинского района ЧИАССР.
460. ДАУРБЕКОВ МАГОМЕД САЛИМХАНОВИЧ*, 04.10.1980 г.р., г. Назрань ЧИАССР.
461. ДАУТМЕРЗАЕВ РИЗВАН АХМАЕВИЧ*, 29.10.1980 г.р., г. Гудермес ЧИАССР.
462. ДАХАЕВ ВАХИТ ШЕРИПУЕВИЧ*, 22.06.1978 г.р., с. Автуры Шалинского района ЧИАССР.
463. ДАЦИЕВ БЕСЛАН ИСАЕВИЧ*, 07.06.1982 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
464. ДАШАЕВ КАИМ ШАМСУДИЕВИЧ*, 08.01.1982 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
465. ДАШАЕВ ТАГИР ШАМСУДИЕВИЧ*, 14.04.1984 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
466. ДАШТАЕВ ИДРИС ИБРАГИМОВИЧ*, 03.05.1977 г.р., нас. пункт Новые Атаги Шалинского района ЧИАССР.
467. ДАШУКАЕВ ВАХИД ВАХАЕВИЧ*, 28.04.1974 г.р., г. Грозный ЧИАССР.
468. ДЕБИРОВ ИСМАИЛ ХУМАИДОВИЧ*, 27.04.1971 г.р., г. Хасавюрт ДАССР.
469. ДЕДИЕВ АСЛАН СЕЛИМОВИЧ*, 10.03.1974 г.р., с. Пролетарское Грозненского района ЧИАССР.
470. ДЕККУШЕВ АДАМ ОСМАНОВИЧ*, 03.02.1962 г.р., г. Карачаевск Карачаево-Черкесской автономной области Ставропольского края.
471. ДЕМЕЛЬХАНОВ АХМЕД РУСЛАНОВИЧ*, 10.10.1983 г.р., г. Грозный ЧИАССР.
472. ДЕМЕЛЬХАНОВ РАУФ ВЯЧЕСЛАВОВИЧ*, 29.06.1985 г.р., г. Грозный ЧИАССР.
473. ДЕНИЕВ РАМЗАН СУЛТАНОВИЧ*, 06.11.1972 г.р., с. Эрсеной Веденского района ЧИАССР.
474. ДЕНИСУЛТАНОВ ЗАУРБЕК ИСМАИЛОВИЧ*, 04.11.1977 г.р., село Плодовитое Малодербетовского района Республики Калмыкия.
475. ДЕРБИШЕВ АЮБ АХМЕДОВИЧ*, 10.12.1983 г.р., с. Кулары Грозненского района ЧИАССР.
476. ДЕЦИЕВ МАУЛАТ МАСУДОВИЧ*, 03.05.1987 г.р., г. Чимкент КазССР.
477. ДЖАБАЕВ РАМЗАН ШАХРУДИНОВИЧ*, 16.04.1958 г.р., с. Алхан Ножай-Юртовского района ЧИАССР.
478. ДЖАБАЕВ САИД-МАГОМЕД АЛИЕВИЧ*, 21.05.1975 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
479. ДЖАБАРОВ ХАМЗАТ ХАМИДОВИЧ*, 18.06.1977 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
480. ДЖАБРАИЛОВ АДАМ МАГОМЕДОВИЧ*, 01.01.1979 г.р., н.п. Курчалой ЧИАССР.
481. ДЖАБРАИЛОВ АЛИК ЛЕШАЕВИЧ*, 10.08.1976 г.р., г. Грозный ЧИАССР.
482. ДЖАБРАИЛОВ АНВАР ПОХАРУДИНОВИЧ*, 10.12.1981 г.р., с. Замай-Юрт Ножай-Юртовского района ЧИАССР.
483. ДЖАБРАИЛОВ ЗЕЛИМХАН МУХОДИНОВИЧ*, 07.09.1978 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
484. ДЖАБРАИЛОВ ИСЛАМ ОБУ-АЛИЕВИЧ*, 19.12.1989 г.р., с. Ведено Веденского района ЧИАССР.
485. ДЖАБРАИЛОВ ЛЕМИ БЕТИЕВИЧ*, 03.09.1967 г.р., с. Джагларги Ножай-Юртовского района ЧИАССР.
486. ДЖАБРАИЛОВ МАГОМЕДГАДЖИ НУРМАГОМЕДОВИЧ*, 04.05.1976 г.р., с. Сильди Цумадинского района ДАССР.
487. ДЖАБРАИЛОВ РАМЗАН ХУМИДОВИЧ*, 10.02.1979 г.р., г. Шали ЧИАССР.
488. ДЖАБРАИЛОВ УСМАН ЗЕЛИМХАНОВИЧ*, 07.04.1986 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
489. ДЖАБРАИЛОВА ТУИТА АБУКОСУМОВНА*, 24.07.1967 г.р., с. Элистанжи Введенского района ЧИАССР.
490. ДЖАЛМАШВИЛИ АРСЕН ЮРЬЕВИЧ*, 03.06.1986 г.р., п. Николаевский Тарбагатаевского района Бурятской АССР.
491. ДЖАМУЛАЕВ ТАМЕРЛАН АХМЕДОВИЧ*, 07.06.1982 г.р., г. Гудермес ЧИАССР.
492. ДЖАНТЕМИРОВ ДОККА СУЛУМБЕКОВИЧ*, 27.05.1974 г.р., г. Грозный ЧИАССР.
493. ДЖАНТУЕВ ТАХИР ХУСЕЙНОВИЧ*, 27.12.1979 г.р., г. Тырнауз Кабардино-Балкарской Республики.
494. ДЖАНХОВАТОВ МАГОМЕД БАДРУДИНОВИЧ*, 10.08.1956 г.р., с. Кадар Буйнакского района Республики Дагестан.
495. ДЖАНХОТОВ АЛВИ АХМАДГИРЕЕВИЧ*, 25.05.1960 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
496. ДЖАНХОТОВ САЛЕХ УСМАНОВИЧ*, 15.02.1985 г.р., с. Кулары Грозненского района ЧИАССР.
497. ДЖАСУЕВ ИМРАН ИДРИСОВИЧ*, 20.12.1985 г.р., г. Грозный ЧИАССР.
498. ДЖАУТХАНОВ СУЛТАН САЛАМОВИЧ*, 27.09.1976 г.р., п. Ойсхара Гудермесского района ЧИАССР.
499. ДЖАЦАЕВ ТУРПАЛ ХАМИДОВИЧ*, 04.12.1966 г.р., с. Курчалой Шалинского района ЧИАССР.
500. ДЖАШЕЕВ ДЖАТДАЙ БАТДАЛОВИЧ (ДЖАШЕЕВ ДЖАТДАЙ БОРИСОВИЧ)*, 21.03.1969 г.р., а. Эльтаркач Усть-Джегутинского района Ставропольского края КЧАО.
501. ДЖВАРИДЗЕ ДАВИД ЛАВРЕНТЬЕВИЧ*, 12.04.1974 г.р., г. Вале Республики Грузия.
502. ДЖИГУЕВ АМХАД МОГИТОВИЧ*, 19.10.1986 г.р., с. Ушкалой Советского района ЧИАССР.
503. ДЖУМАГИШИЕВ АБДУЛЛЯЛИМ АХМАТОВИЧ*, 10.06.1981 г.р., с. Сары-Су Шелковского района ЧИАССР.
504. ДЖУРАЕВ АЛИШЕР МАМАРАСУЛОВИЧ*, 19.06.1978 г.р., пос. им. Исаева Колхозабадского района Халтонской области Республики Таджикистан.
505. ДЖУРАЕВ УМЕДЖОН МИРЗОАХМАДОВИЧ*, 14.10.1980 г.р., г. Худжант Республики Таджикистан.
506. ДЗАНГИЕВ МУСА БОРИСОВИЧ*, 12.09.1972 г.р., с. Алхасты Сунженского района Республики Ингушетия.
507. ДЗЕЙТОВ АДАМ РУКМАНОВИЧ*, 21.12.1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
508. ДЗЕЙТОВ АДЛАН РУКМАНОВИЧ*, 17.08.1978 г.р., х. Веселый Ачхой-Мартановского района Чеченской Республики.
509. ДЗЕЙТОВ САЛМАН РУХМАНОВИЧ*, 08.01.1980 г.р., хутор Веселый Ачхой-Мартановского ЧИАССР.
510. ДЗУБАЙРАЕВ АЛИ ЛЕЧИЕВИЧ*, 29.03.1989 г.р., с. Элистанжи Веденского района ЧИАССР.
511. ДИБИРОВ ДЖАФАР АБДУЛЛАЕВИЧ*, 25.06.1972 г.р., с. Терекли-Мектеб Ногайского р-на Республики Дагестан.
512. ДИКИЕВ СИДИК ГИЛАНИЕВИЧ*, 09.11.1974 г.р., с. Д-Ведено ЧИАССР.
513. ДИНАЕВ ВАХИ АБУБАКАРОВИЧ*, 01.09.1975 г.р., с. Дышне-Ведено Веденского района Чеченской Республики.
514. ДОВЛЕТБИЕВ ИДРИС МОВСАРОВИЧ*, 30.12.1984 г.р., с. Чири-Юрт ЧИАССР.
515. ДОЛГИХ АНАТОЛИЙ ВЛАДИМИРОВИЧ*, 11.03.1976 г.р., с. Бегишево Вагайского р-на Тюменской области.
516. ДОМБАЕВ АСЛАН РУСЛАНОВИЧ*, 07.03.1977 г.р., с. Толстой-Юрт Грозненского района ЧИАССР.
517. ДОТМЕРЗОЕВ МАЙРБЕК ВЛАДИМИРОВИЧ*, 18.11.1986 г.р., ст. Троицкая Сунженского района ЧИАССР.
518. ДРОБОТОВ АЛЕКСЕЙ ВАСИЛЬЕВИЧ*, 16.07.1960 г.р., г. Миллерово Ростовской области.
519. ДРОЗДОВСКАЯ АННА ЮРЬЕВНА*, 27.01.1984 г.р., г. Ярославль.
520. ДУБАЕВ АНЗОР РУСЛАНОВИЧ*, 13.08.1986 г.р., г. Грозный ЧИАССР.
521. ДУБАЕВ БЕСЛАН РИЗВАНОВИЧ*, 23.01.1987 г.р., с. Урус-Мартан ЧИАССР.
522. ДУДАЕВ ХУСЕЙН ЭЛИДОВИЧ*, 20.03.1976 г.р., г. Грозный Чеченской Республики.
523. ДУДУЕВ КАЧАК БИЛАЛОВИЧ*, 29.09.1954 г.р., с. Советское Базаркурголинского района Республики Киргизия.
524. ДУДУЕВА МАРЕТА САЛАВДИНОВНА*, 26.03.1984 г.р., ст. Шелковская Шелковского района Чеченской Республики.
525. ДУДУШЕВ ИБРАГИМ ВАХАХАЖИЕВИЧ*, 15.05.1966 г.р., с. Дышне-Ведено Веденского района Чеченской Республики.
526. ДУЖИЕВ АРСЛАН САДАХМЕДОВИЧ*, 09.06.1973 г.р., с. Ножай-Юрт Ножай-Юртовского района Чеченской Республики.
527. ДУКАЕВ АХМЕД ШАРАНИЕВИЧ*, 25.07.1983 г.р., с. Шали ЧИАССР.
528. ДУКАЕВ ИСА АЛХАЗУРОВИЧ*, 09.04.1968 г.р., с. Кади-Юрт Гудермесского района Чеченской Республики.
529. ДУКУЕВ ИСА СУЛТАНОВИЧ*, 21.01.1986 г.р., г. Гудермес ЧИАССР.
530. ДУКУШОВ АБУ-УМАР УСАМОВИЧ*, 30.05.1983 г.р., с. Урд-Юхой Советского района ЧИАССР.
531. ДУЛАЕВ АХМЕД САИД-ХЕСЕЙНОВИЧ*, 12.11.1980 г.р., с. Памятой Шатойского района ЧИАССР.
532. ДУЛАЕВ МАГОМЕД ВАХАЕВИЧ*, 20.10.1983 г.р., г. Аргун ЧИАССР.
533. ДУЛАТОВ ШАМИЛЬ САЛАУДИНОВИЧ*, 25.05.1980 г.р., с. Большая Мартыновка Мартыновского района Ростовской области.
534. ДУНДАЕВА РАЙСА ДОККАЕВНА*, 11.06.1973 г.р., г. Грозный Чеченской Республики.
535. ДУРАЕВ АСЛАНБЕК ЛЕМАЕВИЧ*, 06.08.1969 г.р., г. Грозный ЧИАССР.
536. ДУРИЕВ АЛИ АБДУЛХАМИДОВИЧ*, 13.05.1977 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
537. ДЫШНИЕВ МАГОМЕД ХУСЕЙНОВИЧ*, 04.02.1982 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
538. ДЬЯЧКОВ АЛЕКСАНДР СЕРГЕЕВИЧ*, 05.10.1980 г.р., п. Октябрьский Устьянского района Архангельской области.
539. ЕДАЕВ ИБРАГИМ РУСЛАНОВИЧ*, 11.11.1983 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
540. ЕДАЕВ РУСЛАН МАГОМЕДОВИЧ*, 07.02.1982 г.р., г. Грозный ЧИАССР.
541. ЕДИСУЛТАНОВ АСЛАН ВАХАЕВИЧ*, 13.11.1975 г.р., с. Белгатой Шалинского района ЧИАССР.
542. ЕПИФАНОВ ПАВЕЛ НИКОЛАЕВИЧ*, 24.08.1976 г.р., г. Грозный ЧИАССР.
543. ЕПРИНЦЕВ НИКОЛАЙ БОРИСОВИЧ*, 08.07.1978 г.р., ст. Исправная Зеленчукского р-на Карачаево-Черкесской Республики.
544. ЕСИН АРТЕМ СЕРГЕЕВИЧ*, 08.03.1981 г.р., г. Чистополь Татарской АССР.
545. ЕФРЕМОВ АНДРЕЙ АНАТОЛЬЕВИЧ*, 15.07.1971 г.р., г. Витебск Республики Беларусь.
546. ЕШУРКАЕВ МУСЛИМ НУРДЫЕВИЧ*, 28.03.1989 г.р., с. Побединское Грозненского района ЧИАССР.
547. ЖАБРАИЛОВ АСЛАН РОМАНОВИЧ*, 15.02.1983 г.р., с. Караванное Лиманского района Астраханской области.
548. ЖАБРАИЛОВ ХИЗИР АЛИЕВИЧ*, 08.05.1980 г.р., с. Аллерой Шалинского района ЧИАССР.
549. ЖАМАЛДАЕВ ЗАУРБЕК АЛХАЗУРОВИЧ*, 01.06.1985 г.р., с. Серноводск Сунженского района ЧИАССР.
550. ЖАНТУЕВ МАГОМЕД ЖАМАЛОВИЧ*, 25.08.1974 г.р., г. Нальчик Кабардино-Балкарской Республики.
551. ЖАПКАЕВ ШАРКАН ИСАЕВИЧ*, 19.12.1974 г.р., с. Хаттуни Веденского района ЧИАССР.
552. ЖАРКОВ СЕРГЕЙ ВЛАДИМИРОВИЧ*, 12.06.1985 г.р., г. Череповец Вологодской области.
553. ЖЕБРАИЛОВ ИБРАГИМ ШУДДИЕВИЧ*, 19.09.1984 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
554. ЖИДАЕВ САЛАМБЕК ИСАНОВИЧ*, 29.10.1982 г.р., с. Ширди-Мохк Веденского района ЧИАССР.
555. ЖИЛИНСКИЙ КИРИЛЛ ВЛАДИМИРОВИЧ*, 26.06.1982 г.р., г. Луга Ленинградской области.
556. ЖУКОВЦОВ ВАЛЕРИЙ ВИТАЛЬЕВИЧ*, 10.04.1988 г.р., г. Москва.
557. ЗАВЛИЕВ КАЗБЕК ГАРСОЛТОВИЧ*, 25.09.1984 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
558. ЗАГАЛАЕВ МОВСАР АНАСОВИЧ*, 23.12.1966 г.р., с. Дарго Веденского района ЧИАССР.
559. ЗАГРЕТДИНОВ МАРАТ АЛЬБЕРТОВИЧ*, 03.06.1985 г.р., г. Азнакаево Республики Татарстан.
560. ЗАИТОВ ВИСАНИ НУРИТОВИЧ*, 02.08.1970 г.р., п. Горагорск Надтеречного района Чеченской Республики.
561. ЗАЙНАГУТДИНОВ РУСТЕМ РАФИКОВИЧ*, 20.10.1971 г.р., г. Салават Республики Башкортостан.
562. ЗАЙНАЛОВ АПТИ РАМЗАНОВИЧ*, 30.06.1980 г.р., с. Ведено ЧИАССР.
563. ЗАЙНУДИНОВ ИСА ИСАЕВИЧ*, 27.12.1938 г.р., с. Кудали Гунибского района ДАССР.
564. ЗАЙЦЕВ АЛЕКСЕЙ ВЛАДИМИРОВИЧ*, 17.11.1971 г.р., г. Томск.
565. ЗАКАЕВ ИБРАГИМ ХУСАЙНОВИЧ*, 25.11.1973 г.р., ст. Галюгаевская Курского района Ставропольского края.
566. ЗАКИРОВ ИЛЬШАТ ШАУКАТОВИЧ*, 22.06.1962 г.р., с. Олуяз Мамадышского района Республики Татарстан.
567. ЗАКРАИЛОВ РУСТАМ ХОЖАХМЕДОВИЧ*, 25.07.1980 г.р., с. Старые Атаги Грозненского района ЧИАССР.
568. ЗАКРИЕВ АРБИ САИДАЛИЕВИЧ*, 21.09.1979 г.р., ст. Николавская Наурского р-на Чеченской Республики.
569. ЗАКРИЕВ НУРДЫ ЯРАГИЕВИЧ*, 15.05.1952 г.р., Каратальский район Алма-Атинской области КССР.
570. ЗАКРИЕВ РАСУЛ АБДУЛВАДУДОВИЧ*, 02.04.1974 г.р., г. Хасавюрт Дагестанской АССР.
571. ЗАКРИЕВ СУЛТАН ШАЙАХМАТОВИЧ*, 19.11.1986 г.р., с. Нурадилово Хасавюртовского района ДАССР.
572. ЗАМТИЕВ ЛЕМА ШАМИЛЬЕВИЧ*, 02.10.1985 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
573. ЗАРИПОВ РАДИК РАМИЛОВИЧ*, 08.10.1985 г.р., с. Большие Кибячи Сабинского района ТАССР.
574. ЗАХАРКИН ВЛАДИМИР ВАЛЕРЬЕВИЧ*, 18.02.1975 г.р., ст. Червленая Шелковского района Чеченской Республики.
575. ЗЕЛЕМХАНОВ ИБРАГИМ МАГАМЕДОВИЧ*, 27.09.1989 г.р., г. Грозный ЧИАССР.
576. ЗЕУШЕВ ЭДУАРД ИСМАИЛОВИЧ*, 02.09.1977 г.р., г. Тырныауз КБР.
577. ЗИЗАЕВ АПТИ АБДУРАХМАНОВИЧ*, 06.05.1981 г.р., г. Урус-Мартан ЧИАССР.
578. ЗИННУРОВ РАУФ РАШИТОВИЧ*, 09.02.1978 г.р., с. Возжаевка Белогородского района Амурской области.
579. ЗИЯВУДИНОВ ЗИЯВУДИН КУРБАНОВИЧ*, 02.05.1977 г.р., с. Кикуни Гергебельского района Республики Дагестан.
580. ЗУБАЙРАЕВ САЙД-АХМЕД САЙДЕМИЕВИЧ*, 24.10.1979 г.р., с. Побединское Грозненского р-на Чеченской Республики.
581. ЗУЛКАРНАЕВ МУСЛИМ ЗАЙНДИЕВИЧ*, 18.07.1977 г.р., с. Муцалаул Хасавюртовского района РеспубликиДагестан.
582. ЗУХАЙРАЕВ АСЛАН НАГАЕВИЧ*, 12.09.1974 г.р., с. Сержен-Юрт Шалинского района ЧИАССР.
583. ЗУХАЙРАЕВ МУСА АЛИЕВИЧ*, 02.05.1974 г.р., г. Грозный ЧИАССР.
584. ЗЯЛИЛОВ ИЛЬНАР ИЛЬЯСОВИЧ*, 27.09.1980 г.р., г. Казань ТАССР.
585. ИБАЕВ РУСЛАН ЛОМ-АЛИЕВИЧ*, 11.11.1983 г.р., с. Старые Атаги Грозненского района ЧИАССР.
586. ИБАКОВ ЯСАВИЙ БУХАРЕВИЧ*, 01.09.1970 г.р., ст. Наурская ЧИАССР.
587. ИБРАГИМОВ АЛИХАН АДНАНОВИЧ*, 21.09.1980 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
588. ИБРАГИМОВ АРБИ ШАХИДОВИЧ*, 19.05.1974 г.р., с. Серноводск Сунженского района ЧИАССР.
589. ИБРАГИМОВ АХМЕД МАМАТОВИЧ*, 01.08.1976 г.р., с. Катыр-Юрт Ачхой-Мартановского района ЧИАССР.
590. ИБРАГИМОВ БИСЛАН МАСХУДОВИЧ*, 27.12.1976 г.р., г. Урус-Мартан Урус-Мартановского района ЧИАССР.
591. ИБРАГИМОВ ДАУД ВАХОДОВИЧ*, 07.12.1982 г.р., с. Урус-Мартан ЧИАССР.
592. ИБРАГИМОВ РУСЛАН ДЖАВАДИЕВИЧ*, 27.07.1982 г.р., г. Грозный ЧИАССР.
593. ИГОЛКИН МИХАИЛ ВИТАЛЬЕВИЧ*, 03.07.1974 г.р., г. Пермь.
594. ИДИГОВ ЗЕЛИМХАН АЛХАЗУРОВИЧ*, 09.06.1977 г.р., с. Старые-Атаги Грозненского района ЧИАССР.
595. ИДИГОВ РАМЗАН АСРУДИНОВИЧ*, 29.06.1979 г.р., с. Курчалой Шалинского района Чеченской Республики.
596. ИДРИСОВ БЕКМИРЗА АХМЕДОВИЧ*, 06.02.1984 г.р., с. Ялхой-Мохк Ножай-Юртовского района ЧИАССР.
597. ИДРИСОВ СУЛБАН СУЛТАНОВИЧ*, 03.06.1983 г.р., г. Шали ЧИАССР.
598. ИДРИСОВ ТИМУР САЙПИЕВИЧ*, 03.11.1974 г.р., г. Аргун ЧИАССР.
599. ИЖАЕВ МОВСАР САЛМАНОВИЧ*, 15.05.1983 г.р., с. Валерик Ачхой-Мартановского района ЧИАССР.
600. ИЗМАЙЛОВ ВАХА РУСЛАНОВИЧ*, 26.11.1983 г.р., г. Назрань ЧИАССР.
601. ИЛИЕВ ИССА ДАВИДОВИЧ*, 11.06.1976 г.р., с. Камбилеевское Пригородного района Северо-Осетинской АССР.
602. ИЛЬЯСОВ АБДУЛМАЛИК АБДУЛХАДЖИЕВИЧ*, 09.02.1959 г.р., с. Мирзааки Узгенский район Ошская область Киргизской ССР.
603. ИЛЬЯСОВ БАХРУДЫ ЗЕМЕЛЬЕВИЧ*, 24.05.1966 г.р., г. Гудермес ЧИАССР (24.05.1953 г.).
604. ИЛЬЯСОВ МУСЛИМ ЯРАГИЕВИЧ*, 09.11.1972 г.р., г. Шали ЧИАССР.
605. ИЛЯСОВ РАСУЛ КУРБАНОВИЧ*, 26.07.1985 г.р., с. Ведено Веденского района ЧИССР.
606. ИНАЛОВ АСЛАМБЕК АБУЯЗИТОВИЧ*, 05.06.1982 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
607. ИНАЛОВ ТИМУР АБУЯЗИТОВИЧ*, 02.09.1988 г.р., с. Ачхой-Мартан ЧИАССР.
608. ИОНОВ РУСЛАН ГАЗРАИЛЕВИЧ*, 31.08.1980 г.р., г. Усть-Джегута Карачаево-Черкесской Республики.
609. ИРИСБИЕВ ВАХИД ХАМИДОВИЧ*, 12.04.1973 г.р., с. Байрамаул Хасавюртовского р-на Республики Дагестан.
610. ИРИСБИЕВ МАГОМЕД УМАРПАШАЕВИЧ*, 02.08.1979 г.р., г. Гудермес Чечено-Ингушской АССР.
611. ИРИСХАНОВ ГЕЛАНИ УМАР-АЛИЕВИЧ*, 09.08.1983 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
612. ИРИСХАНОВ ИЛЕС ГИЛАНИЕВИЧ*, 22.06.1965 г.р., г. Аргун ЧИАССР.
613. ИРИСХАНОВ ЛЕМА УМАР-АЛИЕВИЧ*, 07.08.1978 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
614. ИСАЕВ АЛИХАН АЗИЗОВИЧ*, 1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
615. ИСАЕВ ИСЛАМ ДЕНИЕВИЧ*, 09.05.1984 г.р., Целиноградская область КазССР.
616. ИСАЕВ ЛЕМА ЯХЪЯЕВИЧ*, 30.04.1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
617. ИСАЕВ РАМЗАН УАХИТОВИЧ*, 08.08.1979 г.р., ст. Вознесеновка Малгобекского района ЧИАССР.
618. ИСАЕВ САИД-МАГОМЕД ЛЕЧАЕВИЧ*, 18.04.1978 г.р., с. Ачхой-Мартан ЧИАССР.
619. ИСАЕВ САЛАМБЕК МУСАЕВИЧ*, 14.11.1987 г.р., с. Бурнов Джувалинского района Джамбульской области КазССР.
620. ИСАЕВ ХАСАН БУКУЛИЕВИЧ*, 11.05.1967 г.р., с. Липовка Урус-Мартановского района ЧИАССР.
621. ИСАКОВ АБДУЛКАДЫР МАГОМЕДОВИЧ*, 12.03.1965 г.р., с. Комсомольское Кизилюртовского района Республики Дагестан.
622. ИСАКОВ АСЛАНБЕК МОВЛДЫЕВИЧ*, 08.05.1983 г.р., с. Урус-Мартан Урус-Мартановского района Чеченской Республики.
623. ИСАКОВ БЕСЛАН УРУХМАНОВИЧ*, 07.12.1978 г.р., с. Бережновка Николаевского района Волгоградской области.
624. ИСАКОВ ВАЛИД САИД-АХМЕТОВИЧ*, 12.08.1972 г.р., с. Рошни-Чу Урус-Мартановского района ЧИАССР.
625. ИСАКОВ КАХРАМОН ЭРГАШЕВИЧ*, 23.03.1970 г.р., г. Ташкент Республики Узбекистан.
626. ИСАКОВ ШИРЛАМ ШИРВАНЬЕВИЧ*, 19.10.1979 г.р., г. Грозный ЧИАССР.
627. ИСЛАМОВ ЛЕЧИ СИРАЕВИЧ*, 28.05.1961 г.р., с. Алхазурово Урус-Мартановского района ЧИАССР.
628. ИСЛАМОВ САИД МАГОМЕДОВИЧ*, 31.01.1977 г.р., с. Кислово Быковского района Волгоградской обл.
629. ИСЛАМОВ УСМАН МУСАЕВИЧ*, 17.12.1979 г.р., г. Аргун Шалинского района ЧИАССР.
630. ИСМАИЛОВ АСЛАН БАУДИНОВИЧ*, 11.11.1978 г.р., г. Грозный Чеченской Республики.
631. ИСМАИЛОВ АХМЕД ИМРАНОВИЧ*, 24.06.1974 г.р., г. Чимкент Казахской ССР.
632. ИСМАИЛОВ ИСЛАМ ИСАЕВИЧ*, 29.04.1987 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
633. ИСМАИЛОВ ИСМАИЛ МАГОМЕДОВИЧ*, 03.09.1949 г.р., с. Леваши Левашинского р-на Республики Дагестан.
634. ИСМАИЛОВ КАЗБЕК ВАХИДОВИЧ*, 09.06.1977 г.р., с. Аллерой Ножай-Юртовского района ЧИАССР.
635. ИСМАИЛОВ МУХТАРПАША ХУМАИДОВИЧ*, 11.01.1972 г.р., с. Борагангечу Хасавюртовского района Республики Дагестан.
636. ИСМАИЛОВ САИД-ХУСАЙН ЛЕЧИЕВИЧ*, 16.09.1985 г.р., с. Белгатой Шалинского района ЧИАССР.
637. ИСМАИЛОВ ШАМХАН ШАМСУДИНОВИЧ*, 12.09.1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
638. ИСРАИЛОВ ВАХИТ ХАСЕНОВИЧ*, 12.10.1983 г.р., с. Суворов-Юрт Гудермесского района ЧИАССР.
639. ИСРАИЛОВ ВИСХАН ВАЛИДОВИЧ*, 17.01.1988 г.р., с. Центарой Ножай-Юртовского района ЧИАССР.
640. ИСРАИЛОВ ФАРИД ХАЙРУЛАЕВИЧ*, 12.10.1980 г.р., с. Ведено Веденского района ЧИАССР.
641. ИСРАИЛОВ ХАБИБ ХАВАЖИЕВИЧ*, 16.01.1985 г.р., с. Макажой Веденского района ЧИАССР.
642. ИСРАПИЛОВ АБУ-СЕЛИМ АБУ-МУСЛИМОВИЧ*, 08.01.1976 г.р., с. Рошни-Чу Урус-Мартановского района ЧИАССР.
643. ИСРАПИЛОВ ИБРАГИМ АХМАДОВИЧ*, 13.01.1960 г.р., с. Сюжи Советского района ЧИАССР.
644. ИСТАМУЛОВ БЕКСОЛТ ШИРВАНИЕВИЧ*, 14.03.1979 г.р., с. Ведено Веденского района ЧИАССР.
645. ИСУПХАДЖИЕВ АДАМ ВАХАЕВИЧ*, 13.11.1985 г.р., г. Грозный ЧИАССР.
646. ИСУПХАДЖИЕВ САЙДАМИН АЛМАНОВИЧ*, 25.11.1976 г.р., ст. Калиновская Наурского района ЧИАССР.
647. ИЦАРАЕВ ИСА МАГОМЕДОВИЧ*, 29.11.1976 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
648. ИШКОВ РУСЛАН НАВИЛЬЕВИЧ*, 11.09.1979 г.р., г. Чистополь Республики Татарстан.
649. ИШМУРАТОВ ТИМУР РАВИЛЕВИЧ*, 05.06.1975 г.р., г. Азнакаево Республики Татарстан.
650. КАБИЛОВ БУХАРИ ГЕЛАНИЕВИЧ*, 30.07.1982 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
651. КАБЫЛОВ АДЛАН АДАМОВИЧ*, 26.12.1979 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
652. КАВТАРАШВИЛИ АСЛАН АЛЕКСАНДРОВИЧ*, 22.04.1982 г.р., с. Джоколо Ахметского района Грузинской ССР.
653. КАДИЕВ САИД-САЛАХ ХОЗУЕВИЧ*, 10.02.1974 г.р., с. Шатой Шатойского района ЧИАССР.
654. КАДИСОВ АЛАШ АТОВХАДЖИЕВИЧ*, 02.10.1977 г.р., с. Зандак Ножай-Юртовского района ЧИАССР.
655. КАДЫРОВ АЛИ МОВДАЕВИЧ*, 18.10.1979 г.р., с. Нижний Герзель Гудермесского района ЧИАССР.
656. КАЗАНЧЕВ АСЛАНБЕК ЮРЬЕВИЧ*, 08.11.1971 г.р., г. Нальчик Кабардино-Балкарской Республики.
657. КАЗБУЛАТОВ ШАМИЛЬ КАСИМОВИЧ*, 10.06.1972 г.р., с. Кара-Тюбе Нефтекумского района Ставропольского края.
658. КАЗНИН ОЛЕГ ВАЛЕНТИНОВИЧ*, 02.04.1963 г.
659. КАИМОВ ИЛЬЯС БАУДИНОВИЧ*, 03.04.1984 г.р., г. Грозный ЧИАССР.
660. КАИМОВ ИСА ЛОМ-АЛИЕВИЧ*, 11.07.1985 г.р., г. Грозный ЧИАССР.
661. КАИМОВ МОЛДЫ ЛОМ-АЛИЕВИЧ*, 26.02.1976 г.р., с. Побединское Грозненского района ЧИАССР.
662. КАЛИМУЛЛИН НАФИС МУЗАГИТОВИЧ*, 12.01.1959 г.р., с. Урсаево Азнакаевского района Республики Татарстан.
663. КАМАЛЕТДИНОВ АЙРАТ ГАМИЛОВИЧ*, 26.04.1976 г.р., г. Набарежные Челны ТАССР.
664. КАМЕНИЧЕНКО СЕРГЕЙ СЕРГЕЕВИЧ*, 24.10.1975 г.р., ст. Ассиновская Сунженского района ЧИАССР.
665. КАНАЕВ САИД САЙД-МАГОМЕДОВИЧ*, 14.03.1984 г.р., с. Захарово Рязанской области.
666. КАНТАЕВ АНЗОР ЮСУПОВИЧ*, 10.10.1972 г.р., с. Ачхой-Мартан Ачхой-Матрановского района ЧИАССР.
667. КАНТАЕВ КАЗБЕК МАЙРБЕКОВИЧ*, 21.06.1980 г.р., с. Ачхой-Мартан ЧИАССР.
668. КАНТАЕВ РАДЖУ ХАМЗАНОВИЧ*, 28.09.1982 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
669. КАППУШЕВ АЛИ АНЗАУРОВИЧ*, 28.11.1967 г.р., с. Учкекен Малокарачаевского района Карачаево-Черкесской Республики.
670. КАРАСОВ ТИМУР МУРЗАБЕКОВИЧ*, 07.11.1975 г.р., а. Адыге-Хабль Адыге-Хабльского района Ставропольского края Карачаево-Черкесской Республики (КЧАО).
671. КАРИМОВ ИСА АБДУЛАЕВИЧ*, 23.12.1970 г.р., с. Побединское Грозненского района Чеченской Республики.
672. КАРПЕНКО ВИКТОР ЯКОВЛЕВИЧ*, 09.01.1950 г.р., с. Воронцовка Фрунзенской обл. Кыргызской ССР.
673. КАРТУЕВ УВАЙС МАХМУДОВИЧ*, 13.01.1960 г.р., с. Комсомольское Урус-Мартановского района Чеченской Республики.
674. КАСАТКИНА СВЕТЛАНА ВИКТОРОВНА*, 16.02.1963 г.р., г. Йошкар-Ола.
675. КАСЫМАХУНОВ ЮСУП САЛИМАХУНОВИЧ*, 15.10.1964 г.р., г. Андижан Республики Узбекистан.
676. КАТАЕВ АБУБАКАР ЭЛЬМУРЗАЕВИЧ*, 01.07.1979 г.р., селение Батаюрт Хасавюртовского района Республики Дагестан.
677. КАТАЕВ АХМЕД ВАХАЕВИЧ*, 27.03.1980 г.р., с. Алхан-Кала Грозненского района ЧИАССР.
678. КАТАЕВ САИД-ЭМИН УВАЙСОВИЧ*, 27.12.1984 г.р., с. Старые Атаги Грозненского района ЧИАССР.
679. КАТЧИЕВ РАШИД АБРЕКЗАУРОВИЧ*, 28.08.1974 г.р., с. Учкент Малокарачаевского района Карачаево-Черкесской Республики.
680. КАЦИЕВ СУЭЛДЫ РУСЛАНОВИЧ*, 12.06.1976 г.р., г. Грозный ЧИАССР.
681. КЕРЕЙТОВ РУСЛАН ЮНУСОВИЧ*, 14.04.1977 г.р., а. Эркен-Халк Адыге-Хабльского района Карачаево-Черкесской Республики.
682. КЕЧЕРУКОВ ОЙСУЛ КАЗИ-МАГОМЕДОВИЧ*, 02.01.1966 г.р., с. Учкекен Малокарачаевского района Ставропольского края.
683. КИБИЧОВ РИЗВАН САЛМАНОВАИЧ*, 01.12.1969 г.р., с. Мескеты Ножай-Юртовского района ЧИАССР.
684. КИЛАТ КОНСТАНТИН ВЛАДИМИРОВИЧ*, 27.03.1976 г.р., г. Красноводск Туркменской ССР.
685. КИМ ВАЛЕРИЙ САНГИЛЬЕВИЧ*, 14.10.1976 г.р., пос. Быков Долинского р-на Сахалинской области.
686. КИРИЕНКО КОНСТАНТИН БОРИСОВИЧ*, 13.05.1975 г.р., г. Барнаул Алтайского края.
687. КИРИЛЛОВ ИГОРЬ АНАТОЛЬЕВИЧ*, 05.05.1975 г.р., г. Томск.
688. КЛЕВАЧЕВ МИХАИЛ МИХАЙЛОВИЧ*, 30.03.1958 г.р., г. Москва.
689. КЛИМУК СЕРГЕЙ АЛЕКСАНДРОВИЧ*, 09.12.1970 г.р., пос. Первое Мая Илийского района Алма-Атинской области Казахской ССР.
690. КЛОЧКОВ РУСЛАН СЕРГЕЕВИЧ*, 04.01.1976 г.р., пос. Первомайский Тамбовской области.
691. КОВАЛЬЧУК ФЕДОР СЕРГЕЕВИЧ*, 06.03.1981 г.р., г. Полярные Зори Мурманской обл.
692. КОВРАЕВ АХМЕД МАГОМЕДОВИЧ*, 29.04.1977 г.р., г. Грозный ЧИАССР.
693. КОВРАЕВ ВАХИД ВАХАЕВИЧ*, 15.12.1974 г.р., с. Кулары Грозненского района Чечено-Ингушской АССР.
694. КОВРАЕВ ВИСХАДЖИ ВИСИТАЕВИЧ*, 18.04.1982 г.р., с. Цоци-Юрт Курчалоевского района Чеченской Республики.
695. КОВРАЕВ РАМЗАН АВАЛУЕВИЧ*, 20.12.1969 г.р., г. Грозный ЧИАССР.
696. КОВРАЕВ РУСЛАН МАХМУДОВИЧ*, 03.06.1977 г.р., с. Урус-Мартан Урус-Мартановского р-на Чечено-Ингушской АССР.
697. КОДЗОЕВ МАГОМЕД МАЖИТОВИЧ*, 18.04.1975 г.р., г. Назрань ЧИАССР.
698. КОЗРОЕВ РАМАЗАН ДЖАБРАИЛОВИЧ*, 07.02.1974 г.р., ст. Гребенская Шелковского района ЧИАССР.
699. КОЙТЕМИРОВ АБДУЛГАСАН МАГОМЕДКАМИЛОВИЧ*, 22.02.1969 г.р., с. Н. Казанище ДАССР.
700. КОЙЧУЕВ РУСЛАН НУРПАШАЕВИЧ*, 01.12.1977 г.р., пос. Н.Сулак Кизилюртовского района Республики Дагестан.
701. КОЙЧУЕВ РУСЛАН ХАНАПИЕВИЧ*, 09.11.1969 г.р., г. Усть-Джегута Карачаево-Черкесской Республики.
702. КОКУНАЕВ РУСТАМ АЛЬБЕКОВИЧ*, 06.03.1986 г.р., с. Ачхой-Мартан ЧИАССР.
703. КОЛЧИН ЮРИЙ НИКОЛАЕВИЧ*, 08.04.1968 г.р., г. Дятьково Брянской области.
704. КОРНИЕНКО ГЕННАДИЙ АДАМОВИЧ*, 27.06.1950 г.р., г. Киселевск Кемеровской области.
705. КОРОВИН РУСЛАН МУМАДИЕВИЧ*, 18.07.1983 г.р., г. Грозный Чечено-Ингушской АССР.
706. КОРОЛЕВ НИКОЛАЙ ВАЛЕНТИНОВИЧ*, 31.03.1981 г.р., г. Москва.
707. КОРОЛЕВ СЕРГЕЙ ЕВГЕНЬЕВИЧ*, 12.11.1984 г.р., г. Сокольники Новомосковского района Тульской области.
708. КОРПЕНКО АЛЕКСАНДР ИННОКЕНТЬЕВИЧ*, 10.01.1979 г.р., г. Усть-Кута Иркутской области.
709. КОСАРИМ АНАТОЛИЙ ПЕТРОВИЧ*, 16.02.1961 г.р., п. Крещенский Гордеевского района Брянской области.
710. КОСИЛОВ СЕРГЕЙ ПЕТРОВИЧ*, 16.12.1953 г.р., г. Фатеж Фатежский район Курской области.
711. КОСТАРЕВ ОЛЕГ ВЛАДИМИРОВИЧ*, 25.04.1986 г.р., г. Глазов Удмуртской АССР.
712. КОСТЕНКО НИКОЛАЙ НИКОЛАЕВИЧ*, 20.09.1974 г.р., д. Лукошкино Топкинского района Кемеровской области.
713. КОСТОЕВ МАГОМЕТ БИСУЛТАНОВИЧ*, 29.07.1970 г.р., г. Орджоникидзе СО АССР.
714. КОСУМОВ ХАВАЖ ХУСЕЙНОВИЧ*, 01.02.1978 г.р., г. Аргун ЧИАССР.
715. КРЫМШАМХАЛОВ ЮСУФ ИБРАГИМОВИЧ*, 16.11.1966 г.р., п. Эркен-Шахар Адыге-Хабльского района Ставропольского края.
716. КУБАЧЕВ АХМЕД МОХМАДОВИЧ*, 20.10.1981 г.р., с. Чернокозово Наурского района ЧИАССР.
717. КУДАЕВ АХМЕД РУСЛАНОВИЧ*, 18.05.1985 г.р., г. Грозный ЧИАССР.
718. КУЖУЛОВ АРТУР ГАСАНОВИЧ*, 02.01.1980 г.р., ст. Шелковская Шелковского р-на ЧИАССР.
719. КУЖУЛОВ ИСМАИЛ ИМАНОВИЧ*, 28.06.1966 г.р., с. Эшилхатой Веденского района ЧИАССР.
720. КУЛАЕВ АРТУР ХАЛИТОВИЧ*, 30.07.1980 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
721. КУЛАЕВ НУРПАШИ АБУРГКАШЕВИЧ*, 28.10.1980 г.р., с. Энгеной Ножай-Юртовского района ЧИАССР.
722. КУЛИНИЧ ПАВЕЛ ВАЛЕНТИНОВИЧ*, 17.08.1973 г.р., г. Миасс Челябинской области.
723. КУЛЬВИНЕЦ АНАТОЛИЙ АЛЕКСАНДРОВИЧ*, 02.06.1972 г.р., г. Грозный Чеченской Республики.
724. КУПРИЯНОВ КИРИЛЛ АРНОЛЬДОВИЧ*, 28.11.1973 г.р., Ленинград.
725. КУРАМШИН АДЕЛЬ РУСТЭМОВИЧ*, 09.08.1982 г.р., г. Бугульма Республики Татарстан.
726. КУРАШЕВ НАСРУДИН ВАХИДОВИЧ*, 18.01.1982 г.р., с. Советское Советского района ЧИАССР.
727. КУРГАНОВ ЛАСХАН МАМБЕТОВИЧ*, 24.06.1982 г.р., ст. Щелкозаводская Шелковского района ЧИАССР.
728. КУРЕБЕДА НАТАЛЬЯ ВАЛЕНТИНОВНА*, 13.09.1975 г.р., г. Челябинск.
729. КУРКАЕВ СОСЛАН ХАСАНОВИЧ*, 11.05.1979 г.р., г. Чарск Семипалатинской области КазССР.
730. КУРКАЕВ ХУСЕН АХМЕДОВИЧ*, 29.06.1975 г.р., с. Слепцовская ЧИАССР.
731. КУЧАВА ЕЛГУДЖА ВАХТАНГОВИЧ*, 10.07.1977 г.р., с. Дэнвери Целенджихского района Грузинской ССР.
732. ЛАБАЗАНОВ АСЛАНБЕК СУЛТАНОВИЧ*, 28.04.1971 г.р., с. Советское Советского района Чеченской Республики.
733. ЛАБАЗАНОВ МАНСУР АХЪЯТОВИЧ*, 14.03.1979 г.р., ст. Ишерская Наурского района ЧИАССР.
734. ЛАБАЗАНОВ РИЗВАН ИСАЕВИЧ*, 26.09.1976 г.р., с. Алхан-Кала Грозненского района ЧИАССР.
735. ЛАВАРСЛАНОВ ХАЙБУЛА ЛАВАРСЛАНОВИЧ*, 18.09.1940 г.р., с. Карамахи Буйнакского района Республики Дагестан.
736. ЛАВРЕНОВ ВИТАЛИЙ ВЛАДИМИРОВИЧ*, 25.04.1983 г.р., г. Ленинград.
737. ЛАТЫПОВ САЛАВАТ МИРЗАГИТОВИЧ*, 16.02.1975 г.р., г. Ангрен Ташкентской области Республики Узбекистан.
738. ЛЕЛИЕВ АРСЕН ВИСИРПАШАЕВИЧ*, 24.09.1973 г.р., г. Хасавюрт Республики Дагестан.
739. ЛЕЛИЕВ ТАХИР ВИСИРПАШАЕВИЧ*, 20.04.1983 г.р., г. Хасавюрт Хасавюртовского р-на Республики Дагестан.
740. ЛЕЧИЕВ СУПЬЯН МУСАЕВИЧ*, 02.10.1980 г.р., с. Галайты Ножай-Юртовского района ЧИАССР.
741. ЛИМОНОВ КОНСТАНТИН МИХАЙЛОВИЧ*, 22.03.1976 г.р., пос. Пролетарье Верхотурского района Свердловской области.
742. ЛИСИЦИНА ЮЛИЯ СЕРГЕЕВНА*, 01.07.1982 г.р., г. Усть-Илимск Иркутской области.
743. ЛИХАНОВ АНДРЕЙ ВИКТОРОВИЧ*, 09.08.1978 г.р., г. Зыряновск Восточно-Казахстанской области.
744. ЛОБАЧЕВ ВЛАДИМИР ВЛАДИМИРОВИЧ*, 12.09.1970 г.р., х. Черни Усть-Донецкого района Ростовской области.
745. ЛОЛОХОЕВ МАГОМЕД КУРЕЙШОВИЧ*, 17.07.1978 г.р., с. Экажево Назрановского района Чечено-Ингушской АССР.
746. ЛОМАЕВ МУСА УМУРСОЛТОВИЧ*, 04.06.1981 г.р., г. Грозный Чеченской Республики.
747. ЛОРСАНОВ ИСЛАМ АБДУЛ-МУТАЛИПОВИЧ*, 20.09.1983 г.р., Ачхой-Мартановский район ЧИАССР.
748. ЛОРСАНОВ РУСЛАН ЭМДИЕВИЧ*, 07.02.1983 г.р., г. Грозный ЧИАССР.
749. ЛУКМАНОВ АЙРАТ РАЗИФОВИЧ, 27.09.1974 г.р., г. Дюртюли Республики Башкортостан.
750. ЛУКОЖЕВ ИСЛАМ БАЗДЖИГИТОВИЧ*, 22.01.1975 г.р., с. Тукуй-Мектеб Нефтекумского района Ставропольского края.
751. ЛУКЬЯНЧИКОВ ВИКТОР ВАСИЛЬЕВИЧ*, 08.01.1951 г.р., г. Волчанск Карпинский район Свердловской области.
752. ЛУЛУГОВ СЕРГЕЙ САЙДАЛИЕВИЧ*, 01.09.1955 г.р., с. Конкринка Шартандинского района Акмолинской области КазССР.
753. ЛУЛУЕВ УСПА БАЙДИНОВИЧ*, 08.08.1959 г.р., с. Эшилхатой Веденского района ЧИАССР.
754. ЛУХМЫРИН СТАНИСЛАВ АНДРЕЕВИЧ*, 12.04.1990 г.р., г. Волгоград.
755. ЛЫСОГОР СЕРГЕЙ ВЛАДИМИРОВИЧ*, 31.08.1970 г.р., г. Приморско-Ахтарск Приморско-Ахтарского р-на Краснодарского края.
756. МААЗИЕВ МАКАМАГОМЕД МАГОМЕДШАПИЕВИЧ*, 23.09.1963 г.р., с. Губден Карабудахкентского района Республики Дагестан.
757. МААЛОВ РУСЛАН ШАМСУДИНОВИЧ*, 28.09.1970 г.р., с. Айти-Мохк Ножай-Юртовского района ЧИАССР.
758. МАГАМАДОВ АРСЕН РАМАЗАНОВИЧ*, 23.07.1983 г.р., с. Знаменское Надтеречного района ЧИАССР.
759. МАГАМАДОВ ВАХИ ДУТАЕВИЧ*, 23.02.1986 г.р., с. Катыр-Юрт Ачхой-Мартановского района Чеченской Республики.
760. МАГАМАДОВ ТЕМИРХАН УСМАНОВИЧ*, 06.05.1980 г.р., п. Ики-Бурул Ики-Бурульского района Калмыцкой АССР.
761. МАГАМЕРЗУЕВ ТАХИР САЙДУЛАЕВИЧ*, 19.09.1974 г.р., с. Серноводск ЧИАССР.
762. МАГЕМЕДОВ АДАМ СЕИДИМИЕВИЧ*, 04.10.1981 г.р., г. Гудермес ЧИАССР.
763. МАГОМАДОВ АРСЕН СУЛЕЙМАНОВИЧ*, 20.01.1986 г.р., с. Ачхой-Мартан ЧИАССР.
764. МАГОМАДОВ АСЛАН МАВЛАДОВИЧ*, 09.03.1972 г.р., с. Знаменское Надтеречного р-на ЧИАССР.
765. МАГОМАДОВ АЮБ САИД-АХМЕДОВИЧ*, 06.02.1982 г.р., с. Шовхал-Берды Ножай-Юртовского района ЧИАССР.
766. МАГОМАДОВ БЕСЛАН ЗИЯВДИЕВИЧ*, 23.05.1975 г.р., с. Урус-Мартан ЧИАССР.
767. МАГОМАДОВ ВИСХАН ГЕЛАНИЕВИЧ*, 11.11.1984 г.р., г. Грозный ЧИАССР.
768. МАГОМАДОВ ДЖАБРАИЛ САЙД-ЭМИЕВИЧ*, 04.10.1987 г.р., с. Курчалой ЧИАССР.
769. МАГОМАДОВ ИСЛАМ ШАХИДОВИЧ*, 25.08.1980 г.р., г. Грозный ЧИАССР.
770. МАГОМАДОВ РАСУ ВАХАЕВИЧ*, 18.03.1977 г.р., г. Грозный ЧИАССР.
771. МАГОМАДОВ РИЗВАН РАМАЗАНОВИЧ*, 29.05.1978 г.р., с. Новый-Шарой Ачхой-Мартановского р-на ЧИАССР.
772. МАГОМАДОВ САИД-ЭМИ САЙДАНОВИЧ*, 20.09.1978 г.р., г. Балхаш Эжезказганской области Казахской АССР.
773. МАГОМАДОВ ХУСЕЙН ИСАЕВИЧ*, 23.01.1979 г.р., с. Урус-Мартан ЧИАССР.
774. МАГОМАЗОВ РУСТАМ АБАКАРОВИЧ*, 18.01.1981 г.р., ст. Бороздиновская Шелковского района ЧИАССР.
775. МАГОМЕДОВ АБДУРАХИМ ОМАРОВИЧ*, 15.01.1943 г.р., с. Саситли Цумадинского района ДАССР.
776. МАГОМЕДОВ АХМЕД МАГОМЕДОВИЧ*, 19.03.1976 г.р., г. Махачкала Республики Дагестан.
777. МАГОМЕДОВ БИСЛАН ДАДАЕВИЧ*, 28.08.1978 г.р., ст. Шелковская Шелковского района ЧИАССР.
778. МАГОМЕДОВ ГАСАН АСИЛДЕРОВИЧ*, 19.09.1968 г.р., с. Гунха Ботлихского района Республики Дагестан.
779. МАГОМЕДОВ ЗАЙНУТДИН АБДУРАХМАНОВИЧ*, 05.10.1963 г.р., с. Куппа Левашинского района Республики Дагестан.
780. МАГОМЕДОВ МАГОМЕД-САЙГИД МАГОМЕДРАСУЛОВИЧ (МАГОМЕДОВ МАГОМЕДСАЙГИД МАГОМЕДРАСУЛОВИЧ)*, 16.08.1972 г.р., с. Губден Карабудахкентского района Республики Дагестан (16.08.1972 г.р., с. Каясула Нефтекумского района Ставропольского края).
781. МАГОМЕДОВ МАГОМЕДРАСУЛ ГАЗИДИБИРОВИЧ*, 10.01.1958 г.р., с. Тлондод Цумадинского района Дагестанской АССР.
782. МАГОМЕДОВ МУСЛИМ МУСАЕВИЧ*, 22.10.1985 г.р., с. Киров-Юрт Веденского района ЧИАССР.
783. МАГОМЕДОВ УВАЙС АБДУЛМУСЛИМОВИЧ*, 25.05.1970 г.р., с. Зубутли-Миатли Кизилюртовского района Республики Дагестан.
784. МАГОМЕДОВ УМАХАН РАМАЗАНОВИЧ*, 12.09.1967 г.р., с. Лобко Левашинского района ДАССР.
785. МАГОМЕДОВ ЮСУП БАГАУТДИНОВИЧ*, 05.02.1971 г.р., с. Ташкапур Левашинского района Республика Дагестан.
786. МАГОМЕДШАФИЕВ ЗАВИР МАГОМЕДНАБИЕВИЧ*, 29.09.1988 г.р., г. Махачкала Республики Дагестан.
787. МАДАГОВ МАГОМЕД МОВЛАДИЕВИЧ*, 28.10.1985 г.р., с. Гехи Урус-Мартановского района Чеченской Республики.
788. МАДАЕВ АДНАН ИСАЕВИЧ*, 06.10.1985 г.р., с. Урус-Мартан ЧИАССР.
789. МАДАЕВ АХМЕД РИЗВАНОВИЧ*, 31.10.1976 г.р., с. Знаменское Надтеречного района ЧИАССР.
790. МАДАЕВ ГИЛАНИ САЛАМУЕВИЧ*, 12.08.1967 г.р., с. Шали Шалинского района ЧИАССР.
791. МАДАЕВ УЗУМ-ХАЖИ САЙТАМ-ЗАТОВИЧ*, 14.12.1980 г.р., с. Курчалой Курчалоевского района Чеченской Республики.
792. МАДАРОВ ИСРАИЛ ИСАЕВИЧ*, 04.04.1988 г.р., с. Шали Шалинского р-на ЧИАССР.
793. МАЖИЕВ ХУСЕЙН ИБРАГИМОВИЧ*, 21.11.1971 г.р., г. Аргун ЧИАССР.
794. МАЗАЕВ АКРАМАН ЛОМАЛИЕВИЧ*, 12.09.1986 г.р., с. Ведено Веденского района ЧИАССР.
795. МАЗУЕВ АДЛАН САИД-ХАСАНОВИЧ*, 30.06.1984 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
796. МАЗУЕВ АРСЕН САЙД-ХАСАНОВИЧ*, 05.02.1975 г.р., с. Самашки Ачхой-Мартановского р-на ЧИАССР.
797. МАКАЕВ ИСА АЭЛЕЕВИЧ*, 29.05.1981 г.р., с. Урус-Мартан ЧИАССР.
798. МАКАЕВ МУСЛИМ САИД-АХМЕДОВИЧ*, 07.12.1979 г.р., с. Катыр-Юрт Ачхой-Мартановского р-на Чеченской Республики.
799. МАКАЕВ ЮНУС МОЛДИНОВИЧ*, 09.09.1978 г.р., с. Алхан-Кала Грозненского района ЧИАССР.
800. МАКАРЕНКО АНДРЕЙ ВИКТОРОВИЧ*, 18.07.1962 г.р., г. Киселевск Кемеровской области.
801. МАКСИМЕНКО СЕРГЕЙ ЛЕОНИДОВИЧ*, 17.07.1966 г.р., г. Владивосток Приморского края.
802. МАКУЕВ РУСЛАН АЛАУДИНОВИЧ*, 27.05.1974 г.р., с. Самашки ЧИАССР.
803. МАЛИКОВ ЗЕЛИМХАН СУЛЕЙМАНОВИЧ*, 02.12.1985 г.р., с. Ачхой-Мартан ЧИАССР.
804. МАЛЬСАГОВ АЛИ АХМЕТОВИЧ*, 11.02.1987 г.р., г. Грозный ЧИАССР.
805. МАЛЬСАГОВ ИСЛАМ ВАХИТОВИЧ*, 13.03.1972 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
806. МАЛЬСАГОВ УМАР АХМЕТОВИЧ*, 20.11.1984 г.р., с. Урус-Мартан ЧИАССР.
807. МАМАЕВ АРТУР ЗАПИРОВИЧ*, 06.10.1974 г.р., г. Махачкала ДАССР.
808. МАМАЕВ РУСЛАН РАСУЛОВИЧ*, 21.09.1974 г.р., с. Хамавюрт Хасавюртовского района ДАССР.
809. МАМАКАЕВ ЗАУР МУСАЕВИЧ*, 15.12.1982 г.р., с. Герменчук Шалинского района ЧИАССР.
810. МАМЕДОВ САЙД-МАГОМЕД АБУАЗИТОВИЧ*, 15.06.1977 г.р., г. Грозный ЧИАССР.
811. МАМСУРОВ ХАРОН АЛАУДЫЕВИЧ*, 31.01.1985 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
812. МАМЧУЕВ ХАСАН КЕМАЛОВИЧ*, 10.07.1970 г.р., ст. Каладжинская Лабинского района Краснодарского края.
813. МАНИЯ МУРТАЗИ ГВАНДЖИЕВИЧ*, 07.02.1966 г.р., с. Бзыбь Гагрского района Абхазской АССР.
814. МАНТАГОВ АРСЛАНБЕК НАЙБИРСОЛТАНОВИЧ*, 24.01.1977 г.р., с. Хамавюрт Хасавюртовского района Республики Дагестан.
815. МАНФИРОВ ВАДИМ СЕРГЕЕВИЧ*, 17.06.1982 г.р., г. Кемерово.
816. МАРЗАГИШИЕВ РУСТАМ АЙНОДИНОВИЧ*, 24.07.1976 г.р., с. Бурунское Шелковского района ЧИАССР.
817. МАРКОВ ВЛАДИСЛАВ АЛЕКСЕЕВИЧ*, 12.04.1983 г.р., п. Коммунар Гатчинского района Ленинградской области.
818. МАРКУЕВ АЮБХАН СУЛТАНОВИЧ*, 27.10.1983 г.р., с. Шали Чеченской Республики.
819. МАСЛОВ ДМИТРИЙ ВИКТОРОВИЧ*, 27.03.1973 г.р., г. Закаменск Бурятской АССР.
820. МАСЛОВ ИВАН НИКОЛАЕВИЧ*, 13.07.1986 г.р., г. Пошехонье Ярославской области.
821. МАСТАЕВ АСЛАН ХУСЕЙНОВИЧ*, 20.11.1965 г.р., п. Горагорский Надтеречного района ЧИАССР.
822. МАСХУДОВ УМАТХАДЖИ АЛИЕВИЧ*, 07.12.1987 г.р., г. Грозный ЧИАССР.
823. МАТАЕВ СУПЬЯН САИДГАЛИЕВИЧ*, 18.08.1980 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
824. МАТВЕЕВ АЛЕКСЕЙ НИКОЛАЕВИЧ*, 18.04.1971 г.р., г. Кострома.
825. МАТВЕЕВ ЕВГЕНИЙ ВАЛЕРЬЕВИЧ*, 03.10.1976 г.р., г. Кострома.
826. МАТУЕВ МОВЛДИ АБУЕВИЧ*, 18.11.1977 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
827. МАХАЕВ ХУСЕЙН МАГОМЕДОВИЧ*, 24.02.1985 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
828. МАХАМАДОВ АЛМАН ИМРАНОВИЧ*, 01.10.1975 г.р., с. Дуба-Юрт Шалинского района Чеченской Республики.
829. МАХАТАЕВ АХАТ ТЕМИРСУЛТАНУЛЫ*, 27.07.1978 г.р., с. Советское Ленгерского района Чимкентской области Казахской ССР.
830. МАХАУРИ АЗАМАТ РУСЛАНОВИЧ*, 24.06.1985 г.р., ст. Ассиновская Сунженского р-на ЧИАССР.
831. МАХАУРИ АСЛАН МАХМАТГИРИЕВИЧ*, 08.10.1985 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
832. МАХМУДОВ ЮСУП УМАРОВИЧ*, 30.07.1973 г.р., п. Новогрозненский Гудермесского района Чеченской Республики.
833. МАХМУЕВ ЗЕЛИМХАН АБДУРАШИДОВИЧ*, 20.06.1989 г.р., ст. Калиновская Наурского района ЧИАССР.
834. МАХНЫЧЕВ ВЛАДИМИР АЛЕКСЕЕВИЧ*, 10.07.1970 г.р., ст. Орджоникидзевская Сунженского района Республики Ингушетия.
835. МАХУШЕВ РУСТАМ ВАСИЛЬЕВИЧ*, 02.12.1977 г.р., с. Керла-Юрт Грозненского района ЧИАССР.
836. МАЦАЕВ МАГОМЕД ЛАУДИЕВИЧ*, 08.02.1977 г.р., г. Грозный ЧИАССР.
837. МАЦИЕВ СУЛТАН ДЕЛЕМБЕКОВИЧ*, 13.10.1974 г.р., г. Грозный ЧИАССР.
838. МЕДИЕВ ТАМЕРЛАН ХАЛИДОВИЧ*, 15.12.1986 г.р., с. Хиди-Хутор Ножай-Юртовского района ЧИАССР.
839. МЕДОВ ЗЕЛИМХАН ХУСЕЙНОВИЧ*, 02.02.1981 г.р., с. Сагопши Малгобекского района Республики Ингушетия.
840. МЕЖИДОВ ИСМАИЛ АЙНДИНОВИЧ*, 04.01.1987 г.р., с. Улус-Керт Советского района ЧИАССР.
841. МЕЖИЕВ АБУБАКАР ДОРГУЕВИЧ*, 14.04.1970 г.р., с. Ищерское Наурского района ЧИАССР.
842. МЕЖИЕВ АЛИХАН САЙД-АХМЕДОВИЧ*, 29.10.1978 г.р., с. Махкеты Веденского района ЧИАССР.
843. МЕЖИЕВ АХЯД САЙД-АХМЕДОВИЧ*, 09.09.1969 г.р., с. Махкеты Веденского района ЧИАССР.
844. МЕЖИЕВ ЛЕМА ЛЕЧИЕВИЧ*, 22.11.1988 г.р., с. Садовое Грозненского района ЧИАССР.
845. МЕЖИЕВ МУСА МОВЛАЕВИЧ*, 21.05.1977 г.р., совхоз “Подгорный” Курсавского района Ставропольского края.
846. МЕЖИЕВ РУСТАМ СУПЬЯНОВИЧ*, 17.09.1975 г.р., с. Серноводск Сунженского района ЧИАССР.
847. МЕЗЕНЦЕВ ВИКТОР ВИКТОРОВИЧ*, 19.07.1966 г.р., г. Ишим Тюменской области.
848. МЕРЖОЕВ АЙДИ МАГОМЕДОВИЧ*, 18.08.1979 г.р., с. Бамут Ачхой-Мартановского района ЧИАССР.
849. МЕРЖОЕВ АНЗОР УСМАНОВИЧ*, 28.07.1985 г.р., с. Бамут Ачхой-Мартановского района ЧИАССР.
850. МЕРЖОЕВ КАЗБЕК ОМАРОВИЧ*, 06.11.1981 г.р., с. Бамут Ачхой-Мартановского района ЧИАССР.
851. МЕРКУЛОВ АЛЕКСЕЙ ВЛАДИМИРОВИЧ*, 18.01.1974 г.р., г. Лесичанск Луганской области Украинской ССР.
852. МЕШИЕВ МАГОМЕД УСМАНОВИЧ*, 29.01.1985 г.р., с. Ведено ЧИАССР.
853. МИГАЕВ ИЛЬЯ ВАСИЛЬЕВИЧ*, 10.12.1980 г.р., хутор Веселый Веселовского района Ростовской области.
854. МИГАЛЬ СТАНИСЛАВ ВИКТОРОВИЧ*, 11.12.1973 г.р., г. Камень-на-Оби Алтайского края.
855. МИЗАЕВ АДАМ РАМЗАНОВИЧ*, 05.07.1979 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
856. МИЛЮКОВ АЛЕКСАНДР АРКАДЬЕВИЧ*, 31.08.1977 г.р., г. Назарово Красноярского края.
857. МИНИН АНДРЕЙ ИВАНОВИЧ*, 28.12.1972 г.р., г. Саратов.
858. МИНКАЕВ ИБРАГИМ УМАРОВИЧ*, 10.07.1989 г.р., с. Курчалой Шалинского района ЧИАССР.
859. МИНКАИЛОВ РАСУЛ НИКОЛАЕВИЧ*, 17.11.1978 г.р., с. Новое Солкушино Наурского района ЧИАССР.
860. МИНСУЛТАНОВ АЛИ ИБРАГИМОВИЧ*, 22.03.1979 г.р., с. Ленинаул Казбековского р-на Республики Дагестан.
861. МИРОШКИН ИГОРЬ ДМИТРИЕВИЧ*, 10.10.1970 г.р., г. Норильск Красноярского края.
862. МИТАЕВ СУПЬЯН МУСАЕВИЧ*, 19.04.1979 г.р., г. Гудермес ЧИАССР.
863. МИТАЛАЕВ АСЛАНБЕК НАИБОВИЧ*, 21.06.1979 г.р., с. Ведено Веденского района ЧИАССР.
864. МИТАЛАЕВ ХУСЕЙН УМАРОВИЧ*, 13.02.1977 г.р., с. Ведено Веденского района Чеченской Республики.
865. МИТИГОВ МУСА ВАДУТОВИЧ*, 27.09.1978 г.р., с. Хамавюрт Хасавюртовского района ДССР.
866. МИХАЛОВ ГЕЛАНИ ЗАЙНДИЕВИЧ*, 28.09.1985 г.р., с. Радужное Грозненского района ЧИАССР.
867. МИХАЛОВ ХАВАЖИ ЗЕУДЫЕВИЧ*, 23.10.1984 г.р., с. Побединское Грозненского района ЧИАССР.
868. МИХЕЕВ АЛЕКСАНДР МИХАЙЛОВИЧ*, 06.02.1964 г.р., г. Сельцо Брянской области.
869. МИХЕЕВ ИВАН ВЛАДИМИРОВИЧ*, 01.02.1985 г.р., г. Киров.
870. МОГУШКОВ РУСЛАН АХЪЯЕВИЧ*, 14.05.1976 г.р., с. Насыр-Корт Назрановского района ЧИАССР.
871. МОРОЗОВ РОМАН ИВАНОВИЧ*, 24.11.1974 г.р., село Лебедин Шполянского р-на Черкасской области.
872. МУДАЕВ ДЖАМАЛАЙ ЛЕЧИЕВИЧ*, 07.10.1984 г.р., с. Курчалой Шалинского района ЧИАССР.
873. МУДУШОВ ВАХА-АЛИ САЙДСЕЛИМОВИЧ*, 27.03.1970 г.р., с. Согунты Ножай-Юртовского района ЧИАССР.
874. МУДУШОВ РАСУЛ РУХМАДОВИЧ*, 09.06.1984 г.р., с. Согунты Ножай-Юртовского района ЧИАССР.
875. МУЖАХОЕВА ЗАРЕМА МУСАЕВНА*, 09.02.1980 г.р., станица Ассиновская Сунженского района ЧИАССР.
876. МУЗАЕВ АДАМ ИДРИСОВИЧ*, 21.10.1979 г.р., с. Энгель-Юрт Гудермесского района ЧИАССР.
877. МУЗАЕВ АСЛАН МОВЛДЫЕВИЧ*, 04.04.1977 г.р., н.п. Гой-Чу Урус-Мартановского района ЧИАССР.
878. МУЗАЕВ АХМЕД ВАХИТОВИЧ*, 25.09.1986 г.р., с. Серноводск Сунженского района ЧИАССР.
879. МУЗИЕВ ЭЛЬМАДИ НУРАДИЛОВИЧ*, 28.02.1972 г.р., с. Хасавюрт ДАССР.
880. МУЛАЕВ ИСА МУГУМАТОВИЧ*, 21.01.1987 г.р., с. Труновское Ставропольского края.
881. МУЛАСАНОВ МИХАИЛ ТАЙМАЗХАНОВИЧ*, 20.08.1970 г.р., ст. Шелковская Шелковского района ЧИАССР.
882. МУЛУЕВ РОМАН ЭМИЕВИЧ*, 07.01.1986 г.р., с. Гуни Введенского района ЧИАССР.
883. МУЛЬКАЕВ РАСУЛ РАШИТОВИЧ*, 16.11.1979 г.р., ст. Галюгаевской Курского района Ставропольского края.
884. МУНАЕВ МАГОМЕД АПТИЕВИЧ*, 08.10.1982 г.р., г. Грозный ЧИАССР.
885. МУНАПОВ ЭДИЛБЕК ДАНИЛБЕКОВИЧ*, 18.08.1981 г.р., ст. Шелковская Шелковского района ЧИАССР.
886. МУРДАЛОВ АСЛАН МУСАЕВИЧ*, 02.01.1975 г.р., с. Урус-Мартан ЧИАССР.
887. МУРДАШЕВ ВАХИТ ЛАКАЕВИЧ*, 01.12.1955 г.р., г. Караганда Казахской ССР.
888. МУРЖАХАТОВ АДАМ ИСРАИЛОВИЧ*, 07.10.1982 г.р., с. Зандак Ножай-Юртовского района ЧИАССР.
889. МУРТАЗАЛИЕВ РУСЛАН МУСАЕВИЧ*, 09.01.1984 г.р., ст. Николаевская Наурского района Чеченской Республики.
890. МУРТАЗАЛИЕВА ЗАРА ХАСАНОВНА*, 04.09.1983 г.р., станица Наурская Чеченской Республики.
891. МУРТАЗОВ МАГОМЕД АБДУРАХМАНОВИЧ*, 07.02.1977 г.р., г. Грозный ЧИАССР.
892. МУРТУЗАЛИЕВ ЗУБАЙРУ ОМАРОВИЧ*, 23.11.1949 г.р., с. Леваши Левашинского р-на Республики Дагестан.
893. МУСАБЕКОВ РАГИМХАН ДУВАНБЕКОВИЧ*, 12.07.1972 г.р., с. Стальск Кизилюртовского района ДАССР.
894. МУСАЕВ АДЛАН АЛИЕВИЧ*, 20.11.1979 г.р., г. Грозный ЧИАССР.
895. МУСАЕВ АСЛАН РУСЛАНОВИЧ*, 22.10.1977 г.р., с. Гехи Урус-Мартановского района Чеченской Республики.
896. МУСАЕВ ДЖАМАЛ ХАВАЖИЕВИЧ*, 13.05.1985 г.р., ст. Ильиновская Грозненского района ЧИАССР.
897. МУСАЕВ ДОККИ ДОРШЕВИЧ*, 21.12.1970 г.р., пос. с/х 23 съезда КПСС Джездзинского района Карагандинской области Казахской ССР.
898. МУСАЕВ ИБРАГИМ ШЕРВАНИЕВИЧ*, 30.06.1974 г.р., с. Урус-Мартан ЧИАССР.
899. МУСАЕВ СУЛТАН САЙДБЕКОВИЧ*, 21.12.1981 г.р., с. Старые Атаги Грозненского района ЧИАССР.
900. МУСАЕВ УМАР ЗАЙДХАМЗАТОВИЧ*, 22.09.1982 г.р., с. Самашки Ачхой-Мартановского р-на ЧИАССР.
901. МУСАЛАЕВ ГУСЕЙН ХИЗРИЕВИЧ*, 18.05.1980 г.р., г. Махачкала ДАССР.
902. МУСАЛОВ ГАДЖИМУРАД ШАМИЛОВИЧ*, 28.02.1978 г.р., с. Согратль Гунибского района ДАССР.
903. МУСРАПИЛОВ АДАМ УВАЙСОВИЧ*, 08.10.1973 г.р., с. Гуни Веденского района ЧИАССР.
904. МУСХАНОВ АДАМ МОВЛДИЕВИЧ*, 24.09.1982 г.р., с. Урус-Матран Урус-Мартановского района ЧИАССР.
905. МУСХАНОВ МАГОМЕД МУСУЕВИЧ*, 28.05.1986 г.р., пос. Долинский Грозненского района ЧИАССР.
906. МУТАЕВ БИСЛАН РУСЛАНОВИЧ*, 25.07.1983 г.р., г. Урус-Мартан Урус-Мартановский район ЧИАССР.
907. МУТАЕВ ИСМАИЛ ПАТАХОВИЧ*, 24.06.1981 г.р., г. Гудермес ЧИАССР.
908. МУТАЛИПОВ АСХАБ АДАМОВИЧ*, 12.02.1967 г.р., с. Ца-Ведено Веденского района ЧИАССР.
909. МУТАШЕВ ОСМАН АБУБАКАРОВИЧ*, 08.08.1975 г.р., п. Маныч Ики-Бурульского района Республики Калмыкия.
910. МУТИЕВ ИСА АХМЕТОВИЧ*, 22.12.1985 г.р., с. Новотеречное Наурского района Чеченской Республики.
911. МУТУСХАНОВ МАГОМЕД ГАБАРОВИЧ*, 04.01.1968 г.р., г. Грозный ЧИАССР.
912. МУХАЕВ МЕХТИ МАХМУДОВИЧ*, 20.03.1958 г.р., с. Самашки ЧИАССР.
913. МУХАМЕДОВ НАЗАР МИДХАТОВИЧ*, 06.02.1970 г.р., с. Боз Бозского района Андижанской обл. Республики Узбекистан.
914. МУХАНИН ВЛАДИМИР ВАСИЛЬЕВИЧ*, 10.10.1972 г.р., г. Уфа.
915. МУХТАРОВ БЕСЛАН ВАХАЕВИЧ*, 16.02.1978 г.р., с. Урус-Мартан ЧИАССР.
916. МУХТАРОВ МАГОМЕД СИРАЖУТДИНОВИЧ*, 27.10.1960 г.р., с. Куппа Левашинского района Республики Дагестан.
917. МУЦАЕВ БЕКХАН АДАМОВИЧ*, 14.11.1987 г.р., с. Старая Сунжа ЧИАССР.
918. МУЦАЛХАНОВ МУССА МУСЛИМОВИЧ*, 01.11.1979 г.р., с. Урус-Мартан ЧИАССР.
919. МУЦАЛХАНОВ РИЗВАН МУСЛИМОВИЧ*, 14.11.1977 г.р., с. Танги-Чу Урус-Мартановского района ЧИАССР.
920. МУЦОЛЬГОВ ЗАУР МАГОМЕДОВИЧ*, 14.09.1981 г.р., г. Назрань Республики Ингушетия.
921. МЫЛЬНИКОВ АНАТОЛИЙ ВИКТОРОВИЧ*, 12.12.1946 г.р., г. Ивано-Франковск.
922. НАБИУЛЛИН МУХАММАД ГАЙНУЛЛОВИЧ*, 16.10.1979 г.р., п. Раевский Альшеевского района Республики Башкортостан.
923. НАГИМАТОВ СЕРГЕЙ ИСКАНДЫРОВИЧ*, 18.10.1977 г.р., с. Березовка Брединского района Челябинской области.
924. НАЖАЕВ ШАХ ХАЛИАРОВИЧ*, 20.01.1967 г.р., с. Надтеречное Надтеречного района ЧИАССР.
925. НАЗАРОВ ВЯЧЕСЛАВ ВИТАЛЬЕВИЧ*, 17.10.1970 г.р., г. Рубцовск Алтайского края.
926. НАКОНЕЧНЫЙ ИГОРЬ ЕВГЕНЬЕВИЧ*, 07.01.1966 г.р., г. Уфа Республики Башкортостан.
927. НАКРАЕВ ЭДИЛБЕК ЛЕМАЕВИЧ*, 02.08.1980 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
928. НАСИПОВ РИЗВАН АБДУКАДЫРОВИЧ*, 19.12.1978 г.р., с. Рубежное Наурского р-на ЧИАССР.
929. НАСУРОВ ВАЛИД ХАСМАГАМЕДОВИЧ*, 30.03.1982 г.р., г. Гудермес ЧИАССР.
930. НАСУХАНОВ ИСМАИЛ АХИЯТОВИЧ*, 26.08.1984 г.р., с. Надтеречное Надтереченского района ЧИАССР.
931. НАШАЕВ АЛИХАН АЛЬВИЕВИЧ*, 20.03.1980 г.р., с. Катыр-Юрт Ачхой-Мартановского района ЧИАССР.
932. НАШАЕВ УМАР РАМЗАНОВИЧ*, 25.04.1985 г.р., с. Ведено Веденского района ЧИАССР.
933. НЕВСКАЯ ОЛЬГА АЛЕКСАНДРОВНА*, 09.09.1978 г.р., г. Волжский Волгоградской области.
934. НЕДУЕВ РИЗВАН ИЛЬЯСОВИЧ*, 27.08.1966 г.р., с. Мескер-Юрт Шалинского района ЧИАССР.
935. НЕИЗВЕСТНЫЙ ИВАН АЛЕКСАНДРОВИЧ*, 14.02.1984 г.р., с. Эхаби Охинского района Сахалинской области.
936. НЕМЦЕВ СЕРГЕЙ ВАСИЛЬЕВИЧ*, 16.02.1985 г.р., г. Комсомольск-на-Амуре Хабаровского края.
937. НЕСМЕЯНОВ АНДРЕЙ АЛЕКСАНДРОВИЧ*, 31.05.1970 г.р., г. Миасс Челябинской области.
938. НЕСТЕРОВ ВЯЧЕСЛАВ АЛЕКСАНДРОВИЧ*, 10.04.1981 г.р., г. Таштагол Кемеровской области.
939. НЕСТЕРОВ СЕРГЕЙ АЛЕКСАНДРОВИЧ*, 03.03.1974 г.р., г. Котлас Архангельской области.
940. НИГОМАЕВ АЛЕКСЕЙ НИКОЛАЕВИЧ*, 26.03.1961 г.р., д. Гарюшка Куединского района Пермской области.
941. НИКИТИН СЕРГЕЙ ЮРЬЕВИЧ*, 07.05.1980 г.р., г. Ленинград.
942. НОВОЖИЛОВ АНДРЕЙ НИКОЛАЕВИЧ*, 02.03.1962 г.р., г. Дно Псковской области.
943. НУКАЕВ МАМЕД АХМЕДОВИЧ*, 12.10.1970 г.р., с. Чилгир Яшкульского района Республики Калмыкия.
944. НУКАЕВ ХАМЗАТ ВАХАЕВИЧ*, 05.07.1968 г.р., с. Дуба-Юрт Шалинского р-на ЧИАССР.
945. НУРГАЛИЕВ САЛАВАТ МАЛИКОВИЧ*, 20.04.1979 г.р., с. Суюндюк Бакалинского района Республики Башкирия.
946. НУРИЧЕВ АСЛАМБЕК АБУЯЗИТОВИЧ*, 15.08.1978 г.р., с. Пролетарское Грозненского района ЧИАССР.
947. НУРМАГОМЕДОВ ЗАКИР ХАМИДОВИЧ*, 04.01.1976 г.р., с. Кижани Ботлиховского района Республики Дагестан.
948. НУРМАГОМЕДОВ МАГОМЕД БАГАУТДИНОВИЧ*, 13.06.1979 г.р., с. Хаджалмахи Левашинского района Республика Дагестан.
949. НУРМУХАМЕТОВ ТАГИР ИЛЬДАРОВИЧ*, 10.11.1984 г.р., г. Казань Республики Татарстан.
950. НУЦАЛОВ АРСЕН МУХТАРПАШАЕВИЧ*, 04.01.1980 г.р., с. Казмааул Хасавюртовского р-на Республики Дагестан.
951. ОГАНЕСЯН ГРИГОРИЙ ГУРГЕНОВИЧ*, 24.04.1969 г.р., с. Эдиссия Курского района Ставропольского края.
952. ОЗДИЕВ ИБРАГИМ МАМУРИЕВИЧ*, 18.02.1989 г.р., с. Ведено Веденского района ЧИАССР.
953. ОЗДИЕВ ХАМИД НУРИДОВИЧ*, 04.01.1986 г.р., с. Ведено Веденского района ЧИАССР.
954. ОЗДИЕВ ХАСАН ХАМЗАТОВИЧ*, 01.12.1980 г.р., с. Терси Кайского района Красноярского края.
955. ОЗДОЕВ АДАМ МАГОМЕТОВИЧ*, 21.03.1980 г.р., г. Назрань ЧИАССР.
956. ОЗДОЕВ АЛИХАН МАГОМЕДОВИЧ*, 26.11.1977 г.р., г. Владикавказ РСО-Алания.
957. ОЗДОЕВ АСЛАН МУСТАФАЕВИЧ*, 31.07.1975 г.р., г. Владикавказ РСО-Алания.
958. ОМАРДИБИРОВ МУРАД МАГОМЕДОВИЧ*, 17.06.1972 г.р., г. Каспийск Республики Дагестан.
959. ОМЕЛЬЧЕНКО ОЛЕГ НИКОЛАЕВИЧ*, 09.12.1974 г.р., г. Азов Ростовской области.
960. ОПАРИН ДЕНИС НИКОЛАЕВИЧ*, 19.04.1979 г.р., г. Мончегорск Мурманской области.
961. ОРЗУМИЕВ ИЛЕС АБУСУЛТАНОВИЧ*, 18.03.1979 г.р., с. Нижний Герзель Гудермесского района ЧИАССР.
962. ОСМАЕВ АДАМ ЖАМАЛАЙЛОВИЧ*, 12.11.1978 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
963. ОСМАНОВ МАГОМЕД АБУТАЛИМОВИЧ*, 10.02.1962 г.р., с. Губден Карабудахкентского района Республики Дагестан.
964. ОСУПОВ АЛЬБЕРТ АБУЕЗИТОВИЧ*, 12.07.1985 г.р., с. Ведено Веденского района ЧИАССР.
965. ОТЕГЕНОВ ТИМУР РЕЙЗАЕВИЧ*, 20.06.1973 г.р., с. Иргаклы Степновского района Ставропольского края.
966. ОТЕМИСОВ ЭСМАНБЕТ ЯМАКОВИЧ*, 14.06.1967 г.р., с. Червленные Буруны Ногайского района Республики Дагестан.
967. ОТЕПОВ НАРИМАН ОРАЗБИЕВИЧ*, 18.04.1976 г.р., с. Иргаклы Степновского района Ставропольского края.
968. ОХАЕВ ЛЕМ САЛМАНОВИЧ*, 07.07.1974 г.р., г. Грозный ЧИАССР.
969. ОЧАРХАДЖИЕВ ДЖАБРАИЛ НАИМСОЛТАЕВИЧ*, 07.01.1982 г.р., с. Ишхой-Юрт Гудермесского района ЧИАССР.
970. ОЧЕРХАДЖИЕВ АСЛАН ИБРАГИМОВИЧ*, 26.08.1979 г.р., г. Грозный ЧИАССР.
971. ПАВЛИКОВ ЭДУАРД ВИКТОРОВИЧ*, 02.03.1972 г.р., г. Златоуст Челябинской области.
972. ПАДАЕВ ИСЛАМ МУХАМЕТСАЛЫЕВИЧ*, 30.03.1985 г.р., с. Чонтаул Кизилюртовского района Республики Дагестан.
973. ПАК АЛЕКСАНДР АЛЕКСАНДРОВИЧ*, 20.06.1979 г.р., с. Стародубское Долинского р-на Сахалинской области.
974. ПАНИН АНДРЕЙ КОНСТАНТИНОВИЧ*, 22.06.1980 г.р., г. Норильск Красноярского края.
975. ПЕТРИЧЕНКО ДМИТРИЙ АЛЕКСАНДРОВИЧ*, 26.09.1979 г.р., г. Дрезден Республика Германия.
976. ПИВОВАРОВ ДМИТРИЙ ВИТАЛЬЕВИЧ*, 04.10.1974 г.р., г. Гудермес ЧИАССР.
977. ПИДИЕВ АДАМ МУСТАФАЕВИЧ*, 16.12.1979 г.р., ст. Орджоникидзевская ЧИАССР.
978. ПИРОВ ИСКАНДАР КУРБОНАЛИЕВИЧ*, 31.03.1984 г.р., с. Курбаншахи Восейского района Кулябской области Республики Таджикистан.
979. ПЛЮСНИН ДЕНИС АЛЕКСАНДРОВИЧ*, 05.04.1991 г.р., д. Середина Юрьянского района Кировской области.
980. ПОЗДЯЕВ АЛЕКСЕЙ НИКОЛАЕВИЧ*, 30.03.1963 г.р., с. Ст. Турдаки Кочкуровского района Республики Мордовия.
981. ПОЛИКАРПОВ ВЛАДИМИР СЕРГЕЕВИЧ*, 16.04.1976 г.р., с. Косой Брод Полевского района Свердловской области.
982. ПОЛЫНЦЕВ ГРИГОРИЙ АЛЕКСАНДРОВИЧ*, 28.11.1979 г.р., г. Нукус Республики Каракалпакия.
983. ПОНАРЬИН МАКСИМ АЛЕКСАНДРОВИЧ*, 15.11.1976 г.р., г. Будапешт Венгерской Народной Республики.
984. ПОПОВ МИХАИЛ КОНСТАНТИНОВИЧ*, 06.08.1977 г.р., г. Новосибирск.
985. ПОТЕХИН ЕВГЕНИЙ ПЕТРОВИЧ*, 26.03.1978 г.р., п. Мохнатушка г. Барнаула Алтайского края.
986. ПРИВЕДЕННАЯ ЮЛИЯ АНАТОЛЬЕВНА*, 23.05.1974 г.р., г. Стерлитамак Башкирской АССР.
987. ПРОСВЕТОВ ЕВГЕНИЙ ВИКТРОВИЧ*, 13.08.1976 г.р., г. Комсомольск-на-Амуре Хабаровского края.
988. ПРОЦЕНКО ВЯЧЕСЛАВ НИКОЛАЕВИЧ*, 23.09.1958 г.р., ст. Октябрьская Павловского района Краснодарского края.
989. ПРОЩАВАЕВ ВЯЧЕСЛАВ ВИКТОРОВИЧ*, 01.07.1973 г.р., пос. Сокол Долинского р-на Сахалинской области.
990. ПУХТЕЕВ АЛЕКСЕЙ АЛЕКСАНДРОВИЧ*, 22.08.1982 г.р., д. Большуха Кировского района Калужской обл.
991. РАБАДАНОВ РИЗВАНУЛЛА МАММАЕВИЧ*, 01.01.1972 г.р., с. Гинти Акушинского района ДАССР.
992. РАДЧЕНКО ВЛАДИМИР ГЕННАДЬЕВИЧ*, 06.12.1958 г.р., с. Дмитриевка Ижморского района Кемеровской области.
993. РАЖАПОВ РУСЛАН АБДУЛ-ВАХИДОВИЧ*, 28.08.1966 г.р., с. Бачи-Юрт Шалинского р-на ЧИАССР.
994. РАЖИПОВ МУСТАПА МАГОМЕДШАПИЕВИЧ*, 02.07.1965 г.р., с. Карамахи Буйнакского района Республики Дагестан.
995. РАЗЗАКОВ ХАФИЗ ХАМЗАЕВИЧ*, 05.09.1975 г.р., ст. Зиадин Пахтачийского Самаркандской области Республики Узбекистан.
996. РАКС НАДЕЖДА ГЕОРГИЕВНА*, 13.01.1973 г.р., г. Ровно Республики Украина.
997. РАСКОВАЛОВ АЛЕКСЕЙ ВЯЧЕСЛАВОВИЧ*, 21.01.1964 г.р., г. Верхняя Пышма Свердловской области.
998. РАСУЕВ АДАМ ИБРАГИМОВИЧ*, 30.12.1986 г.р., с. Урус-Мартан Урус-Мартановского района Чеченской Республики.
999. РАФИКОВ ДИАС АЛЬБЕРДОВИЧ*, 31.05.1986 г.р., г. Казань.
1000. РАХИМОВ АРСЕН ХАМЗАТОВИЧ*, 03.05.1978 г.р., г. Грозный ЧИАССР.
1001. РЕВТОВ ПАВЕЛ ИВАНОВИЧ*, 05.01.1979 г.р., г. Кустанай Кахахской ССР.
1002. РОЗОВ ДМИТРИЙ ВАЛЕРЬЕВИЧ*, 25.08.1982 г.р., г. Ленинград.
1003. РОМАНОВА ЛАРИСА ВАЛЕРЬЕВНА*, 23.04.1974 г.р., г. Москва.
1004. РЯДИНСКИЙ ВИТАЛИЙ НИКОЛАЕВИЧ*, 15.08.1976 г.р., п. Никитинка Боровского района Кустанайской области Казахской ССР.
1005. САБИРОВ АЗАТ ФАНИСОВИЧ*, 06.02.1987 г.р., г. Брежнев ТАССР (г. Набережные Челны Республики Татарстан).
1006. САБИТОВ РАФАЭЛЬ РИФГАТОВИЧ*, 18.06.1985 г.р., г. Казань Республики Татарстан.
1007. САБИТОВ РАФИС РИФГАТОВИЧ*, 26.07.1978 г.р., г. Казань.
1008. САВЕЛЬЕВ ЕВГЕНИЙ АНАТОЛЬЕВИЧ*, 05.01.1984 г.р., г. Белорецк.
1009. САВЧЕНКО ИГОРЬ АНАТОЛЬЕВИЧ*, 03.05.1972 г.р., пос. Лазаревское, г. Сочи Краснодарского края.
1010. САГАИПОВ ШАМХАН ШАРПУДИНОВИЧ*, 03.07.1977 г.р., с. Чири-Юрт Шалинского района Чеченской Республики.
1011. САГАРИЕВ РУСТАМ ШАМСУДИНОВИЧ*, 16.11.1980 г.р., г. Грозный ЧИАССР.
1012. САДАЕВ МАГОМЕД ХАМЗАТОВИЧ*, 21.08.1975 г.р., г. Грозный ЧИАССР.
1013. САДУЕВ СУЛТАН ШАХРАДИЕВИЧ*, 07.03.1968 г.р., г. Аргун Чеченской Республики.
1014. САДЫКОВ АРТУР ХАКИМОВИЧ*, 12.03.1979 г.р., г. Кизляр ДАССР.
1015. САДЫКОВ РАМЗАН РИЗВАНОВИЧ*, 30.08.1976 г.р., г. Грозный Чеченской Республики.
1016. САЗОНОВ ЕВГЕНИЙ АЛЕКСАНДРОВИЧ*, 28.12.1976 г.р., с. Орой Акшинского района Читинской области.
1017. САИДБЕКОВ МАГОМЕД ГАДЖИЕВИЧ*, 06.01.1949 г.р., с. Эчеда Цумадинского района Республики Дагестан.
1018. САИДОВ АСЛАН ХАМЗАТОВИЧ*, 19.12.1988 г.р., с. Автуры ЧИАССР.
1019. САИДОВ МАГОМЕД РАМЗАНОВИЧ*, 21.12.1981 г.р., с. Автуры Шалинского района ЧИАССР.
1020. САИДОВ МАХМУД СУЛЕЙМАНОВИЧ*, 27.10.1978 г.р., ст. Старощедринская Шелковского района ЧИАССР.
1021. САИЕВ ИБРАГИМ БЕКСАЛТАНОВИЧ*, 29.12.1982 г.р., пос. Новогрозненский Гудермесского района ЧИАССР.
1022. САИЕВ ЛЕМА МАЗЛАКОВИЧ*, 18.01.1969 г.р., г. Элиста Калмыкской АССР.
1023. САИТОВ РАСУЛ АХМЕДОВИЧ*, 04.02.1985 г.р., с. Ведено Веденского района ЧИАССР.
1024. САЙБАТАЛОВ МАРАТ ТЕМЕРБУЛАТОВИЧ*, 05.05.1972 г.р., г. Тюмень.
1025. САЙГИДОВ САЙГИД НУРМАГОМЕДОВИЧ*, 16.07.1979 г.р., с. Сильди Цумадинского района Республики Дагестан.
1026. САЙДАЕВ БАДРУДИ АЛАУДЫЕВИЧ*, 05.12.1972 г.р., с. Хиди-Хутор Ножай-Юртовского района ЧИАССР.
1027. САЙДАЕВ ХАСАН ГОЦУЕВИЧ*, 26.08.1956 г.р., с. Ново-Павловка Кызыл-Аскеровского района Киргизской ССР.
1028. САЙДАЛИЕВ АЛИХАН ОБУСУПЬЯНОВИЧ*, 21.11.1976 г.р., с. Энгеной Ножай-Юртовского района ЧИАССР.
1029. САЙДУЛАЕВ АДНАН ИСАЕВИЧ*, 28.08.1977 г.р., с. Алхан-Кала Грозненского района Чеченской Республики.
1030. САЙДУЛАЕВ АРТУР ИСАЕВИЧ*, 12.12.1983 г.р., с. Алхан-Кала Грозненского района ЧИАССР.
1031. САЙДУЛАЕВ АСЛАНБЕК ЗАУДИЕВИЧ*, 06.11.1976 г.р., с. Майртуп Шалинского района ЧИАССР.
1032. САЙДУЛАЕВ МУСА ЗУДИНОВИЧ*, 01.03.1972 г.р., с. Майртуп Шалинского района ЧИАССР.
1033. САЙДУМОВ МУСА САЛАМУЕВИЧ*, 05.12.1976 г.р., с. Дышне-Ведено Веденского района ЧИАССР.
1034. САЙТАМУЛОВ АЛИ БАЙТЕМИРОВИЧ*, 02.08.1977 г.р., г. Хасавюрт Республика Дагестан.
1035. САЛАВАТОВ ШАМСУДИН ДАДАШЕВИЧ*, 30.01.1971 г.р., с. Автуры Шалинского р-на ЧИАССР.
1036. САЛАМОВ БАЙ-АЛИ САИД-ЭМИЕВИЧ*, 11.06.1987 г.р., с. Курчалой Шалинского района ЧИАССР.
1037. САЛАТАЕВ АБУБАКАР БАВАДИЕВИЧ*, 13.09.1969 г.р., с. Ялхой-Мохк Ножай-Юртовского района ЧИАССР.
1038. САЛАТАЕВ ИБРАГИМ САЛАМБЕКОВИЧ*, 23.06.1977 г.р., г. Аргун ЧИАССР.
1039. САЛАТАЕВ ИЛЬЯС ДАЛАМБЕКОВИЧ*, 15.03.1972 г.р., г. Гудермес ЧИАССР.
1040. САЛИХОВ АЛИСУЛТАН САПИЮЛАЕВИЧ*, 06.11.1969 г.р., Гунибский район ДАССР.
1041. САЛИХОВ БАГАУТДИН САПИЮЛАЕВИЧ*, 30.03.1972 г.р., г. Буйнакск ДАССР.
1042. САЛМУРЗАЕВ МАГОМЕД ШАМАНОВИЧ*, 27.12.1980 г.р., х. Семечный Дубовского района Ростовской области.
1043. САЛПАГАРОВ ДАХИР МЕКЕРОВИЧ*, 04.01.1964 г.р., аул Джегута Усть-Джегутского района Карачаево-Черкесской Республики.
1044. САЛПАГАРОВ МУРАТ КОРНЕЕВИЧ*, 18.09.1965 г.р., ст. Сторожевая Зеленчукского района Карачаево-Черкесской Республики.
1045. САЛПАГАРОВ ХЫЗЫР МЕКЕРОВИЧ*, 08.01.1959 г.р., а. Джегута Усть-Джегутинского района Карачаево-Черкесской Республики.
1046. САЛСАНОВ УМАР САЛМАНОВИЧ*, 20.07.1976 г.р., с. Валерик Ачхой-Мартановского района Чечено-Ингушской АССР.
1047. САМБИЕВ АЙНДИ МУТАЕВИЧ*, 16.12.1977 г.р., с. Улус-Керт Советского р-на ЧИАССР.
1048. САМБИЕВ ИСА СОНТАЕВИЧ*, 24.05.1964 г.р., с. Липовка Урус-Мартановского района ЧИАССР.
1049. САМБИЕВ МОВСАР МУТАЕВИЧ*, 28.02.1984 г.р., с. Улус-Керт Советского р-на ЧИАССР.
1050. САНГАРИЕВ ЗЕЛИМХАН РАМЗАНОВИЧ*, 16.08.1986 г.р., с. Уштобе Каратальского района Талды-Курганской области КазССР.
1051. САНГАРИЕВ РУСЛАН АБУСОЛТОВИЧ*, 13.05.1977 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1052. САНГИРАЕВ САЛАМБЕК ШАРПУДИНОВИЧ*, 13.10.1988 г.р., с. Новые-Атаги Шалинского района ЧИАССР.
1053. САРАЛИЕВ АЛИ УВАЙСОВИЧ*, 27.07.1970 г.р., с. Гехи Урус-Мартановского р-на Чеченской Республики.
1054. САРДАЛОВ АДАМ АХМЕДОВИЧ*, 31.07.1982 г.р., с. Троицкое Целинного района Калмыцкой АССР.
1055. САРДАЛОВ МАМЕД МЕРЖУЕВИЧ*, 22.04.1972 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1056. САРДАЛОВ СУЛИМАН ТАУСОВИЧ (САРДАЛОВ СУЛЕЙМАН ТАУСОВИЧ)*, 08.12.1986 г.р., г. Грозный ЧИАССР (1986 г.).
1057. САРДАЛОВ УМАР АХМЕДОВИЧ*, 18.07.1984 г.р., пос. Первомайское Яшкульского района Калмыкской АССР.
1058. САРИЕВ УМАР ВЛАДИМИРОВИЧ*, 03.07.1966 г.р., с. Усть-Джегута Карачаево-Черкесской Республики.
1059. САТАБАЕВ ТИМУР ВИСИТАЕВИЧ*, 30.07.1976 г.р., с. Урус-Мартан Урус-Мартановского р-на ЧИАССР.
1060. САТИАДЖИЕВ МУЖАИД АЛЕВДИНОВИЧ (САТИ-АДЖИЕВ МУЖАИД АЛИРДИНОВИЧ; САТИ-АДЖИЕВ МУЖАИД АЛИВДИНОВИЧ)*, 05.04.1959 г.р., г. Хасавюрт ДАССР.
1061. СВЕТЛИЧНЫЙ ЮРИЙ ВАЛЕРЬЕВИЧ*, 02.04.1980 г.р., г. Киселевск Кемеровской области.
1062. СЕЛИМОВ АСЛАНБЕК СЛАВДИНОВИЧ*, 28.04.1975 г.р., с. Новосельское Хасавюртовского района ДАССР.
1063. СЕМАНОВ АЛЕКСЕЙ СЕРГЕЕВИЧ*, 29.11.1973 г.р., Емецкий с/с Холмогорского района Архангельской области.
1064. СЕНИН ИГОРЬ МИХАЙЛОВИЧ*, 22.09.1965 г.р., г. Москва.
1065. СЕРИТХАНОВ АДАМ ЗАЙНАЛБЕКОВИЧ*, 26.05.1984 г.р., с. Джалагаш Джалагашского района Кзыл-Ординской области Казахской АССР.
1066. СЕРСУЛТАНОВ АДАМ АХМЕДОВИЧ*, 02.01.1985 г.р., г. Грозный ЧИАССР.
1067. СЕТОВ АСКЕР НУРБИЕВИЧ*, 13.09.1982 г.р., аул Шовгеновский Шовгеновского района Республики Адыгея.
1068. СИГАЧЕВ ДМИТРИЙ ИГОРЕВИЧ*, 10.02.1977 г.р., г. Москва.
1069. СИДЕЛЬНИК ВЛАДИМИР ЕВГЕНЬЕВИЧ*, 18.02.1962 г.р., г. Армавир Краснодарского края.
1070. СИНЯЧКИН АЛЕКСЕЙ МИХАЙЛОВИЧ*, 12.08.1986 г.р., деревня Алешино Касимовского района Рязанской обл.
1071. СИРАЖДИНОВ ЛЕЧИ СУЛТАНОВИЧ*, 26.02.1976 г.р., с. Нижний Герзель Гудермесского района ЧИАССР.
1072. СИТАЕВ ЕВГЕНИЙ АЛЕКСАНДРОВИЧ*, 14.04.1983 г.р., станица Смоленская Северского р-на Краснодарского края.
1073. СИТНИКОВ ЮРИЙ АЛЕКСАНДРОВИЧ*, 31.10.1971 г.р., с. Филипповка Кунгурского района Пермской обл.
1074. СКВОРЦОВ ГЕННАДИЙ ГЕННАДЬЕВИЧ*, 09.03.1979 г.р., г.п. Чунский Иркутской области.
1075. СКЛЯР ВАЛЕРИЙ ВАСИЛЬЕВИЧ*, 17.09.1965 г.р., г. Фрунзе Республики Киргизия.
1076. СКОЛОТЯН РОМАН ПАВЛОВИЧ*, 07.10.1978 г.р., г. Березняки Пермской области.
1077. СКОРОВ ЕВГЕНИЙ СЕРГЕЕВИЧ*, 13.04.1987 г.р., г. Иркутск.
1078. СМОРОДНИКОВ НИКОЛАЙ ВИКТОРОВИЧ*, 14.07.1978 г.р., п. Карымское Карымского р-на Читинской обл.
1079. СОБРАЛИЕВ ХАМПАША ХАМЗАТОВИЧ*, 05.01.1972 г.р., с. Ца-Ведено Веденского района ЧИАССР.
1080. СОВМИЗ РУСЛАН АСЛАНОВИЧ*, 16.06.1983 г.р., а. Козет Тахтамукайского района Республики Адыгея.
1081. СОКОЛОВ ВАЛЕРИЙ АНАТОЛЬЕВИЧ*, 22.06.1966 г.р., г. Рыбинск.
1082. СОКОЛОВ ИГОРЬ ЛЕОНИДОВИЧ*, 05.09.1970 г.р., г. Тверь.
1083. СОЛСАНОВ МАМЕД АХМЕДОВИЧ*, 29.06.1979 г.р., с. Чернокозово Наурского района ЧИАССР.
1084. СОЛТАМУРАДОВ РУСТАМ БАТЫРСУЛТАНОВИЧ*, 13.03.1978 г.р., ст. Гребенская Шелковского района ЧИАССР.
1085. СОЛТАХАНОВ УМАР АСЛАМБЕКОВИЧ*, 03.01.1982 г.р., с. Лиман Лиманского района Астраханской области.
1086. СОЛТМУРАДОВ ИСЛАМ АРБИЕВИЧ*, 09.07.1977 г.р., с. Мескер-Юрт Шалинского района Чеченской Республики.
1087. СОЛТУХАНОВ ХИЗИР БУВАЙСАРИЕВИЧ*, 23.03.1983 г.р., с. Автуры Шалинского района ЧИАССР.
1088. СОРОКИН СЕРГЕЙ АНАТОЛЬЕВИЧ*, 23.01.1975 г.р., г. Вязьма Смоленской области.
1089. СОСЛАМБЕКОВ ШАМИЛЬ ШАХИДОВИЧ*, 28.03.1981 г.р., г. Грозный ЧИАССР.
1090. СОЮПОВ МУСЛИМ РАМЗАНОВИЧ*, 20.01.1982 г.р., с. Закон-Юрт Ачхой-Мартановского района ЧИАССР.
1091. СТРУГАНОВ ВИЛОР ВИКТОРОВИЧ*, 24.09.1962 г.р., г. Мариинск Кемеровской области.
1092. СУГАИПОВ АРСЕН ПАЗЛУДИНОВИЧ*, 11.09.1982 г.р., с. Племзавод Ногайского района ДАССР.
1093. СУГАТИЕВ АНЗОР ИСАЕВИЧ*, 17.01.1979 г.р., г. Гудермес ЧИАССР.
1094. СУГАЮНОВ ГАДЕЛЬ МАХМУДЖАНОВИЧ*, 08.04.1985 г.р., г. Азнакаево Республики Татарстан.
1095. СУЛАЙМАНОВ САЛМАН АЮБОВИЧ*, 24.08.1984 г.р., с. Ленинаул Казбековского р-на Республики Дагестан.
1096. СУЛЕБАНОВ ДЖАБРАИЛ АКАЕВИЧ*, 14.10.1960 г.р., с. Карамахи Буйнакского района ДАССР.
1097. СУЛЕЙМАНОВ АСХАБ АБДУЛВАХИДОВИЧ*, 21.09.1985 г.р., с. Успеновка Ленгерского района Чимкентской области КазССР.
1098. СУЛЕЙМАНОВ АХМЕД АЛИЕВИЧ*, 04.10.1974 г.р., с. Бачи-Юрт Шалинского района ЧИАССР.
1099. СУЛЕЙМАНОВ ВАЛИД АЛАВДИНОВИЧ*, 27.07.1974 г.р., с. Тазен-Кала Веденского района ЧИАССР, возможно г. Грозный.
1100. СУЛЕЙМАНОВ МАЙР-АЛИ МАЙРБЕКОВИЧ*, 19.05.1984 г.р., с. Автуры Шалинского района ЧИАССР.
1101. СУЛЕЙМАНОВ РУСЛАН ХАМИДОВИЧ*, 17.11.1968 г.р., г. Шали Шалинского района Чеченской Республики.
1102. СУЛЕЙМАНОВ РУСТАМ ВИСРАИЛОВИЧ*, 18.06.1987 г.р., с. Нурадилова Хасавюртовского района ДАССР.
1103. СУЛЕЙМАНОВ ХУСЕЙН УАЙСОВИЧ*, 12.08.1977 г.р., г. Грозный ЧИАССР.
1104. СУЛЕМАНОВ СУЛТАН ВАХАЕВИЧ*, 30.04.1977 г.р., с. Гойты Урус-Мартановского района Чеченской Республики.
1105. СУЛИМАНОВ АДАМ АЮБОВИЧ*, 19.02.1964 г.р., с. Шали ЧИАССР.
1106. СУЛИМАНОВ ШАРПУДИ ВАХАЕВИЧ*, 30.06.1966 г.р., с. Сержень-Юрт Шалинского района ЧИАССР.
1107. СУЛТАНГЕРИЕВ БЕСЛАН АДЛАНОВИЧ*, 26.09.1987 г.р., с. Урус-Мартан ЧИАССР.
1108. СУЛТАНМУРАДОВ МУСЛИМ АБДУРАХМАНОВИЧ*, 26.01.1987 г.р., с. Ахар Новолакского района ДАССР.
1109. СУЛТАНОВ АСЛАН МАГОМЕТОВИЧ*, 11.07.1980 г.р., ст. Ассиновская Сунженского района ЧИАССР.
1110. СУЛТАНОВ ВАХА МАГОМЕДОВИЧ*, 04.09.1985 г.р., ст. Ассиновская Сунженского района ЧИАССР.
1111. СУЛТАНОВ МУССА МОВСАРОВИЧ*, 11.11.1979 г.р., с. Мескер-Юрт Шалинского района Чеченской Республики.
1112. СУЛТАНОВ ХАЛИД АХМЕДОВИЧ*, 01.12.1982 г.р., с. Майское Сырдарьинского района Кзыл-Ординской области.
1113. СУЛТУХАНОВ УМАР САЙД-ХАМЗАТОВИЧ*, 27.07.1983 г.р., г. Грозный ЧИАССР.
1114. СУНАЕВ МАХМУД АБДУЛБАСИРОВИЧ*, 27.07.1963 г.р., с. В. Казанище Буйнакского района Республики Дагестан.
1115. СУНГУРОВ АБДУРАХМАН ЯНУРОВИЧ*, 07.12.1974 г.р., с. Хуна Лакского района ДАССР.
1116. СУСАРИЕВ АРСАН АЛАУДИНОВИЧ*, 17.03.1976 г.р., с. Серноводское Сунженского района Чеченской Республики.
1117. СУСЛИКОВ АЛЕКСАНДР ВЛАДИМИРОВИЧ*, 24.01.1958 г.р., г. Москва.
1118. СУСХАНОВ ИСЛАМ РУСЛАНОВИЧ*, 30.11.1984 г.р., г. Грозный ЧИАССР.
1119. СУЮПОВ УСМАН АЛЬВИЕВИЧ*, 20.07.1974 г.р., с. Гехи-Чу Урус-Мартановского района ЧИАССР.
1120. СЫСКЕВИЧ ДМИТРИЙ ВЛАДИМИРОВИЧ*, 16.06.1972 г.р., г. Томск.
1121. ТАВГАЗОВ СОСЛАН АРАМОВИЧ*, 06.09.1982 г.р., с. Коста-Хетагурова Карачаевского района Карачаево-Черкесской Республики.
1122. ТАВСУЛТАНОВ ИСА АХМЕДОВИЧ*, 19.10.1987 г.р., пос. Рассвет Ленинского р-на Волгоградской обл.
1123. ТАВСУЛТАНОВ САИД СЕЛИМ-АЛИМОВИЧ*, 27.06.1976 г.р., с. Ачхой-Мартан ЧИАССР.
1124. ТАЗАБАЕВ ЛЕЧИ СУЛТАНОВИЧ*, 20.05.1986 г.р., с. Ведено Веденского района ЧИАССР.
1125. ТАЗУЕВ САЙДИ ПАДИШАХОВИЧ*, 20.01.1952 г.р., с. Константино Вишневский район Акмолинской области Казахской ССР.
1126. ТАЗУРКАЕВ АХМЕД САЙДУЛАЕВИЧ*, 04.07.1980 г.р., с. Ачхой-Мартан ЧИАССР.
1127. ТАЗУРКАЕВ ОЛХАЗАР АБДУРОХМАНОВИЧ*, 08.03.1966 г.р., с. Катыр-Юрт Ачхой-Мартановского района ЧИАССР.
1128. ТАЙМАСОВ МАГОМЕДШАРИП АБДУЛМУСЛИМОВИЧ*, 22.04.1975 г.р., с. Губден Карабудахкентского района Республики Дагестан.
1129. ТАЙМАСХАНОВ РИЗВАН ТАГИРОВИЧ*, 10.04.1979 г.р., г. Гудермес ЧИАССР.
1130. ТАЙМАСХАНОВА ФАТИМА ДАНИЛБЕКОВНА*, 28.04.1973 г.р., г. Аргун Шалинского района ЧИАССР.
1131. ТАЙСУМОВ РИЗВАН БАЛАВДИЕВИЧ*, 06.11.1979 г.р., с. Ялхой-Мохк Курчалоевского района ЧИАССР.
1132. ТАЙСУМОВ ХИЗИР ХУСАИНОВИЧ*, 27.02.1983 г.р., г. Грозный ЧИАССР.
1133. ТАКАЕВ МОВСАР АРБИЕВИЧ*, 03.08.1982 г.р., г. Грозный ЧИАССР.
1134. ТАЛГАЕВ ИМРАН ШИРВАНИЕВИЧ*, 20.08.1971 г.р., г. Урус-Мартан ЧИАССР.
1135. ТАЛХАДОВ РОМАН ХАСБУЛАТОВИЧ*, 28.12.1968 г.р., х. Клинков станицы Мекенской Наурского района ЧИАССР.
1136. ТАЛХИГОВ ЗАУРБЕК ЮНУСОВИЧ*, 22.07.1977 г.р., с. Шали Шалинского района ЧИАССР.
1137. ТАМИМДАРОВ ШАМИЛ ГАМБАРОВИЧ*, 12.08.1958 г.р., с. Сюльте Илишевского района Республики Башкортостан.
1138. ТАРАМОВ АДАМ АПТИЕВИЧ*, 05.01.1975 г.р., с. Старые Атаги Грозненского района ЧИАССР.
1139. ТАРАСУНОВ МУРАДИН ИОСИФОВИЧ*, 29.03.1972 г.р., а. Псыж Прикубанского района Ставропольского края.
1140. ТАРМАЛИЕВ АСЛАНБЕК МОВЛИДОВИЧ*, 12.08.1977 г.р., с. Катыр-Юрт Ачхой-Мартановского района ЧИАССР.
1141. ТАСАЕВ МАГОМЕД СЕРГЕЕВИЧ*, 05.02.1987 г.р., с. Сельментаузен Веденского района ЧИАССР.
1142. ТАСУЕВ АХМЕД АБДУЛСАИТОВИЧ*, 11.11.1980 г.р., г. Грозный ЧИАССР.
1143. ТАСУЕВ ИЛЬЯС ХАСАНОВИЧ*, 16.05.1979 г.р., с. Советское Приозерного района Республики Калмыкии.
1144. ТАТАЕВ АБДУРАХМАН ШАМИЛЬЕВИЧ*, 30.06.1963 г.р., с. Курчалой Шалинского района ЧИАССР.
1145. ТАТАЕВ АСЛАН ШАМИЛЬЕВИЧ*, 29.01.1971 г.р., с. Курчалой Шалинского района ЧИАССР.
1146. ТАТАЕВ АТА АБАКАРОВИЧ*, 10.12.1971 г.р., г. Махачкала ДАССР.
1147. ТАТАЕВ ГУСЕЙН ХАМЗАТОВИЧ*, 16.01.1977 г.р., с. Османюрт Хасавюртовского района ДАССР.
1148. ТАТАЕВ ДАУР ЮСУПОВИЧ*, 29.06.1976 г.р., с. Дойкура-Эвл Грозненского района ЧИАССР.
1149. ТАТАЕВ ИМРАН ЛЕЧАЕВИЧ*, 20.10.1986 г.р., с. Ачхой-Мартан ЧИАССР.
1150. ТАТАЕВ ТУРПАЛ РУСЛАНОВИЧ*, 09.10.1980 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1151. ТАТАЛОВ ХАСАН ЛОМАЛИЕВИЧ*, 03.08.1970 г.р., с. Степное Гудермесского района ЧИАССР.
1152. ТАУШЕВ АРСЛАН КАДРАЛИЕВИЧ*, 18.06.1973 г.р., ст. Шелковская ЧИАССР.
1153. ТАШАЕВ АРБИ ИМАЛИЕВИЧ*, 16.03.1976 г.р., г. Гудермес ЧИАССР.
1154. ТАШУЕВ РУСЛАН АСЛАМБЕКОВИЧ*, 29.11.1979 г.р., с. Автуры Шалинского района ЧИАССР.
1155. ТЕБЕКОВ ЭЖЕР МИХАЙЛОВИЧ*, 07.01.1986 г.р., с. Бельтир Кош-Агачского р-на Алтайского края.
1156. ТЕГАЕВ АСЛАН УВАЙСОВИЧ*, 26.12.1984 г.р., с. Котлован Удомельского района Калининской области РФ.
1157. ТЕГАЕВ ТАМЕРЛАН УМАР-ЭЛИЕВИЧ*, 25.09.1980 г.р., с. Алхан-Кала Грозненского р-на ЧИАССР.
1158. ТЕКЕЕВ ЭНВЕР ХАСАНОВИЧ*, 05.11.1963 г.р., с. Садовое Киргизской ССР.
1159. ТЕМИРБИЕВ МАХМУД ГУДАБЕРТОВИЧ*, 13.09.1979 г.р., г. Владикавказ Республики Северная Осетия – Алания.
1160. ТЕМИРБИЕВ МОВСАР АБДУЛ-ВАГАПОВИЧ*, 07.12.1977 г.р., г. Владикавказ Республики Северная Осетия-Алания.
1161. ТЕМИРБУЛАТОВ САЛМАН САИДОВИЧ*, 19.12.1972 г.р., пос. Новогрозный Гудермесского района ЧИАССР.
1162. ТЕМИРБУЛАТОВ СУЛТУМБЕК СУЛТАНОВИЧ*, 04.02.1979 г.р., с. Шали Шалинского района ЧИАССР.
1163. ТЕМИРСУЛТАНОВ АРСЕН ЗУВАДИЕВИЧ*, 10.08.1988 г.р., г. Хасавюрт ДАССР.
1164. ТЕМИРСУЛТАНОВ ВАХА АБДРАХМАНОВИЧ*, 20.02.1979 г.р., с. Уманцево Саринского района Калмыцкой АССР.
1165. ТЕМИРСУЛТАНОВ ИДРИС РАМЗАНОВИЧ*, 14.10.1978 г.р., с. Суворов-Юрт Гудермесского района ЧИАССР.
1166. ТЕМИРСУЛТАНОВ ХАМЗАТ АБДРАХМАНОВИЧ*, 11.05.1979 г.р., с. Октябрьское Шалинского района ЧИАССР.
1167. ТЕПСАЕВ ХУСЕЙН ВАГИДОВИЧ*, 01.04.1967 г.р., с. Гойты Урус-Мартановского района ЧИАССР.
1168. ТЕРХОЕВ ЗАУР ВАХАЕВИЧ*, 17.02.1990 г.р., ст. Орджоникидзевская Сунженского района ЧИАССР.
1169. ТИЛИЕВ ИСА ХАМЗАТОВИЧ*, 24.03.1975 г.р., г. Гудермес ЧИАССР.
1170. ТИМАЕВ ОСМАН РАМАЗАНОВИЧ*, 21.11.1983 г.р., с. Покровское Хасавюртовского района Республики Дагестан.
1171. ТИМАРБУЛАТОВ СУЛЕЙМАН АХЪЯДОВИЧ*, 19.11.1979 г.р., с. Катар-Юрт Ачхой-Мартановского района ЧИАССР.
1172. ТИМЕРБУЛАТОВ МЕХИД МАГОМЕДОВИЧ*, 06.05.1970 г.р., с. Кади-Юрт Гудермесского района Чеченской Республики.
1173. ТИМИРБУЛАТОВ САЛАУДИН ХАСМАГАМАДОВИЧ*, 01.01.1960 г.р., с. Борзой Советского района ЧИАССР.
1174. ТИМКИН ИГОРЬ ВЛАДИМИРОВИЧ*, 09.06.1981 г.р., с. Поспелиха Алтайского края.
1175. ТИМКО АЛЕКСАНДР АЛЕКСАНДРОВИЧ*, 20.12.1977 г.р., п. Южный (г. Городовиковск) Городовиковского р-на Республики Калмыкия.
1176. ТИМОШИН СЕРГЕЙ СЕРГЕЕВИЧ*, 30.05.1981 г.р., г. Харьков Украинской ССР.
1177. ТИПСУРКАЕВ ИБРАГИМ СЕРГЕЕВИЧ*, 20.10.1983 г.р., с. Урус-Мартан ЧИАССР.
1178. ТИТАЕВ ВИСИТА ВАХИДОВИЧ*, 03.10.1985 г.р., г. Аргун ЧИАССР.
1179. ТИХОМИРОВ ИЛЬЯ ЮРЬЕВИЧ*, 26.07.1986 г.р., г. Москва.
1180. ТИХОНОВ ВИКТОР ИВАНОВИЧ*, 08.12.1954 г.р., г. Новосибирск.
1181. ТЛЕПСУК ЮРИЙ АСХАДОВИЧ*, 08.10.1981 г.р., г. Краснодар.
1182. ТЛИАП АСЛАН ХАЗРЕТОВИЧ*, 26.01.1983 г.р., г. Краснодар.
1183. ТЛИСОВ АЗАМАТ АЛИ-МУРЗОВИЧ*, 12.06.1978 г.р., пос. Кавказский Прикубанского района Ставропольского края.
1184. ТОВСУЛТАНОВ ИБРАГИМ МАГОМЕТ-САЛИЕВИЧ*, 02.11.1984 г.р., с. Алхан-Кала Грозненского района ЧИАССР.
1185. ТОДИКОВ ГЕННАДИЙ ГЕОРГИЕВИЧ*, 16.06.1938 г.р., г. Черемхово Иркутской области.
1186. ТОКАРЬ АЛЕКСАНДР МИХАЙЛОВИЧ*, 01.08.1983 г.р., п. Невская Дубровка Всеволжского района Ленинградской области.
1187. ТОСУЕВ МАХАРБИ ЗАКРИЕВИЧ*, 02.02.1977 г.р., ст. Курдюковская Шелковского района ЧИАССР.
1188. ТОТЧИЕВ АДАМ ИСАЕВИЧ*, 02.01.1981 г.р., с. Серноводское Сунженского района ЧИАССР.
1189. ТОФАН ВИТАЛИЙ ВАСИЛЬЕВИЧ*, 16.06.1983 г.р., с. Сиротское Ширяевского района Одесской области УССР.
1190. ТУГАНБАЕВ МУРАТБИЙ МАХАМБЕТОВИЧ*, 21.12.1979 г.р., ст. Преградная Урупского района КЧАО.
1191. ТУПЕЙКО БОРИС СЕРГЕЕВИЧ*, 25.05.1973 г.р., г. Душанбе Республики Таджикистан.
1192. ТУРАЕВ АСЛАНБЕК АРБИЕВИЧ*, 07.10.1969 г.р., с. Рошни-Чу Урус-Мартановского района ЧИАССР.
1193. ТУРАЕВ ОБУСАЛАХ ГАЗАЛИЕВИЧ*, 01.04.1966 г.р., с. Агишбатой Чеченской Республики.
1194. ТУРЛУЕВ РУСТАМ БАРДЕЛОВИЧ*, 23.06.1975 г.р., с. Соцы-Алды Акульского района Талды-Курганского района Казахской ССР.
1195. ТУРЛУЕВ УСАМ РУКМАНОВИЧ*, 22.07.1980 г.р., пос. Новогрозненский Гудермесского района ЧИАССР.
1196. ТУРПУЛХАНОВ ИСЛАМ ЛЕЧАЕВИЧ*, 14.09.1980 г.р., с. Урус-Мартан Чечено-Ингушской АССР.
1197. ТУРШАЕВ МАГОМЕД ОМАРОВИЧ*, 13.11.1986 г.р., пос. Никольский Енотаевского района Астраханской области.
1198. ТУТАЕВ ТИМУР АПТИЕВИЧ*, 24.12.1984 г.р., г. Грозный ЧИАССР.
1199. ТУХАШЕВ ИСЛАМ ШАМИЛЬЕВИЧ*, 22.05.1981 г.р., с. Ведено Веденского района Чеченской Республики.
1200. ТЭППО АЛЕКСАНДР НИКОЛАЕВИЧ*, 10.04.1975 г.р., г. Новосибирск.
1201. ТЯГАЕВ ЗЕЛИМХАН ИСАЕВИЧ*, 19.03.1985 г.р., с. Ново-Георгиевска Тарумского района Дагестанской АССР.
1202. УЗДЕНОВ МИКАИЛ ИБРАГИМОВИЧ*, 27.06.1979 г.р., селение Ленинаул Казбековского района Республики Дагестан.
1203. УЛАБАЕВ МИКАИЛ ДОШАЕВИЧ*, 17.01.1971 г.р., с. Алхан-Кала Чеченской Республики.
1204. УЛЬБИЕВ АСЛАН ВАХИДОВИЧ*, 31.07.1981 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
1205. УМАЕВ ХУСЕЙН ВАХАЕВИЧ*, 20.07.1966 г.р., с. Алхан-Юрт Урус-Мартановского района ЧИАССР.
1206. УМАЛАТОВ ВАХА СУПЕНОВИЧ*, 25.03.1981 г.р., с. Подгорное Надтеречного района ЧИАССР.
1207. УМАНЦЕВ СЕМЕН ГРИГОРЬЕВИЧ*, 24.12.1984 г.р., ст. Шелковская Шелковского района ЧИАССР.
1208. УМАРОВ АДАМ РУСЛАНОВИЧ*, 02.12.1988 г.р., с. Ачхой-Мартан ЧИАССР.
1209. УМАРОВ ЗЕЛИМХАН АХМЕДОВИЧ*, 15.07.1981 г.р., г. Грозный ЧИАССР.
1210. УМАРОВ МОВСАР ИБРАГИМОВИЧ*, 30.05.1986 г.р., ст. Орджоникидзевская Сунженского района ЧИАССР.
1211. УМАРОВ МУРАД ХОЖБАХУДИЕВИЧ*, 30.12.1984 г.р., с. Беной-Ведено Ножай-Юртовского района ЧИАССР.
1212. УМАРОВ РАМЗАН ХАМЗАТОВИЧ*, 18.02.1989 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1213. УМАРОВ САЛЕХ РУСЛАНОВИЧ*, 24.12.1974 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
1214. УМАРОВ СОСЛАН САЙХАНОВИЧ*, 21.03.1980 г.р., с. Бамут Ачхой-Мартановского района ЧИАССР.
1215. УМАРОВ УСМАН ХАДЖИЕВИЧ*, 20.05.1963 г.р., с. Кенхи Советского района ЧИАССР.
1216. УМАРПАШАЕВ ИСЛАМ ИРИСБАЕВИЧ*, 11.02.1986 г.р., с. Зандак Ножай-Юртовского района ЧИАССР.
1217. УМАРХАЖИЕВ ИСА ДЖЕБРОИЛОВИЧ*, 29.05.1980 г.р., с. Зандак Ножай-Юртовского района ЧИАССР.
1218. УМАХАНОВ АДАМ ГИХОЕВИЧ*, 18.10.1983 г.р., г. Грозный ЧИАССР.
1219. УМАХАНОВ ШАМИЛЬ ГАСАНАЛИЕВИЧ*, 23.11.1964 г.р., г. Махачкала Республики Дагестан.
1220. УРБАКОВ СЕРГЕЙ МИХАЙЛОВИЧ*, 24.10.1970 г.р., г. Улан-Удэ.
1221. УСАЕВ АДРАХИН ТУРПАЛОВИЧ*, 15.01.1976 г.р., с. Н.- Курчали Веденского района ЧИАССР.
1222. УСМАНОВ АПТИ ИСАЕВИЧ*, 07.06.1973 г.р., с. Знаменское Надтеречного района ЧИАССР.
1223. УСМАНОВ АХМЕД ЗАЙНДИЕВИЧ*, 29.07.1975 г.р., г. Аргун ЧИАССР.
1224. УСМАНОВ ЛОМАЛИ ГИЛАЕВИЧ*, 26.03.1985 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1225. УСМАНОВ РАСУЛ МОУДИЕВИЧ*, 08.11.1987 г.р., г. Грозный ЧИАССР.
1226. УСМАНОВ ТИМУР ЛЕЧИЕВИЧ*, 27.10.1979 г.р., с. Автуры ЧИАССР.
1227. УСМАНОВ ХАМПАША ШЕРИЕВИЧ*, 06.09.1978 г.р., с. Курчалой Курчалоевского района ЧИАССР.
1228. УСПАНОВ АХМЕД АБДУЛ-КЕРИМОВИЧ*, 03.01.1981 г.р., с. Осакаровка Карагандинской области Казахской ССР.
1229. УСПАНОВ ИМРАН ВАХИДОВИЧ*, 08.10.1975 г.р., с. Чемульга Сунженского района ЧИАССР.
1230. УСТАЕВ КЮРИ АХМЕДОВИЧ*, 22.07.1981 г.р., с. Ачхой-Мартан ЧИАССР.
1231. УСТАЕВ РУСТАМ САЙД-АХМЕТОВИЧ*, 26.03.1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1232. УСТАРХАНОВ КАЗБЕК САЛМАНОВИЧ*, 01.06.1982 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1233. УЦАЕВ АБУ ИСМАИЛОВИЧ*, 12.06.1981 г.р., с. Шали ЧИАССР.
1234. УЦМИГОВ АСЛАН ХУСЕЙНОВИЧ*, 16.01.1978 г.р., ст. Старогладовская Шелковского района ЧИАССР.
1235. ФАЙЗУЛИН ФАРХАТ РИЗАЕВИЧ*, 14.02.1966 г.р., пос. Балезино Балезинского района Удмуртской АССР.
1236. ФАЙРУЗОВ РАФИС АТЛАСОВИЧ*, 05.01.1986 г.р., г. Азнакаево Республики Татарстан.
1237. ФАРЗАЛИЕВ КАЗБЕК ХАЧМАСОВИЧ*, 06.01.1976 г.р., г. Дербент Республики Дагестан.
1238. ФЕДОРЕНКО ИЛЬЯ ВЛАДИМИРОВИЧ*, 27.05.1983 г.р., с. Среднее Верховского района Орловской области.
1239. ФИЛИН СЕРГЕЙ ВИТАЛЬЕВИЧ*, 23.12.1968 г.р., г. Магадан.
1240. ФРАНЦУЗОВ ТАУКАН КАЗИМОВИЧ*, 22.10.1962 г.р., а. Нижняя Теберда Карачаевского р-на КЧАО.
1241. ХАБИЛАЕВ ИСЛАМ САПАРБЕКОВИЧ*, 15.10.1983 г.р., д. Ильятино Бологовского района Калининской области.
1242. ХАДЖАЕВ РИЗВАН САЛАУДИЕВИЧ*, 25.02.1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
1243. ХАДЖАЛИЕВ ИСРАИЛ ВИСАМУРАДОВИЧ*, 19.04.1979 г.р., г. Ленинаул Казбековского р-на ДАССР.
1244. ХАДЖАЛИЕВ САИД ХИЗАРОВИЧ*, 29.06.1978 г.р., с. Гойты Урус-Мартановского района ЧИАССР.
1245. ХАДЖИЕВ АДАМ МОГДАНОВИЧ*, 28.11.1985 г.р., г. Чимкент КазССР.
1246. ХАДЖИЕВ АЛХАСТ САЙДСЕЛИМОВИЧ*, 02.06.1976 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
1247. ХАДЖИЕВ МУРАД ТАУЗОВИЧ*, 30.07.1981 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1248. ХАДЖИЕВ РАМЗАН ЗАЙНУЛЛАЕВИЧ*, 12.04.1974 г.р., с. Алпатово Наурского района ЧИАССР.
1249. ХАДЖИЕВ УМАР ИБРАГИМОВИЧ*, 09.05.1977 г.р., ст. Наурская ЧИАССР.
1250. ХАДЖИМУРАДОВ ВИСХАН УМАРОВИЧ*, 02.07.1979 г.р., г. Грозный ЧИАССР.
1251. ХАДЗИЕВ УМАР БАГАУДИНОВИЧ*, 29.04.1984 г.р., г. Владикавказ РСО-Алания.
1252. ХАДИЗОВ МУРАД ДЖАМИРЗОЕВИЧ*, 16.03.1982 г.р., с. Ачхой-Мартан ЧИАССР.
1253. ХАДИСОВ РУСЛАН РАМЗАНОВИЧ*, 24.10.1976 г.р., ст. Каргалинская Щелковского р-на ЧИАССР.
1254. ХАДИСОВ ШАМИЛЬ УСМАНОВИЧ*, 13.12.1981 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
1255. ХАЖБАХМАДОВ УМАР МУСАЕВИЧ*, 08.07.1986 г.р., с. Киселевка Заветинского района Ростовской области.
1256. ХАЖМАГАМАЕВ ЛЕЧИ ЗУБАЙРАЕВИЧ*, 21.01.1985 г.р., с. Зандак Ножай-Юртовского района ЧИАССР.
1257. ХАЗАМОВ МАГОМЕДЗАГИД АБДУЛАЕВИЧ*, 21.03.1973 г.р., с. Согратль Гунибского района ДАССР.
1258. ХАЗБУЛАТОВ АБУБАКАР МАЛАТОВИЧ*, 20.12.1982 г.р., с. Надтеречное Надтеречного р-на ЧИАССР.
1259. ХАЗБУЛАТОВ АСЛАН ИБРАГИМОВИЧ*, 07.11.1984 г.р., г. Грозный ЧИАССР.
1260. ХАЙДАЕВ ХУМАЙД АБДУЛХАМИДОВИЧ*, 20.09.1979 г.р., с. Ишхой-Юрт Гудермесского района ЧИАССР.
1261. ХАЙДЕРХАНОВ АЛЬВИ ЛЕЧЕВИЧ*, 26.08.1979 г.р., г. Аргун ЧИАССР.
1262. ХАЙРУЛЛИН ВИЛЬСУР РАФИЛЕВИЧ*, 22.04.1982 г.р., пос. Кукмор Кукморского района Республики Татарстан.
1263. ХАЙХАРОЕВ АХЪЯД АЛАУДИНОВИЧ*, 17.10.1975 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1264. ХАЙХАРОЕВ ИМРАН УМАРОВИЧ*, 30.07.1976 г.р., с. Солдатско-Степное Быковского района Волгоградской обл.
1265. ХАКИМОВ АЛИ МАГОМЕДОВИЧ*, 19.08.1980 г.р., г. Урус-Мартан ЧИАССР.
1266. ХАКИМОВ БУЛАТ БИБОЛТОВИЧ*, 27.07.1982 г.р., х. Павловка Курсавского района Ставропольского края.
1267. ХАКИМОВ МАГОМЕД УСАМОВИЧ*, 21.09.1987 г.р., с. Сельментаузен Веденского района ЧИАССР.
1268. ХАКИМОВ МОВСАР АВАЛУЕВИЧ*, 12.12.1975 г.р., с. Алхан-Юрт Урус-Мартановского района ЧИАССР.
1269. ХАЛАЕВ РУСЛАН САЛАУДИНОВИЧ*, 07.06.1984 г.р., с. Новые Атаги Шалинского района ЧИАССР.
1270. ХАЛАЕВ ШАРУДИН БАДРУДИНОВИЧ*, 07.04.1979 г.р., с. Новые Атаги Шалинского района ЧИАССР.
1271. ХАЛЕТОВ УМАР АБДУРАХМАНОВИЧ*, 24.04.1980 г.р., с. Аралбай Джангильдинского района Тургайской области Казахской АССР.
1272. ХАЛИМОВ ВАХИД ХАМЕДОВИЧ*, 22.03.1984 г.р., с. Кулары ЧИАССР.
1273. ХАЛЬДИХОРОЕВ МАЛИД ИСРАПИЛОВИЧ*, 26.09.1976 г.р., пос. Октябрьский Грозненского района ЧИАССР.
1274. ХАМБУРАЕВ МАГОМЕД МАКШАРИПОВИЧ*, 13.11.1984 г.р., ст. Орджоникидзевская ЧИАССР.
1275. ХАМЗАЕВ МАЙРБЕК РУСЛАНОВИЧ*, 11.12.1981 г.р., с. Урус-Мартан Урус-Мартановского р-на ЧИАССР.
1276. ХАМЗАЛАТОВ АСЛАН ХАМИТОВИЧ*, 14.03.1981 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
1277. ХАМЗАТОВ АДЛАН МАГОМЕД-САЛИХОВИЧ*, 31.10.1984 г.р., с. Самашки (с. Ачхой-Мартан) Ачхой-Мартановского района ЧИАССР.
1278. ХАМЗАТОВ АЛЬВИ АЛАУДИНОВИЧ*, 13.12.1966 г.р., с. Чистопольское Алакульского района Алма-атинской области КазССР.
1279. ХАМЗАТОВ ИЛЕС АЛАУДИНОВИЧ*, 06.06.1974 г.р., с. Самашки ЧИАССР.
1280. ХАМЗАТОВ ИСМАИЛ АЛАУДИЕВИЧ*, 01.05.1979 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
1281. ХАМЗАТХАНОВ РАХИМ АДДИЕВИЧ*, 04.09.1979 г.р., с. Ца-Ведено Веденского р-на ЧИАССР.
1282. ХАМИЕВ ЛОРС НОХЧОЕВИЧ*, 11.01.1984 г.р., г. Грозный ЧИАССР.
1283. ХАМИСБИЕВ НАЗИРБЕК АЛИФТИНОВИЧ*, 08.03.1981 г.р., с. Виноградное Грозненского района ЧИАССР.
1284. ХАМСТХАНОВ ХАСАН ИЛЕСОВИЧ*, 04.12.1980 г.р., с. Катар-Юрт Ачхой-Мртановского района ЧИАССР.
1285. ХАМУРАДОВ АЛИ-ХАН МАУСАРОВИЧ*, 20.08.1982 г.р., с. Старокозинка Мичуринского района Тамбовской области.
1286. ХАМУРЗАЕВ МАРТАН УСМАНОВИЧ*, 03.01.1984 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
1287. ХАМХОЕВ МАГОМЕД ГАБОЕВИЧ*, 03.12.1978 г.р., с. Яндаре Назрановского района ЧИАССР.
1288. ХАНИЕВ УМАР ИСАЕВИЧ*, 07.07.1984 г.р., с. Октябрьское Пригородного района РСО-Алания.
1289. ХАНОВ МАГОМЕД АХМЕДОВИЧ*, 14.02.1966 г.р., с. Куппа Левашинского р-на ДАССР.
1290. ХАНТАЕВ ЗАУРБЕК РАМЗАНОВИЧ*, 16.12.1981 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1291. ХАРАТОКОВ ЭДУАРД МУХАМЕДОВИЧ*, 15.10.1981 г.р., а. Кубина Усть-Джегутинского района Карачаево-Черкесской Республики.
1292. ХАРИХАНОВ АНЗОР МАГОМЕДАЛИЕВИЧ*, 04.09.1985 г.р., г. Грозный Чеченской Республики.
1293. ХАРОНОВ СУЛИМАН ХАМИДОВИЧ*, 28.03.1978 г.р., с. Бешил-Ирзу Ножай-Юртовского района ЧИАССР.
1294. ХАСАЕВ ВАХА АХМЕТОВИЧ*, 09.05.1980 г.р., с. Н. Янгуль Ставропольского края.
1295. ХАСАНОВ АЗАТ ДАМИРОВИЧ*, 20.12.1977 г.р., с. Малые Болгояры Апастовского района ТАССР.
1296. ХАСАНОВ АЛМАЗ ДАМИРОВИЧ*, 20.12.1977 г.р., дер. Малые Болгояры Апастовского района ТАССР.
1297. ХАСАНОВ ИСА МАГОМЕДОВИЧ*, 28.08.1985 г.р., с. Шалажи Урус-Мартановского района ЧИАССР.
1298. ХАСАНОВ МАГАМЕД ВАХАЕВИЧ*, 20.03.1961 г.р., с. Урус-Мартан ЧИАССР.
1299. ХАСАНЬШИН ДАНИЛ РАФАИЛОВИЧ*, 16.11.1977 г.р., г. Ташкент Республики Узбекистан.
1300. ХАСАРБИЕВ ИСЛАМ ДЕНИЛОВИЧ*, 20.10.1972 г.р., г. Грозный ЧИАССР.
1301. ХАСАРОВ МАГОМЕД СУЛУМБЕКОВИЧ*, 20.05.1979 г.р., с. Ачхой-Мартан ЧИАССР.
1302. ХАСАХАНОВ САЛМАН ВАЛИТОВИЧ*, 01.01.1981 г.р., г. Грозный ЧИАССР.
1303. ХАСБУЛАТОВ АБДУЛА МАГОМЕДОВИЧ*, 30.07.1969 г.р., с. Карамахи Буйнакского района ДАССР.
1304. ХАСБУЛАТОВ АБУБАКАР МАЛАТОВИЧ*, 20.12.1982 г.р., с. Надтеречное Надтеречного района ЧИАССР.
1305. ХАСБУЛАТОВ АХМАД ИССАКОВИЧ*, 25.09.1973 г.р., с. Дуба-Юрт Шалинского района Чеченской Республики.
1306. ХАСБУЛАТОВ ГАСАН ХАСБУЛАТОВИЧ*, 19.02.1958 г.р., с. Карамахи Буйнакского района ДАССР.
1307. ХАСБУЛАТОВ ЗАКАРЬЯ МАГОМЕДОВИЧ*, 13.12.1975 г.р., с. Карамахи Буйнакского района Республики Дагестан.
1308. ХАСБУЛАТОВ РУСЛАН ХАМЗАИТОВИЧ*, 05.01.1980 г.р., с. Ножай-Юрт Ножай-Юртовского района ЧИАССР.
1309. ХАСИЕВ РУСЛАН ДУКВАХАЕВИЧ*, 04.07.1980 г.р., с. Валерик Ачхой-Мартановского района ЧИАССР.
1310. ХАСИЕВ ХАМЗАТ БАУДИНОВИЧ*, 23.11.1956 г.р., с. Дуба-Юрт Шалинского района Чеченской Республики.
1311. ХАСИЕВА ЯХА МУТАГИРОВНА*, 23.09.1956 г.р., КазССР.
1312. ХАСУХАНОВ ИСЛАМ ШАЙХ-АХМЕДОВИЧ*, 29.11.1954 г.р., с. Ворошиловское Ворошиловского района Киргизской ССР.
1313. ХАТАЕВ АЛИХАН НЕБИЮЛАЕВИЧ*, 04.06.1987 г.р., с. Дарго Веденского района ЧИАССР.
1314. ХАТУЕВ АБДУРАХМАН МОВСАРОВИЧ*, 22.12.1952 г.р., г. Караганда КазССР.
1315. ХАТУЕВ БИСЛАН АБУЯЗИТОВИЧ*, 11.04.1972 г.р., с. Орехово Ачхой-Мартановского района ЧИАССР.
1316. ХАТУЕВ НУР-МАГОМЕД ШАХИДОВИЧ*, 16.05.1967 г.р., с. Гойты Урус-Мартановского района ЧИАССР (1966 г.).
1317. ХАЦИЕВ БЕЛАН ВИСАНГИРЕЕВИЧ*, 18.06.1978 г.р., г. Джамбул Казахской ССР.
1318. ХАЧЛАЕВ ТАМИРЛАН ИЛЬЯСОВИЧ*, 08.06.1974 г.р., г. Хасавюрт ДАССР.
1319. ХАЧУКАЕВ ИЗРАИЛ САЛМАНОВИЧ*, 02.01.1980 г.р., г. Грозный ЧИАССР.
1320. ХАЧУКАЕВ ИМРАН САЙД-АХМЕДОВИЧ*, 16.02.1972 г.р., с. Новый-Шарой Ачхой-Мартановского района ЧИАССР.
1321. ХАЧУКАЕВ ЭРШТХО СУЛТАНОВИЧ*, 02.02.1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1322. ХАШУМОВ РАШИД АМИРБЕКОВИЧ*, 08.02.1979 г.р., с. Эникали Ножай-Юртовского района ЧИАССР.
1323. ХИДЕРЛЕЗОВ РАСУЛ СОЛТАНСАИДОВИЧ*, 30.06.1982 г.р., г. Хасавюрт Республики Дагестан.
1324. ХИДИРБЕКОВ МАГОМЕДСОЛТАН МАГОМЕДСАИДОВИЧ*, 17.05.1965 г.р., с. Манас Карабудахкентского района ДАССР.
1325. ХИДИРОВ АРСЕН МАГОМЕДНАБИЕВИЧ*, 07.12.1974 г.р., г. Махачкала ДАССР.
1326. ХИЗИРОВ УМАР ИМРАНОВИЧ*, 16.05.1977 г.р., с. Дуба-Юрт Шалинского р-на ЧИАССР.
1327. ХИЗРИЕВ ЗЕЛИМХА МУСЛИМОВИЧ*, 28.04.1978 г.р., с/х Дюрский Новокузнецкого района Саратовской области.
1328. ХИЗРИЕВ ИДРИС БУХАЙСЕРОВИЧ*, 12.01.1977 г.р., с. Кургалой Шалинского района Чеченской Республики.
1329. ХИЗРИЕВ ИЛЕС ВАХИТОВИЧ*, 17.01.1982 г.р., с. Автуры Шалинского района ЧИАССР.
1330. ХИЗРИЕВ РУСТАМ ВИСИРКОВИЧ*, 22.09.1978 г.р., с. Курчалой Шалинского района ЧИАССР.
1331. ХИРИХАНОВ ИБРАГИМ ЛЕЧАЕВИЧ*, 28.11.1982 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1332. ХИСИМИКОВ САИД-МАГОМЕД ХАМЗАЕВИЧ*, 14.03.1980 г.р., г. Грозный Чечено-Ингушской АССР.
1333. ХИТИЕВА ЗАРГАН БАУДИНОВНА*, 23.02.1957 г.р., г. Кызыл-Орда Казахской ССР.
1334. ХИХОЕВ ХУСЕЙН ОМАРОВИЧ*, 02.11.1978 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1335. ХОЖАЕВ АНЗОР АХМЕТОВИЧ*, 14.09.1988 г.р., с. Пригородное Грозненского района ЧИАССР.
1336. ХОЗЯИНОВ ДМИТРИЙ ВЛАДИМИРОВИЧ*, 22.10.1979 г.р., г. Нарьян-Мар Архангельской области.
1337. ХРАМЦОВ СЕРГЕЙ АНАТОЛЬЕВИЧ*, 07.11.1978 г.р., пос. Светлый Котельнического района Кировской области.
1338. ХУБИЕВ АРАСУЛ ПАВЛОВИЧ*, 02.07.1977 г.р., с. Важное Усть-Джегутинского р-на Карачаево-Черкесской Республики.
1339. ХУБИЕВ ТАМБИЙ АНАТОЛЬЕВИЧ*, 25.04.1977 г.р., с. Учкекен Малокарачаевского района Карачаево-Черкесской Республики.
1340. ХУГУЕВ ХАЛИД ХАСМАГОМАДОВИЧ*, 01.01.1956 г.р., пос. Чу Джамбульской области Казахской ССР.
1341. ХУДОЯРОВ ЗАЙНАДИН АЛИМХАНОВИЧ*, 22.08.1979 г.р., с. Коби Шелковского района ЧИАССР.
1342. ХУДУЛОВ ВИСХАДЖИ ХУСАЙИНОВИЧ*, 06.06.1974 г.р., с. Бильты Ножай-Юртовского района ЧИАССР.
1343. ХУСАИНОВ АБДУЛ-МЕЛИК НАЖМУДИНОВИЧ*, 05.05.1967 г.р., с. Киров-Юрт Веденского района ЧИАССР.
1344. ХУСАИНОВ БЕСЛАН НАЖМУДИНОВИЧ, 10.12.1977 г.р., с. Киров-Юрт Веденского района ЧИАССР.
1345. ХУСАИНОВ УМАР БИЛАЛОВИЧ*, 06.04.1987 г.р., ст. Курдюковская ЧИАССР.
1346. ХУСЕЙНОВ АЛИ ХАЛИДОВИЧ*, 10.04.1979 г.р., с. Новый Шарой Ачхой-Мартановского района ЧИАССР.
1347. ХУТИЕВ АБДУЛРАХИМ ХАЖБЕКАРОВИЧ*, 07.01.1978 г.р., с. Октябрьское Пригородного района РСО-Алания.
1348. ХУТОВ АНЗОР ЭЛЬВЕРОВИЧ*, 21.11.1978 г.р., ст. Ессентукская Предгорного района Ставропольского края.
1349. ХУТОВ РУЗАЛИ ЭЛЬВЕРОВИЧ*, 27.01.1977 г.р., совхоз Кисловодский Предгорного района Ставропольского края.
1350. ХУЦАЕВ ДУКВАХА ИСАЕВИЧ*, 15.07.1985 г.р., с. Ачхой-Мартан ЧИАССР.
1351. ХУЦАЕВ РУСТАМ ИСАЕВИЧ*, 11.07.1980 г.р., с. Урус-Мартан ЧИАССР.
1352. ЦАКАЕВ АЛИ САЙД-ХУСЕНОВИЧ*, 04.01.1977 г.р., с. Татай-Хутор Ножай-Юртовского района ЧИАССР.
1353. ЦАКАЕВ АМХАД УМАРСОЛТАЕВИЧ*, 24.03.1988 г.р., с. Татай-Хутор Ножай-Юртовского района Чеченской Республики.
1354. ЦАКАЕВ БЕСЛАН САИД-ХУСЕЙНОВИЧ*, 03.11.1983 г.р., с. Татай-Хутор Ножай-Юртовского района ЧИАССР.
1355. ЦАХИГОВ МАГОМЕД ВАХИДОВИЧ*, 22.12.1976 г.р., с. Гойты Урус-Мартановского района Чеченской Республики.
1356. ЦАЦАЕВА МАЛИКАТ АДАМОВНА*, 25.05.1952 г.р., с. Садовое Московского района КиргССР.
1357. ЦВИГУН ВАЛЕРИЙ ВЛАДИМИРОВИЧ*, 20.08.1982 г.р., г. Набережные Челны Татарской АССР.
1358. ЦЕЧОЕВ АДАМ АХМЕТОВИЧ*, 29.09.1976 г.р., ст. Орджоникидзевская Сунженского района Республики Ингушетия.
1359. ЦЕЧОЕВ МАГОМЕД-ХАМИД РУСЛАНОВИЧ*, 02.10.1974 г.р., г. Назрань Республики Ингушетия.
1360. ЦИНАЕВ МУРАД МАГОМЕДОВИЧ*, 10.09.1984 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
1361. ЦИЦАЕВ РУСТАМ ИЛЬЯСОВИЧ*, 05.12.1982 г.р., г. Шали Шалинского района ЧИАССР.
1362. ЦИЦИЕВ РАМЗАН МАГОМЕДОВИЧ*, 18.03.1982 г.р., с. Ножай-Юрт Ножай-Юртовского района ЧИАССР.
1363. ЦОКАЛАЕВ МАГОМЕД ЛЕЧАЕВИЧ*, 21.05.1988 г.р., с. Ачхой-Мартан ЧИАССР.
1364. ЦУРАЕВ САЙД-ХАСАН УВАЙСОВИЧ*, 12.08.1980 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1365. ЦУРОВ АДАМ МУССАЕВИЧ*, 05.07.1980 г.р., п. Карца Промышленного района г. Владикавказа РСО-Алания.
1366. ЦУРОВ РУСТАМ ЮНУСОВИЧ*, 12.08.1979 г.р., г. Владикавказ Республики Северная Осетия-Алания.
1367. ЦУРОЕВ АХМЕТ АЛИХАНОВИЧ*, 30.07.1979 г.р., г. Назрань Республики Ингушетия.
1368. ЧАБДАЕВ БИСЛАН УСАМОВИЧ*, 02.10.1973 г.р., х. Бударка Котельниковского района Волгоградской области.
1369. ЧАГАЕВ САЛМАН АСЛАХОВИЧ*, 28.07.1975 г.р., с. Шалажи Урус-Мартановского района ЧИАССР.
1370. ЧАГИЛОВ АЛИБЕК МУХТАРОВИЧ*, 06.09.1976 г.р., г. Карачаевск Карачаево-Черкесской Республики.
1371. ЧАГИЛОВ РУСТАМ РУСЛАНОВИЧ*, 14.06.1978 г.р., г. Карачаевск Карачаево-Черкесской Республики.
1372. ЧАКАЕВ АЮБ САЙДАХМЕТОВИЧ*, 05.09.1981 г.р., г. Гудермес ЧИАССР.
1373. ЧАЛАЕВ ИСЛАМ ТУРГУНБАЕВИЧ*, 07.06.1986 г.р., с. Симсир Ножай-Юртовского района ЧИАССР.
1374. ЧАЛАЕВ СУЛИМАН ХАСАНБЕКОВИЧ*, 06.07.1976 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1375. ЧАМАЕВ АХМЕД МУХАДИНОВИЧ*, 18.11.1975 г.р., с. А. Шерипова ЧИАССР.
1376. ЧАНИЕВ АХМЕД ШАБАЗГИРЕЕВИЧ*, 10.09.1966 г.р., д. Горно-Слинкино Тюменской области.
1377. ЧАРАЕВ МАГОМЕД ХУСЕЙНОВИЧ*, 08.03.1986 г.р., с. Курчалой Шалинского района ЧИАССР.
1378. ЧАУШЕВ ОСМАН БОРИСОВИЧ*, 12.11.1977 г.р., а. Эльбурган Хабезского района Ставропольского края.
1379. ЧАХКИЕВ РУСЛАН МАГОМЕТОВИЧ*, 25.01.1978 г.р., с. Куртат Пригородного района Республики Северная Осетия-Алания.
1380. ЧЕРНОБРОВКИН ВИТАЛИЙ АЛЕКСАНДРОВИЧ*, 28.09.1975 г.р., г. Чита.
1381. ЧЕРНОВ АЛЕКСЕЙ АНАТОЛЬЕВИЧ*, 13.07.1977 г.р., с. Ламки Узловского района Тульской области.
1382. ЧЕРНЯВСКИЙ ЮРИЙ ВЛАДИМИРОВИЧ*, 04.10.1968 г.р., г. Приозерск Карагандинской области Казахской ССР.
1383. ЧЕСНОКОВ ВЯЧЕСЛАВ ВЛАДИМИРОВИЧ*, 23.11.1963 г.р., г. Свердловск.
1384. ЧИМАЕВ АНЗОР ВАХАЕВИЧ*, 05.03.1978 г.р., г. Грозный Чеченской Республики.
1385. ЧИНТАГОВ РАДЖИ МАГОМЕДОВИЧ*, 21.02.1986 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1386. ЧИСТЯКОВ АЛЕКСАНДР ИВАНОВИЧ*, 25.03.1982 г.р., пгт. Пойковский Нефтеюганского района Тюменской области.
1387. ЧИТАЕВ СУРХО АЛИЕВИЧ*, 10.09.1980 г.р., г. Грозный ЧИАССР.
1388. ЧУДАЛОВ МУСЛИМ МУСАЕВИЧ*, 11.10.1979 г.р., г. Грозный (с. Аллерой Шалинского района) ЧИАССР.
1389. ЧУНЧАЕВ САЙПУДИ ЛЕЧАЕВИЧ*, 23.06.1977 г.р., с. Урус-Мартан ЧИАССР.
1390. ЧУПАЛАЕВ САИД-МАГОМЕД ЦУГАЕВИЧ*, 04.04.1957 г.р., с. Ириновка Урджарского р-на Семипалатинской области Казахской ССР.
1391. ШАВАЕВ МАГОМЕД НАИПОВИЧ*, 13.12.1975 г.р., г. Грозный ЧИАССР.
1392. ШАВАЕВ МУРАТ ИСМАИЛОВИЧ*, 17.02.1975 г.р., г. Нальчик Кабардино-Балкарской Республики.
1393. ШАВХАЛОВ ИБРАГИМ САЙДАХМЕДОВИЧ*, 23.08.1987 г.р., г. Хасавюрт ДАССР.
1394. ШАВХАЛОВ РАМЗАН РУСЛАНОВИЧ*, 08.10.1980 г.р., с. Алхан-Кала ЧИАССР.
1395. ШАГАЛИЕВ ИЛЬШАТ ИСМАГИЛОВИЧ*, 04.07.1986 г.р., г. Набережные Челны Республики Татарстан.
1396. ШАДУКАЕВ РИЗВАН БУКАЕВИЧ*, 09.08.1968 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1397. ШАИПОВ МАГОМЕД ВАХАЕВИЧ*, 09.04.1983 г.р., с. Урус-Мартан Урус-Мартановского района Чеченской Республики.
1398. ШАИПОВ ТИМУР СУРПАШЕВИЧ*, 10.03.1984 г.р., г. Хасавюрт Республики Дагестан.
1399. ШАИПОВ ШАМХАН ШАМСУДИНОВИЧ*, 17.05.1977 г.р., п. Маныч Ики-Бурульского района Республики Калмыкия.
1400. ШАЙДУЛЛИН ИЛЬМИР ИЛЬГИЗОВИЧ*, 31.10.1983 г.р., г. Азнакаево Республики Татарстан.
1401. ШАЙДУЛЛИН РУСТЕМ ИЛЬГИЗОВИЧ*, 26.02.1987 г.р., г. Азнакаево Республики Татарстан.
1402. ШАЙЛИЕВ ХАЛИС СУЛТАНОВИЧ*, 21.01.1967 г.р., г. Карачаевск Карачаево-Черкесской Республики.
1403. ШАЙХИЕВ ШИРВАНИ ХАСМАГОМЕДОВИЧ*, 14.08.1951 г.р., с. Кара-Кочкар Ошской области Киргизской ССР.
1404. ШАЙХУТДИНОВ ФАНИС АГЛЯМОВИЧ*, 27.06.1965 г.р., с. Агерзе Азнакаевского района ТАССР.
1405. ШАЛАЕВ АЙНДИ ЗАИНДИЕВИЧ*, 19.12.1974 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1406. ШАМАЕВ АЛЬВИ АИНДЫЕВИЧ*, 18.09.1984 г.р., г. Грозный ЧИАССР.
1407. ШАМАНОВ ТИМУР КАЗБЕКОВИЧ*, 28.01.1975 г.р., г. Песчаный Приютненского района Калмыцкой АССР.
1408. ШАМСАДОВ ИСА МУСАЕВИЧ*, 10.09.1986 г.р., с. Советское Советского района ЧИАССР.
1409. ШАМСАДОВ СУПЬЯН МУХАДИНОВИЧ*, 14.08.1969 г.р., с. Тазбичи Советского района ЧИАССР.
1410. ШАМСАДОВ ТИМУР МАГОМЕДОВИЧ*, 01.06.1981 г.р., г. Грозный ЧИАССР.
1411. ШАМСУДИНОВ АСЛАНБЕК АЗИЗОВИЧ*, 20.12.1972 г.р., с. Танги-Чу ЧИАССР.
1412. ШАМУРЗАЕВ МАГОМЕД САЛМАНОВИЧ*, 12.07.1974 г.р., с. Комсомольское Гудермесского района ЧИАССР.
1413. ШАМХАЛОВ ШАМИЛЬ ЮСУПОВИЧ*, 12.12.1979 г.р., г. Махачкала Республики Дагестан.
1414. ШАРГО МАКСИМ МАКСИМОВИЧ*, 04.10.1974 г.р., г. Петропавловск-Камчатский.
1415. ШАХГИРИЕВ РУСЛАН АБАЕВИЧ*, 21.11.1964 г.р., с. Агишбатой Веденского района Чеченской Республики.
1416. ШЕВЛЯКОВ АНАТОЛИЙ ЮРЬЕВИЧ*, 06.11.1984 г.р., г. Грозный ЧИАССР.
1417. ШЕЙХОВ БАММАТХАН КАМИЛОВИЧ*, 04.04.1964 г.р., г. Буйнакск Республики Дагестан.
1418. ШЕПИЕВ АСЛАН АХЪЯЕВИЧ*, 08.05.1969 г.р., с. Джалка Гудермесского района ЧИАССР.
1419. ШЕПИЕВ РУДОЛЬФ АЛЕКСАНДРОВИЧ*, 11.07.1980 г.р., ст. Каргалинская Шелковского района ЧИАССР.
1420. ШИДИЕВ РИЗВАН ШУДИЕВИЧ*, 11.07.1987 г.р., с. Гуни Веденского района ЧИАССР.
1421. ШИМАЕВ ХАСУ АЙНДИЕВИЧ*, 20.04.1982 г.р., с. Урус-Мартан Урус-Мартановского района Чеченской Республики.
1422. ШИХОВ АЗАТ ФАТТАХОВИЧ*, 11.04.1978 г.р., с. Ульт-Ягун Сургутского района Тюменской области.
1423. ШИШХАНОВ МАЙРБЕК ОМАРОВИЧ*, 23.09.1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
1424. ШОВХАЛОВ ВИСХАН ВАХИТОВИЧ*, 28.06.1986 г.р., д. Волково Артинского района Свердловской области.
1425. ШОВХАЛОВ РУСЛАН САЛАМУВИЧ*, 11.03.1977 г.р., совхоз Джетикульский Джамбутинского района Уральской области КазССР.
1426. ШУКУРОВ ИЛХОМ ИБРАГИМОВИЧ*, 06.12.1976 г.р., г. Карши Кашкадарьинской области Республики Узбекистан.
1427. ШУКУРОВ ШЕРАЛИ ИБРАГИМОВИЧ*, 17.07.1974 г.р., г. Карши Кашкадарьинской области Республики Узбекистан.
1428. ШУМИЛКИН АЛЕКСАНДР ЕВГЕНЬЕВИЧ*, 23.11.1970 г.р., с. Первомайский Перелюбского района Саратовской области.
1429. ЩЕРБОВ СЕРГЕЙ ВАСИЛЬЕВИЧ*, 09.10.1977 г.р., с. Ярославичи Подпорожского района Ленинградской области.
1430. ЩУКИН ДМИТРИЙ АЛЕКСАНДРОВИЧ*, 14.02.1979 г.р., г. Витебск Республики Беларусь.
1431. ЭДИЛСУЛТАНОВ РАМЗАН МАК-МАГОМЕДОВИЧ*, 25.10.1980 г.р., с. Курчалой Шалинского района ЧИАССР.
1432. ЭДИЛСУЛТАНОВ РУСЛАН МАГОМЕДОВИЧ*, 09.05.1967 г.р., с. Курчалой Шалинского района ЧИАССР.
1433. ЭДИЛЬСУЛТАНОВ ХУСЕЙН КУСУЕВИЧ*, 14.03.1961 г.р., с. Курчалой Шалинского района ЧИАССР.
1434. ЭЖИЕВ РУСТАМ ХАМИДОВИЧ*, 21.01.1972 г.р., с. Сержень-Юрт Шалинского района.
1435. ЭЗЕРХАНОВ АХМЕТ РАСУЛОВИЧ*, 07.03.1985 г.р., г. Грозный ЧИАССР.
1436. ЭЗИРХАНОВ САЙД-ЭМИ САЙД-АХМЕДОВИЧ*, 02.03.1985 г.р., с. Кошкельды Гудермесского района ЧИАССР.
1437. ЭКЗЕКОВ МУРАТ УМАРОВИЧ*, 28.05.1979 г.р., г. Черкесск Карачаево-Черкесской Республики.
1438. ЭКТУМАЕВ ЗАУРБЕК МУХАРБЕКОВИЧ*, 30.08.1980 г.р., х. Веселый Ачхой-Мартановского района ЧИАССР.
1439. ЭКТУМАЕВ ИСЛАМ СУЛЕЙМАНОВИЧ*, 31.05.1982 г.р., ст. Орджоникидзевская Сунженского района ЧИАССР.
1440. ЭКТУМАЕВ МУСЛИМ МАГОМЕДОВИЧ*, 27.06.1977 г.р., с. Бамут Ачхой-Мартановского района ЧИАССР.
1441. ЭЛАЕВ АДЛАН САЛМАНОВИЧ*, 01.10.1972 г.р., с. Дай ЧИАССР.
1442. ЭЛЖУРКАЕВ АСЛАН АРБИЕВИЧ*, 04.11.1986 г.р., г. Грозный ЧИАССР.
1443. ЭЛИХАДЖИЕВ ДАНИЛХАН СУЛЕЙМАНОВИЧ*, 17.07.1984 г.р., с. Курчалой Курчалоевского района ЧИАССР.
1444. ЭЛИХАНОВ ИБРАГИМ ТУХАНОВИЧ*, 19.11.1985 г.р., п. Новогрозненский Гудермесского района ЧИАССР.
1445. ЭЛИХАНОВ МАГОМЕД АЙСАЕВИЧ*, 18.01.1985 г.р., с. Новые Атаги Шалинского района ЧИАССР.
1446. ЭЛИХАНОВ РУСЛАН АБУБАКАРОВИЧ*, 11.06.1983 г.р., с. Ялхой-Мохк Ножай-Юртовского района ЧИАССР.
1447. ЭЛИХАНОВ РУСТАМ ИСАЕВИЧ*, 25.09.1986 г.р., с. Каримово Бижбуляжского района Башкирской АССР.
1448. ЭЛИХАНОВ САЙД-ХУСЕЙН ХАСАНОВИЧ*, 20.10.1978 г.р., село Бачи-Юрт Шалинского района ЧИАССР.
1449. ЭЛЬГЕРЕЕВ РОМАН ЭЛЛИЕВИЧ*, 04.10.1977 г.р., г. Гудермес ЧИАССР.
1450. ЭЛЬДАРОВ МАГОМЕД ИСАЕВИЧ*, 03.10.1979 г.р., г. Грозный ЧИАССР.
1451. ЭЛЬКАНОВ ОСМАН САЙДАХМАТОВИЧ*, 31.03.1982 г.р., п. Новый Карачай Карачаевского района Карачаево-Черкесской Республики.
1452. ЭЛЬМУРЗАЕВ АРСЛАН МАМАСОЛЕБОВИЧ*, 15.03.1976 г.р., ст. Шелковская ЧИАССР.
1453. ЭЛЬМУРЗАЕВ АСЛАНБЕК ХАМЗАТОВИЧ*, 10.08.1979 г.р., с. Зоны Советского района Чеченской Республики.
1454. ЭЛЬМУРЗАЕВ КАЗБЕК АБДУЛ-ВАХАБОВИЧ*, 19.11.1983 г.р., г. Аргун ЧИАССР.
1455. ЭЛЬМУРЗАЕВ МАХМА МАГОМЕДОВИЧ*, 01.09.1953 г.р., г. Усть-Каменогорск КазССР.
1456. ЭЛЬМУРЗАЕВ САИД ШАМАНОВИЧ*, 07.12.1981 г.р., г. Грозный ЧИАССР.
1457. ЭЛЬМУРЗИЕВ МУССА КУРЕЙШЕВИЧ*, 20.06.1968 г.р., г. Орджоникидзе Республики Северная Осетия.
1458. ЭЛЬСАЕВ ТИМУР КЮРАЕВИЧ*, 04.10.1987 г.р., с. Ачхой-Мартан ЧИАССР.
1459. ЭЛЬСИЕВ ЮНАДИ СУЛТАНОВИЧ*, 29.11.1979 г.р., с. Урус-Мартан ЧИАССР.
1460. ЭЛЬХАДЖИЕВ АНЗОР СУЛТАНБЕКОВИЧ*, 13.09.1979 г.р., с. Хамавюрт Хасавюртовского района ДагАССР.
1461. ЭЛЬХОДЖИЕВ АЗАМАТ СУЛТАНБЕКОВИЧ*, 23.02.1982 г.р., с. Хамавюрт Хасавюртовского района ДагАССР.
1462. ЭРЗАНУКАЕВ МОХМАД ИНДАРБЕКОВИЧ*, 20.01.1987 г.р., с. Агишты Веденского района ЧИАССР.
1463. ЭРСАБИЕВ АЛЬВИ АНДИЕВИЧ*, 25.11.1988 г.р., г. Грозный Чеченской Республики.
1464. ЭРСИМИКОВ ИБРАГИМ БИСЛАНОВИЧ*, 12.07.1983 г.р., г. Аргун ЧИАССР.
1465. ЭСАЕВ РАХМАН РАМЗАНОВИЧ*, 01.05.1988 г.р., с. Ведено ЧИАССР.
1466. ЭСАМБАЕВ ХАСМАГОМЕД ХАМИДОВИЧ*, 21.04.1960 г.р., с. Ачеришки Ножай-Юртовского района ЧИАССР.
1467. ЭСКАРБИЕВ ВИСЛАН ВАХАРПАШАЕВИЧ*, 01.08.1976 г.р., с. Гиляны Ножай-Юртовского района ЧИАССР.
1468. ЭСКЕРХАНОВ АЙНДИ САЙПУДИНОВИЧ*, 01.01.1982 г.р., с. Советское Советского района ЧИАССР.
1469. ЭСКЕРХАНОВ САЛМАН ТАРХАНОВИЧ*, 26.09.1970 г.р., с. Кулары Грозненского район ЧИАССР.
1470. ЭСКИРХАНОВ ЭЛИ САЛАМОЕВИЧ*, 14.04.1974 г.р., с. Сарай Новороссийского района Актюбинской области КазССР.
1471. ЮНУСОВ АСЛАМБЕК ИДРИСОВИЧ*, 19.04.1979 г.р., с. Побединское Грозненского района Чеченской Республики.
1472. ЮНУСОВ АСЛАН АНДИЕВИЧ*, 23.07.1976 г.р., совхоз Алгайский Новоузенского района Саратовской области.
1473. ЮНУСОВ ДЖАБРАИЛ МАЙРБЕКОВИЧ*, 29.03.1970 г.р., станица Калиновская Наурского р-на ЧИАССР.
1474. ЮНУСОВ ДУКВАХИ ИЙСАЕВИЧ*, 13.10.1978 г.р., г. Грозный ЧИАССР.
1475. ЮНУСОВ РАМЗАН ДАУДОВИЧ*, 24.06.1984 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
1476. ЮНУСОВ РУСЛАН ИЙСАЕВИЧ*, 14.11.1974 г.р., г. Грозный ЧИАССР.
1477. ЮНУСОВ ЮСУП РАМЗАНОВИЧ*, 21.07.1978 г.р., с. Курчали Веденского района ЧИАССР.
1478. ЮСУПОВ АЛИ СУЛТАНОВИЧ*, 01.06.1974 г.р., с. Новые-Атаги Шалинского района ЧИАССР.
1479. ЮСУПОВ АЛИБЕК АЙНДЫЕВИЧ*, 25.04.1983 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1480. ЮСУПОВ АЛИБЕК ХУСАИНОВИЧ*, 19.08.1978 г.р., с. Урус-Мартановского р-на ЧИАССР.
1481. ЮСУПОВ АМХАД СУЛТАНОВИЧ*, 22.01.1981 г.р., с. Майртуп Шалинского района ЧИАССР.
1482. ЮСУПОВ АРЗУ МАГОМЕДОВИЧ*, 17.02.1985 г.р., с. Суворов-Юрт Гудермесского района ЧИАССР.
1483. ЮСУПОВ ВАХМУРАД АЙНУТДИНОВИЧ*, 06.08.1984 г.р., г. Хасавюрт Республики Дагестан.
1484. ЮСУПОВ ВИСИТА ВАХИТОВИЧ*, 02.02.1988 г.р., г. Гудермес ЧИАССР.
1485. ЮСУПОВ ИМРАН БОЙСУЕВИЧ*, 01.01.1983 г.р., с. Кошкельды Гудермесского района ЧИАССР.
1486. ЮСУПОВ ИСЛАМ АБУЕВИЧ*, 04.10.1986 г.р., с. Чири-Юрт Шалинского района ЧИАССР.
1487. ЮСУПОВ КАЗБЕК САЛМАНОВИЧ*, 20.02.1981 г.р., с. Урус-Мартан ЧИАССР.
1488. ЮСУПОВ МАХМАД ГИЛАНИЕВИЧ*, 22.06.1982 г.р., с. Новые-Атаги ЧИАССР.
1489. ЮСУПОВ РАСАНБЕК ХАМИДОВИЧ*, 06.11.1984 г.р., с. Ножай-Юрт Ножай-Юртовского района ЧИАССР.
1490. ЮСУПОВ СКАНДАРБЕК СУЛТАНОВИЧ*, 20.12.1955 г.р., колхоз им. Крупской Сталинского района Фрунзенской области Киргизской ССР.
1491. ЮСУПОВ СУЛУМБЕК АХМЕДОВИЧ*, 21.05.1985 г.р., с. Бешил-Ирзой Ножай-Юртовского района Чеченской Республики.
1492. ЮСУПОВ ХАВАЖ ХАМИДОВИЧ*, 04.04.1986 г.р., с. Аллерой Ножай-Юртовского района ЧИАССР.
1493. ЮСУПОВ ХАМЗАТ САЙДАЕВИЧ*, 05.07.1957 г.р., с. Кандыковка Шемонайхинского района Восточно-Казахстанской области КазССР.
1494. ЮШАЕВ СУЛИМА САЛМАНОВИЧ*, 17.09.1981 г.р., г. Гудермес ЧИАССР.
1495. ЯКОВЛЕВ АНДРЕЙ ЮРЬЕВИЧ*, 05.01.1970 г.р., г. Армавир Краснодарского края.
1496. ЯКОВЛЕВ ЕВГЕНИЙ ИВАНОВИЧ*, 10.10.1960 г.р., д. Кошноруй Канашского района Чувашской Республики.
1497. ЯКУБОВ АСЛАН НАСРУДИЕВИЧ*, 15.05.1970 г.р., с. Шали Шалинского района ЧИАССР.
1498. ЯКУЕВ ЗАУРБЕК НАБИУЛЛЫЕВИЧ*, 30.11.1981 г.р., с. Рубежное Наурского р-на ЧИАССР.
1499. ЯКУШЕВ РОМАН ВЛАДИМИРОВИЧ*, 03.07.1982 г.р., г. Алексин Тульской области.
1500. ЯЛХОРОЕВ ДЖАБРАИЛ УМАТ-ГИРЕЕВИЧ*, 30.11.1970 г.р., г. Грозный ЧИАССР.
1501. ЯНДАРБИЕВ ЗЕЛИМХАН АБДУЛ-МУСЛИМОВИЧ*, 12.09.1951 г.р., Верхубинский район Восточно-Казахской области Казахской ССР.
1502. ЯНДИЕВ АЛИЯ СУЛТАНОВИЧ*, 20.09.1975 г.р., г. Назрань ЧИАССР.
1503. ЯРМОЛАТОВ РАМЗАН ВАХИТОВИЧ*, 02.12.1983 г.р., с. Автуры ЧИАССР.
1504. ЯРМОЛАТОВ УМАР ВАХИТОВИЧ*, 06.07.1987 г.р., г. Шали ЧИАССР.
1505. ЯСАКОВ РЕШЕД ИБРАГИМОВИЧ*, 23.02.1972 г.р., с. Кади-Юрт Гудермесского района ЧИАССР.
1506. ЯСУЕВ АСЛАНБЕК ШАРПУДИЕВИЧ*, 26.12.1984 г.р., с. Старые Атаги Грозненского района ЧИАССР.
1507. ЯСУЕВ МОВЛАДИ САИД-МАГОМЕДОВИЧ*, 21.10.1984 г.р., с. Улус-Керт Советского р-на ЧИАССР.
1508. ЯХЪЯЕВ ЯКУБ ИСМАИЛОВИЧ*, 09.03.1974 г.р., х. Мирный Дубовского района Ростовской области.
1509. ЯХЬЯЕВ ДУК-ВАХА ИДРИСОВИЧ*, 03.02.1974 г.р., г. Урус-Мартан ЧИАССР.
1510. ЯШУЕВ ТАМЕРЛАН САЙДМАГОМЕДОВИЧ*, 03.08.1983 г.р., н.п. Кошкельды Гудермесского района ЧИАССР.
Примечание: 1. Отмечены (*) организации и физические лица, в отношении которых имеются сведения об их причастности к терроризму.
[Note: 1. Individuals and organizations marked (*) indicate that there is evidence of their involvement in terrorism.]

![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict0.jpg) Protesters gather in Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011. Egyptian police are clashing with anti-government protesters for a fifth day in Cairo. Tens of thousands of protesters in Tahrir Square have rejected a promise by Egypt’s military ruler to speed up a presidential election to the first half of next year. They want Field Marshal Hussein Tantawi to step down immediately in favor of an interim civilian council. (Tara Todras-Whitehill)
Protesters gather in Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011. Egyptian police are clashing with anti-government protesters for a fifth day in Cairo. Tens of thousands of protesters in Tahrir Square have rejected a promise by Egypt’s military ruler to speed up a presidential election to the first half of next year. They want Field Marshal Hussein Tantawi to step down immediately in favor of an interim civilian council. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict15.jpg) An injured protester, center, is aided by men on a motorcycle during clashes with Egyptian riot police, not pictured, near Tahrir square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
An injured protester, center, is aided by men on a motorcycle during clashes with Egyptian riot police, not pictured, near Tahrir square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict10.jpg) An injured protester is carried by other men during clashes with the Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
An injured protester is carried by other men during clashes with the Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict13.jpg) Egyptian riot policeman clash with protesters near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
Egyptian riot policeman clash with protesters near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict1.jpg) An Egyptian protester using scrap metal as a shield takes cover from tear gas during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
An Egyptian protester using scrap metal as a shield takes cover from tear gas during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict2.jpg) An Egyptian protester, center, uses a sling shot during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
An Egyptian protester, center, uses a sling shot during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict3.jpg) Egyptian protesters take cover from tear gas during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
Egyptian protesters take cover from tear gas during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict11.jpg) Egyptian protesters throw stones at security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
Egyptian protesters throw stones at security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict12.jpg) An Egyptian riot policeman throws a rock at protesters during clashes near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
An Egyptian riot policeman throws a rock at protesters during clashes near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict4.jpg) A protester takes a break during clashes with Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
A protester takes a break during clashes with Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict6.jpg) An injured Egyptian cleric from Al-Azhar, the country’s most prominent Islamic institution, wears a scarf as a mask to shield him from tear gas during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
An injured Egyptian cleric from Al-Azhar, the country’s most prominent Islamic institution, wears a scarf as a mask to shield him from tear gas during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict9.jpg) A wounded protester is aided by a comrade during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
A wounded protester is aided by a comrade during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict17.jpg) A protester walks away from tear gas fired during clashes with Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
A protester walks away from tear gas fired during clashes with Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict5.jpg) Female medics and doctors distribute supplies during nearby clashes with Egyptian riot police, in Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
Female medics and doctors distribute supplies during nearby clashes with Egyptian riot police, in Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict8.jpg) An Egyptian protester waves a national flag during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
An Egyptian protester waves a national flag during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict7.jpg) Protesters sit on a partially demolished wall during a temporary cease-fire with the Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
Protesters sit on a partially demolished wall during a temporary cease-fire with the Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict14.jpg) Protesters sit on a barricade during a temporary cease-fire with the Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
Protesters sit on a barricade during a temporary cease-fire with the Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict16.jpg) Protesters sit on the sidewalk during a temporary cease-fire with the Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
Protesters sit on the sidewalk during a temporary cease-fire with the Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.












![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict39.jpg) Protesters keep a pathway clear to move injured people during nearby clashes with Egyptian riot police in Tahrir Square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s ruling military moved up the date for transferring power to a civilian government to July next year and consulted Tuesday with political parties on forming a new Cabinet. But the major concessions were immediately rejected by tens of thousands of protesters in Cairo’s iconic Tahrir Square threatening a “second revolution.” (Tara Todras-Whitehill)
Protesters keep a pathway clear to move injured people during nearby clashes with Egyptian riot police in Tahrir Square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s ruling military moved up the date for transferring power to a civilian government to July next year and consulted Tuesday with political parties on forming a new Cabinet. But the major concessions were immediately rejected by tens of thousands of protesters in Cairo’s iconic Tahrir Square threatening a “second revolution.” (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict41.jpg) Women protesters stand in a group during nearby clashes with Egyptian riot police in Tahrir Square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s ruling military moved up the date for transferring power to a civilian government to July next year and consulted Tuesday with political parties on forming a new Cabinet. But the major concessions were immediately rejected by tens of thousands of protesters in Cairo’s iconic Tahrir Square threatening a “second revolution.” (AP Photo/Tara Todras-Whitehill)
Women protesters stand in a group during nearby clashes with Egyptian riot police in Tahrir Square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s ruling military moved up the date for transferring power to a civilian government to July next year and consulted Tuesday with political parties on forming a new Cabinet. But the major concessions were immediately rejected by tens of thousands of protesters in Cairo’s iconic Tahrir Square threatening a “second revolution.” (AP Photo/Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict40.jpg) Egyptian protesters perform prayers as they are guarded by other protesters who hold the national flag at Tahrir Square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egyptian politicians say the ruling military has moved up the date for transferring power to a civilian government to July 1, 2012. (Ahmed Ali)
Egyptian protesters perform prayers as they are guarded by other protesters who hold the national flag at Tahrir Square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egyptian politicians say the ruling military has moved up the date for transferring power to a civilian government to July 1, 2012. (Ahmed Ali)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict42.jpg) Protesters demonstrate during clashes with Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s ruling military moved up the date for transferring power to a civilian government to July next year and consulted Tuesday with political parties on forming a new Cabinet. But the major concessions were immediately rejected by tens of thousands of protesters in Cairo’s iconic Tahrir Square threatening a “second revolution.” (Tara Todras-Whitehill)
Protesters demonstrate during clashes with Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s ruling military moved up the date for transferring power to a civilian government to July next year and consulted Tuesday with political parties on forming a new Cabinet. But the major concessions were immediately rejected by tens of thousands of protesters in Cairo’s iconic Tahrir Square threatening a “second revolution.” (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict43.jpg) Protesters chant slogans during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011.Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)
Protesters chant slogans during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011.Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict44.jpg) A protester runs to throw a tear gas canister away during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011.Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)
A protester runs to throw a tear gas canister away during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011.Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict45.jpg) Protesters run for cover during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)
Protesters run for cover during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict46.jpg) Protesters carry a wounded man during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011.Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)
Protesters carry a wounded man during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011.Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict47.jpg) A protester on a motorcycle chants slogans during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)
A protester on a motorcycle chants slogans during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict48.jpg) An Egyptian riot police officer fires tear gas during clashes with protesters near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)
An Egyptian riot police officer fires tear gas during clashes with protesters near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict49.jpg) Egyptian protesters and riot police face off in Alexandria, Egypt, Monday, Nov. 21, 2011. Security forces fired tear gas and clashed Monday with several thousand protesters in Cairo’s Tahrir Square in the third straight day of violence that has killed dozens of people and has turned into the most sustained challenge yet to the rule of Egypt’s military.
Egyptian protesters and riot police face off in Alexandria, Egypt, Monday, Nov. 21, 2011. Security forces fired tear gas and clashed Monday with several thousand protesters in Cairo’s Tahrir Square in the third straight day of violence that has killed dozens of people and has turned into the most sustained challenge yet to the rule of Egypt’s military.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict50.jpg) Protesters gather in Tahrir Square in Cairo, Egypt, Monday, Nov. 21, 2011. Security forces fired tear gas and clashed Monday with several thousand protesters in Cairo’s Tahrir Square in the third straight day of violence that has killed dozens of people and has turned into the most sustained challenge yet to the rule of Egypt’s military.(Khalil Hamra)
Protesters gather in Tahrir Square in Cairo, Egypt, Monday, Nov. 21, 2011. Security forces fired tear gas and clashed Monday with several thousand protesters in Cairo’s Tahrir Square in the third straight day of violence that has killed dozens of people and has turned into the most sustained challenge yet to the rule of Egypt’s military.(Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict51.jpg) Protesters evacuate a wounded man during clashes with Egyptian riot police to a field hospital near Tahrir Square in Cairo, Egypt, Monday, Nov. 21, 2011. Security forces fired tear gas and clashed Monday with several thousand protesters in Cairo’s Tahrir Square in the third straight day of violence that has killed at least two dozen people and has turned into the most sustained challenge yet to the rule of Egypt’s military. (Tara Todras-Whitehill)
Protesters evacuate a wounded man during clashes with Egyptian riot police to a field hospital near Tahrir Square in Cairo, Egypt, Monday, Nov. 21, 2011. Security forces fired tear gas and clashed Monday with several thousand protesters in Cairo’s Tahrir Square in the third straight day of violence that has killed at least two dozen people and has turned into the most sustained challenge yet to the rule of Egypt’s military. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict52.jpg) Canadian volunteer nurse, Merikel, below right, helps an Egyptian medical team to treat an injured protester at a field hospital at Tahrir Square in Cairo, Egypt, Monday, Nov. 21, 2011. Egyptian riot police clashed Monday with thousands of protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. (Amr Nabil)
Canadian volunteer nurse, Merikel, below right, helps an Egyptian medical team to treat an injured protester at a field hospital at Tahrir Square in Cairo, Egypt, Monday, Nov. 21, 2011. Egyptian riot police clashed Monday with thousands of protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. (Amr Nabil)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict53.jpg) Egyptian protesters throw stones at Egyptian riot police, unseen, in Tahrir Square in Cairo, Egypt, Monday, Nov. 21, 2011. Police are clashing for a third day in Cairo’s central Tahrir Square with stone-throwing protesters demanding the country’s military rulers quickly transfer power to a civilian government. (Ahmed Ali)
Egyptian protesters throw stones at Egyptian riot police, unseen, in Tahrir Square in Cairo, Egypt, Monday, Nov. 21, 2011. Police are clashing for a third day in Cairo’s central Tahrir Square with stone-throwing protesters demanding the country’s military rulers quickly transfer power to a civilian government. (Ahmed Ali)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict54.jpg) Protesters throw stones as they take cover during clashes with Egyptian riot police near the interior ministry in downtown Cairo, Egypt, Sunday, Nov. 20, 2011. Firing tear gas and rubber bullets, Egyptian riot police on Sunday clashed for a second day with thousands of rock-throwing protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. The police battled an estimated 5,000 protesters in and around central Cairo’s Tahrir Square.
Protesters throw stones as they take cover during clashes with Egyptian riot police near the interior ministry in downtown Cairo, Egypt, Sunday, Nov. 20, 2011. Firing tear gas and rubber bullets, Egyptian riot police on Sunday clashed for a second day with thousands of rock-throwing protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. The police battled an estimated 5,000 protesters in and around central Cairo’s Tahrir Square.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict55.jpg) Tear gas surrounds Egyptian riot police as they stand guard during clashes in Tahrir Square in Cairo, Egypt, Saturday, Nov. 19, 2011. Thousands of police clashed with protesters for control of downtown Cairo’s Tahrir Square on Saturday after security forces tried to stop activists from staging a long-term sit-in there. The violence took place just nine days before Egypt’s first elections since the ouster of longtime President Hosni Mubarak in February. (Khalil Hamra)
Tear gas surrounds Egyptian riot police as they stand guard during clashes in Tahrir Square in Cairo, Egypt, Saturday, Nov. 19, 2011. Thousands of police clashed with protesters for control of downtown Cairo’s Tahrir Square on Saturday after security forces tried to stop activists from staging a long-term sit-in there. The violence took place just nine days before Egypt’s first elections since the ouster of longtime President Hosni Mubarak in February. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict56.jpg) Egyptian riot police clash with protesters in Tahrir Square in Cairo, Egypt, Saturday, Nov. 19, 2011. Egyptian riot police beat protesters and dismantled a small tent city set up to commemorate revolutionary martyrs in Cairo’s Tahrir Square on Saturday. The clashes occurred after activists camped in the central square overnight following a massive Friday rally. The military tolerates daytime demonstrations in the central square, a symbol of the country’s Jan. 25-Feb. 11 uprising.
Egyptian riot police clash with protesters in Tahrir Square in Cairo, Egypt, Saturday, Nov. 19, 2011. Egyptian riot police beat protesters and dismantled a small tent city set up to commemorate revolutionary martyrs in Cairo’s Tahrir Square on Saturday. The clashes occurred after activists camped in the central square overnight following a massive Friday rally. The military tolerates daytime demonstrations in the central square, a symbol of the country’s Jan. 25-Feb. 11 uprising.![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict54.jpg) In this Friday, Nov. 18, 2011, photo University of California, Davis Police Lt. John Pike uses pepper spray to move Occupy UC Davis protesters while blocking their exit from the school’s quad Friday in Davis, Calif. Two University of California, Davis police officers involved in pepper spraying seated protesters were placed on administrative leave Sunday, Nov. 20, 2011, as the chancellor of the school accelerates the investigation into the incident. (Wayne Tilcock)
In this Friday, Nov. 18, 2011, photo University of California, Davis Police Lt. John Pike uses pepper spray to move Occupy UC Davis protesters while blocking their exit from the school’s quad Friday in Davis, Calif. Two University of California, Davis police officers involved in pepper spraying seated protesters were placed on administrative leave Sunday, Nov. 20, 2011, as the chancellor of the school accelerates the investigation into the incident. (Wayne Tilcock)![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict55.jpg) In this Friday, Nov. 18, 2011, photo Occupy University of California, Davis, protesters including David Buscho, far left, react after being pepper sprayed by police who came to remove tents set up on the school’s quad Friday in Davis, Calif. Two University of California, Davis police officers involved in pepper spraying seated protesters were placed on administrative leave Sunday, Nov. 20, 2011, as the chancellor of the school accelerates the investigation into the incident. (Wayne Tilcock)
In this Friday, Nov. 18, 2011, photo Occupy University of California, Davis, protesters including David Buscho, far left, react after being pepper sprayed by police who came to remove tents set up on the school’s quad Friday in Davis, Calif. Two University of California, Davis police officers involved in pepper spraying seated protesters were placed on administrative leave Sunday, Nov. 20, 2011, as the chancellor of the school accelerates the investigation into the incident. (Wayne Tilcock)![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict53.jpg) In this Friday, Nov. 18, 2011, photo occupy protester David Buscho is helped after being pepper sprayed by campus police while blocking their exit from the school’s Quad Friday in Davis, Calif. Two University of California, Davis police officers involved in pepper spraying seated protesters were placed on administrative leave Sunday, Nov. 20, 2011, as the chancellor of the school accelerates the investigation into the incident. (Wayne Tilcock)
In this Friday, Nov. 18, 2011, photo occupy protester David Buscho is helped after being pepper sprayed by campus police while blocking their exit from the school’s Quad Friday in Davis, Calif. Two University of California, Davis police officers involved in pepper spraying seated protesters were placed on administrative leave Sunday, Nov. 20, 2011, as the chancellor of the school accelerates the investigation into the incident. (Wayne Tilcock)![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict31.jpg) In this image made from video, a police officer uses pepper spray as he walks down a line of Occupy demonstrators sitting on the ground at the University of California, Davis on Friday, Nov. 18, 2011. The video – posted on YouTube – was shot Friday as police moved in on more than a dozen tents erected on campus and arrested 10 people, nine of them students. AP
In this image made from video, a police officer uses pepper spray as he walks down a line of Occupy demonstrators sitting on the ground at the University of California, Davis on Friday, Nov. 18, 2011. The video – posted on YouTube – was shot Friday as police moved in on more than a dozen tents erected on campus and arrested 10 people, nine of them students. AP
![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict30.jpg) University of California, Davis, student Mike Fetterman, receives a treatment for pepper spray by UC Davis firefighter Nate Potter, after campus police dismantled an Occupy Wall Street encampment on the campus quad in Davis, Calif. , Friday, Nov. 18, 2011. UC Davis officials say eight men and two women were taken into custody. AP
University of California, Davis, student Mike Fetterman, receives a treatment for pepper spray by UC Davis firefighter Nate Potter, after campus police dismantled an Occupy Wall Street encampment on the campus quad in Davis, Calif. , Friday, Nov. 18, 2011. UC Davis officials say eight men and two women were taken into custody. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict33.jpg) A police officer uses pepper spray on an Occupy Portland protestor at Pioneer Courthouse Square in Portland Ore. , Thursday, Nov. 17, 2011. AP
A police officer uses pepper spray on an Occupy Portland protestor at Pioneer Courthouse Square in Portland Ore. , Thursday, Nov. 17, 2011. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict28.jpg) A protester affiliated with the Occupy Wall Street movement pours liquid over the eyes of another fellow protester to ease the pain from pepper spray during an unannounced raid by the New York City Police Department outside Zuccotti Park in New York, in the early hours of November 15, 2011. Police wearing helmets and carrying shields evicted protesters with the Occupy Wall Street movement early on Tuesday from the park in New York City’s financial district where they have camped since September. Reuters
A protester affiliated with the Occupy Wall Street movement pours liquid over the eyes of another fellow protester to ease the pain from pepper spray during an unannounced raid by the New York City Police Department outside Zuccotti Park in New York, in the early hours of November 15, 2011. Police wearing helmets and carrying shields evicted protesters with the Occupy Wall Street movement early on Tuesday from the park in New York City’s financial district where they have camped since September. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict34.jpg) Seattle Police officers deploy pepper spray into a crowd during an Occupy Seattle protest on Tuesday, Nov. 15, 2011 at Westlake Park in Seattle. Protesters gathered in the intersection of 5th Avenue and Pine Street after marching from their camp at Seattle Central Community College in support of Occupy Wall Street. Many refused to move from the intersection after being ordered by police. Police then began spraying pepper spray into the gathered crowd hitting dozens of people. AP
Seattle Police officers deploy pepper spray into a crowd during an Occupy Seattle protest on Tuesday, Nov. 15, 2011 at Westlake Park in Seattle. Protesters gathered in the intersection of 5th Avenue and Pine Street after marching from their camp at Seattle Central Community College in support of Occupy Wall Street. Many refused to move from the intersection after being ordered by police. Police then began spraying pepper spray into the gathered crowd hitting dozens of people. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict35.jpg) Seattle activist Dorli Rainey, 84, reacts after being hit with pepper spray during an Occupy Seattle protest on Tuesday, Nov. 15, 2011 at Westlake Park in Seattle. Protesters gathered in the intersection of 5th Avenue and Pine Street after marching from their camp at Seattle Central Community College in support of Occupy Wall Street. Many refused to move from the intersection after being ordered by police. Police then began spraying pepper spray into the gathered crowd hitting dozens of people. AP
Seattle activist Dorli Rainey, 84, reacts after being hit with pepper spray during an Occupy Seattle protest on Tuesday, Nov. 15, 2011 at Westlake Park in Seattle. Protesters gathered in the intersection of 5th Avenue and Pine Street after marching from their camp at Seattle Central Community College in support of Occupy Wall Street. Many refused to move from the intersection after being ordered by police. Police then began spraying pepper spray into the gathered crowd hitting dozens of people. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict36.jpg) A woman who gave her name as Jennifer and said she was two months pregnant is rushed to an ambulance after being hit with pepper spray at an Occupy Seattle protest on Tuesday, Nov. 15, 2011 at Westlake Park in Seattle. Protesters gathered in the intersection of 5th Avenue and Pine Street after marching from their camp at Seattle Central Community College in support of Occupy Wall Street. Many refused to move from the intersection after being ordered by police. Police then began spraying pepper spray into the gathered crowd hitting dozens of people. AP
A woman who gave her name as Jennifer and said she was two months pregnant is rushed to an ambulance after being hit with pepper spray at an Occupy Seattle protest on Tuesday, Nov. 15, 2011 at Westlake Park in Seattle. Protesters gathered in the intersection of 5th Avenue and Pine Street after marching from their camp at Seattle Central Community College in support of Occupy Wall Street. Many refused to move from the intersection after being ordered by police. Police then began spraying pepper spray into the gathered crowd hitting dozens of people. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict23.jpg) A man is treated by fellow protesters after he was sprayed in the face with pepper spray by police during the Occupy Seattle’s protest against JPMorgan Chase CEO Jamie Dimon in Seattle November 2, 2011. About 300 rain-soaked protesters blocked the street outside the Sheraton hotel where Dimon was scheduled to speak at an event organized by the University of Washington’s school of business. Reuters
A man is treated by fellow protesters after he was sprayed in the face with pepper spray by police during the Occupy Seattle’s protest against JPMorgan Chase CEO Jamie Dimon in Seattle November 2, 2011. About 300 rain-soaked protesters blocked the street outside the Sheraton hotel where Dimon was scheduled to speak at an event organized by the University of Washington’s school of business. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict24.jpg) A police officer escorts an Occupy Tulsa protestor who was pepper sprayed in the face while being arresting for an alleged curfew violation for inhabiting a city park at night at Centennial Green in downtown Tulsa, Okla. , early Wednesday morning Nov. 2, 2011. Police warned demonstrators that they were in violation of a city curfew and gave them the choice of leaving before applying pepper spray and forcibly removing demonstrators sitting in a circle at the park shortly before 2 a.m. AP
A police officer escorts an Occupy Tulsa protestor who was pepper sprayed in the face while being arresting for an alleged curfew violation for inhabiting a city park at night at Centennial Green in downtown Tulsa, Okla. , early Wednesday morning Nov. 2, 2011. Police warned demonstrators that they were in violation of a city curfew and gave them the choice of leaving before applying pepper spray and forcibly removing demonstrators sitting in a circle at the park shortly before 2 a.m. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict27.jpg) Protesters use a metal structure against riot police as the police use pepper spray against them during clashes outside the Greek parliament in Athens, Wednesday, Oct. 19, 2011. Greek anger over new austerity measures and layoffs erupted into violence outside parliament on Wednesday, as demonstrators hurled chunks of marble and gasoline bombs and riot police responded with tear gas and stun grenades that echoed across Athens’ main square. Wednesday was the first day of a two-day general strike that unions described as the largest protests in years, with at least 100,000 people marching through central Athens. AP
Protesters use a metal structure against riot police as the police use pepper spray against them during clashes outside the Greek parliament in Athens, Wednesday, Oct. 19, 2011. Greek anger over new austerity measures and layoffs erupted into violence outside parliament on Wednesday, as demonstrators hurled chunks of marble and gasoline bombs and riot police responded with tear gas and stun grenades that echoed across Athens’ main square. Wednesday was the first day of a two-day general strike that unions described as the largest protests in years, with at least 100,000 people marching through central Athens. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict42.jpg) A San Diego Police officer maces a demonstrator at the Civic Center Plaza Friday, Oct. 14, 2011 in San Diego. Police on Friday began removing about a half-dozen tents after warning demonstrators that their personal belongings couldn’t stay in the Occupy San Diego camp. (Lenny Ignelzi)
A San Diego Police officer maces a demonstrator at the Civic Center Plaza Friday, Oct. 14, 2011 in San Diego. Police on Friday began removing about a half-dozen tents after warning demonstrators that their personal belongings couldn’t stay in the Occupy San Diego camp. (Lenny Ignelzi)![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict26.jpg) A demonstrator receives help after San Diego Police used pepper spray during a demonstration at the Civic Center Plaza Friday, Oct. 14, 2011 in San Diego. Police on Friday began removing about a half-dozen tents after warning demonstrators that their personal belongings couldn’t stay in the Occupy San Diego camp. AP
A demonstrator receives help after San Diego Police used pepper spray during a demonstration at the Civic Center Plaza Friday, Oct. 14, 2011 in San Diego. Police on Friday began removing about a half-dozen tents after warning demonstrators that their personal belongings couldn’t stay in the Occupy San Diego camp. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict25.jpg) A demomstrator tries to wash pepper spray from his eyes after a clash with the San Diego Police at the Civic Center Plaza Friday, Oct. 14, 2011 in San Diego. Police on Friday began removing about a half-dozen tents after warning demonstrators that their personal belongings couldn’t stay in the Occupy San Diego camp. AP
A demomstrator tries to wash pepper spray from his eyes after a clash with the San Diego Police at the Civic Center Plaza Friday, Oct. 14, 2011 in San Diego. Police on Friday began removing about a half-dozen tents after warning demonstrators that their personal belongings couldn’t stay in the Occupy San Diego camp. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict29.jpg) Two demonstrators cover themselves after San Diego Police used pepper spray during a protest at the Civic Center Plaza Friday, Oct. 14, 2011 in San Diego. Police on Friday began removing about a half-dozen tents after warning demonstrators that their personal belongings couldn’t stay in the Occupy San Diego camp. AP
Two demonstrators cover themselves after San Diego Police used pepper spray during a protest at the Civic Center Plaza Friday, Oct. 14, 2011 in San Diego. Police on Friday began removing about a half-dozen tents after warning demonstrators that their personal belongings couldn’t stay in the Occupy San Diego camp. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict43.jpg) One demonstrator helps another flush her eyes with water after after police pepper-sprayed a group of protestors, who were trying to get into the National Air and Space Museum in Washington Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)
One demonstrator helps another flush her eyes with water after after police pepper-sprayed a group of protestors, who were trying to get into the National Air and Space Museum in Washington Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)
![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict44.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict45.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict46.jpg) NYPD Deputy Inspector Anthony Bologna sprays protestors, 26 September 2011. Charlie Grapski via Daily Kos
NYPD Deputy Inspector Anthony Bologna sprays protestors, 26 September 2011. Charlie Grapski via Daily Kos
![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict47.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict38.jpg) A protester is hit by pepper spray when police used them against protesters as they broke through a police cordon to carry out a sit-in protest in the Hong Kong’s central business district Friday, July 1, 2011, Tens of thousands people march to vent their anger over skyrocketing property prices and government policies, the 14th anniversary of the former British colony’s return to Chinese rule. AP
A protester is hit by pepper spray when police used them against protesters as they broke through a police cordon to carry out a sit-in protest in the Hong Kong’s central business district Friday, July 1, 2011, Tens of thousands people march to vent their anger over skyrocketing property prices and government policies, the 14th anniversary of the former British colony’s return to Chinese rule. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict40.jpg) A riot police reacts, after his colleagues used pepper spray, against protesters outside the Health Ministry in Athens, Thursday, May 26, 2011. Police have used pepper spray to disperse protesting doctors and state hospital staff, in the latest protest against public spending cuts.
A riot police reacts, after his colleagues used pepper spray, against protesters outside the Health Ministry in Athens, Thursday, May 26, 2011. Police have used pepper spray to disperse protesting doctors and state hospital staff, in the latest protest against public spending cuts.![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict39.jpg) Israeli riot police detain a man whose face was sprayed with pepper spray during riots in the East Jerusalem neighborhood of Issawiya on May 13, 2011 as Israeli police flooded the streets of Jerusalem, fearing violence as Palestinians began marking the ‘Nakba’ or ‘catastrophe’ which befell them following Israel’s establishment in 1948.
Israeli riot police detain a man whose face was sprayed with pepper spray during riots in the East Jerusalem neighborhood of Issawiya on May 13, 2011 as Israeli police flooded the streets of Jerusalem, fearing violence as Palestinians began marking the ‘Nakba’ or ‘catastrophe’ which befell them following Israel’s establishment in 1948.![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict41.jpg) Police spray pepper gas and water canons at protesters in Ankara, Turkey, Thursday, Feb. 3, 2011, trying to stop a march on Parliament by workers protesting government-proposed legislation that they say will strip them of their rights. About ten thousands of workers, many of whom had traveled from across Turkey, had gathered in the capital Ankara and vowed to reach Parliament in defiance of laws that bar demonstrations near the assembly building. AP
Police spray pepper gas and water canons at protesters in Ankara, Turkey, Thursday, Feb. 3, 2011, trying to stop a march on Parliament by workers protesting government-proposed legislation that they say will strip them of their rights. About ten thousands of workers, many of whom had traveled from across Turkey, had gathered in the capital Ankara and vowed to reach Parliament in defiance of laws that bar demonstrations near the assembly building. AP







![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict36.jpg) Members of the Galician pro-indepence group Ceive stage a protest in favor of the transfert of jailed Galician independentist to Galician jails, next to a polling station in the village of Escravitude, some 20 kms from Santiago de Compostela, northwestern Spain, on November 20, 2011. Spaniards voted in rain-swept elections Sunday that were all but certain to hand a thundering victory to the right and topple yet another debt-laden eurozone government. Bowed by a 21,5 percent jobless rate, economic stagnation and deep spending cuts, the first voters of the 36 million-strong Spanish electorate headed to polls ready to punish the ruling Socialists. Getty
Members of the Galician pro-indepence group Ceive stage a protest in favor of the transfert of jailed Galician independentist to Galician jails, next to a polling station in the village of Escravitude, some 20 kms from Santiago de Compostela, northwestern Spain, on November 20, 2011. Spaniards voted in rain-swept elections Sunday that were all but certain to hand a thundering victory to the right and topple yet another debt-laden eurozone government. Bowed by a 21,5 percent jobless rate, economic stagnation and deep spending cuts, the first voters of the 36 million-strong Spanish electorate headed to polls ready to punish the ruling Socialists. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict34.jpg) A protester gestures during clashes with Egyptian riot police, not seen, near the interior ministry in downtown Cairo, Egypt, Sunday, Nov. 20, 2011. Firing tear gas and rubber bullets, Egyptian riot police on Sunday clashed for a second day with thousands of rock-throwing protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. (Tara Todras-Whitehill)
A protester gestures during clashes with Egyptian riot police, not seen, near the interior ministry in downtown Cairo, Egypt, Sunday, Nov. 20, 2011. Firing tear gas and rubber bullets, Egyptian riot police on Sunday clashed for a second day with thousands of rock-throwing protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict33.jpg) A protester overcome with tear gas inhalation is helped inside a cafe during clashes with the Egyptian riot police, not seen, near the interior ministry in downtown Cairo, Egypt, Sunday, Nov. 20, 2011. Firing tear gas and rubber bullets, Egyptian riot police on Sunday clashed for a second day with thousands of rock-throwing protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. (Tara Todras-Whitehill)
A protester overcome with tear gas inhalation is helped inside a cafe during clashes with the Egyptian riot police, not seen, near the interior ministry in downtown Cairo, Egypt, Sunday, Nov. 20, 2011. Firing tear gas and rubber bullets, Egyptian riot police on Sunday clashed for a second day with thousands of rock-throwing protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict35.jpg) Wounded protesters are seen in a field hospital during clashes with Egyptian riot police in Tahrir Square in Cairo, Egypt, Sunday, Nov. 20, 2011. Firing tear gas and rubber bullets, Egyptian riot police on Sunday clashed for a second day with thousands of rock-throwing protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. (Khalil Hamra)
Wounded protesters are seen in a field hospital during clashes with Egyptian riot police in Tahrir Square in Cairo, Egypt, Sunday, Nov. 20, 2011. Firing tear gas and rubber bullets, Egyptian riot police on Sunday clashed for a second day with thousands of rock-throwing protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict25.jpg) Occupy Oakland protester Abby Balanda demonstrates during a march through Oakland, Calif., on Saturday, Nov. 19, 2011. Anti-Wall Street protesters in Oakland pushed down a chain-link fence surrounding a city-owned vacant lot where they planned a new encampment on Saturday. (Noah Berger)
Occupy Oakland protester Abby Balanda demonstrates during a march through Oakland, Calif., on Saturday, Nov. 19, 2011. Anti-Wall Street protesters in Oakland pushed down a chain-link fence surrounding a city-owned vacant lot where they planned a new encampment on Saturday. (Noah Berger)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict28.jpg) An Occupy Oakland protester, who declined to give her name, pitches a tent to establish a new encampment in Oakland, Calif., on Saturday, Nov. 19, 2011. Police raided the group’s previous camp on Monday. Anti-Wall Street protesters in Oakland pushed down a chain-link fence surrounding a city-owned vacant lot where they planned a new encampment on Saturday. (Noah Berger)
An Occupy Oakland protester, who declined to give her name, pitches a tent to establish a new encampment in Oakland, Calif., on Saturday, Nov. 19, 2011. Police raided the group’s previous camp on Monday. Anti-Wall Street protesters in Oakland pushed down a chain-link fence surrounding a city-owned vacant lot where they planned a new encampment on Saturday. (Noah Berger)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict29.jpg) A police officer arrests a demonstrator affiliated with the Occupy Wall Street movement as they block the entrance to the New York Stock Exchange on Broad Street, Thursday, Nov. 17, 2011 in New York. Two days after the encampment that sparked the global Occupy protest movement was cleared by authorities, demonstrators marched through New York’s financial district and promised a national day of action with mass gatherings in other cities. (Mary Altaffer)
A police officer arrests a demonstrator affiliated with the Occupy Wall Street movement as they block the entrance to the New York Stock Exchange on Broad Street, Thursday, Nov. 17, 2011 in New York. Two days after the encampment that sparked the global Occupy protest movement was cleared by authorities, demonstrators marched through New York’s financial district and promised a national day of action with mass gatherings in other cities. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict30.jpg) Police officers arrest a demonstrator affiliated with the Occupy Wall Street movement, Thursday, Nov. 17, 2011 in New York. Two days after the encampment that sparked the global Occupy protest movement was cleared by authorities, demonstrators marched through New York’s financial district and promised a national day of action with mass gatherings in other cities. (Mary Altaffer)
Police officers arrest a demonstrator affiliated with the Occupy Wall Street movement, Thursday, Nov. 17, 2011 in New York. Two days after the encampment that sparked the global Occupy protest movement was cleared by authorities, demonstrators marched through New York’s financial district and promised a national day of action with mass gatherings in other cities. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict21.jpg) Naked Israeli women pose for a photograph in Tel Aviv, November 19, 2011, to show solidarity with Egyptian blogger Aliaa Magda Elmahdy, who put naked pictures of herself on the Internet, support free expression and protest against Islamic extremism. The banner reads: “Love With No Boundaries”. Picture taken November 19, 2011. Reuters
Naked Israeli women pose for a photograph in Tel Aviv, November 19, 2011, to show solidarity with Egyptian blogger Aliaa Magda Elmahdy, who put naked pictures of herself on the Internet, support free expression and protest against Islamic extremism. The banner reads: “Love With No Boundaries”. Picture taken November 19, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict23.jpg) Tibetan Buddhist nun Palden Choetso sits in a house, in this handout picture taken in 1998 and recently released by the
Tibetan Buddhist nun Palden Choetso sits in a house, in this handout picture taken in 1998 and recently released by the ![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict24.jpg) Activists are blocked by the police during a march against the use of fur on November 19, 2011 in Paris, France. The march, in its third year, is held to protest the use of animal fur in fashion and animal cruelty. Getty
Activists are blocked by the police during a march against the use of fur on November 19, 2011 in Paris, France. The march, in its third year, is held to protest the use of animal fur in fashion and animal cruelty. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict27.jpg) Pro-Syrian regime protesters shout pro-Syrian President Bashar Assad slogans during a demonstration to show their soldarity with their president, in Damascus, Syria, on Sunday Nov. 20, 2011. Residents in the Syrian capital awoke to two loud explosions Sunday amid reports from activists that the Damascus headquarters of the ruling Baath party had been hit by several rocket-propelled grenades. But eyewitnesses said the party headquarters appeared intact and reported no significant security deployments.
Pro-Syrian regime protesters shout pro-Syrian President Bashar Assad slogans during a demonstration to show their soldarity with their president, in Damascus, Syria, on Sunday Nov. 20, 2011. Residents in the Syrian capital awoke to two loud explosions Sunday amid reports from activists that the Damascus headquarters of the ruling Baath party had been hit by several rocket-propelled grenades. But eyewitnesses said the party headquarters appeared intact and reported no significant security deployments.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict15.jpg) Women supporters hold placards during a protest organised by Awami National Conference in Srinagar on November 19, 2011. The protesters demanded revocation of Armed Forces Special Powers Act in restive Kashmir. The draconian Armed Forces Special Powers Act (AFSPA) was introduced in 1990 to give the army and paramilitary forces sweeping powers to detain people, use deadly force and destroy property. Violence is at its lowest in Indian Kashmir since the start of the insurgency that has so far left more than 47,000 people dead by official count but separatists putting the toll twice as high. Getty
Women supporters hold placards during a protest organised by Awami National Conference in Srinagar on November 19, 2011. The protesters demanded revocation of Armed Forces Special Powers Act in restive Kashmir. The draconian Armed Forces Special Powers Act (AFSPA) was introduced in 1990 to give the army and paramilitary forces sweeping powers to detain people, use deadly force and destroy property. Violence is at its lowest in Indian Kashmir since the start of the insurgency that has so far left more than 47,000 people dead by official count but separatists putting the toll twice as high. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict14.jpg) Spain’s ‘indignant’ protesters demostrate in the Puerta del Sol square in Madrid on November 19, 2011 against spending cuts, high unemployment and political corruption, a week before a general election. Spain’s so-called ‘indignant’ protest movement was born when thousands of people set up camp in Madrid’s Puerta del Sol square ahead of May 22 municipal elections. Getty
Spain’s ‘indignant’ protesters demostrate in the Puerta del Sol square in Madrid on November 19, 2011 against spending cuts, high unemployment and political corruption, a week before a general election. Spain’s so-called ‘indignant’ protest movement was born when thousands of people set up camp in Madrid’s Puerta del Sol square ahead of May 22 municipal elections. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict6.jpg) A female protester gestures as she argues with Egyptian riot police officers in Tahrir Square in Cairo, Egypt, Saturday, Nov. 19, 2011. Egyptian riot police beat protesters and dismantled a small tent city set up to commemorate revolutionary martyrs in Cairo’s Tahrir Square on Saturday. (Khalil Hamra)
A female protester gestures as she argues with Egyptian riot police officers in Tahrir Square in Cairo, Egypt, Saturday, Nov. 19, 2011. Egyptian riot police beat protesters and dismantled a small tent city set up to commemorate revolutionary martyrs in Cairo’s Tahrir Square on Saturday. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict9.jpg) Egyptian women wave flags during a rally in Cairo’s Tahrir square, Egypt, Friday, Nov.18, 2011, in a protest against what they say are attempts by the country’s military rulers to reinforce their powers. The rally Friday was dominated by the country’s most organized political group, the Muslim Brotherhood.
Egyptian women wave flags during a rally in Cairo’s Tahrir square, Egypt, Friday, Nov.18, 2011, in a protest against what they say are attempts by the country’s military rulers to reinforce their powers. The rally Friday was dominated by the country’s most organized political group, the Muslim Brotherhood.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict5.jpg) Egyptian Laila Soueif, at left, the mother of prominent blogger Alaa Abdel-Fattah who was jailed by Egypt’s ruling generals, who is on hunger strike to protest her son’s detention, as they celebrate Alaa’s 30th birthday in Cairo’s Tahrir square, Friday, Nov. 18, 2011. At Friday’s rally in Tahrir square, protesters gathered to celebrate the birthday of one of the most prominent revolutionary bloggers to be jailed by the military prosecutor. (Amr Nabil)
Egyptian Laila Soueif, at left, the mother of prominent blogger Alaa Abdel-Fattah who was jailed by Egypt’s ruling generals, who is on hunger strike to protest her son’s detention, as they celebrate Alaa’s 30th birthday in Cairo’s Tahrir square, Friday, Nov. 18, 2011. At Friday’s rally in Tahrir square, protesters gathered to celebrate the birthday of one of the most prominent revolutionary bloggers to be jailed by the military prosecutor. (Amr Nabil)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict2.jpg) Bahraini demonstrators gesture Friday, Nov. 18, 2011, in A’ali, Bahrain, in front of a replica of the massive protest encampment that was demolished by government forces last spring in the crackdown on a pro-democracy uprising, complete with tents and a model of the landmark pearl monument (unseen). Thousands of Shiite-led protesters calling for greater rights streamed into the area outside the capital of Manama in one of the largest demonstrations in weeks against the Gulf kingdom’s rulers.
Bahraini demonstrators gesture Friday, Nov. 18, 2011, in A’ali, Bahrain, in front of a replica of the massive protest encampment that was demolished by government forces last spring in the crackdown on a pro-democracy uprising, complete with tents and a model of the landmark pearl monument (unseen). Thousands of Shiite-led protesters calling for greater rights streamed into the area outside the capital of Manama in one of the largest demonstrations in weeks against the Gulf kingdom’s rulers.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict16.jpg) Muslims rally in Foley Square during a protest of ethnic profiling by law enforcement on November 18, 2011 in New York City. Muslims held a rally and Friday prayers and were joined by protesters affiliated with Occupy Wall Street. Getty
Muslims rally in Foley Square during a protest of ethnic profiling by law enforcement on November 18, 2011 in New York City. Muslims held a rally and Friday prayers and were joined by protesters affiliated with Occupy Wall Street. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict17.jpg) Animal activists, painted in “blood”, lie on a pile of fur during a protest in Belgrade November 18, 2011. The protest was held in conjunction with the “anti-fur” campaign in Europe. Reuters
Animal activists, painted in “blood”, lie on a pile of fur during a protest in Belgrade November 18, 2011. The protest was held in conjunction with the “anti-fur” campaign in Europe. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict19.jpg) Syrians living in Turkey write ‘Freedom’ with their blood during a protest against the government of Syria’s President Bashar al-Assad in front of the Syrian consulate in Istanbul, on November 18, 2011. Turkey added its voice Friday to warnings that civil war threatens Syria, while France’s top diplomat called for stepped up sanctions against Damascus, which he said had left it too late to reform. Getty
Syrians living in Turkey write ‘Freedom’ with their blood during a protest against the government of Syria’s President Bashar al-Assad in front of the Syrian consulate in Istanbul, on November 18, 2011. Turkey added its voice Friday to warnings that civil war threatens Syria, while France’s top diplomat called for stepped up sanctions against Damascus, which he said had left it too late to reform. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict20.jpg) Opponents of ousted Thai premier Thaksin Shinawatra hold banners as they shout during a protest in central Bangkok November 18, 2011. Opponents of Thaksin Shinawatra said on Thursday they could take to the streets if the government led by his sister tried to push through an amnesty that would let him return from exile a free man. Reuters
Opponents of ousted Thai premier Thaksin Shinawatra hold banners as they shout during a protest in central Bangkok November 18, 2011. Opponents of Thaksin Shinawatra said on Thursday they could take to the streets if the government led by his sister tried to push through an amnesty that would let him return from exile a free man. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict0.jpg) Muslims listen during a rally in Foley Square to protest against the NYPD surveillance operations of Muslim communities, Friday, Nov. 18, 2011, in New York. Hundreds of Muslims gathered in prayer Friday to oppose a decade of police spying on Muslim communities. The crowd filled about three-fourths of Foley Square in lower Manhattan, not far from City Hall. Demonstrators were scheduled to march on police headquarters (Bebeto Matthews)
Muslims listen during a rally in Foley Square to protest against the NYPD surveillance operations of Muslim communities, Friday, Nov. 18, 2011, in New York. Hundreds of Muslims gathered in prayer Friday to oppose a decade of police spying on Muslim communities. The crowd filled about three-fourths of Foley Square in lower Manhattan, not far from City Hall. Demonstrators were scheduled to march on police headquarters (Bebeto Matthews)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict3.jpg) Dorli Rainey, 84, left, who was pepper-sprayed by police last Tuesday while taking part in an “Occupy Seattle” protest, speaks Friday, Nov. 18, 2011, in front of police headquarters in downtown Seattle. Rainey and several dozen others marched to the station Friday and held the rally to call attention to how protesters have been treated. (Ted S. Warren)
Dorli Rainey, 84, left, who was pepper-sprayed by police last Tuesday while taking part in an “Occupy Seattle” protest, speaks Friday, Nov. 18, 2011, in front of police headquarters in downtown Seattle. Rainey and several dozen others marched to the station Friday and held the rally to call attention to how protesters have been treated. (Ted S. Warren)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict4.jpg) Virila Perez, left, and Francisco Gonzalez, who work as municipal trash collectors, demonstrate against proposed lay-offs by lying on broken glass in Asuncion, Paraguay, Friday Nov. 18, 2011. Asuncion’s municipal government is proposing cuts in employment to reduce the cost of municipal workers to 60% of the city budget. The sign covering them reads in Spanish “Until the final fight, overcome or die.” (Jorge Saenz)
Virila Perez, left, and Francisco Gonzalez, who work as municipal trash collectors, demonstrate against proposed lay-offs by lying on broken glass in Asuncion, Paraguay, Friday Nov. 18, 2011. Asuncion’s municipal government is proposing cuts in employment to reduce the cost of municipal workers to 60% of the city budget. The sign covering them reads in Spanish “Until the final fight, overcome or die.” (Jorge Saenz)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict22.jpg) Annette Jones waits with other demonstrators to be arrested during a protest organized by Occupy Chicago and Stand Up Chicago November 17, 2011 in Chicago, Illinois. The demonstration was one of many protests held nationwide to mark the second month of the Occupy Wall Street protests. Getty
Annette Jones waits with other demonstrators to be arrested during a protest organized by Occupy Chicago and Stand Up Chicago November 17, 2011 in Chicago, Illinois. The demonstration was one of many protests held nationwide to mark the second month of the Occupy Wall Street protests. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict10.jpg) Occupy Seattle protestors demonstrate at the University Bridge, temporarily shutting it down, after meeting others from Seattle Central Community College during a national day of action, Thursday, Nov. 17, 2011, in Seattle. Traffic was snarled around Seattle’s University District as two rallies marched toward the bridge. (Kevin P. Casey)
Occupy Seattle protestors demonstrate at the University Bridge, temporarily shutting it down, after meeting others from Seattle Central Community College during a national day of action, Thursday, Nov. 17, 2011, in Seattle. Traffic was snarled around Seattle’s University District as two rallies marched toward the bridge. (Kevin P. Casey)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict7.jpg) Eugene Police officers carry an Occupy Eugene protester away after arresting her for blocking the entrance to a Chase Bank in Eugene, Ore. Nov. 17, 2011. Occupy Eugene protesters spent an afternoon demonstrating at bank offices, and 17 were arrested. (Chris Pietsch)
Eugene Police officers carry an Occupy Eugene protester away after arresting her for blocking the entrance to a Chase Bank in Eugene, Ore. Nov. 17, 2011. Occupy Eugene protesters spent an afternoon demonstrating at bank offices, and 17 were arrested. (Chris Pietsch)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict11.jpg) A Occupy Portland protester is arrested by Portland Police officers after protesters take over a Wells Fargo bank Thursday, Nov. 17, 2011, in Portland, Ore. Occupy Wall Street demonstrators held modestly sized, but energetic rallies around the country Thursday to celebrate two months since the movement’s birth and signal that they aren’t ready to quit yet, despite police raids that have destroyed some of their encampments. (Rick Bowmer)
A Occupy Portland protester is arrested by Portland Police officers after protesters take over a Wells Fargo bank Thursday, Nov. 17, 2011, in Portland, Ore. Occupy Wall Street demonstrators held modestly sized, but energetic rallies around the country Thursday to celebrate two months since the movement’s birth and signal that they aren’t ready to quit yet, despite police raids that have destroyed some of their encampments. (Rick Bowmer)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict8.jpg) Occupy Wall Street protesters walk across the Brooklyn Bridge after a rally in Foley Square, Thursday, Nov. 17, 2011 in New York. Organizers with the Service Employees International Union and progressive groups staged similar bridge marches in several cities in an event that was planned weeks ago, but happened to coincide with rallies marking two months since the start of the Occupy movement (Henny Ray Abrams)
Occupy Wall Street protesters walk across the Brooklyn Bridge after a rally in Foley Square, Thursday, Nov. 17, 2011 in New York. Organizers with the Service Employees International Union and progressive groups staged similar bridge marches in several cities in an event that was planned weeks ago, but happened to coincide with rallies marking two months since the start of the Occupy movement (Henny Ray Abrams)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict12.jpg) Protesters willing to be arrested, including Donna Cassult, left, of Minneapolis, linked arms and sat on the roadway of the 10th Ave. Bridge in Minneapolis and waited for police to place them in custody Thursday, Nov. 17, 2011. Demonstrators peacefully shut down the 10th Ave. Bridge during rush hour to call attention to the need for more jobs and racial equality in employment.
Protesters willing to be arrested, including Donna Cassult, left, of Minneapolis, linked arms and sat on the roadway of the 10th Ave. Bridge in Minneapolis and waited for police to place them in custody Thursday, Nov. 17, 2011. Demonstrators peacefully shut down the 10th Ave. Bridge during rush hour to call attention to the need for more jobs and racial equality in employment.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict13.jpg) Police officers arrest a demonstrators affiliated with the Occupy Wall Street movement, Thursday, Nov. 17, 2011 in New York. Two days after the encampment that sparked the global Occupy protest movement was cleared by authorities, demonstrators marched through New York’s financial district and promised a national day of action with mass gatherings in other cities. (Mary Altaffer)
Police officers arrest a demonstrators affiliated with the Occupy Wall Street movement, Thursday, Nov. 17, 2011 in New York. Two days after the encampment that sparked the global Occupy protest movement was cleared by authorities, demonstrators marched through New York’s financial district and promised a national day of action with mass gatherings in other cities. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/Aliaa-Magda-Elmahdy-nude-30.jpg) 20-year-old Egyptian blogger Aliaa Mahdy. Photograph: Aliaa Mahdy
20-year-old Egyptian blogger Aliaa Mahdy. Photograph: Aliaa Mahdy![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict8.jpg) Spanish ‘indignant’ protesters hold a placard reading ‘We do not want fascists’ during a protest in front of a campaign meeting of the far-right party ‘Plataforma per Catalunya’ on November 13, 2011 in Barcelona. Hundreds of Spain’s ‘indignant’ protesters marched through the streets of Madrid Sunday to protest spending cuts, high unemployment and political corruption, a week before a general election. In Barcelona about 30 members of the movement decided at an assembly Saturday to camp out in the Plaza de Catalunya until the general election on November 20. Getty
Spanish ‘indignant’ protesters hold a placard reading ‘We do not want fascists’ during a protest in front of a campaign meeting of the far-right party ‘Plataforma per Catalunya’ on November 13, 2011 in Barcelona. Hundreds of Spain’s ‘indignant’ protesters marched through the streets of Madrid Sunday to protest spending cuts, high unemployment and political corruption, a week before a general election. In Barcelona about 30 members of the movement decided at an assembly Saturday to camp out in the Plaza de Catalunya until the general election on November 20. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict0.jpg) Two girls holds a coffin with a doll inside that wearing a mask with the faces of presidential candidates of Popular Party Mariano Rajoy and Socialist Party Alfredo Perez Rubalcaba during a demonstration against the government and banks in Madrid on Sunday, Nov. 13, 2011. Spain goes to the polls for presidential elections on November 20. (Arturo Rodriguez)
Two girls holds a coffin with a doll inside that wearing a mask with the faces of presidential candidates of Popular Party Mariano Rajoy and Socialist Party Alfredo Perez Rubalcaba during a demonstration against the government and banks in Madrid on Sunday, Nov. 13, 2011. Spain goes to the polls for presidential elections on November 20. (Arturo Rodriguez)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict10.jpg) Public workers march during a protest in Lisbon’s main avenue of Liberdade November 12, 2011. Public workers, policemen and military personnel are holding several protests in Lisbon against the job and 2012 state budget cuts. Reuters
Public workers march during a protest in Lisbon’s main avenue of Liberdade November 12, 2011. Public workers, policemen and military personnel are holding several protests in Lisbon against the job and 2012 state budget cuts. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict9.jpg) A woman holds up a sign that reads “No is No” as she takes part in the “Marcha de las Putas” (SlutWalk), held to protest against discrimination and violence against women in Lima, November 12, 2011. The march is part of the SlutWalk protest movement which started after a policeman advised women students in Canada to “avoid dressing like sluts”. Reuters
A woman holds up a sign that reads “No is No” as she takes part in the “Marcha de las Putas” (SlutWalk), held to protest against discrimination and violence against women in Lima, November 12, 2011. The march is part of the SlutWalk protest movement which started after a policeman advised women students in Canada to “avoid dressing like sluts”. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict1.jpg) Pro-Syrian regime protesters, hold up portraits of Syrian President Bashar Assad with Arabic words: ” The lion (Assad) of resistance and the rejectionism” during a demonstration against the Arab League decision to suspend Syria in front the Syrian embassy, in Beirut, Lebanon, on Sunday Nov. 13, 2011. Tens of thousands of pro-regime demonstrators gathered in a Damascus square Sunday to protest the Arab League’s vote to suspend Syria over its bloody crackdown on the country’s eight-month-old uprising.
Pro-Syrian regime protesters, hold up portraits of Syrian President Bashar Assad with Arabic words: ” The lion (Assad) of resistance and the rejectionism” during a demonstration against the Arab League decision to suspend Syria in front the Syrian embassy, in Beirut, Lebanon, on Sunday Nov. 13, 2011. Tens of thousands of pro-regime demonstrators gathered in a Damascus square Sunday to protest the Arab League’s vote to suspend Syria over its bloody crackdown on the country’s eight-month-old uprising.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict7.jpg) Syrian protesters shout anti-Syrian Preident Bashar Assad slogans during a protest in front of the Arab League headquarters in Cairo, Egypt, Saturday, Nov.12, 2011 where the League emergency session on Syria is to discuss the country’s failure to end bloodshed caused by government crackdowns on civil protests. Protesters called the Arab League to suspend the country’s membership. Arabic read ” step out, we need to build civilian modern country” (Amr Nabil)
Syrian protesters shout anti-Syrian Preident Bashar Assad slogans during a protest in front of the Arab League headquarters in Cairo, Egypt, Saturday, Nov.12, 2011 where the League emergency session on Syria is to discuss the country’s failure to end bloodshed caused by government crackdowns on civil protests. Protesters called the Arab League to suspend the country’s membership. Arabic read ” step out, we need to build civilian modern country” (Amr Nabil)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict5.jpg) Demonstrators with cooking pots and colanders on their heads stand in front of the European Central Bank in Frankfurt, Germany, Saturday, Nov.12, 2011. Thousands of people formed a human chain around the Frankfurt bank towers protesting against the power of banks. German police say more than ten thousand people are protesting against the banks’ dominance in two of the country’s major cities.
Demonstrators with cooking pots and colanders on their heads stand in front of the European Central Bank in Frankfurt, Germany, Saturday, Nov.12, 2011. Thousands of people formed a human chain around the Frankfurt bank towers protesting against the power of banks. German police say more than ten thousand people are protesting against the banks’ dominance in two of the country’s major cities.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict2.jpg) A group of protesters prepare their signs before heading out into the ocean to hold an anti-APEC protest at Waikiki Beach in Honolulu on Saturday, Nov. 12, 2011 as the summit is held in Oahu over the weekend. (Marco Garcia)
A group of protesters prepare their signs before heading out into the ocean to hold an anti-APEC protest at Waikiki Beach in Honolulu on Saturday, Nov. 12, 2011 as the summit is held in Oahu over the weekend. (Marco Garcia)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict4.jpg) Demonstrators hold a ribbon reading “smash banks, redistribute wealth” in front of the European Central Bank in Frankfurt, Germany, Saturday, Nov.12, 2011. Thousands of people formed a human chain with the ribbon around the Frankfurt bank towers to protest against the power of banks.Thousands of people formed a human chain around the Frankfurt bank towers protesting against the worldwide power of banks. German police say more than ten thousand people are protesting against the banks’ dominance in two of the country’s major cities.
Demonstrators hold a ribbon reading “smash banks, redistribute wealth” in front of the European Central Bank in Frankfurt, Germany, Saturday, Nov.12, 2011. Thousands of people formed a human chain with the ribbon around the Frankfurt bank towers to protest against the power of banks.Thousands of people formed a human chain around the Frankfurt bank towers protesting against the worldwide power of banks. German police say more than ten thousand people are protesting against the banks’ dominance in two of the country’s major cities.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict3.jpg) Protestors march through downtown Lisbon during a demonstration by military personnel associations against austerity measures Saturday, Nov. 12 2011. The Portuguese government plans to introduce more pay cuts and steep tax hikes next year while the country is struggling to restore its fiscal health despite a euro78 billion ($106 billion) bailout earlier this year. Banner reads ” Amnesty for the military punished for offenses of opinion” refering to military who have been punished for taking part in protests.
Protestors march through downtown Lisbon during a demonstration by military personnel associations against austerity measures Saturday, Nov. 12 2011. The Portuguese government plans to introduce more pay cuts and steep tax hikes next year while the country is struggling to restore its fiscal health despite a euro78 billion ($106 billion) bailout earlier this year. Banner reads ” Amnesty for the military punished for offenses of opinion” refering to military who have been punished for taking part in protests.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict67.jpg) Students march against government plans to reform higher education in Medellin, Colombia, Thursday, Nov. 10, 2011. Thousands of students march in the country’s main cities despite President Juan Manuel Santos’ proposal to withdraw a reform bill on higher education. (Luis Benavides)
Students march against government plans to reform higher education in Medellin, Colombia, Thursday, Nov. 10, 2011. Thousands of students march in the country’s main cities despite President Juan Manuel Santos’ proposal to withdraw a reform bill on higher education. (Luis Benavides)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict80.jpg) A UCLA student arrested by Los Angeles Police Department officers after she attempted to escape after eleven student protesters sat in circle in middle of the Westwood and Wilshire boulevard intersection as part of a protest of bank practices and rising fees at public universities on November 9, 2011 in Los Angeles, California. The protest organized by ReFund California was one of several planned at universities around the state. Getty
A UCLA student arrested by Los Angeles Police Department officers after she attempted to escape after eleven student protesters sat in circle in middle of the Westwood and Wilshire boulevard intersection as part of a protest of bank practices and rising fees at public universities on November 9, 2011 in Los Angeles, California. The protest organized by ReFund California was one of several planned at universities around the state. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict76.jpg) Students demonstrate against an education reform bill in Bogota, on November 10, 2011. Thousands of students from more than 30 public universities took to the streets in Colombia to protest against proposed education reforms they fear will partially privatize higher education. The students have been on strike over the past month to protest a bill put forward by President Juan Manuel Santos that would require public universities to generate some of their own revenues. On Wednesday Santos offered to withdraw the draft and open a dialogue if the more than half a million students on strike lift their form of pressure. Getty
Students demonstrate against an education reform bill in Bogota, on November 10, 2011. Thousands of students from more than 30 public universities took to the streets in Colombia to protest against proposed education reforms they fear will partially privatize higher education. The students have been on strike over the past month to protest a bill put forward by President Juan Manuel Santos that would require public universities to generate some of their own revenues. On Wednesday Santos offered to withdraw the draft and open a dialogue if the more than half a million students on strike lift their form of pressure. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict72.jpg) A demonstrator holds a banner against the ECB in Naples on November 11, 2011 during a rally called ‘Occupy Napoli’ (Occupy Naples), refering to the Occupy Wall Street movement in New York, to protest against banks and international financial power. Getty
A demonstrator holds a banner against the ECB in Naples on November 11, 2011 during a rally called ‘Occupy Napoli’ (Occupy Naples), refering to the Occupy Wall Street movement in New York, to protest against banks and international financial power. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict71.jpg) Hungarian and foreign activists and sympathizers of the ‘True Democracy Now’ group hold banners reading ‘Direct Democracy’ (R) and ‘Be part’, (L) as an elderly woman mouth’s is covered by a fake 1000 euro bill in front the central bank of Budapest on November 11, 2011 during a demonstration for a better and livable world and to protest against the political and economical system. Getty
Hungarian and foreign activists and sympathizers of the ‘True Democracy Now’ group hold banners reading ‘Direct Democracy’ (R) and ‘Be part’, (L) as an elderly woman mouth’s is covered by a fake 1000 euro bill in front the central bank of Budapest on November 11, 2011 during a demonstration for a better and livable world and to protest against the political and economical system. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict70.jpg) A protester holds a sign reading “Neither Tremonti nor Monti” during a protest in front of the Ministry of Finance in Rome November 11, 2011. The package of austerity measures that were demanded by the European Union will now go to the Italian lower house, which is expected to approve it on Saturday. That vote will trigger the resignation of Prime Minister Silvio Berlusconi. The signs refer to Italian Finance Minister Giulio Tremonti and former European Commissioner Mario Monti, who is tipped as the favourite to replace Berlusconi. Reuters
A protester holds a sign reading “Neither Tremonti nor Monti” during a protest in front of the Ministry of Finance in Rome November 11, 2011. The package of austerity measures that were demanded by the European Union will now go to the Italian lower house, which is expected to approve it on Saturday. That vote will trigger the resignation of Prime Minister Silvio Berlusconi. The signs refer to Italian Finance Minister Giulio Tremonti and former European Commissioner Mario Monti, who is tipped as the favourite to replace Berlusconi. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict73.jpg) A Yemeni woman covers her mouth with her hand painted in the colours of the national flag during to a protest against the regime of Ali Abdullah Saleh in the capital Sanaa, on November11, 2011. Forces loyal to Yemeni President Abdullah Saleh shelled the country’s second largest city Taez, killing nine people, among them two women and a child, a medic and witnesses said. Getty
A Yemeni woman covers her mouth with her hand painted in the colours of the national flag during to a protest against the regime of Ali Abdullah Saleh in the capital Sanaa, on November11, 2011. Forces loyal to Yemeni President Abdullah Saleh shelled the country’s second largest city Taez, killing nine people, among them two women and a child, a medic and witnesses said. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict74.jpg) A protester holding a banner camps outside the Banca d’Italia on November 11, 2011 in Venice, Italy. Protest in several Italian cities have been called by the Indignados, students, social centres and other organizations for today 11.11.11 to protest against financial insitutions and cuts proposed by the Government. Getty
A protester holding a banner camps outside the Banca d’Italia on November 11, 2011 in Venice, Italy. Protest in several Italian cities have been called by the Indignados, students, social centres and other organizations for today 11.11.11 to protest against financial insitutions and cuts proposed by the Government. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict69.jpg) Dalbir Kaur, sister of Indian national Sarabjit Singh on death row in Pakistan, second right, along with supporters of All India Youth Foundation takes an oath for securing his release in front of the India Gate war memorial at 11:11 am, in New Delhi, India, Friday, Nov. 11, 2011. A placard on left reads, “People’s Voice, Sarabjit.” (Gurinder Osan)
Dalbir Kaur, sister of Indian national Sarabjit Singh on death row in Pakistan, second right, along with supporters of All India Youth Foundation takes an oath for securing his release in front of the India Gate war memorial at 11:11 am, in New Delhi, India, Friday, Nov. 11, 2011. A placard on left reads, “People’s Voice, Sarabjit.” (Gurinder Osan)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict68.jpg) An Indonesian Muslim woman wears a Palestinian flag face mask during a solidarity protest for the Palestinian people in Jakarta, Indonesia, Thursday, Nov. 10, 2011. (Irwin Fedriansyah)
An Indonesian Muslim woman wears a Palestinian flag face mask during a solidarity protest for the Palestinian people in Jakarta, Indonesia, Thursday, Nov. 10, 2011. (Irwin Fedriansyah)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict77.jpg) Demonstrators of a group “Occupy Rio” protest against Rio de Janeiro’s governor Sergio Cabral in downtown Rio de Janeiro November 10, 2011. The demonstration, inspired by the Occupy Wall Street movement, seeks to address the corruption in the police and the problems with the health care system under the governance of Cabral. Cabral had originally organized a demonstration to rally against an oil reform amendment approved by the lower house of Congress. Reuters
Demonstrators of a group “Occupy Rio” protest against Rio de Janeiro’s governor Sergio Cabral in downtown Rio de Janeiro November 10, 2011. The demonstration, inspired by the Occupy Wall Street movement, seeks to address the corruption in the police and the problems with the health care system under the governance of Cabral. Cabral had originally organized a demonstration to rally against an oil reform amendment approved by the lower house of Congress. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict78.jpg) Protesters from the communist-affiliated trade union PAME shout slogans during an anti-government protest in Athens November 10, 2011. Greece named former European Central Bank vice-president Lucas Papademos on Thursday to head a crisis government, ending a chaotic search for a leader to save the country from default, bankruptcy and an exit from the euro zone. Reuters
Protesters from the communist-affiliated trade union PAME shout slogans during an anti-government protest in Athens November 10, 2011. Greece named former European Central Bank vice-president Lucas Papademos on Thursday to head a crisis government, ending a chaotic search for a leader to save the country from default, bankruptcy and an exit from the euro zone. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict64.jpg) A demonstrator marches during a student protest against government plans to reform higher education at the main square in Bogota, Colombia, Thursday, Nov. 10, 2011. Thousands of students marched in the country’s main cities despite a government proposal to withdraw a reform bill on higher education. (William Fernando Martinez)
A demonstrator marches during a student protest against government plans to reform higher education at the main square in Bogota, Colombia, Thursday, Nov. 10, 2011. Thousands of students marched in the country’s main cities despite a government proposal to withdraw a reform bill on higher education. (William Fernando Martinez)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict66.jpg) People wave flags of Rio de Janeiro state during a protest against an oil reform amendment in Rio de Janeiro, Brazil, Thursday, Nov. 10, 2011. Thousands of Brazilians are demonstrating against a plan that reduces revenue for oil-producing states and the federal government while increasing oil royalties for non-producing states. (Felipe Dana)
People wave flags of Rio de Janeiro state during a protest against an oil reform amendment in Rio de Janeiro, Brazil, Thursday, Nov. 10, 2011. Thousands of Brazilians are demonstrating against a plan that reduces revenue for oil-producing states and the federal government while increasing oil royalties for non-producing states. (Felipe Dana)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict65.jpg) Christian fundamentalist holds a candle during a demonstration against Italian director Romeo Castellucci’s play “On the Concept of the Face, Regarding the Son of God” in Rennes, western France, Thursday Nov. 10, 2011. Christian fundamentalists gathered outside the cultural palace the Theatre National de Bretagne, (National Theatre of Brittany), to protest against the play which they claim is blasphemous. (David Vincent)
Christian fundamentalist holds a candle during a demonstration against Italian director Romeo Castellucci’s play “On the Concept of the Face, Regarding the Son of God” in Rennes, western France, Thursday Nov. 10, 2011. Christian fundamentalists gathered outside the cultural palace the Theatre National de Bretagne, (National Theatre of Brittany), to protest against the play which they claim is blasphemous. (David Vincent)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict75.jpg) One of the students with peaceful attitude cleans the shield of a riot policemen that was stained with paint by more violent protesters, during a demonstration against an education reform bill at Bogota’s main square Plaza de Bolivar, on November 10, 2011. Thousands of students from more than 30 public universities took to the streets in Colombia to protest against proposed education reforms they fear will partially privatize higher education. The students have been on strike over the past month to protest a bill put forward by President Juan Manuel Santos that would require public universities to generate some of their own revenues. On Wednesday Santos offered to withdraw the draft and open a dialogue if the more than half a million students on strike lift their form of pressure. Getty
One of the students with peaceful attitude cleans the shield of a riot policemen that was stained with paint by more violent protesters, during a demonstration against an education reform bill at Bogota’s main square Plaza de Bolivar, on November 10, 2011. Thousands of students from more than 30 public universities took to the streets in Colombia to protest against proposed education reforms they fear will partially privatize higher education. The students have been on strike over the past month to protest a bill put forward by President Juan Manuel Santos that would require public universities to generate some of their own revenues. On Wednesday Santos offered to withdraw the draft and open a dialogue if the more than half a million students on strike lift their form of pressure. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict79.jpg) NOVEMBER 09: UCLA graduate student Cheryl Deutsch is arrested by Los Angeles Police Department officers after she and 10 other student protesters sat in circle in middle of the Westwood and Wilshire boulevard intersection as part of a protest of bank practices and rising fees at public universities on November 9, 2011 in Los Angeles, California. The protest organized by ReFund California was one of several planned at universities around the state. Getty
NOVEMBER 09: UCLA graduate student Cheryl Deutsch is arrested by Los Angeles Police Department officers after she and 10 other student protesters sat in circle in middle of the Westwood and Wilshire boulevard intersection as part of a protest of bank practices and rising fees at public universities on November 9, 2011 in Los Angeles, California. The protest organized by ReFund California was one of several planned at universities around the state. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict61.jpg) A woman shouts out as police officers move into the crowd of demonstrators and push people back during a student anti-cuts protest in London, Wednesday, Nov. 9, 2011. Thousands of students marched through central London on Wednesday to protest cuts to public spending and a big increase in university tuition fees. Police said there were “a number of arrests for public order offenses” Wednesday, but the march was largely peaceful as demonstrators made their way through the city center.
A woman shouts out as police officers move into the crowd of demonstrators and push people back during a student anti-cuts protest in London, Wednesday, Nov. 9, 2011. Thousands of students marched through central London on Wednesday to protest cuts to public spending and a big increase in university tuition fees. Police said there were “a number of arrests for public order offenses” Wednesday, but the march was largely peaceful as demonstrators made their way through the city center.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict62.jpg) A protester cries out as students and campaigners march through the streets of London in a protest against higher tuition fees and government cuts, Wednesday, Nov. 9, 2011. (Sang Tan)
A protester cries out as students and campaigners march through the streets of London in a protest against higher tuition fees and government cuts, Wednesday, Nov. 9, 2011. (Sang Tan)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict63.jpg) A lone protester stands outside the Scottsdale Plaza Resort to protest Republican Presidential candidate Herman Cain who was addressing the media Tuesday, Nov. 8, 2011, in Scottsdale, Ariz. Cain said Tuesday that he would not drop his bid for the Republicans’ presidential nomination in the face of decade-old allegations of inappropriate sexual behavior. (Charlie Leight)
A lone protester stands outside the Scottsdale Plaza Resort to protest Republican Presidential candidate Herman Cain who was addressing the media Tuesday, Nov. 8, 2011, in Scottsdale, Ariz. Cain said Tuesday that he would not drop his bid for the Republicans’ presidential nomination in the face of decade-old allegations of inappropriate sexual behavior. (Charlie Leight)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict59.jpg) Two members of People for the Ethical Treatment of Animals (PETA) who are covered from head to toe in green and blue bodypaint, as they hold a banner reading, “Save the Planet, Go Vegan,” at the Nanjing pedestrian street in Shanghai, China Wednesday, Nov. 9, 2011. (Eugene Hoshiko)
Two members of People for the Ethical Treatment of Animals (PETA) who are covered from head to toe in green and blue bodypaint, as they hold a banner reading, “Save the Planet, Go Vegan,” at the Nanjing pedestrian street in Shanghai, China Wednesday, Nov. 9, 2011. (Eugene Hoshiko)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict57.jpg) Protestors from Occupy Philly participate in a ‘die in’ demonstration outside a PNC Bank branch in Philadelphia on Monday Nov. 7, 2011. The demonstration was conducted to draw attention to PNC Bank’s business practices. (Joseph Kaczmarek)
Protestors from Occupy Philly participate in a ‘die in’ demonstration outside a PNC Bank branch in Philadelphia on Monday Nov. 7, 2011. The demonstration was conducted to draw attention to PNC Bank’s business practices. (Joseph Kaczmarek)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict54.jpg) A Syrian woman, who lives in Cairo, reacts as others wave a giant Syrian revolution flag during an anti-Syrian President Bashar Assad demonstration at Tahrir Square, the focal point of Egyptian uprisings, in Cairo, Egypt, Sunday, Nov. 6, 2011 to support protesters in Syria during the first day of Islamic Eid al-Adha, or Feast of the Sacrifice. (Amr Nabil)
A Syrian woman, who lives in Cairo, reacts as others wave a giant Syrian revolution flag during an anti-Syrian President Bashar Assad demonstration at Tahrir Square, the focal point of Egyptian uprisings, in Cairo, Egypt, Sunday, Nov. 6, 2011 to support protesters in Syria during the first day of Islamic Eid al-Adha, or Feast of the Sacrifice. (Amr Nabil)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict56.jpg) An activist of the Ukrainian female rights organization “Femen” shows a placard demanding freedom for women, during a protest at the end of Pope Benedict XVI’s Angelus prayer in St. Peter’s Square at the Vatican, Sunday, Nov. 6, 2011. (Pier Paolo Cito)
An activist of the Ukrainian female rights organization “Femen” shows a placard demanding freedom for women, during a protest at the end of Pope Benedict XVI’s Angelus prayer in St. Peter’s Square at the Vatican, Sunday, Nov. 6, 2011. (Pier Paolo Cito)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict55.jpg) Yemeni girls hold a giant Yemeni flag, left, as Syrians hold their revolution flag, right, during a protest against Yemeni and Syrian regimes at Tahrir Square, the focal point of Egyptian uprising, in Cairo, Egypt, Sunday, Nov. 6, 2011 to support protesters in Yemen and Syria during the first day of Islamic Eid al-Adha, or Feast of the Sacrifice. (Amr Nabil)
Yemeni girls hold a giant Yemeni flag, left, as Syrians hold their revolution flag, right, during a protest against Yemeni and Syrian regimes at Tahrir Square, the focal point of Egyptian uprising, in Cairo, Egypt, Sunday, Nov. 6, 2011 to support protesters in Yemen and Syria during the first day of Islamic Eid al-Adha, or Feast of the Sacrifice. (Amr Nabil)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict53.jpg) Amy Barnes protests as police move in to clear a downtown street during an Occupy Atlanta demonstration late Saturday, Nov. 5, 2011 in Atlanta. (David Goldman)
Amy Barnes protests as police move in to clear a downtown street during an Occupy Atlanta demonstration late Saturday, Nov. 5, 2011 in Atlanta. (David Goldman)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict58.jpg) In this Nov. 27, 2010 file photo, Susanna Camusso, leader of Italy’s largest labor confederation CGIL, arrives to deliver her speech during a demonstration to protest government policies regarding the economical crisis, in Rome. In an interview with The Associated Press Monday Nov. 7, 2011, Camusso is predicting 2012 will be a “terrifying” year for the economy even if beleaguered Premier Silvio Berlusconi leaves power soon.
In this Nov. 27, 2010 file photo, Susanna Camusso, leader of Italy’s largest labor confederation CGIL, arrives to deliver her speech during a demonstration to protest government policies regarding the economical crisis, in Rome. In an interview with The Associated Press Monday Nov. 7, 2011, Camusso is predicting 2012 will be a “terrifying” year for the economy even if beleaguered Premier Silvio Berlusconi leaves power soon.
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict23.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict16.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-21/pict10.jpg)



![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict16.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict21.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict23.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict30.jpg) These gents appear leery of being photographed, and rightly so, due to persistent infiltration and photography by cops. Or could be undercover cops.
These gents appear leery of being photographed, and rightly so, due to persistent infiltration and photography by cops. Or could be undercover cops.![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict33.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict34.jpg)




![[Image]](https://i0.wp.com/cryptome.org/ows-shutdown-2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/ows-shutdown-4.jpg)








 In His Own Words “Mr. So and So, I understand that you’re going to whip any FBI agent that walks into your store. I’m not armed, but I wanted to let you know if you would like to whip me, let’s get started…”
In His Own Words “Mr. So and So, I understand that you’re going to whip any FBI agent that walks into your store. I’m not armed, but I wanted to let you know if you would like to whip me, let’s get started…”






 Intimidation…vandalism…assault…rape…murder. These are crimes by anyone’s definition. But add an element of bias against the victims—because of their race or religion, for example—and these traditional crimes become hate crimes.
Intimidation…vandalism…assault…rape…murder. These are crimes by anyone’s definition. But add an element of bias against the victims—because of their race or religion, for example—and these traditional crimes become hate crimes.
![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict38.jpg) Occupy Wall Street Encampment at Zuccotti Park seen is empty of demonstrators, Tuesday, Nov. 15, 2011 in New York. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Mary Altaffer)
Occupy Wall Street Encampment at Zuccotti Park seen is empty of demonstrators, Tuesday, Nov. 15, 2011 in New York. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict39.jpg) Occupy Wall Street protesters hold a general assembly meeting inside an enclosed site near Canal Street on Tuesday, Nov. 15, 2011. Hundreds of police officers in riot gear before dawn Tuesday raided the New York City park where the Occupy Wall Street protests began, evicting and arresting hundreds of protesters from what has become the epicenter of the worldwide movement protesting corporate greed and economic inequality. (Seth Wenig) [Photo taken and transmitted before Seth Wenig was arrested along with the protestors.]
Occupy Wall Street protesters hold a general assembly meeting inside an enclosed site near Canal Street on Tuesday, Nov. 15, 2011. Hundreds of police officers in riot gear before dawn Tuesday raided the New York City park where the Occupy Wall Street protests began, evicting and arresting hundreds of protesters from what has become the epicenter of the worldwide movement protesting corporate greed and economic inequality. (Seth Wenig) [Photo taken and transmitted before Seth Wenig was arrested along with the protestors.]![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict40.jpg) Police prepare to enter an enclosed site near Canal Street where Occupy Wall Street protesters gathered on Tuesday, Nov. 15, 2011. Hundreds of police officers in riot gear before dawn Tuesday raided the New York City park where the Occupy Wall Street protests began, evicting and arresting hundreds of protesters from what has become the epicenter of the worldwide movement protesting corporate greed and economic inequality. (Seth Wenig)
Police prepare to enter an enclosed site near Canal Street where Occupy Wall Street protesters gathered on Tuesday, Nov. 15, 2011. Hundreds of police officers in riot gear before dawn Tuesday raided the New York City park where the Occupy Wall Street protests began, evicting and arresting hundreds of protesters from what has become the epicenter of the worldwide movement protesting corporate greed and economic inequality. (Seth Wenig)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict34.jpg) Occupy Wall Street activists gain entrance in to Duarte Square to protest after police removed the protesters early in the morning from Zuccotti Park on November 15, 2011 in New York City. Getty
Occupy Wall Street activists gain entrance in to Duarte Square to protest after police removed the protesters early in the morning from Zuccotti Park on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict33.jpg) NYPD officers standoff with Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty
NYPD officers standoff with Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict27.jpg) NYPD officers clear out Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty [AP journalist Karen Matthews is at upper right in light blue jacket (and in earlier photos below). She was arrested with AP photographer Seth Wenig (at center in following photo).]
NYPD officers clear out Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty [AP journalist Karen Matthews is at upper right in light blue jacket (and in earlier photos below). She was arrested with AP photographer Seth Wenig (at center in following photo).]![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict37.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict31.jpg) NYPD officers arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty
NYPD officers arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict32.jpg) NYPD officers arrest Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty
NYPD officers arrest Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict28.jpg) NYPD officers attempt to arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty
NYPD officers attempt to arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict30.jpg) NYPD officers arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty
NYPD officers arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict26.jpg) NYPD officers arrest Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Police removed the protesters early in the morning from their encampment in Zuccotti Park. Hundreds of protesters, who rallied against inequality in America, have slept in tents and under tarps since September 17 in Zuccotti Park, which has since become the epicenter of the global Occupy movement. The raid in New York City follows recent similar moves in Oakland, California, and Portland, Oregon. Getty
NYPD officers arrest Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Police removed the protesters early in the morning from their encampment in Zuccotti Park. Hundreds of protesters, who rallied against inequality in America, have slept in tents and under tarps since September 17 in Zuccotti Park, which has since become the epicenter of the global Occupy movement. The raid in New York City follows recent similar moves in Oakland, California, and Portland, Oregon. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict20.jpg) Occupy Wall Street protesters return to Zuccotti Park on Tuesday, Nov. 15, 2011 in New York. After an early police raid removing protesters, hundreds returned to Zuccotti Park carrying photocopies of a court order they say gives them the right to return to the park. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules.
Occupy Wall Street protesters return to Zuccotti Park on Tuesday, Nov. 15, 2011 in New York. After an early police raid removing protesters, hundreds returned to Zuccotti Park carrying photocopies of a court order they say gives them the right to return to the park. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict21.jpg) Police arrest an Occupy Wall Street protester at Zuccotti Park on Tuesday, Nov. 15, 2011 in New York. After an early police raid removing protesters, hundreds returned to Zuccotti Park carrying photocopies of a court order they say gives them the right to return there.
Police arrest an Occupy Wall Street protester at Zuccotti Park on Tuesday, Nov. 15, 2011 in New York. After an early police raid removing protesters, hundreds returned to Zuccotti Park carrying photocopies of a court order they say gives them the right to return there.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict22.jpg) Occupy Wall Street protesters rally in a small park on Canal Street in New York, Tuesday, Nov. 15, 2011. Police officers evicted the protesters from their base in Zuccotti Park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)
Occupy Wall Street protesters rally in a small park on Canal Street in New York, Tuesday, Nov. 15, 2011. Police officers evicted the protesters from their base in Zuccotti Park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict23.jpg) A police officer watches from the grounds of City Hall as Occupy Wall Street protesters linked hands to block media from attending a news conference held by Mayor Michael Bloomberg in New York, Tuesday, Nov. 15, 2011. The protesters eventually dispersed peacefully.
A police officer watches from the grounds of City Hall as Occupy Wall Street protesters linked hands to block media from attending a news conference held by Mayor Michael Bloomberg in New York, Tuesday, Nov. 15, 2011. The protesters eventually dispersed peacefully.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict24.jpg) An empty and closed Zuccotti Park is seen in New York, Tuesday, Nov. 15, 2011. Police officers evicted Occupy Wall Street protesters from the park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)
An empty and closed Zuccotti Park is seen in New York, Tuesday, Nov. 15, 2011. Police officers evicted Occupy Wall Street protesters from the park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict25.jpg) A pedestrian takes a picture of an empty and closed Zuccotti Park in New York, Tuesday, Nov. 15, 2011. Police officers evicted Occupy Wall Street protesters from the park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)
A pedestrian takes a picture of an empty and closed Zuccotti Park in New York, Tuesday, Nov. 15, 2011. Police officers evicted Occupy Wall Street protesters from the park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict0.jpg) An Occupy Wall Street protestor draws contact from a police officer near Zuccotti Park after being ordered to leave the longtime encampment in New York, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park.
An Occupy Wall Street protestor draws contact from a police officer near Zuccotti Park after being ordered to leave the longtime encampment in New York, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict12.jpg) Occupy Wall Street protesters clash with police at Zuccotti Park after being ordered to leave their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Craig Ruttle)
Occupy Wall Street protesters clash with police at Zuccotti Park after being ordered to leave their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Craig Ruttle)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict1.jpg) An Occupy Wall Street protestor is arrested on the ground by police near Zuccotti Park after being ordered to leave their longtime encampment in New York, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park.
An Occupy Wall Street protestor is arrested on the ground by police near Zuccotti Park after being ordered to leave their longtime encampment in New York, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict14.jpg) A demonstrator yells at police officers as they order Occupy Wall Street protesters to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)
A demonstrator yells at police officers as they order Occupy Wall Street protesters to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict13.jpg) An Occupy Wall Street protester yells out at police after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)
An Occupy Wall Street protester yells out at police after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict3.jpg) Occupy Wall Street protesters clash with police near Zuccotti Park after being ordered to leave their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)
Occupy Wall Street protesters clash with police near Zuccotti Park after being ordered to leave their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict4.jpg) Occupy Wall Street protesters are pushed by police near the encampment at Zuccotti Park in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous.
Occupy Wall Street protesters are pushed by police near the encampment at Zuccotti Park in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict2.jpg) Demonstrators clash with police after being ordered to leave the Occupy Wall Street encampment at Zuccotti Park in New York on Tuesday, Nov. 15, 2011. Police handed out notices earlier from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Craig Ruttle)
Demonstrators clash with police after being ordered to leave the Occupy Wall Street encampment at Zuccotti Park in New York on Tuesday, Nov. 15, 2011. Police handed out notices earlier from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Craig Ruttle)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict6.jpg) An Occupy Wall Street protester is arrested by police near the encampment at Zuccotti Park in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents.
An Occupy Wall Street protester is arrested by police near the encampment at Zuccotti Park in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict7.jpg) An Occupy Wall Street protestor is arrested during a march on Broadway, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)
An Occupy Wall Street protestor is arrested during a march on Broadway, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict9.jpg) An Occupy Wall Street protester is detained by police officers after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)
An Occupy Wall Street protester is detained by police officers after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict10.jpg) Occupy Wall Street protesters are detained by police officers after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)
Occupy Wall Street protesters are detained by police officers after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict11.jpg) Occupy Wall Street demonstrators are arrested after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)
Occupy Wall Street demonstrators are arrested after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict17.jpg) Occupy Wall Street protesters march through the streets after they were evicted from Zuccotti Park on November 15, 2011 in New York. Hundreds of police in riot gear dismantled the Occupy Oakland camp Monday, evicting and arresting protesters in the second such US move in as many days as authorities get tough against the two-month-old protest movement. Getty
Occupy Wall Street protesters march through the streets after they were evicted from Zuccotti Park on November 15, 2011 in New York. Hundreds of police in riot gear dismantled the Occupy Oakland camp Monday, evicting and arresting protesters in the second such US move in as many days as authorities get tough against the two-month-old protest movement. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict8.jpg) A police officer carries trash through Zuccotti Park, the longtime encampment for Occupy Wall Street protesters in New York, as the cleanup effort begins early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)
A police officer carries trash through Zuccotti Park, the longtime encampment for Occupy Wall Street protesters in New York, as the cleanup effort begins early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict5.jpg) Two protesters and their dog, who said they have stayed slept with other protesters for the last 56 nights, sit along a police barricade at the edge of Zuccotti Park in New York, Tuesday, Nov. 15, 2011 after the Occupy Wall Street encampment was cleared from the park in the early morning hours after a nearly two month occupation,wa;;w and before the park reopened. (Craig Ruttle)
Two protesters and their dog, who said they have stayed slept with other protesters for the last 56 nights, sit along a police barricade at the edge of Zuccotti Park in New York, Tuesday, Nov. 15, 2011 after the Occupy Wall Street encampment was cleared from the park in the early morning hours after a nearly two month occupation,wa;;w and before the park reopened. (Craig Ruttle)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict16.jpg) New York City sanitation crews clean Zuccotti Park after city officials evicted the ‘Occupy Wall Street’ protest from the park in the early morning hours of November 15, 2011 in New York. Occupy Wall Street protestors most feared the coming winter, but it was on the mildest of nights, when activists slept soundly in their tents, that New York police sprang a surprise operation to end the eight-week demonstration. Getty
New York City sanitation crews clean Zuccotti Park after city officials evicted the ‘Occupy Wall Street’ protest from the park in the early morning hours of November 15, 2011 in New York. Occupy Wall Street protestors most feared the coming winter, but it was on the mildest of nights, when activists slept soundly in their tents, that New York police sprang a surprise operation to end the eight-week demonstration. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict15.jpg) People walk past New York Police Department officers guarding a closed Zuccotti Park after city officials evicted the ‘Occupy Wall Street’ protest from the park in the early morning hours of November 15, 2011 in New York. Getty
People walk past New York Police Department officers guarding a closed Zuccotti Park after city officials evicted the ‘Occupy Wall Street’ protest from the park in the early morning hours of November 15, 2011 in New York. Getty
 Nachfolgend bringen wir eine Original-Pressemeldung von „
Nachfolgend bringen wir eine Original-Pressemeldung von „












![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict26.jpg) An official from the Tokyo Electric Power Co. (TEPCO), wearing a protective suit and mask, uses a plastic covered megaphone to speak to fellow TEPCO workers and journalists as they drive towards the crippled Fukushima Dai-ichi nuclear power station in Okuma, Japan, Saturday, Nov. 12, 2011. Conditions at Japan’s wrecked Fukushima nuclear power plant, devastated by a tsunami in March, were slowly improving to the point where a “cold shutdown” would be possible as planned, officials said on Saturday during a tour of the facility. The nuclear reactor buildings were still surrounded by crumpled trucks, twisted metal fences, and large, dented water tanks. Smaller office buildings around the reactors were left as they were abandoned on March 11, when the tsunami hit.
An official from the Tokyo Electric Power Co. (TEPCO), wearing a protective suit and mask, uses a plastic covered megaphone to speak to fellow TEPCO workers and journalists as they drive towards the crippled Fukushima Dai-ichi nuclear power station in Okuma, Japan, Saturday, Nov. 12, 2011. Conditions at Japan’s wrecked Fukushima nuclear power plant, devastated by a tsunami in March, were slowly improving to the point where a “cold shutdown” would be possible as planned, officials said on Saturday during a tour of the facility. The nuclear reactor buildings were still surrounded by crumpled trucks, twisted metal fences, and large, dented water tanks. Smaller office buildings around the reactors were left as they were abandoned on March 11, when the tsunami hit.![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict25.jpg) Japanese police man a checkpoint near the edge of the contaminated exclusion zone around the crippled Fukushima Dai-ichi nuclear power station near Okuma, Fukushima prefecture, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
Japanese police man a checkpoint near the edge of the contaminated exclusion zone around the crippled Fukushima Dai-ichi nuclear power station near Okuma, Fukushima prefecture, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict13.jpg) A deserted street inside the contaminated exclusion zone around the crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011.
A deserted street inside the contaminated exclusion zone around the crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011.![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict22.jpg) A deserted field and buildings inside the contaminated exclusion zone around the crippled Fukushima Dai-ichi nuclear power station are seen through a bus window near Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
A deserted field and buildings inside the contaminated exclusion zone around the crippled Fukushima Dai-ichi nuclear power station are seen through a bus window near Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict23.jpg) An official from the Tokyo Electric Power Co., right, and an unidentified man, both wearing protective suits and masks ride on a bus as they pass by the crippled Fukushima Dai-ichi nuclear power station, seen through the window, in Okuma, Japan, Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
An official from the Tokyo Electric Power Co., right, and an unidentified man, both wearing protective suits and masks ride on a bus as they pass by the crippled Fukushima Dai-ichi nuclear power station, seen through the window, in Okuma, Japan, Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict20.jpg) Officials from the Tokyo Electric Power Co. and Japanese journalists look at the crippled Fukushima Dai-ichi nuclear power station from bus windows in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)
Officials from the Tokyo Electric Power Co. and Japanese journalists look at the crippled Fukushima Dai-ichi nuclear power station from bus windows in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict19.jpg) A view of Tokyo Electric Power Co’s tsunami-crippled Fukushima Daiichi nuclear power plant in Fukushima prefecture November 12, 2011. (David Guttenfelder, Pool)
A view of Tokyo Electric Power Co’s tsunami-crippled Fukushima Daiichi nuclear power plant in Fukushima prefecture November 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict2.jpg) The crippled Fukushima Daiichi nuclear power plant’s No.4, No.3, No.2 and No.1 (R-L) reactor buildings are seen from bus windows in Fukushima prefecture November 12, 2011. Reuters
The crippled Fukushima Daiichi nuclear power plant’s No.4, No.3, No.2 and No.1 (R-L) reactor buildings are seen from bus windows in Fukushima prefecture November 12, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict3.jpg) The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters
The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict21.jpg) The Unit 4 reactor building of the crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)
The Unit 4 reactor building of the crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict32.jpg) The Unit 4 reactor building of the crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
The Unit 4 reactor building of the crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict27.jpg) Broken vehicles are abandoned outside Unit 4 turbine building at the crippled Fukushima Dai-ichi nuclear power station as they are observed from inside a bus in Okuma, Fukushima Prefecture, Japan, Saturday, Nov. 12, 2011.
Broken vehicles are abandoned outside Unit 4 turbine building at the crippled Fukushima Dai-ichi nuclear power station as they are observed from inside a bus in Okuma, Fukushima Prefecture, Japan, Saturday, Nov. 12, 2011.![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict0.jpg) The crippled Fukushima Daiichi nuclear power plant’s upper part of the No.3 reactor building is seen from a bus window in Fukushima prefecture, November 12, 2011. Reuters
The crippled Fukushima Daiichi nuclear power plant’s upper part of the No.3 reactor building is seen from a bus window in Fukushima prefecture, November 12, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict29.jpg) The crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)
The crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict4.jpg) The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters
The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict16.jpg) The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters
The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict24.jpg) Crushed piping is observed from inside a bus at the crippled Fukushima Dai-ichi nuclear power station in Okuma, Fukushima Prefecture, Japan, Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned trucks, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (Ikuro Aiba, Pool)
Crushed piping is observed from inside a bus at the crippled Fukushima Dai-ichi nuclear power station in Okuma, Fukushima Prefecture, Japan, Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned trucks, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (Ikuro Aiba, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict31.jpg) Units five and six of the Fukushima Dai-ichi nuclear power station are seen through a bus window in Futaba, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
Units five and six of the Fukushima Dai-ichi nuclear power station are seen through a bus window in Futaba, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict28.jpg) Members of the media, wearing protective suits, interview Japan’s Minister of the Environment, Goshi Hosono, and Chief of the Fukushima Dai-ichi nuclear power plant, Masao Yoshida, inside the emergency operation center at the crippled nuclear power station in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
Members of the media, wearing protective suits, interview Japan’s Minister of the Environment, Goshi Hosono, and Chief of the Fukushima Dai-ichi nuclear power plant, Masao Yoshida, inside the emergency operation center at the crippled nuclear power station in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict33.jpg) Tokyo Electric Power Co. employees work inside the emergency operation center at the crippled Fukushima Dai-ichi nuclear power station in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
Tokyo Electric Power Co. employees work inside the emergency operation center at the crippled Fukushima Dai-ichi nuclear power station in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)








 “Today, with the flip of a switch, the FBI and our partners dismantled the Rove criminal enterprise. Thanks to the collective effort across the U.S. and in Estonia, six leaders of the criminal enterprise have been arrested and numerous servers operated by the criminal organization have been disabled. Additionally, thanks to a coordinated effort of trusted industry partners, a mitigation plan commenced today, beginning with the replacement of rogue DNS servers with clean DNS servers to keep millions online, while providing ISPs the opportunity to coordinate user remediation efforts.”
“Today, with the flip of a switch, the FBI and our partners dismantled the Rove criminal enterprise. Thanks to the collective effort across the U.S. and in Estonia, six leaders of the criminal enterprise have been arrested and numerous servers operated by the criminal organization have been disabled. Additionally, thanks to a coordinated effort of trusted industry partners, a mitigation plan commenced today, beginning with the replacement of rogue DNS servers with clean DNS servers to keep millions online, while providing ISPs the opportunity to coordinate user remediation efforts.”
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict21.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict16.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict17.jpg)






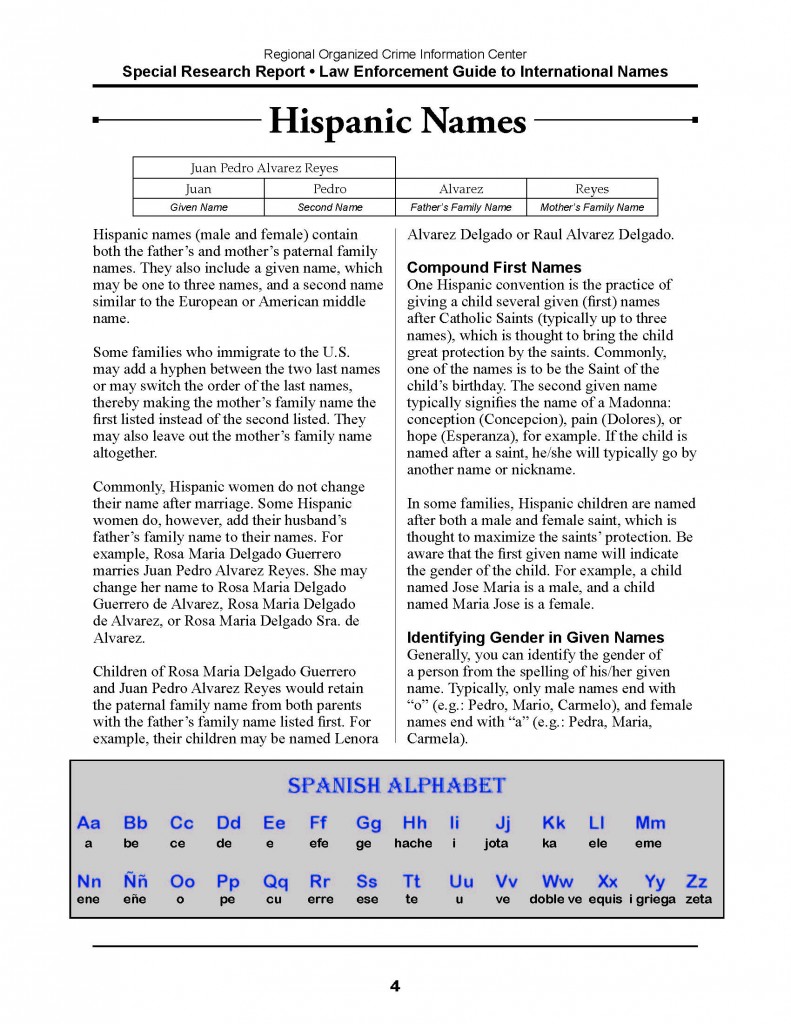
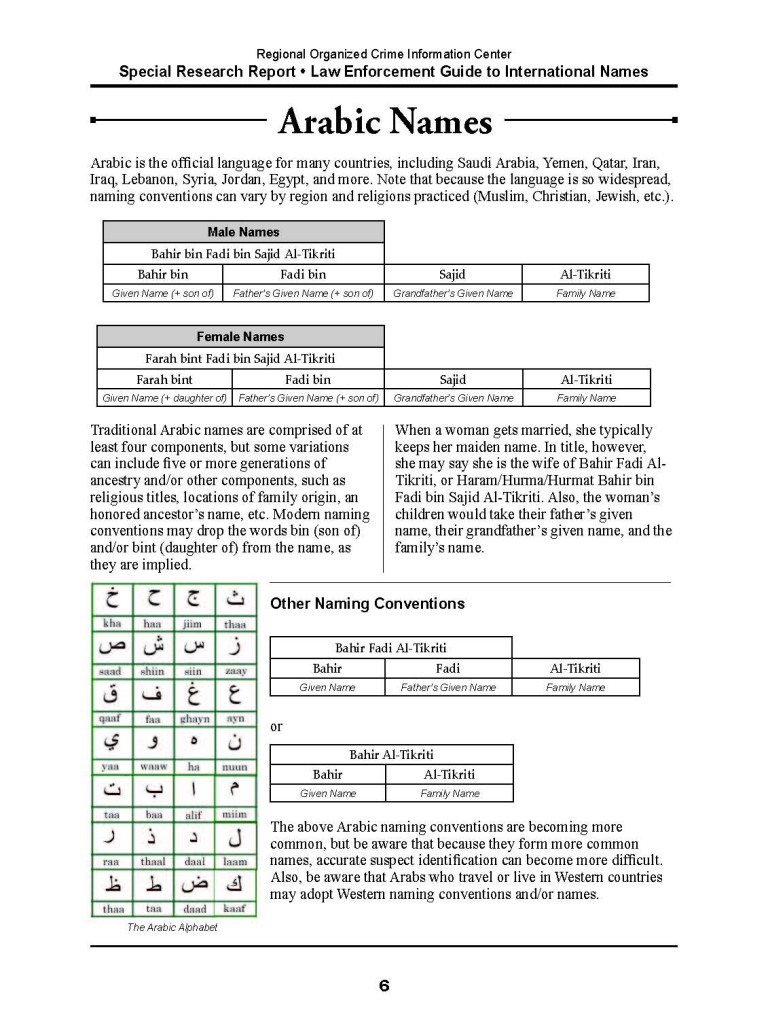

![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict0.jpg) In this Saturday, June 25, 2011 file photo, Yemeni women, wearing headbands that read in Arabic, “housewives”, attend a demonstration demanding the resignation of President Ali Abdullah Saleh, in Sanaa, Yemen. As demonstrations first swelled in Yemen, the regime distributed a photo of female activist Tawakkul Kamran in a protest test with a male colleague _ cutting out others around them _ to taint her for sinfully sitting alone with a man. Kamran’s Nobel peace prize win win draws attention to the role of women in the Arab Spring uprisings.
In this Saturday, June 25, 2011 file photo, Yemeni women, wearing headbands that read in Arabic, “housewives”, attend a demonstration demanding the resignation of President Ali Abdullah Saleh, in Sanaa, Yemen. As demonstrations first swelled in Yemen, the regime distributed a photo of female activist Tawakkul Kamran in a protest test with a male colleague _ cutting out others around them _ to taint her for sinfully sitting alone with a man. Kamran’s Nobel peace prize win win draws attention to the role of women in the Arab Spring uprisings.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict35.jpg) On October 5, 2011, a jury in State Supreme Court in Queens foundthe woman, Barbara Sheehan, not guilty of second-degree murder charges in a case that had been viewed as a strenuous test of a battered-woman defense. Her son and daughter, the children of her slain husband, wept with joy. During the trial, the jury heard how Ms. Sheehan had been relentlessly abused by her husband, Raymond Sheehan, a former police sergeant, during their 24 years of marriage. (Uli Seit)
On October 5, 2011, a jury in State Supreme Court in Queens foundthe woman, Barbara Sheehan, not guilty of second-degree murder charges in a case that had been viewed as a strenuous test of a battered-woman defense. Her son and daughter, the children of her slain husband, wept with joy. During the trial, the jury heard how Ms. Sheehan had been relentlessly abused by her husband, Raymond Sheehan, a former police sergeant, during their 24 years of marriage. (Uli Seit)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict22.jpg) Africa’s first democratically elected female president, a Liberian peace activist and a woman who stood up to Yemen’s authoritarian regime won the Nobel Peace Prize on Friday Oct. 7, 2011 for their work to secure women’s rights, which the prize committee described as fundamental to advancing world peace. Seen in this combo from left: Tawakkul Karman of Yemen, Liberian peace activist Leymah Gbowee and Liberia’s President Ellen Johnson Sirleaf. (AP Photo)
Africa’s first democratically elected female president, a Liberian peace activist and a woman who stood up to Yemen’s authoritarian regime won the Nobel Peace Prize on Friday Oct. 7, 2011 for their work to secure women’s rights, which the prize committee described as fundamental to advancing world peace. Seen in this combo from left: Tawakkul Karman of Yemen, Liberian peace activist Leymah Gbowee and Liberia’s President Ellen Johnson Sirleaf. (AP Photo)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict2.jpg) In this Tuesday, March 8, 2011 file photo, an Egyptian female protester, second right, argues with a man as hundreds of women marched to Cairo’s central Tahrir Square to celebrate International Women’s Day, Egypt. As demonstrations first swelled in Yemen, the regime distributed a photo of female activist Tawakkul Kamran in a protest test with a male colleague _ cutting out others around them _ to taint her for sinfully sitting alone with a man. Kamran’s Nobel peace win draws attention to the role of women in the Arab Spring uprisings.
In this Tuesday, March 8, 2011 file photo, an Egyptian female protester, second right, argues with a man as hundreds of women marched to Cairo’s central Tahrir Square to celebrate International Women’s Day, Egypt. As demonstrations first swelled in Yemen, the regime distributed a photo of female activist Tawakkul Kamran in a protest test with a male colleague _ cutting out others around them _ to taint her for sinfully sitting alone with a man. Kamran’s Nobel peace win draws attention to the role of women in the Arab Spring uprisings.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict1.jpg) In this Friday, April 1, 2011 file photo, Egyptian women chant slogans as they attend a demonstration in Tahrir Square in Cairo, Egypt. As demonstrations first swelled in Yemen, the regime distributed a photo of female activist Tawakkul Kamran in a protest test with a male colleague _ cutting out others around them _ to taint her for sinfully sitting alone with a man. Kamran’s Nobel peace win draws attention to the role of women in the Arab Spring uprisings.
In this Friday, April 1, 2011 file photo, Egyptian women chant slogans as they attend a demonstration in Tahrir Square in Cairo, Egypt. As demonstrations first swelled in Yemen, the regime distributed a photo of female activist Tawakkul Kamran in a protest test with a male colleague _ cutting out others around them _ to taint her for sinfully sitting alone with a man. Kamran’s Nobel peace win draws attention to the role of women in the Arab Spring uprisings.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict3.jpg) Ellen Rios, right, donates a vegan lasagna she made to a protestor at the “Occupy Wall Street” protests in Zuccotti Park, Friday, October 7, 2011, in New York. The three-week-old campout in a lower Manhattan plaza looks like a jumble of tattered sleeping bags, but teams of volunteers working on food, sanitation, health care and other needs keep the shifting population of protesters functioning like an impromptu city within the city. (Andrew Burton)
Ellen Rios, right, donates a vegan lasagna she made to a protestor at the “Occupy Wall Street” protests in Zuccotti Park, Friday, October 7, 2011, in New York. The three-week-old campout in a lower Manhattan plaza looks like a jumble of tattered sleeping bags, but teams of volunteers working on food, sanitation, health care and other needs keep the shifting population of protesters functioning like an impromptu city within the city. (Andrew Burton)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict4.jpg) A woman helps unpack boxes of donations in the “Shipping and Receiving” section of Zuccotti Park, where “Occupy Wall Street” protests are taking place, in New York, Friday, October 7, 2011. The three-week-old campout in a lower Manhattan plaza looks like a jumble of tattered sleeping bags, but teams of volunteers working on food, sanitation, health care and other needs keep the shifting population of protesters functioning like an impromptu city within the city. (Andrew Burton)
A woman helps unpack boxes of donations in the “Shipping and Receiving” section of Zuccotti Park, where “Occupy Wall Street” protests are taking place, in New York, Friday, October 7, 2011. The three-week-old campout in a lower Manhattan plaza looks like a jumble of tattered sleeping bags, but teams of volunteers working on food, sanitation, health care and other needs keep the shifting population of protesters functioning like an impromptu city within the city. (Andrew Burton)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict19.jpg) In this Thursday, Feb. 10, 2011 file photo, Yemeni activist Tawakkul Karman, left, chants slogans along with other demonstrators holding banners during an anti-government protest in Sanaa, Yemen. Banner on right reads in Arabic, “33 years of authoritarian rule.” The 2011 Nobel Peace Prize was awarded Friday, Oct. 7, 2011 to Liberian President Ellen Johnson Sirleaf, Liberian peace activist Leymah Gbowee and Tawakkul Karman of Yemen for their work on women’s rights. (Hani Mohammed)
In this Thursday, Feb. 10, 2011 file photo, Yemeni activist Tawakkul Karman, left, chants slogans along with other demonstrators holding banners during an anti-government protest in Sanaa, Yemen. Banner on right reads in Arabic, “33 years of authoritarian rule.” The 2011 Nobel Peace Prize was awarded Friday, Oct. 7, 2011 to Liberian President Ellen Johnson Sirleaf, Liberian peace activist Leymah Gbowee and Tawakkul Karman of Yemen for their work on women’s rights. (Hani Mohammed)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict21.jpg) Protesters hold carnations in their mouths in Bucharest, Romania, Thursday, Oct. 6, 2011, during the Romanian version of the Slut Walk march. The Slut Walk, a protest against harassment of women initiated by the outfits they wear or their behavior in public, was the first of it’s kind in Romania, a country where it is still quite widely believed that sexual aggression victims bear at least some responsibility for being targeted.(Vadim Ghirda)
Protesters hold carnations in their mouths in Bucharest, Romania, Thursday, Oct. 6, 2011, during the Romanian version of the Slut Walk march. The Slut Walk, a protest against harassment of women initiated by the outfits they wear or their behavior in public, was the first of it’s kind in Romania, a country where it is still quite widely believed that sexual aggression victims bear at least some responsibility for being targeted.(Vadim Ghirda)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict20.jpg) Protesters including Jean Blackwood, left, of Columbia, Mo, and Crystal Elinski, center, of Portland, Ore., hold bundles representing killed children next to a “corporate America” flag, during a march past the White House in Washington, Friday, Oct. 7, 2011, part of Occupy DC activities in Washington. (Jacquelyn Martin)
Protesters including Jean Blackwood, left, of Columbia, Mo, and Crystal Elinski, center, of Portland, Ore., hold bundles representing killed children next to a “corporate America” flag, during a march past the White House in Washington, Friday, Oct. 7, 2011, part of Occupy DC activities in Washington. (Jacquelyn Martin)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict30.jpg) Occupy Boston protesters march through the Financial district in Boston, Wednesday, Oct. 5, 2011. The group is part of a nationwide grassroots movement in support of the ongoing Wall Street protests in New York. (Elise Amendola)
Occupy Boston protesters march through the Financial district in Boston, Wednesday, Oct. 5, 2011. The group is part of a nationwide grassroots movement in support of the ongoing Wall Street protests in New York. (Elise Amendola)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict33.jpg) One of several demonstrators is taken into custody by police after refusing to leave a Bank of America branch in downtown Los Angeles, Thursday, Oct. 6, 2011. The arrests Thursday afternoon came at the end of a demonstration that moved among high-rises housing the offices of banks and other financial institutions. (Chris Carlson)
One of several demonstrators is taken into custody by police after refusing to leave a Bank of America branch in downtown Los Angeles, Thursday, Oct. 6, 2011. The arrests Thursday afternoon came at the end of a demonstration that moved among high-rises housing the offices of banks and other financial institutions. (Chris Carlson)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict34.jpg) Theresa Shoatz protests in a cross walk near City Hall Thursday, Oct. 6, 2011, in Philadelphia. Organizers of the Occupy Philadelphia demonstration say Thursday’s protest is a stand against corporate greed. (Matt Rourke)
Theresa Shoatz protests in a cross walk near City Hall Thursday, Oct. 6, 2011, in Philadelphia. Organizers of the Occupy Philadelphia demonstration say Thursday’s protest is a stand against corporate greed. (Matt Rourke)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict36.jpg) A woman holds up a placard with the image of German Chancellor Angela Merkel during a protest outside the German embassy in the Greek capital Athens, on Thursday Oct. 6, 2011. The placard reads, “Europe will become German.” The small group of protesters said Germany must pay Greece reparations for its occupation of the country during WWII before Greece pays off its debts. (Kostas Tsironis)
A woman holds up a placard with the image of German Chancellor Angela Merkel during a protest outside the German embassy in the Greek capital Athens, on Thursday Oct. 6, 2011. The placard reads, “Europe will become German.” The small group of protesters said Germany must pay Greece reparations for its occupation of the country during WWII before Greece pays off its debts. (Kostas Tsironis)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict24.jpg) Occupy Wall Street protesters march towards Zuccotti Park in New York’s Financial District, Wednesday, Oct. 5, 2011. Protests against Wall Street entered their 18th day Tuesday as demonstrators across the country show their anger over the wobbly economy and what they see as corporate greed by marching on Federal Reserve banks and camping out in parks from Los Angeles to Portland, Maine. (Jason DeCrow)
Occupy Wall Street protesters march towards Zuccotti Park in New York’s Financial District, Wednesday, Oct. 5, 2011. Protests against Wall Street entered their 18th day Tuesday as demonstrators across the country show their anger over the wobbly economy and what they see as corporate greed by marching on Federal Reserve banks and camping out in parks from Los Angeles to Portland, Maine. (Jason DeCrow)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict23.jpg) Pakistani opposition lawmakers rally outside the parliament to condemn severe power shortages, corruption and lawlessness, Islamabad, Pakistan, Thursday, Oct, 6. 2011. Dozens of opposition parliamentarians boycotted a session of parliament and held a sit-in protest at the gate of Presidential palace condemning severe power shortages, corruption and lawlessness in Pakistan. Placard on left reads “corrupt government, let poor live.”(B.K. Bangash)
Pakistani opposition lawmakers rally outside the parliament to condemn severe power shortages, corruption and lawlessness, Islamabad, Pakistan, Thursday, Oct, 6. 2011. Dozens of opposition parliamentarians boycotted a session of parliament and held a sit-in protest at the gate of Presidential palace condemning severe power shortages, corruption and lawlessness in Pakistan. Placard on left reads “corrupt government, let poor live.”(B.K. Bangash)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict28.jpg) An Occupy Wall Street protester is penned in by barricades and police after trying to march to Wall Street in New York, Wednesday, Oct. 5, 2011. Protesters in suits and T-shirts with union slogans left work early to march with activists who have been camped out in Zuccotti Park for days. Some marchers brought along their children, hoisting them onto their shoulders as they walked down Broadway. (Seth Wenig)
An Occupy Wall Street protester is penned in by barricades and police after trying to march to Wall Street in New York, Wednesday, Oct. 5, 2011. Protesters in suits and T-shirts with union slogans left work early to march with activists who have been camped out in Zuccotti Park for days. Some marchers brought along their children, hoisting them onto their shoulders as they walked down Broadway. (Seth Wenig)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict31.jpg) Riot police detain a protester during minor clashes in Athens, Wednesday, Oct. 5, 2011. Greek civil servants walked off the job on a 24-hour strike Wednesday, paralyzing the public sector in a protest over ever-deeper austerity measures applied as the government struggles to avoid a catastrophic default. At least 16,000 protesters converged in the Greek capital, and a crowd of about 10,000 gathered in the northern city of Thessaloniki. (Thanassis Stavrakis)
Riot police detain a protester during minor clashes in Athens, Wednesday, Oct. 5, 2011. Greek civil servants walked off the job on a 24-hour strike Wednesday, paralyzing the public sector in a protest over ever-deeper austerity measures applied as the government struggles to avoid a catastrophic default. At least 16,000 protesters converged in the Greek capital, and a crowd of about 10,000 gathered in the northern city of Thessaloniki. (Thanassis Stavrakis)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict29.jpg) Occupy Wall Street protesters march to join a union rally at Foley Square in New York, Wednesday, Oct. 5, 2011. The protests have gathered momentum and gained participants in recent days as news of mass arrests and a coordinated media campaign by the protestors have given rise to similar demonstrations around the country. (Seth Wenig)
Occupy Wall Street protesters march to join a union rally at Foley Square in New York, Wednesday, Oct. 5, 2011. The protests have gathered momentum and gained participants in recent days as news of mass arrests and a coordinated media campaign by the protestors have given rise to similar demonstrations around the country. (Seth Wenig)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict32.jpg) Jordan McCarthy, 22, from Sandwich, N.H., awakes from under a makeshift shelter where she is camped out among participants in the Occupy Wall Street Protest at Zuccotti Park in lower Manhattan on Wednesday, Oct. 5, 2011 in New York. “We have allowed greed to be more important than humans,” said McCarthy who joined the camp a week ago.
Jordan McCarthy, 22, from Sandwich, N.H., awakes from under a makeshift shelter where she is camped out among participants in the Occupy Wall Street Protest at Zuccotti Park in lower Manhattan on Wednesday, Oct. 5, 2011 in New York. “We have allowed greed to be more important than humans,” said McCarthy who joined the camp a week ago.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict25.jpg) Foley Square, New York, NY, October 5, 2011. (Cryptome)
Foley Square, New York, NY, October 5, 2011. (Cryptome)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict5.jpg) Demonstrator Andrea Vitale cries during a protest to stop the eviction of Matias Gonzalez, a 52-year-old Spanish citizen who can’t pay his mortage, Barcelona Spain, Monday, Oct. 3, 2011. As in many European countries, Spanish mortgages are not like US-style ones in which defaulters can return the keys to the bank and walk away from their debt, albeit with their credit rating in ruins. Here, mortgage holders not only have to give the house back, but also pay off bank debt.
Demonstrator Andrea Vitale cries during a protest to stop the eviction of Matias Gonzalez, a 52-year-old Spanish citizen who can’t pay his mortage, Barcelona Spain, Monday, Oct. 3, 2011. As in many European countries, Spanish mortgages are not like US-style ones in which defaulters can return the keys to the bank and walk away from their debt, albeit with their credit rating in ruins. Here, mortgage holders not only have to give the house back, but also pay off bank debt.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict6.jpg) Occupy Wall Street protestor Alexi Morris is arrested along with at several others in the financial district’s Zucotti park, Monday, Oct. 3, 2011, in New York. The arrests of 700 people on Brooklyn Bridge over the weekend fueled the anger of the protesters camping in a Manhattan park and sparked support elsewhere in the country as the campaign entered its third week. (John Minchillo)
Occupy Wall Street protestor Alexi Morris is arrested along with at several others in the financial district’s Zucotti park, Monday, Oct. 3, 2011, in New York. The arrests of 700 people on Brooklyn Bridge over the weekend fueled the anger of the protesters camping in a Manhattan park and sparked support elsewhere in the country as the campaign entered its third week. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict7.jpg) Occupy Wall Street protestors play drums and sing songs in the financial district’s Zuccotti park Sunday, Oct. 2, 2011, in New York. The protests have gathered momentum and gained participants in recent days as news of mass arrests and a coordinated media campaign by the protestors have given rise to similar demonstrations around the country. (John Minchillo)
Occupy Wall Street protestors play drums and sing songs in the financial district’s Zuccotti park Sunday, Oct. 2, 2011, in New York. The protests have gathered momentum and gained participants in recent days as news of mass arrests and a coordinated media campaign by the protestors have given rise to similar demonstrations around the country. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict8.jpg) In this citizen journalism image made on a mobile phone and provided by Shaam News Network, anti-Syrian President Bashar Assad protesters flash V-victory signs as a woman in the foreground displays her hands with the Arabic word reading: “leave”, during a demonstration against the Syrian regime, in Edlib province, Syria, on Friday, Sept. 30, 2011. Syrian security forces opened fire on protesters Friday as thousands rallied across the country to call for the downfall of President Bashar Assad.
In this citizen journalism image made on a mobile phone and provided by Shaam News Network, anti-Syrian President Bashar Assad protesters flash V-victory signs as a woman in the foreground displays her hands with the Arabic word reading: “leave”, during a demonstration against the Syrian regime, in Edlib province, Syria, on Friday, Sept. 30, 2011. Syrian security forces opened fire on protesters Friday as thousands rallied across the country to call for the downfall of President Bashar Assad.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict9.jpg) Tibetan exiles hold placards at a protest in New Delhi, India, Friday, Sept. 30, 2011. The protest was to express solidarity with two monks who self-immolated on Sept. 26 in Eastern Tibet and against alleged Chinese oppression. (Tsering Topgyal)
Tibetan exiles hold placards at a protest in New Delhi, India, Friday, Sept. 30, 2011. The protest was to express solidarity with two monks who self-immolated on Sept. 26 in Eastern Tibet and against alleged Chinese oppression. (Tsering Topgyal)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict10.jpg) High school students chant slogans during a protest in front of the Greek Parliament in Athens, Thursday, Sept 29 2011. Weeks-long education protests have recently spread to state schools,with a growing number of building occupations around the country. Greece’s troubled Socialist government is facing a growing number of protests against austerity measures, aimed at securing continued bailout loan payment from eurozone countries and the IMF. (Kostas Tsironis)
High school students chant slogans during a protest in front of the Greek Parliament in Athens, Thursday, Sept 29 2011. Weeks-long education protests have recently spread to state schools,with a growing number of building occupations around the country. Greece’s troubled Socialist government is facing a growing number of protests against austerity measures, aimed at securing continued bailout loan payment from eurozone countries and the IMF. (Kostas Tsironis)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict11.jpg) Members of French aid group Medecins du Monde carrying a giant cotton bud and placards reading ” Free consultations”, demonstrate for an Universal Health Coverage, outside a meeting of the G20 Labour and Employment Ministers in Paris, Monday, Sept. 26, 2011. (Thibault Camus)
Members of French aid group Medecins du Monde carrying a giant cotton bud and placards reading ” Free consultations”, demonstrate for an Universal Health Coverage, outside a meeting of the G20 Labour and Employment Ministers in Paris, Monday, Sept. 26, 2011. (Thibault Camus)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict12.jpg) Activists hold a prayer vigil at Sule pagoda in Yangon, Myanmar, Monday, Sept. 26, 2011. The protesters said they demonstrated to honor persons killed and jailed during pro-democracy protests for years ago led by Buddhist monks. (Khin Maung Win)
Activists hold a prayer vigil at Sule pagoda in Yangon, Myanmar, Monday, Sept. 26, 2011. The protesters said they demonstrated to honor persons killed and jailed during pro-democracy protests for years ago led by Buddhist monks. (Khin Maung Win)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict14.jpg) Demonstrators march near the headquarters of Tokyo Electric Power Co. (TEPCO) during their anti-nuclear power protest, in Tokyo, Saturday, Aug. 6, 2011. TEPCO’s Fukushima Dai-ichi nuclear power plant was crippled by an earthquake and tsunami March 11, which caused the worst nuclear crisis since Chernobyl. (Shizuo Kambayashi)
Demonstrators march near the headquarters of Tokyo Electric Power Co. (TEPCO) during their anti-nuclear power protest, in Tokyo, Saturday, Aug. 6, 2011. TEPCO’s Fukushima Dai-ichi nuclear power plant was crippled by an earthquake and tsunami March 11, which caused the worst nuclear crisis since Chernobyl. (Shizuo Kambayashi)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict13.jpg) In this June 24, 2011 photo, Pakistani students rally against right-wing student union Jamiat at the Punjab University in Lahore, Pakistan. Two months after the covert U.S. raid that killed Osama bin Laden, posters emblazoned with images of the burning World Trade Center towers appeared at the prestigious university advertising a literary contest to glorify the slain al-Qaida chief. (K.M. Chaudary)
In this June 24, 2011 photo, Pakistani students rally against right-wing student union Jamiat at the Punjab University in Lahore, Pakistan. Two months after the covert U.S. raid that killed Osama bin Laden, posters emblazoned with images of the burning World Trade Center towers appeared at the prestigious university advertising a literary contest to glorify the slain al-Qaida chief. (K.M. Chaudary)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict17.jpg) Women protest during a rally denouncing corruption, demanding better civil rights and demanding a new constitution, in Casablanca Sunday, April 24, 2011. Banners read, at left, “Freedom, equality and civil rights” and at right “Clause 19 of Constitution must go!” revering to King Mohammed VI’s power. (Abdeljalil Bounhar)
Women protest during a rally denouncing corruption, demanding better civil rights and demanding a new constitution, in Casablanca Sunday, April 24, 2011. Banners read, at left, “Freedom, equality and civil rights” and at right “Clause 19 of Constitution must go!” revering to King Mohammed VI’s power. (Abdeljalil Bounhar)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest/pict15.jpg) Women protest holding banners reading “the True Libya” and “Freedom for Libya” during a demonstration against Libyan leader Moammar Gadhafi in the centre of Madrid, Spain, Sunday, Feb. 27, 2011. (Andres Kudacki)
Women protest holding banners reading “the True Libya” and “Freedom for Libya” during a demonstration against Libyan leader Moammar Gadhafi in the centre of Madrid, Spain, Sunday, Feb. 27, 2011. (Andres Kudacki)















![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict27.jpg) A demonstrator sits holding a sign during a protest against bullfighting in Lima, Peru, Saturday, Nov. 5, 2011. Peru hosts the oldest bullring in the Americas, the Plaza de Acho, inaugurated in 1766 under the ruling of Viceroy Manuel de Amat y Juniet, where every year bullfighters compete for the renown ‘Escapulario de Oro’ or ‘Golden Scapular’, one of the most important bullfighting trophies worldwide. (Karel Navarro)
A demonstrator sits holding a sign during a protest against bullfighting in Lima, Peru, Saturday, Nov. 5, 2011. Peru hosts the oldest bullring in the Americas, the Plaza de Acho, inaugurated in 1766 under the ruling of Viceroy Manuel de Amat y Juniet, where every year bullfighters compete for the renown ‘Escapulario de Oro’ or ‘Golden Scapular’, one of the most important bullfighting trophies worldwide. (Karel Navarro)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict30.jpg) Iranian opposition members hold an old Iranian flag as they protest against the regime in their country, asking the release of jailed dissidents and union members, in Ankara, Turkey, Saturday, Nov. 5, 2011.(Burhan Ozbilici)
Iranian opposition members hold an old Iranian flag as they protest against the regime in their country, asking the release of jailed dissidents and union members, in Ankara, Turkey, Saturday, Nov. 5, 2011.(Burhan Ozbilici)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict23.jpg) An activist supporting the repeal of the Armed Forces Special Powers Act (AFSPA) stands in front of banners in support of rights activist Irom Chanu Sharmila during a protest in New Delhi on November 5, 2011. Sharmila has been on a 10-year hunger strike demanding the Indian government to repeal the AFSPA. Getty
An activist supporting the repeal of the Armed Forces Special Powers Act (AFSPA) stands in front of banners in support of rights activist Irom Chanu Sharmila during a protest in New Delhi on November 5, 2011. Sharmila has been on a 10-year hunger strike demanding the Indian government to repeal the AFSPA. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict25.jpg) More than 100 police moved on Occupy Sydney protesters at Martin Place October 23, 2011, resulting in the arrest of 40 people. Damian Baker
More than 100 police moved on Occupy Sydney protesters at Martin Place October 23, 2011, resulting in the arrest of 40 people. Damian Baker![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict24.jpg) Occupy Wall Street demonstrator Mimi Ho, right, gestures as she carries her daughter Juniper, 1, after she withdrew her savings from a Wells Fargo Bank as part of the protest in downtown Oakland, Calif. , Friday, Nov. 4, 2011. At left is Kimi Lee, who also withdrew her savings. Saturday is Bank Transfer Day for supporters to take their money out of major banks and put their money into smaller banks. AP
Occupy Wall Street demonstrator Mimi Ho, right, gestures as she carries her daughter Juniper, 1, after she withdrew her savings from a Wells Fargo Bank as part of the protest in downtown Oakland, Calif. , Friday, Nov. 4, 2011. At left is Kimi Lee, who also withdrew her savings. Saturday is Bank Transfer Day for supporters to take their money out of major banks and put their money into smaller banks. AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict21.jpg) Students stage a protest in front of the government house in Riga November 4, 2011. Thousands of students staged the protest against education budget cuts the Latvian government is planning for 2012, local media reported. Reuters
Students stage a protest in front of the government house in Riga November 4, 2011. Thousands of students staged the protest against education budget cuts the Latvian government is planning for 2012, local media reported. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict22.jpg) Albanian citizens protest in front of the parliament building to stop the passing of a law that will allow the import of waste into the country, in Tirana November 3, 2011. The Albanian government insists that the controversial bill will only allow the import of a limited list of non-toxic waste for recycling purposes, but environmental activists insist that bill would turn Albania into a backyard recycling bin of Europe?s richer countries. A similar attempt to pass a law that would allow import of waste was thwarted in 2004 due to strong public opposition. Reuters
Albanian citizens protest in front of the parliament building to stop the passing of a law that will allow the import of waste into the country, in Tirana November 3, 2011. The Albanian government insists that the controversial bill will only allow the import of a limited list of non-toxic waste for recycling purposes, but environmental activists insist that bill would turn Albania into a backyard recycling bin of Europe?s richer countries. A similar attempt to pass a law that would allow import of waste was thwarted in 2004 due to strong public opposition. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict7.jpg) University students with their necks painted protest at Bolivar square in Bogota, Colombia, Thursday Nov. 3, 2011. Their signs read in Spanish “We have the right to be outraged,” left, and “Excellent education and for all!!” Students are protesting education reforms planned by the government that propose private funding for public institutions. (Fernando Vergara)
University students with their necks painted protest at Bolivar square in Bogota, Colombia, Thursday Nov. 3, 2011. Their signs read in Spanish “We have the right to be outraged,” left, and “Excellent education and for all!!” Students are protesting education reforms planned by the government that propose private funding for public institutions. (Fernando Vergara)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict9.jpg) Protesters chant slogans in front of the Greek Parliament during an anti-austerity protest in Athens, Thursday, Nov. 3 2011. Greece’s prime minister abandoned his explosive plan to put a European rescue deal to popular vote and opened emergency talks Thursday with his opponents, demanding their support in parliament to pass the hard-fought agreement into law. (Kostas Tsironis)
Protesters chant slogans in front of the Greek Parliament during an anti-austerity protest in Athens, Thursday, Nov. 3 2011. Greece’s prime minister abandoned his explosive plan to put a European rescue deal to popular vote and opened emergency talks Thursday with his opponents, demanding their support in parliament to pass the hard-fought agreement into law. (Kostas Tsironis)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict11.jpg) Anti-government protesters pass through their makeshift barricades Thursday, Nov. 3, 2011, during a demonstration in the western village of Malkiya, Bahrain. Men, women and children waved national flags, chanted against the regime and called for prisoners to be freed. Such barricades are used in restive Shiite areas nationwide to slow riot police jeeps who often arrive to disperse the daily demonstrations. (Hasan Jamali)
Anti-government protesters pass through their makeshift barricades Thursday, Nov. 3, 2011, during a demonstration in the western village of Malkiya, Bahrain. Men, women and children waved national flags, chanted against the regime and called for prisoners to be freed. Such barricades are used in restive Shiite areas nationwide to slow riot police jeeps who often arrive to disperse the daily demonstrations. (Hasan Jamali)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict18.jpg) Aileen Mioko Smith, center, executive director of pro-sustainable energy NGO group Green Action, and supporters shout anti-nuclear slogans by a yarn ball made by women in Fukushima as they stage a sit-in demonstration, opposing the government’s nuclear energy policy in front of the Economy, Trade and Industry Ministry in Tokyo Thursday, Nov. 3, 2011. (Shuji Kajiyama)
Aileen Mioko Smith, center, executive director of pro-sustainable energy NGO group Green Action, and supporters shout anti-nuclear slogans by a yarn ball made by women in Fukushima as they stage a sit-in demonstration, opposing the government’s nuclear energy policy in front of the Economy, Trade and Industry Ministry in Tokyo Thursday, Nov. 3, 2011. (Shuji Kajiyama)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict16.jpg) An exile Tibetan woman tries to immolate herself as others from the community try to stop her, during a protest against China and to honor Tibetans who have immolated themselves since March in a restive Tibetan area of western China, in Katmandu, Nepal, Wednesday, Nov. 2, 2011. Protesters urged G20 leaders to raise the issue of rights violation and crackdown on monasteries in Tibet. (Niranjan Shrestha)
An exile Tibetan woman tries to immolate herself as others from the community try to stop her, during a protest against China and to honor Tibetans who have immolated themselves since March in a restive Tibetan area of western China, in Katmandu, Nepal, Wednesday, Nov. 2, 2011. Protesters urged G20 leaders to raise the issue of rights violation and crackdown on monasteries in Tibet. (Niranjan Shrestha)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict20.jpg) Occupy Chicago protesters march in downtown Chicago, Wednesday, Nov. 2, 2011. Protesters are gathering in Chicago’s financial district to march in solidarity with other anti-Wall Street protesters nationwide for an Iraq War veteran who was injured in clashes between protesters and police in California. (Nam Y. Huh)
Occupy Chicago protesters march in downtown Chicago, Wednesday, Nov. 2, 2011. Protesters are gathering in Chicago’s financial district to march in solidarity with other anti-Wall Street protesters nationwide for an Iraq War veteran who was injured in clashes between protesters and police in California. (Nam Y. Huh)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict19.jpg) An Occupy Oakland protester wears makeup in observance of the traditional Mexican holiday “Day of the Dead,” Wednesday, Nov. 2, 2011, in Oakland, Calif. Oakland’s citywide general strike, a hastily planned and ambitious action called by Occupy protesters a day after police forcibly removed their City Hall encampment last week, seeks to shut down the Port of Oakland. (Ben Margot)
An Occupy Oakland protester wears makeup in observance of the traditional Mexican holiday “Day of the Dead,” Wednesday, Nov. 2, 2011, in Oakland, Calif. Oakland’s citywide general strike, a hastily planned and ambitious action called by Occupy protesters a day after police forcibly removed their City Hall encampment last week, seeks to shut down the Port of Oakland. (Ben Margot)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict5.jpg) A woman holds her child during a protest in Ciudad Juarez November 1, 2011. Police arrested around 25 protesters as they were trying to put up crosses in a public area in representation of the thousands of victims of the drug war. Reuters
A woman holds her child during a protest in Ciudad Juarez November 1, 2011. Police arrested around 25 protesters as they were trying to put up crosses in a public area in representation of the thousands of victims of the drug war. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict14.jpg) In this photograph taken by AP Images for AIDS Healthcare Foundation, Protestors from the AIDS Healthcare Foundation deliver a bag full of petitions requesting lower AIDS drug pricing to Johnson & Johnson headquarters in New Brunswick, NJ on Wednesday, Nov. 2, 2011. (Charles Sykes)
In this photograph taken by AP Images for AIDS Healthcare Foundation, Protestors from the AIDS Healthcare Foundation deliver a bag full of petitions requesting lower AIDS drug pricing to Johnson & Johnson headquarters in New Brunswick, NJ on Wednesday, Nov. 2, 2011. (Charles Sykes)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict10.jpg) An anti-G20 demonstrator poses on a fake beach during a photobooth session as she takes part in a protest against globalisation in Nice, southeastern France, November 2, 2011. G20 leaders will gather in Cannes for the final summit of France’s presidency on November 3 and 4. Reuters
An anti-G20 demonstrator poses on a fake beach during a photobooth session as she takes part in a protest against globalisation in Nice, southeastern France, November 2, 2011. G20 leaders will gather in Cannes for the final summit of France’s presidency on November 3 and 4. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict17.jpg) A woman involved in the clean-up operation after the Chernobyl nuclear disaster shouts slogans during a protest in front of riot police at Cabinet in Kiev, Ukraine, Wednesday, Nov. 2, 2011. The veterans were demanding the right to keep the social benefits given to them after the clean-up. (Efrem Lukatsky)
A woman involved in the clean-up operation after the Chernobyl nuclear disaster shouts slogans during a protest in front of riot police at Cabinet in Kiev, Ukraine, Wednesday, Nov. 2, 2011. The veterans were demanding the right to keep the social benefits given to them after the clean-up. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict8.jpg) Indian police officers detain Members of the Tibetan Youth Congress during a protest, on the eve of G20 summit in France , outside the Chinese Embassy in New Delhi on November 2, 2011. The protesters flew Tibetan flags,and burned Chinese flags to express their opposition to China’s policies in Tibet, and to call for support for their movement from leaders of the G20. Getty
Indian police officers detain Members of the Tibetan Youth Congress during a protest, on the eve of G20 summit in France , outside the Chinese Embassy in New Delhi on November 2, 2011. The protesters flew Tibetan flags,and burned Chinese flags to express their opposition to China’s policies in Tibet, and to call for support for their movement from leaders of the G20. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict15.jpg) Protester Alexis Marvel, of Boston, front, holds an American flag and shouts slogans while joining with members of the Occupy Boston movement, students from area colleges, and union workers as they march through downtown Boston, Wednesday, Nov. 2, 2011. The march was held to protest the nations growing student debt burden. AP
Protester Alexis Marvel, of Boston, front, holds an American flag and shouts slogans while joining with members of the Occupy Boston movement, students from area colleges, and union workers as they march through downtown Boston, Wednesday, Nov. 2, 2011. The march was held to protest the nations growing student debt burden. AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict6.jpg) Demonstrators shout slogans in front of riot police on November 2, 2011 during a protest as the Ukrainian cabinet was meeting in Kiev. Ukrainian veterans of the clean-up from the Chernobyl nuclear disaster are demonstrating against planned benefit cuts. In September, lawmakers gave initial approval to a bill cutting back benefits paid to those who helped clean up the April 1986 nuclear disaster and those who still live on the affected lands. Getty
Demonstrators shout slogans in front of riot police on November 2, 2011 during a protest as the Ukrainian cabinet was meeting in Kiev. Ukrainian veterans of the clean-up from the Chernobyl nuclear disaster are demonstrating against planned benefit cuts. In September, lawmakers gave initial approval to a bill cutting back benefits paid to those who helped clean up the April 1986 nuclear disaster and those who still live on the affected lands. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict2.jpg) Tibetan nationals demonstrate to protest against China’s President Hu Jintao visit to France for Cannes’ G20 meeting, on November 2, 2011 in Paris. Getty
Tibetan nationals demonstrate to protest against China’s President Hu Jintao visit to France for Cannes’ G20 meeting, on November 2, 2011 in Paris. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict0.jpg) Young unemployed graduates protest against unemployment and the cost of living, in front of the Moroccan Parliament in Rabat November 2, 2011. Reuters
Young unemployed graduates protest against unemployment and the cost of living, in front of the Moroccan Parliament in Rabat November 2, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict1.jpg) Anti-Wall Street protesters demonstrate in front of a closed bank in Oakland, California, November 2, 2011. Hundreds of protesters took to the streets of downtown Oakland at the start of what they called a general strike to protest economic conditions and police brutality in the city. Reuters
Anti-Wall Street protesters demonstrate in front of a closed bank in Oakland, California, November 2, 2011. Hundreds of protesters took to the streets of downtown Oakland at the start of what they called a general strike to protest economic conditions and police brutality in the city. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict3.jpg) Members of the New York City chapter of Iraq Veterans Against the War and dozens of other uniformed veterans known as ‘Veterans of the 99%’ march from Vietnam Veterans Plaza to Zucotti Park where the Occupy Wall Street movement is centered on November 2, 2011 in New York City. The veterans groups, which feature current and former members of the United States military, marched in support of Occupy Wall Street and to pay homage to Scott Olsen, a former Marine and Iraq War vet who sustained a skull fracture after he was injured by police at an Occupy Oakland protest. Getty
Members of the New York City chapter of Iraq Veterans Against the War and dozens of other uniformed veterans known as ‘Veterans of the 99%’ march from Vietnam Veterans Plaza to Zucotti Park where the Occupy Wall Street movement is centered on November 2, 2011 in New York City. The veterans groups, which feature current and former members of the United States military, marched in support of Occupy Wall Street and to pay homage to Scott Olsen, a former Marine and Iraq War vet who sustained a skull fracture after he was injured by police at an Occupy Oakland protest. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict4.jpg) A demonstrator tries to cross a police line during a protest against the Islamist Ennahda movement in Tunis November 2, 2011. The moderate Islamist party Ennahda, which advocates democracy and pledges not to impose religious bans on the secularist minority here, won 40 percent of the vote in the October 23 election for a constituent assembly. Reuters
A demonstrator tries to cross a police line during a protest against the Islamist Ennahda movement in Tunis November 2, 2011. The moderate Islamist party Ennahda, which advocates democracy and pledges not to impose religious bans on the secularist minority here, won 40 percent of the vote in the October 23 election for a constituent assembly. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict12.jpg) A woman holds a placard on November 1, 2011 during a demonstration in the French city of Nice, two days ahead of the G20 summit to be held in Cannes on November 3 and 4. Thousands of anti-capitalists are to march through the streets of Nice today to protest corporate greed ahead of the G20 summit, echoing protests worldwide. The placard reads : ‘Life not money’. Getty
A woman holds a placard on November 1, 2011 during a demonstration in the French city of Nice, two days ahead of the G20 summit to be held in Cannes on November 3 and 4. Thousands of anti-capitalists are to march through the streets of Nice today to protest corporate greed ahead of the G20 summit, echoing protests worldwide. The placard reads : ‘Life not money’. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict13.jpg) In this Thursday, Sept. 8, 2011 file photo, a female protestor, center, flashes the victory sign during a demonstration in Sanaa, Yemen demanding the resignation of President Ali Abdullah Saleh. Women are fighting to keep a voice for their rights sounding out amid the tumult of Yemen’s landmark revolt. The main goal of the protests by millions around the country, day in and day out since February, is the ouster of President Saleh.
In this Thursday, Sept. 8, 2011 file photo, a female protestor, center, flashes the victory sign during a demonstration in Sanaa, Yemen demanding the resignation of President Ali Abdullah Saleh. Women are fighting to keep a voice for their rights sounding out amid the tumult of Yemen’s landmark revolt. The main goal of the protests by millions around the country, day in and day out since February, is the ouster of President Saleh.









 Zielvorstellung Marine 2025+
Zielvorstellung Marine 2025+




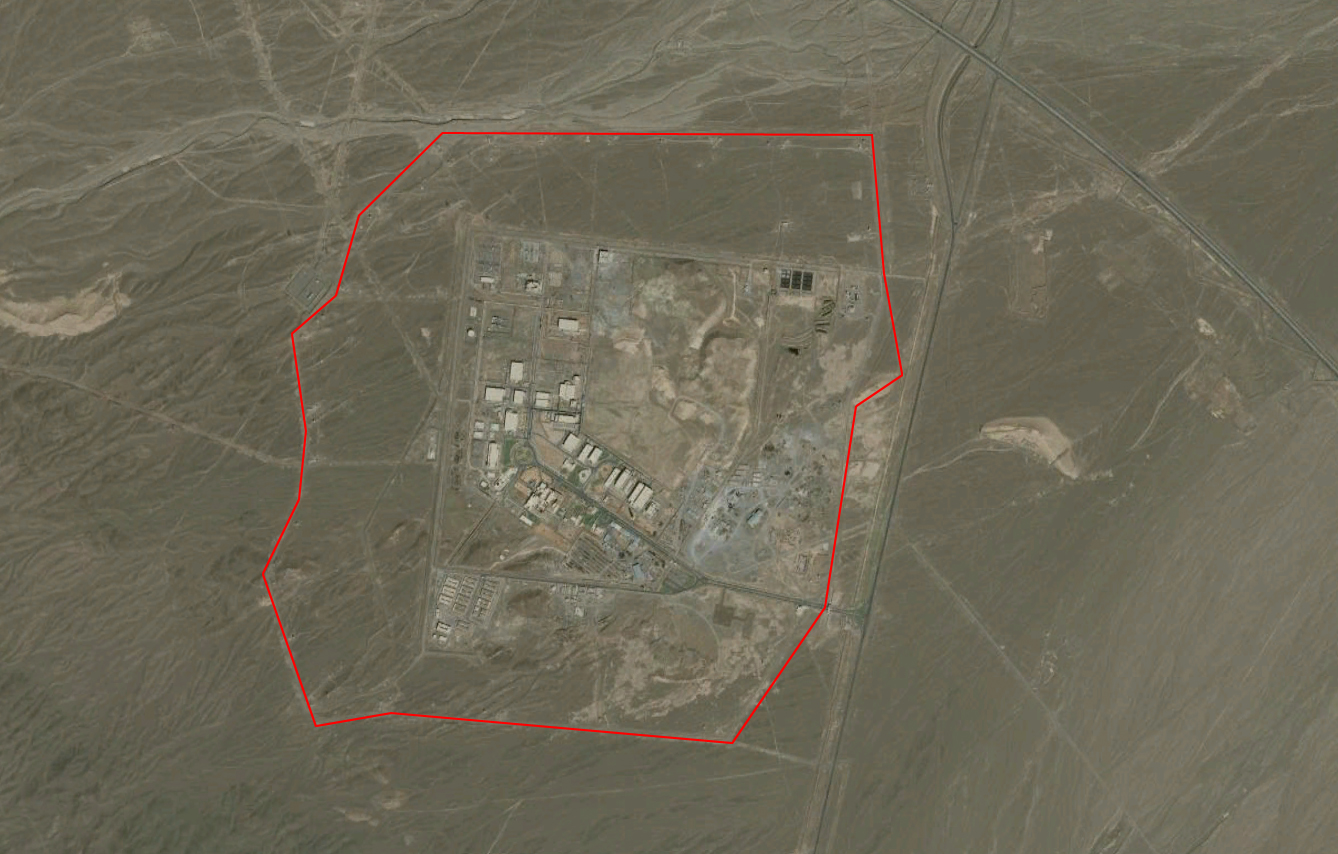
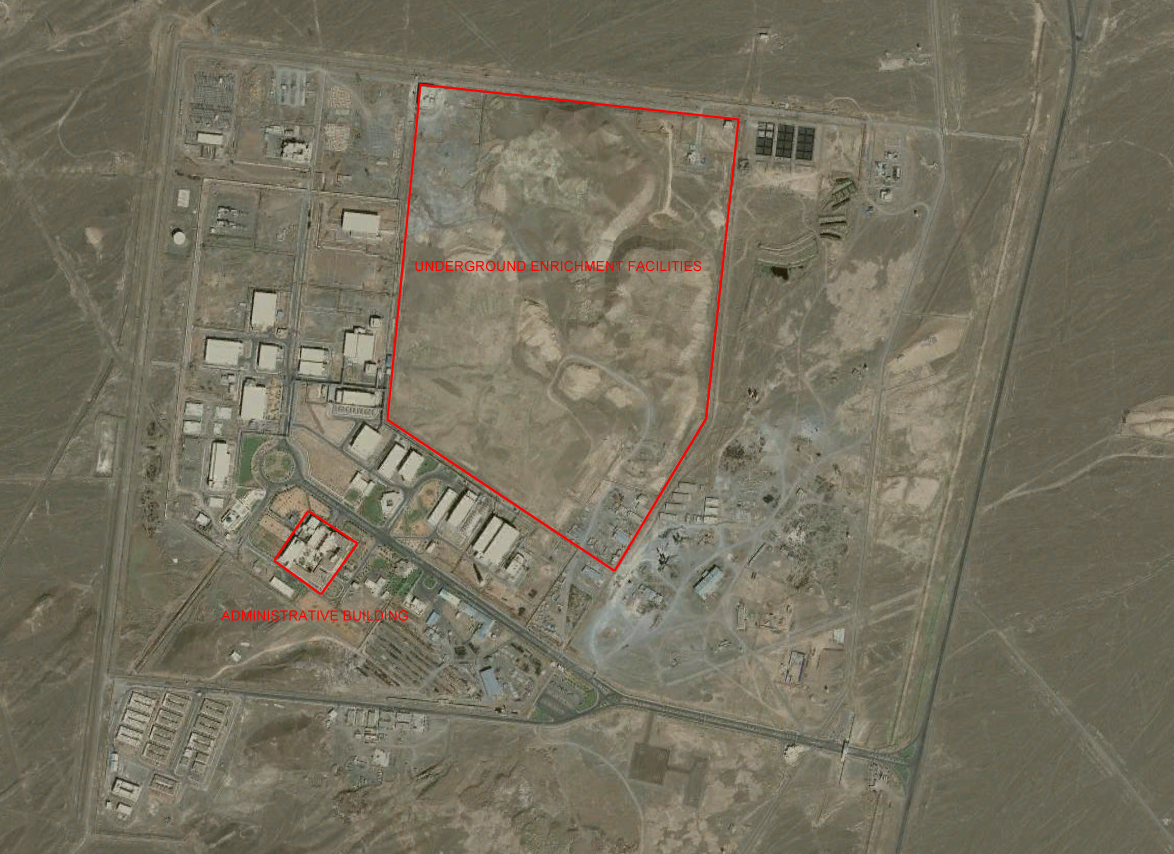
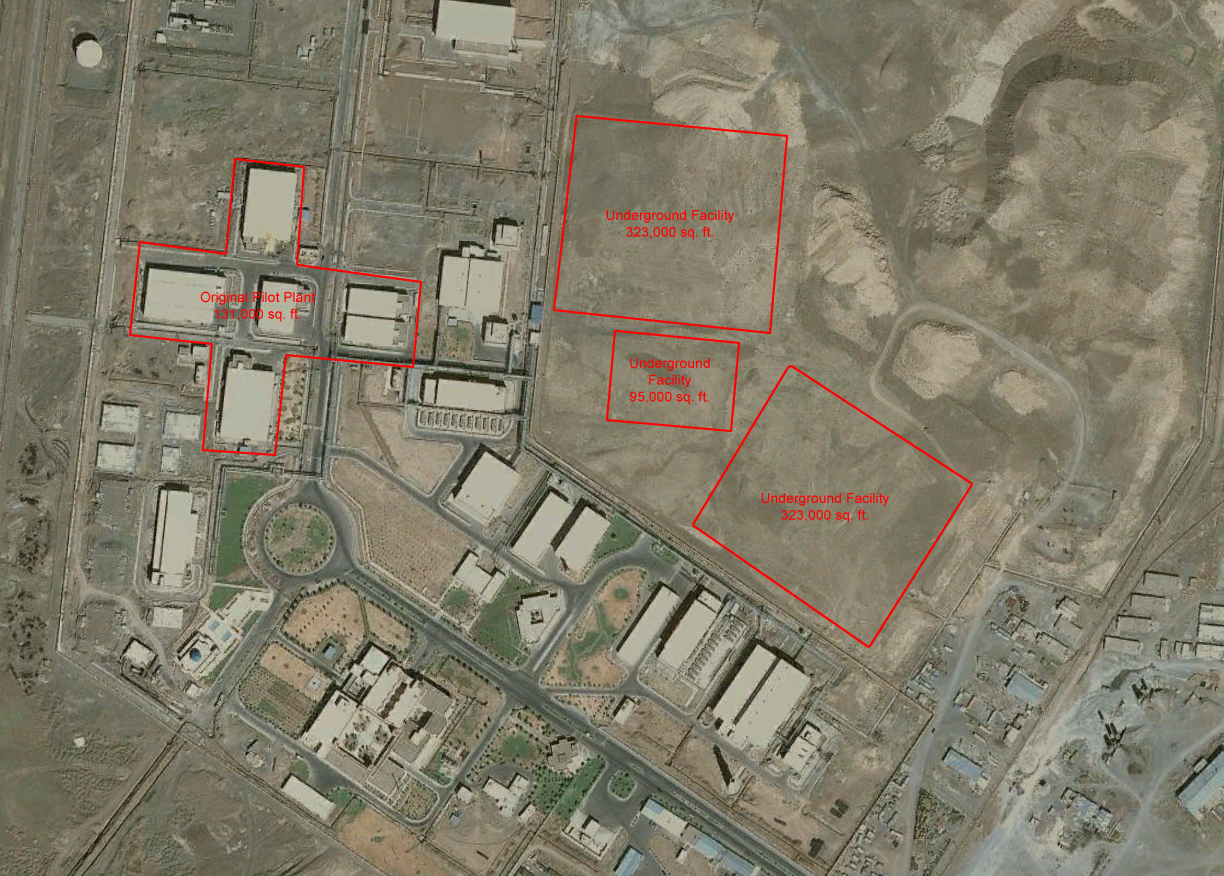





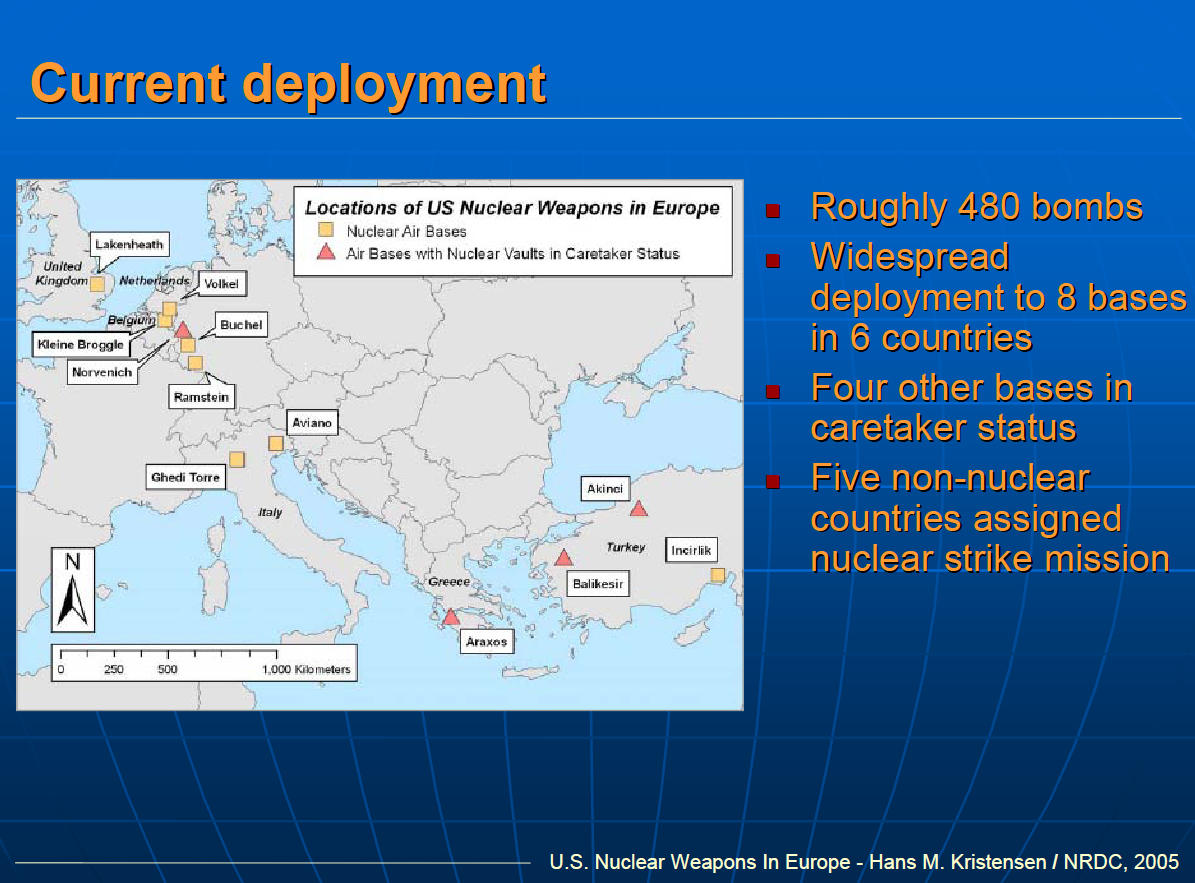

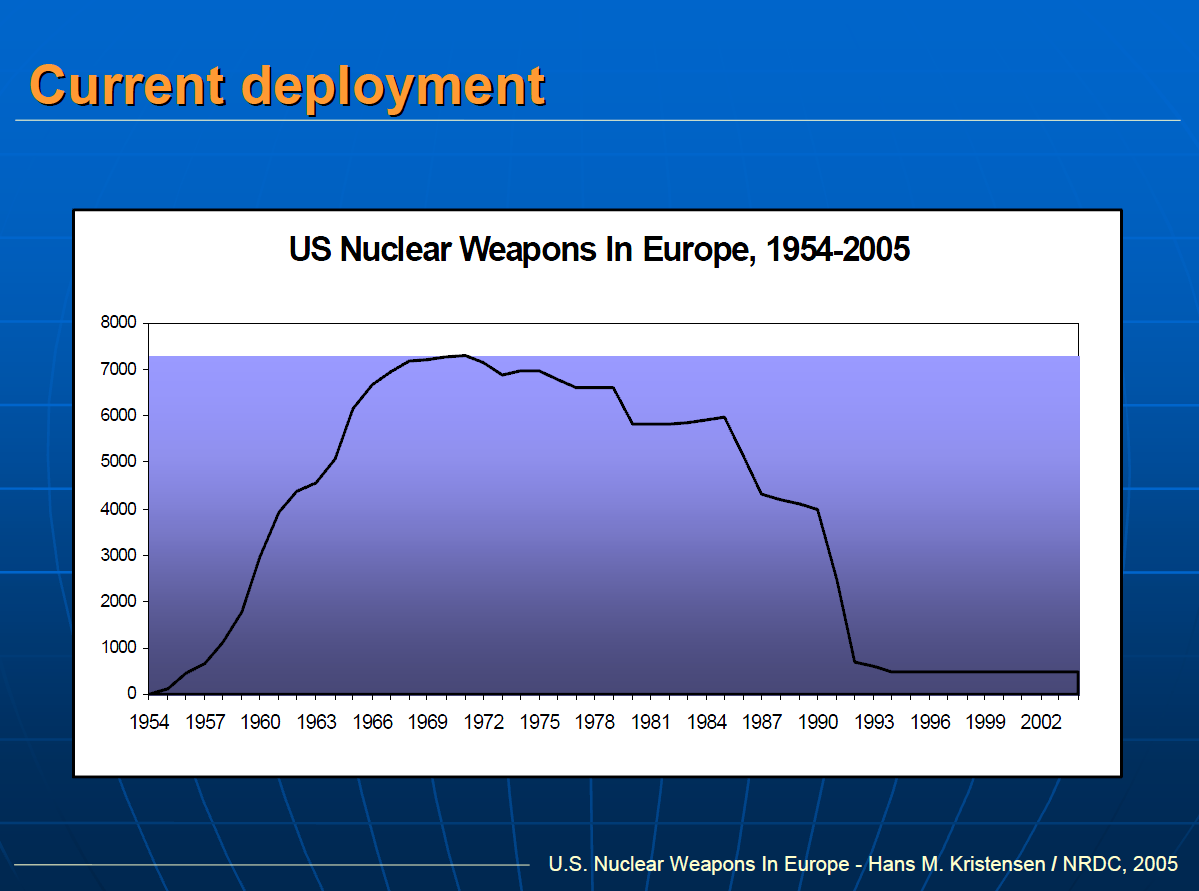
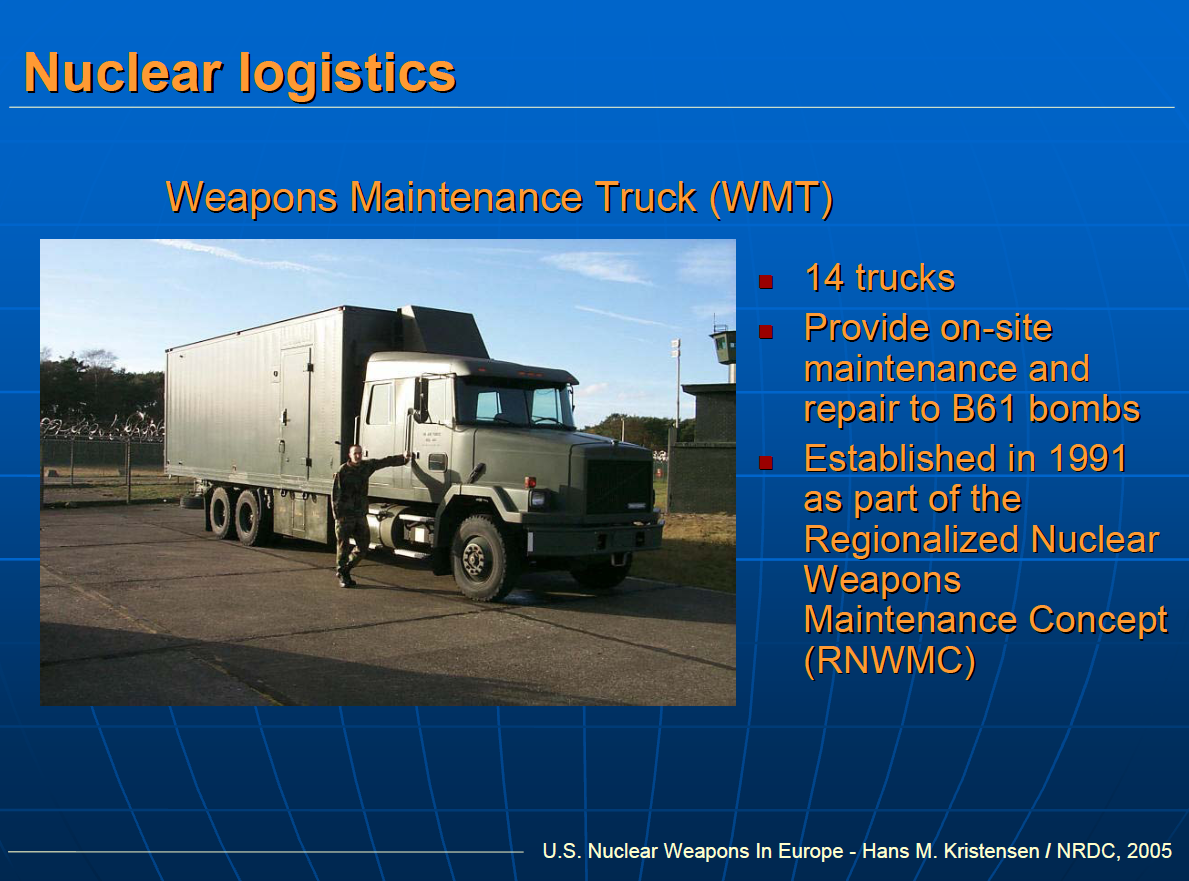
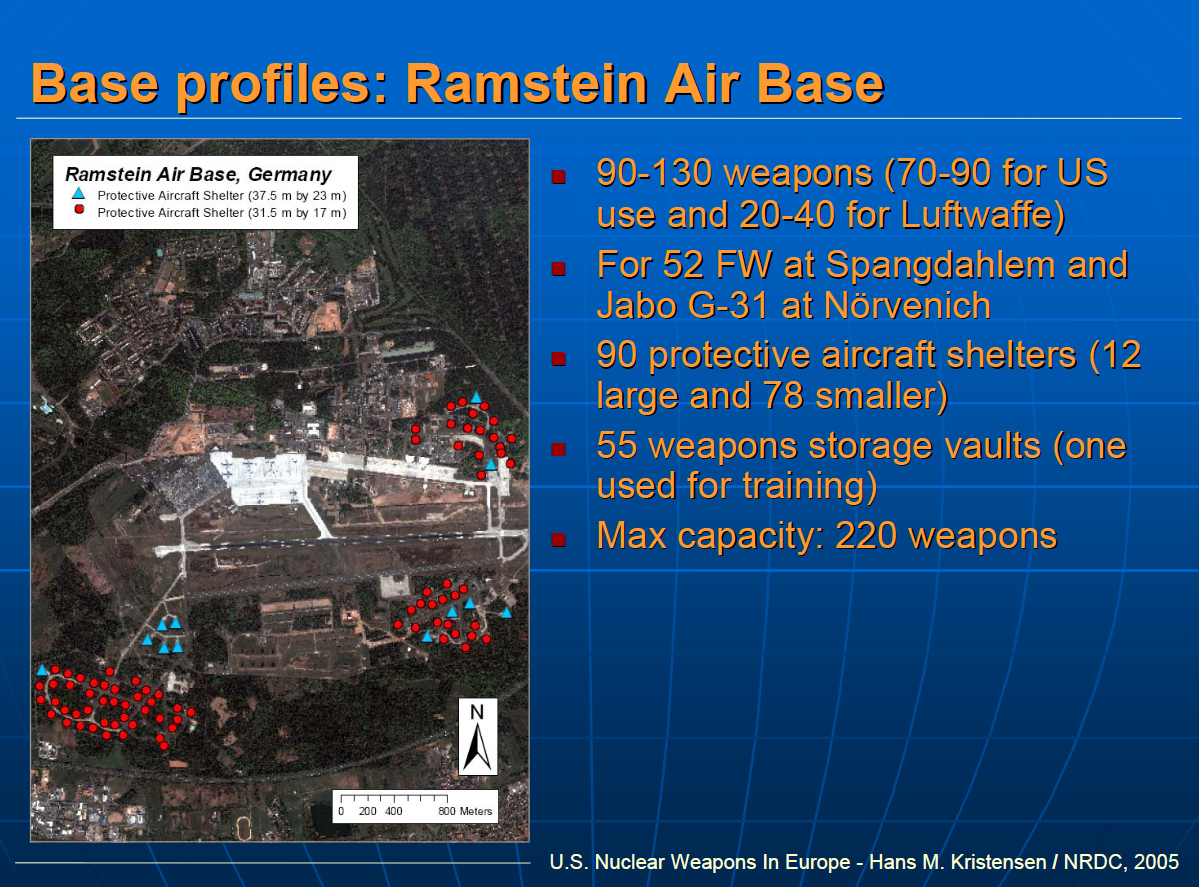


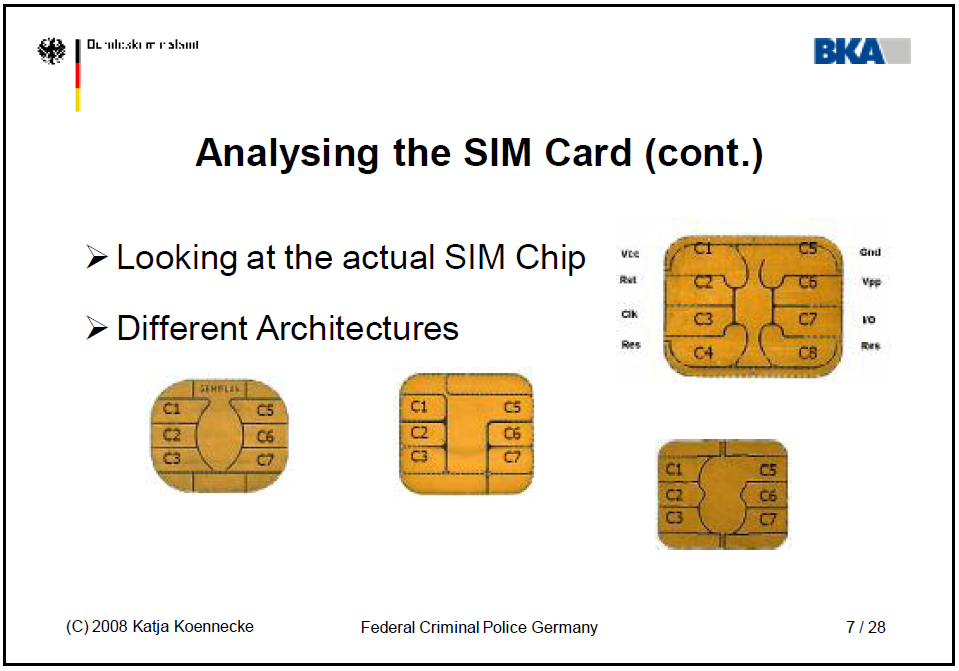
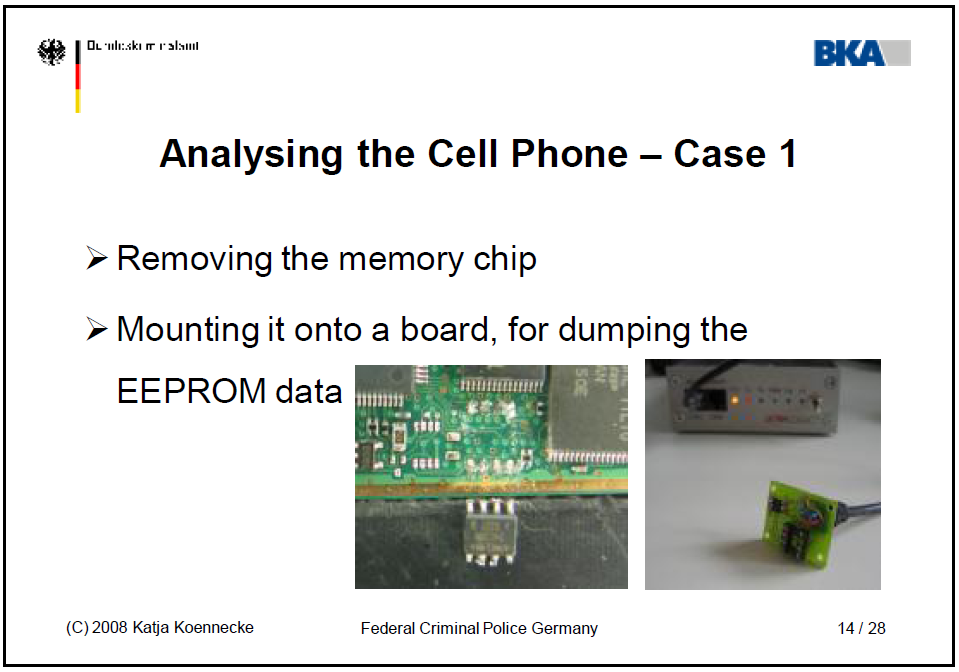




 h
h




![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict45.jpg) Ellinda McKinney offers her message to police during the Occupy Denver protest, Saturday, Oct. 29, 2011 in Denver. Occupy Denver protesters and law enforcement officers faced off on the steps of the state Capitol and Civic Center after protesters marched through downtown Denver for the fourth week in a row. (Craig F. Walker)
Ellinda McKinney offers her message to police during the Occupy Denver protest, Saturday, Oct. 29, 2011 in Denver. Occupy Denver protesters and law enforcement officers faced off on the steps of the state Capitol and Civic Center after protesters marched through downtown Denver for the fourth week in a row. (Craig F. Walker)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict28.jpg) A woman performs as a widow during a protest against violence in Mexico City on October 28, 2011. More than 41,000 people have been killed in rising drug-related violence in Mexico since December 2006, when President Felipe Calderon deployed soldiers and federal police to take on organized crime. Getty
A woman performs as a widow during a protest against violence in Mexico City on October 28, 2011. More than 41,000 people have been killed in rising drug-related violence in Mexico since December 2006, when President Felipe Calderon deployed soldiers and federal police to take on organized crime. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict31.jpg) Demonstrators march towards the Treasury Department and the White House in Washington on October 29, 2011 during a protest organized by the Occupy DC movement to call for increased taxes on the rich, a so-called ‘Robin Hood tax.’ Getty
Demonstrators march towards the Treasury Department and the White House in Washington on October 29, 2011 during a protest organized by the Occupy DC movement to call for increased taxes on the rich, a so-called ‘Robin Hood tax.’ Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict29.jpg) Israelis protest against the high costs of living in Tel Aviv, Israel, Saturday, Oct. 29, 2011. According to police estimates over 30,000 participated in the Tel Aviv protest and thousands of others protested in Jerusalem on Saturday. A wave of social protests swept the country this summer as Israelis held mass protests to protest a wide range of social issues, especially high housing costs. (Maya Hasson)
Israelis protest against the high costs of living in Tel Aviv, Israel, Saturday, Oct. 29, 2011. According to police estimates over 30,000 participated in the Tel Aviv protest and thousands of others protested in Jerusalem on Saturday. A wave of social protests swept the country this summer as Israelis held mass protests to protest a wide range of social issues, especially high housing costs. (Maya Hasson)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict23.jpg) A protester of the Occupy Berlin movement drinks champagne during a protest demonstration against the finance system in central Berlin, Saturday, Oct. 29, 2011. (Markus Schreiber)
A protester of the Occupy Berlin movement drinks champagne during a protest demonstration against the finance system in central Berlin, Saturday, Oct. 29, 2011. (Markus Schreiber)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict27.jpg) A demonstrator is seen during a protest organized by the Islamic Central Council of Switzerland (ICCS), on October 29, 2011 in Bern. More than 1000 persons attend the demonstration. The Islamic Central Council of Switzerland (ICCS), a conservative Muslim group was under criticism after chosen a symbol reminiscent of the Jewish Star of David with the word ‘Muslim’ framed by a yellow star. Getty
A demonstrator is seen during a protest organized by the Islamic Central Council of Switzerland (ICCS), on October 29, 2011 in Bern. More than 1000 persons attend the demonstration. The Islamic Central Council of Switzerland (ICCS), a conservative Muslim group was under criticism after chosen a symbol reminiscent of the Jewish Star of David with the word ‘Muslim’ framed by a yellow star. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict26.jpg) A woman holds a crucifix and a rosary as she demonstrates among around one thousand people called by ‘Civitas’ association, close to Christian fundamentalists on October 29, 2011 in Paris to protest against the play ‘Sur le concept du visage du fils de Dieu’ (On the Concept of the Face, Regarding the Son of God) by Italian Romeo Castellucci which is performed at the Paris Theatre de la Ville from October 20 to 30. Every evening, protesters demonstrate in front of the building to denounce the’ of the play which they found insulting. Getty
A woman holds a crucifix and a rosary as she demonstrates among around one thousand people called by ‘Civitas’ association, close to Christian fundamentalists on October 29, 2011 in Paris to protest against the play ‘Sur le concept du visage du fils de Dieu’ (On the Concept of the Face, Regarding the Son of God) by Italian Romeo Castellucci which is performed at the Paris Theatre de la Ville from October 20 to 30. Every evening, protesters demonstrate in front of the building to denounce the’ of the play which they found insulting. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict25.jpg) Occupy Nashville protesters, from the left, Megan Riges, Lauren Plummer and Lindsey Krinks, celebrate Friday, Oct. 28, 2011, after they were released by police after being arrested overnight on Legislative Plaza in downtown Nashville, Tenn. Twenty-nine Wall Street protesters in Nashville have been issued misdemeanor citations for criminal trespassing after being arrested by state troopers overnight. (John Partipilo)
Occupy Nashville protesters, from the left, Megan Riges, Lauren Plummer and Lindsey Krinks, celebrate Friday, Oct. 28, 2011, after they were released by police after being arrested overnight on Legislative Plaza in downtown Nashville, Tenn. Twenty-nine Wall Street protesters in Nashville have been issued misdemeanor citations for criminal trespassing after being arrested by state troopers overnight. (John Partipilo)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict24.jpg) Protesters affiliated with the Occupy Wall Street Movement are seen at the Tennessee Capitol, Friday, Oct. 28, 2011. Tennessee’s safety commissioner says Republican Gov. Bill Haslam’s office approved a pre-dawn roundup of Wall Street protesters from the state Capitol grounds. Twenty-nine people were arrested, but a night judge refused to sign warrants because the policy had only been in effect since the previous afternoon. (Erik Schelzig)
Protesters affiliated with the Occupy Wall Street Movement are seen at the Tennessee Capitol, Friday, Oct. 28, 2011. Tennessee’s safety commissioner says Republican Gov. Bill Haslam’s office approved a pre-dawn roundup of Wall Street protesters from the state Capitol grounds. Twenty-nine people were arrested, but a night judge refused to sign warrants because the policy had only been in effect since the previous afternoon. (Erik Schelzig)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict10.jpg) A dressed woman attends a protest in Bogota, Colombia, Wednesday Oct. 26, 2011. The protest was against education reforms planned by the government that propose private funding for public institutions. (Fernando Vergara)
A dressed woman attends a protest in Bogota, Colombia, Wednesday Oct. 26, 2011. The protest was against education reforms planned by the government that propose private funding for public institutions. (Fernando Vergara)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict20.jpg) Activists of Femen, a Ukrainian women movement, wearing masks representing the slaughtered animals, shout slogans and hold placards reading ‘Zoomorgue’, ‘Slaughten house’, ‘Zooghetto’ as they stage a topless protest on a roof at the entrance of the zoo in Kiev on October 27, 2011. They rally against, as they say, the intolerable living conditions for animals in the zoo. Every year the Zoo is claiming the lives of hundreds of rare and exotic animals, that die a horrific death of hunger, cold or disease, as they report to AFP. The FEMEN movement demands that the Ukrainian authorities close the Kievs ZooMorgue as they call it. Getty
Activists of Femen, a Ukrainian women movement, wearing masks representing the slaughtered animals, shout slogans and hold placards reading ‘Zoomorgue’, ‘Slaughten house’, ‘Zooghetto’ as they stage a topless protest on a roof at the entrance of the zoo in Kiev on October 27, 2011. They rally against, as they say, the intolerable living conditions for animals in the zoo. Every year the Zoo is claiming the lives of hundreds of rare and exotic animals, that die a horrific death of hunger, cold or disease, as they report to AFP. The FEMEN movement demands that the Ukrainian authorities close the Kievs ZooMorgue as they call it. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict22.jpg) Supporters of Pakistan Muslim League-N (PML-N) attend a rally against Pakistan’s President Asif Ali Zardari in Lahore on October 28, 2011. More than 30,000 supporters of Pakistan’s main opposition party took to the streets in a protest rally on October 28, burning an effigy of President Asif Ali Zardari and demanding that he quit. The Pakistan Muslim League-N (PML-N) called the rally in Lahore to exploit talk of early elections in its political heartland, where it controls the Punjab provincial government despite being in opposition at national level. Getty
Supporters of Pakistan Muslim League-N (PML-N) attend a rally against Pakistan’s President Asif Ali Zardari in Lahore on October 28, 2011. More than 30,000 supporters of Pakistan’s main opposition party took to the streets in a protest rally on October 28, burning an effigy of President Asif Ali Zardari and demanding that he quit. The Pakistan Muslim League-N (PML-N) called the rally in Lahore to exploit talk of early elections in its political heartland, where it controls the Punjab provincial government despite being in opposition at national level. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict11.jpg) Supporters of Pakistani politician Imran Khan and chief of Tehreek-e-Insaf (Movement for Justice) party, carry placards as they march during protest rally in Islamabad on October 28, 2011 against US drone attacks in Pakistani tribal region. Khan staged a rally along with tribal elders in Islamabad against the continued US drone attacks in tribal areas which they said were killing hundreds of innocent people. Nearly 60 US drone strikes have been reported in Pakistan so far this year, dozens of them since Navy SEALs killed Al-Qaeda leader Osama bin Laden in the garrison city of Abbottabad, close to the capital Islamabad, on May 2. Getty
Supporters of Pakistani politician Imran Khan and chief of Tehreek-e-Insaf (Movement for Justice) party, carry placards as they march during protest rally in Islamabad on October 28, 2011 against US drone attacks in Pakistani tribal region. Khan staged a rally along with tribal elders in Islamabad against the continued US drone attacks in tribal areas which they said were killing hundreds of innocent people. Nearly 60 US drone strikes have been reported in Pakistan so far this year, dozens of them since Navy SEALs killed Al-Qaeda leader Osama bin Laden in the garrison city of Abbottabad, close to the capital Islamabad, on May 2. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict0.jpg) Protesters throw mud at a caricature of President Benigno Aquino III during a protest Friday Oct. 28, 2011 in Manila, Philippines against the President’s alleged continued support for big corporations including the big three oil companies in the country. The protest, part of the nationwide “Women’s Day of Protest,” was held following another round of oil price hike implemented late last week. (Bullit Marquez)
Protesters throw mud at a caricature of President Benigno Aquino III during a protest Friday Oct. 28, 2011 in Manila, Philippines against the President’s alleged continued support for big corporations including the big three oil companies in the country. The protest, part of the nationwide “Women’s Day of Protest,” was held following another round of oil price hike implemented late last week. (Bullit Marquez)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict6.jpg) Relatives of missing Kashmiri youth participate in a protest demonstration organized by the Association of Parents of Disappeared Persons (APDP) in Srinagar, India, Friday, Oct. 28, 2011. According to APDP some 8,000-10,000 people have gone missing since the beginning of the Kashmir conflict in 1989, after being arrested by Indian security forces and other security agencies. (Dar Yasin)
Relatives of missing Kashmiri youth participate in a protest demonstration organized by the Association of Parents of Disappeared Persons (APDP) in Srinagar, India, Friday, Oct. 28, 2011. According to APDP some 8,000-10,000 people have gone missing since the beginning of the Kashmir conflict in 1989, after being arrested by Indian security forces and other security agencies. (Dar Yasin)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict5.jpg) Anti-austerity protesters shout slogans before a scheduled military parade in the northern Greek city of Thessaloniki, Friday, Oct. 28, 2011. Thousands of anti-austerity protesters in the city forced the cancellation of Friday’s annual military parade commemorating Greece’s entry into World War II. The demonstrators heckled Greek President Karolos Papoulias and other attending officials, calling Papoulias a traitor. (Nikolas Giakoumidis)
Anti-austerity protesters shout slogans before a scheduled military parade in the northern Greek city of Thessaloniki, Friday, Oct. 28, 2011. Thousands of anti-austerity protesters in the city forced the cancellation of Friday’s annual military parade commemorating Greece’s entry into World War II. The demonstrators heckled Greek President Karolos Papoulias and other attending officials, calling Papoulias a traitor. (Nikolas Giakoumidis)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict12.jpg) Campaigners on the ‘Occupy London Stock Exchange’ protest encampment outside St Paul’s Cathedral on October 28, 2011 in London, England. St Paul’s Cathedral is due to reopen after being closed due to the adjacent ‘Occupy London Stock Exchange’ protest against the global financial system which has been in place for almost two weeks. Getty
Campaigners on the ‘Occupy London Stock Exchange’ protest encampment outside St Paul’s Cathedral on October 28, 2011 in London, England. St Paul’s Cathedral is due to reopen after being closed due to the adjacent ‘Occupy London Stock Exchange’ protest against the global financial system which has been in place for almost two weeks. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict13.jpg) Filipino Muslims hold their Friday prayers near the Presidential Palace during a “Prayer-for-Peace” rally Friday Oct. 28, 2011 in Manila, Philippines. The prayer protest was held to call for peace following the military’s launching of air strikes and military operations after one of the worst clashes in three years with the Moro Islamic Liberation Front (MILF) this month killed 26 soldiers, three policemen and an undetermined number of Muslim rebels. Close to 30,000 civilians have been displaced in the ongoing operation, officials said. AP
Filipino Muslims hold their Friday prayers near the Presidential Palace during a “Prayer-for-Peace” rally Friday Oct. 28, 2011 in Manila, Philippines. The prayer protest was held to call for peace following the military’s launching of air strikes and military operations after one of the worst clashes in three years with the Moro Islamic Liberation Front (MILF) this month killed 26 soldiers, three policemen and an undetermined number of Muslim rebels. Close to 30,000 civilians have been displaced in the ongoing operation, officials said. AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict14.jpg) A man consoles a distressed woman as she weeps at a protest during the Commonwealth Heads of Government Meeting (CHOGM) in Perth, Australia, Friday, Oct. 28, 2011. Queen Elizabeth II opened CHOGM Friday with more than 50 commonwealth nations’ leaders attending the three-day forum to discuss global and Commonwealth issues and collective policies and initiatives. AP
A man consoles a distressed woman as she weeps at a protest during the Commonwealth Heads of Government Meeting (CHOGM) in Perth, Australia, Friday, Oct. 28, 2011. Queen Elizabeth II opened CHOGM Friday with more than 50 commonwealth nations’ leaders attending the three-day forum to discuss global and Commonwealth issues and collective policies and initiatives. AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict15.jpg) Members of the Mexican Huichole community take part in a protest against Canadian mining projects in Mexico City on October 27, 2011. Huicholes from Durango, Nayarit and Jalisco marched along Reforma avenue towards the presidential palace to demand the end of the Canadian exploitation of silver in Cerro del Quemado, San Luis Potosi, arguing it affects nature and their sacred path. Getty
Members of the Mexican Huichole community take part in a protest against Canadian mining projects in Mexico City on October 27, 2011. Huicholes from Durango, Nayarit and Jalisco marched along Reforma avenue towards the presidential palace to demand the end of the Canadian exploitation of silver in Cerro del Quemado, San Luis Potosi, arguing it affects nature and their sacred path. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict16.jpg) A member of the Mexican Huichole community takes part in a protest against Canadian mining projects in Mexico City on October 27, 2011. Huicholes from Durango, Nayarit and Jalisco marched along Reforma avenue towards the presidential palace to demand the end of the Canadian exploitation of silver in Cerro del Quemado, San Luis Potosi, arguing it affects nature and their sacred path. Getty
A member of the Mexican Huichole community takes part in a protest against Canadian mining projects in Mexico City on October 27, 2011. Huicholes from Durango, Nayarit and Jalisco marched along Reforma avenue towards the presidential palace to demand the end of the Canadian exploitation of silver in Cerro del Quemado, San Luis Potosi, arguing it affects nature and their sacred path. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict17.jpg) A resident speaks with journalists as they protest outside the refinery compound of Italian oil company Eni at the town of Tazarka, about 70 km (43.5 miles) south-east of capital Tunis October 27, 2011. The protesters say that the refinery owners have not honoured their commitments to provide the local community with jobs and investments in infrastructure. Message written in Arabic reads “protest”. Reuters
A resident speaks with journalists as they protest outside the refinery compound of Italian oil company Eni at the town of Tazarka, about 70 km (43.5 miles) south-east of capital Tunis October 27, 2011. The protesters say that the refinery owners have not honoured their commitments to provide the local community with jobs and investments in infrastructure. Message written in Arabic reads “protest”. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict19.jpg) People march during a protest in Zhili town, Huzhou city, Zhejiang province October 27, 2011. Hundreds of people have clashed with police and smashed public property in China’s eastern Zhejiang province after a dispute between tax authorities and a local shop owner snowballed into protests, a government-run news site said. Reuters
People march during a protest in Zhili town, Huzhou city, Zhejiang province October 27, 2011. Hundreds of people have clashed with police and smashed public property in China’s eastern Zhejiang province after a dispute between tax authorities and a local shop owner snowballed into protests, a government-run news site said. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict18.jpg) People watch as riot police walk along the central square during a protest in Zhili town, Huzhou city, Zhejiang province October 27, 2011. Hundreds of people have clashed with police and smashed public property in China’s eastern Zhejiang province after a dispute between tax authorities and a local shop owner snowballed into protests, a government-run news site said. Reuters
People watch as riot police walk along the central square during a protest in Zhili town, Huzhou city, Zhejiang province October 27, 2011. Hundreds of people have clashed with police and smashed public property in China’s eastern Zhejiang province after a dispute between tax authorities and a local shop owner snowballed into protests, a government-run news site said. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict1.jpg) A Christian activist holds a placard reading “No fraternity without respect of the other” as she prays during a demonstration, in Paris, Thursday Oct. 27, 2011, in front of the Theatre de la ville, where the Italian director Romeo Castellucci’s play “On the Concept of the Face, Regarding the Son of God” is being performed. Christian fundamentalists protest against the play featuring the face of Christ drizzled with fake excrement. (Thibault Camus)
A Christian activist holds a placard reading “No fraternity without respect of the other” as she prays during a demonstration, in Paris, Thursday Oct. 27, 2011, in front of the Theatre de la ville, where the Italian director Romeo Castellucci’s play “On the Concept of the Face, Regarding the Son of God” is being performed. Christian fundamentalists protest against the play featuring the face of Christ drizzled with fake excrement. (Thibault Camus)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict2.jpg) About 1300 hundred people attend a candlelight vigil for Scott Olsen on Thursday, Oct. 27, 2011, in Oakland, Calif. During an Occupy Oakland protest Tuesday night, a projectile apparently fired by police struck the Iraq veteran in the head leaving him in critical condition with a fractured skull. (Noah Berger)
About 1300 hundred people attend a candlelight vigil for Scott Olsen on Thursday, Oct. 27, 2011, in Oakland, Calif. During an Occupy Oakland protest Tuesday night, a projectile apparently fired by police struck the Iraq veteran in the head leaving him in critical condition with a fractured skull. (Noah Berger)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict4.jpg) Participants of the Occupy Wall Street movement, right, talk to pedestrians trying to walk past their tent at the encampment at Zuccotti Park, Thursday, Oct. 27, 2011 in New York. The protests, which started on Sept. 17 with a few dozen demonstrators near Wall Street, as grown into a nationwide and international movement. (Mary Altaffer)
Participants of the Occupy Wall Street movement, right, talk to pedestrians trying to walk past their tent at the encampment at Zuccotti Park, Thursday, Oct. 27, 2011 in New York. The protests, which started on Sept. 17 with a few dozen demonstrators near Wall Street, as grown into a nationwide and international movement. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict7.jpg) Demonstrators supporting the Occupy Wall Street movement march in the hallways during a rally inside the state Capitol in Albany, N.Y., Thursday, Oct. 27, 2011. Several speakers criticized Gov. Andrew Cuomo for blocking a bill that would tax New Yorkers making over $1 million a year at a higher rate while cutting aid to schools, colleges and the poor. Cuomo, who was in New York City, had no immediate comment Thursday. (Hans Pennink)
Demonstrators supporting the Occupy Wall Street movement march in the hallways during a rally inside the state Capitol in Albany, N.Y., Thursday, Oct. 27, 2011. Several speakers criticized Gov. Andrew Cuomo for blocking a bill that would tax New Yorkers making over $1 million a year at a higher rate while cutting aid to schools, colleges and the poor. Cuomo, who was in New York City, had no immediate comment Thursday. (Hans Pennink)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict8.jpg) Police officers look at the Occupy London Stock Exchange camp as they stand on the steps outside St Paul’s Cathedral in London, Thursday, Oct. 27, 2011. St. Paul’s Cathedral says it will reopen Friday, a week after is shut its doors because of an anti-capitalist protest camp outside. It will reopen to tourists on Saturday. Protesters have been camped outside the building since Oct. 15. Days later, cathedral officials shut the building to the public.
Police officers look at the Occupy London Stock Exchange camp as they stand on the steps outside St Paul’s Cathedral in London, Thursday, Oct. 27, 2011. St. Paul’s Cathedral says it will reopen Friday, a week after is shut its doors because of an anti-capitalist protest camp outside. It will reopen to tourists on Saturday. Protesters have been camped outside the building since Oct. 15. Days later, cathedral officials shut the building to the public.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict9.jpg) Demonstrators hold cutouts representing women during a protest in front of the National Assembly building during a protest to demand the return of the therapeutic abortion law, in Managua, Nicaragua, Wednesday Oct. 26, 2011. The therapeutic abortion law, which allows the termination of a pregnancy to save a mother’s life, was repealed by the legislature in 2006, handing down eight-year prison sentences to those who terminated risky pregnancies. (Esteban Felix)
Demonstrators hold cutouts representing women during a protest in front of the National Assembly building during a protest to demand the return of the therapeutic abortion law, in Managua, Nicaragua, Wednesday Oct. 26, 2011. The therapeutic abortion law, which allows the termination of a pregnancy to save a mother’s life, was repealed by the legislature in 2006, handing down eight-year prison sentences to those who terminated risky pregnancies. (Esteban Felix)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict3.jpg) In this Wednesday, Sept. 28, 2011 file photo demonstrators burn copies of emergency tax notices during a protest by the Communist-backed labor union. Groups of lawyers, trade unions and campaigners have tried to derail government efforts to collect new taxes, or to suspend tens of thousands of civil servants on partial pay. State buildings have been occupied, municipalities have stalled in delivering emergency notices ordering strikers back to work.
In this Wednesday, Sept. 28, 2011 file photo demonstrators burn copies of emergency tax notices during a protest by the Communist-backed labor union. Groups of lawyers, trade unions and campaigners have tried to derail government efforts to collect new taxes, or to suspend tens of thousands of civil servants on partial pay. State buildings have been occupied, municipalities have stalled in delivering emergency notices ordering strikers back to work.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest3/pict21.jpg) Two activists of the Femen Movement from Ukraine protest during a press conference ‘Euro 2012: Corruption and Prostitution’ organised in the Culture Center Nowy Wspanialy Swiat, in Warsaw, Poland, on September 15, 2011. The members of the Femen Movement were presented during the conference as Blyadek and Blyadko – alternative mascots of Euro 2012, who like sex, football and alcohol. FEMEN activists want to demostrate the ‘dark side’ of Ukraine’s preparation for Euro 2012 and expose the corrupt schemes associated with the football championships. Getty
Two activists of the Femen Movement from Ukraine protest during a press conference ‘Euro 2012: Corruption and Prostitution’ organised in the Culture Center Nowy Wspanialy Swiat, in Warsaw, Poland, on September 15, 2011. The members of the Femen Movement were presented during the conference as Blyadek and Blyadko – alternative mascots of Euro 2012, who like sex, football and alcohol. FEMEN activists want to demostrate the ‘dark side’ of Ukraine’s preparation for Euro 2012 and expose the corrupt schemes associated with the football championships. Getty



![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict2.jpg) Occupy Wall Street protesters help a man injured after police used tear gas to disperse a large crowd of protesters at 14th Street and Broadway in Oakland, Calif., Tuesday, Oct. 25, 2011. (Darryl Bush)
Occupy Wall Street protesters help a man injured after police used tear gas to disperse a large crowd of protesters at 14th Street and Broadway in Oakland, Calif., Tuesday, Oct. 25, 2011. (Darryl Bush)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict0.jpg) Occupy Wall Street protesters huddle together after police use tear gas to disperse a large crowd that gathered at 14th Street and Broadway in Oakland, Calif., Tuesday, October 25, 2011. Many demonstrators were arrested. (Darryl Bush)
Occupy Wall Street protesters huddle together after police use tear gas to disperse a large crowd that gathered at 14th Street and Broadway in Oakland, Calif., Tuesday, October 25, 2011. Many demonstrators were arrested. (Darryl Bush)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict1.jpg) An Occupy Wall Street protester stands with a banner after police use tear gas to disperse a large crowd that gathered at 14th Street and Broadway in Oakland, Calif., Tuesday, October 25, 2011. Scores of demonstrators were arrested. (Darryl Bush)
An Occupy Wall Street protester stands with a banner after police use tear gas to disperse a large crowd that gathered at 14th Street and Broadway in Oakland, Calif., Tuesday, October 25, 2011. Scores of demonstrators were arrested. (Darryl Bush)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict7.jpg) Oakland police fire tear gas as they prepare to move in to Frank Ogawa Plaza to disperse Occupy Oakland protesters on Tuesday. Oct. 25, 2011 in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)
Oakland police fire tear gas as they prepare to move in to Frank Ogawa Plaza to disperse Occupy Oakland protesters on Tuesday. Oct. 25, 2011 in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict9.jpg) Police prepare to enter Occupy Oakland’s City Hall encampment on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)
Police prepare to enter Occupy Oakland’s City Hall encampment on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict10.jpg) Oakland Occupy protestors form a line opposing the police at the Frank Ogawa Plaza on Tuesday. Oct. 25, 2011 in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)
Oakland Occupy protestors form a line opposing the police at the Frank Ogawa Plaza on Tuesday. Oct. 25, 2011 in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict6.jpg) Oakland police search tents in Frank Ogawa Plaza as they disperse Occupy Oakland protesters on Tuesday. Oct. 25, 2011 in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)
Oakland police search tents in Frank Ogawa Plaza as they disperse Occupy Oakland protesters on Tuesday. Oct. 25, 2011 in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict3.jpg) Oakland police search tents in Frank Ogawa Plaza as they disperse Occupy Oakland protesters on Tuesday, Oct. 25, 2011 in Oakland, Calif. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)
Oakland police search tents in Frank Ogawa Plaza as they disperse Occupy Oakland protesters on Tuesday, Oct. 25, 2011 in Oakland, Calif. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict12.jpg) An Occupy Oakland protester waits in his tent as police clear the group’s Snow Park encampment on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)
An Occupy Oakland protester waits in his tent as police clear the group’s Snow Park encampment on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict5.jpg) Unidentified protesters link arms as police advance on their City Hall encampment on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)
Unidentified protesters link arms as police advance on their City Hall encampment on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict4.jpg) An Occupy Oakland camper carries belonging in his teeth as he’s arrested from the group’s city hall encampment on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)
An Occupy Oakland camper carries belonging in his teeth as he’s arrested from the group’s city hall encampment on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict8.jpg) The Oakland Occupy encampment at Frank Ogawa Plaza after Oakland Police disbanded the tent community leaving debris strewn throughout the plaza on Tuesday. Oct. 25, 2011 in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Noah Berger)
The Oakland Occupy encampment at Frank Ogawa Plaza after Oakland Police disbanded the tent community leaving debris strewn throughout the plaza on Tuesday. Oct. 25, 2011 in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Noah Berger)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict14.jpg) Tents and debris are seen on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Noah Berger)
Tents and debris are seen on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Noah Berger)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict13.jpg) An Oakland police officer in riot gear stands guard over Frank H. Ogawa plaza Tuesday, Oct. 25, 2011, in Oakland, Calif. Occupy Oakland protestors were evicted from the plaza early this morning. (AP Photo/Ben Margot)
An Oakland police officer in riot gear stands guard over Frank H. Ogawa plaza Tuesday, Oct. 25, 2011, in Oakland, Calif. Occupy Oakland protestors were evicted from the plaza early this morning. (AP Photo/Ben Margot)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict11.jpg)









 Long before it was acknowledged to be a significant criminal and national security threat, the FBI established a forward-looking organization to proactively address the issue of cyber crime.
Long before it was acknowledged to be a significant criminal and national security threat, the FBI established a forward-looking organization to proactively address the issue of cyber crime.


































 In den Akten der Staatssicherheit findet sich zum Fall Günter Litfin auch ein undatiertes Foto: Gedenkstein für Günter Litfin am Friedrich-List-Ufer, aufgestellt am 24.8.1962. Heute befindet sich der Gedenkstein an der Sandkrugbrücke in der Berliner Invalidenstraße. Quelle: BStU, MfS, HA IX, Fo 1673, Bild 88
In den Akten der Staatssicherheit findet sich zum Fall Günter Litfin auch ein undatiertes Foto: Gedenkstein für Günter Litfin am Friedrich-List-Ufer, aufgestellt am 24.8.1962. Heute befindet sich der Gedenkstein an der Sandkrugbrücke in der Berliner Invalidenstraße. Quelle: BStU, MfS, HA IX, Fo 1673, Bild 88






 Born of an immigrant family in Brooklyn, New York in 1899, Al Capone quit school after the sixth grade and associated with a notorious street gang, becoming accepted as a member. Johnny Torrio was the street gang leader and among the other members was Lucky Luciano, who would later attain his own notoriety.
Born of an immigrant family in Brooklyn, New York in 1899, Al Capone quit school after the sixth grade and associated with a notorious street gang, becoming accepted as a member. Johnny Torrio was the street gang leader and among the other members was Lucky Luciano, who would later attain his own notoriety.






![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict143.jpg) Demonstrators chat while warming their hands on a makeshift fire in the park near the European Central Bank in Frankfurt, central Germany, Monday, Oct. 17, 2011. Thousands of people demonstrated against corporate greed in cities across Europe on Saturday, along with much smaller protests in cities across the U.S. Banners on tent read right: ‘WTF where is freedom?’ and at left : ‘A good life instead of profit’. (Thomas Lohnes)
Demonstrators chat while warming their hands on a makeshift fire in the park near the European Central Bank in Frankfurt, central Germany, Monday, Oct. 17, 2011. Thousands of people demonstrated against corporate greed in cities across Europe on Saturday, along with much smaller protests in cities across the U.S. Banners on tent read right: ‘WTF where is freedom?’ and at left : ‘A good life instead of profit’. (Thomas Lohnes)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict144.jpg) A protester stands outside the Toronto Stock Exchange in the city’s financial district on Monday Oct. 17, 2011 as the Occupy Bay Street protest continues into it’s third day. (Chris Young)
A protester stands outside the Toronto Stock Exchange in the city’s financial district on Monday Oct. 17, 2011 as the Occupy Bay Street protest continues into it’s third day. (Chris Young)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict145.jpg) A participant who asked not to identified and a dog begin the day along with others at the Occupy Wall Street protests at Zuccotti Park in New York Monday, Oct. 17, 2011 as the protest enters it’s 30th day. (Craig Ruttle)
A participant who asked not to identified and a dog begin the day along with others at the Occupy Wall Street protests at Zuccotti Park in New York Monday, Oct. 17, 2011 as the protest enters it’s 30th day. (Craig Ruttle)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict140.jpg) [Published October 17, 2011.] In this Oct. 14, 2011 photo, demonstrators affiliated with the Occupy Wall Street protests stand in line to be served lunch at Zuccotti Park in New York. The outcry against the nation’s financial institutions that has swept the country in recent weeks has crossed many boundaries, including class, gender and age. But a stubborn hurdle in many cities has been a lack of racial inclusion, something noted by organizers and participants alike. (Mary Altaffer)
[Published October 17, 2011.] In this Oct. 14, 2011 photo, demonstrators affiliated with the Occupy Wall Street protests stand in line to be served lunch at Zuccotti Park in New York. The outcry against the nation’s financial institutions that has swept the country in recent weeks has crossed many boundaries, including class, gender and age. But a stubborn hurdle in many cities has been a lack of racial inclusion, something noted by organizers and participants alike. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict141.jpg) [Published October 17, 2011.] In this Oct. 14, 2011 photo, Nicole Carty, 23, from Atlanta, confers with fellow organizing colleagues as she prepares to conduct a general assembly meeting for participants of Zuccotti Park’s Occupy Wall Street encampment, in New York. She is considered a core facilitator who organizes activities at the encampment. The outcry against the nation’s financial institutions that has swept the country in recent weeks has crossed many boundaries, including class, gender and age. But a stubborn hurdle But a stubborn hurdle in many cities has been a lack of racial inclusion, something noted by organizers and participants alike.
[Published October 17, 2011.] In this Oct. 14, 2011 photo, Nicole Carty, 23, from Atlanta, confers with fellow organizing colleagues as she prepares to conduct a general assembly meeting for participants of Zuccotti Park’s Occupy Wall Street encampment, in New York. She is considered a core facilitator who organizes activities at the encampment. The outcry against the nation’s financial institutions that has swept the country in recent weeks has crossed many boundaries, including class, gender and age. But a stubborn hurdle But a stubborn hurdle in many cities has been a lack of racial inclusion, something noted by organizers and participants alike.![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict142.jpg) [Published October 17, 2011.] In this Oct. 15, 2011 photo, a woman participates in an Occupy Atlanta protest at the state Capitol, in Atlanta. The outcry against the nation’s financial institutions that has swept the country in recent weeks has crossed many boundaries, including class, gender and age. But a stubborn hurdle in many cities has been a lack of racial inclusion, something noted by organizers and participants alike. (Erik S. Lesser)
[Published October 17, 2011.] In this Oct. 15, 2011 photo, a woman participates in an Occupy Atlanta protest at the state Capitol, in Atlanta. The outcry against the nation’s financial institutions that has swept the country in recent weeks has crossed many boundaries, including class, gender and age. But a stubborn hurdle in many cities has been a lack of racial inclusion, something noted by organizers and participants alike. (Erik S. Lesser)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict139.jpg) Two security guards stand at the entrance to the NYSE Euronext stock exchange in Amsterdam, Netherlands, Monday Oct. 17, 2011, plastered with slogans in support of the Occupy Wall Street movement. Hundreds of thousands demonstrated against corporate greed in cities across Europe on Saturday, along with much smaller protests in cities across the U.S. (Peter Dejong)
Two security guards stand at the entrance to the NYSE Euronext stock exchange in Amsterdam, Netherlands, Monday Oct. 17, 2011, plastered with slogans in support of the Occupy Wall Street movement. Hundreds of thousands demonstrated against corporate greed in cities across Europe on Saturday, along with much smaller protests in cities across the U.S. (Peter Dejong)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict132.jpg) A protest banner put up by protesters from the Occupy London Stock Exchange group hangs besides tents pitched outside St Paul’s Cathedral before sunrise, as they continue their demonstration that started there on Saturday near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)
A protest banner put up by protesters from the Occupy London Stock Exchange group hangs besides tents pitched outside St Paul’s Cathedral before sunrise, as they continue their demonstration that started there on Saturday near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict134.jpg) A protester from the Occupy London Stock Exchange group puts up a notice on an information point on the side of St Paul’s Cathedral as they continue their demonstration that started on Saturday near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)
A protester from the Occupy London Stock Exchange group puts up a notice on an information point on the side of St Paul’s Cathedral as they continue their demonstration that started on Saturday near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict135.jpg) A masked protester from the Occupy London Stock Exchange group offers passing business people ‘Free Hugs’ as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)
A masked protester from the Occupy London Stock Exchange group offers passing business people ‘Free Hugs’ as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict133.jpg) A protester from the Occupy London Stock Exchange group puts the finishing touches to a placard stating “London Hug Exchange”, as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)
A protester from the Occupy London Stock Exchange group puts the finishing touches to a placard stating “London Hug Exchange”, as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict129.jpg) Police officers chat to protesters beside tents put up by supporters of the Occupy London Stock Exchange group as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)
Police officers chat to protesters beside tents put up by supporters of the Occupy London Stock Exchange group as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict130.jpg) Protesters begin to rise from sleep before sunrise beside tents put up by supporters of the Occupy London Stock Exchange group, as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)
Protesters begin to rise from sleep before sunrise beside tents put up by supporters of the Occupy London Stock Exchange group, as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict128.jpg) Business people walk past tents put up by protesters from the Occupy London Stock Exchange group as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)
Business people walk past tents put up by protesters from the Occupy London Stock Exchange group as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict131.jpg) A businessman walks past tents put up by protesters from the Occupy London Stock Exchange group as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham) [Note “Fire Access Point” and safety corridors, a sign of capable oversight.]
A businessman walks past tents put up by protesters from the Occupy London Stock Exchange group as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham) [Note “Fire Access Point” and safety corridors, a sign of capable oversight.]![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict136.jpg) In this photo taken Saturday, Oct. 15, 2011, protesters take part in a march and rally at Michigan and Congress in Chicago for the Global Day of Occupation. About 2,000 people participated Saturday in an Occupy Chicago demonstration, and about 500 pitched tents in Congress Plaza that evening. Chicago police say the protesters were told to remove their tents and leave the park when it closed at 11 p.m. When they didn’t, police began cutting down the tents and making arrests. (Chicago Sun Times)
In this photo taken Saturday, Oct. 15, 2011, protesters take part in a march and rally at Michigan and Congress in Chicago for the Global Day of Occupation. About 2,000 people participated Saturday in an Occupy Chicago demonstration, and about 500 pitched tents in Congress Plaza that evening. Chicago police say the protesters were told to remove their tents and leave the park when it closed at 11 p.m. When they didn’t, police began cutting down the tents and making arrests. (Chicago Sun Times)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict137.jpg) Hip Hop Mogul Russell Simmons, right, listens to a protester at the camp for the Occupy Wall Street demonstration in New York, Sunday, Oct. 16, 2011. (David Karp) [The cardboard, twine and rain-sheet shelter deftly by-passes Brookfield Properties’ forbidden tents and tarps.]
Hip Hop Mogul Russell Simmons, right, listens to a protester at the camp for the Occupy Wall Street demonstration in New York, Sunday, Oct. 16, 2011. (David Karp) [The cardboard, twine and rain-sheet shelter deftly by-passes Brookfield Properties’ forbidden tents and tarps.]![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict138.jpg) A group of activists hold a strategy meeting in a storage space for supplies supporting the camp of Occupy Wall Street protesters, Sunday, Oct. 16, 2011, in New York. The goods are housed in an unused space donated by the United Federation of Teachers. (David Karp) [From a base in Liberty Park there are thousands of spaces available for sharing openly and not so openly in New York City and worldwide cities as “Wall Street” is widely dispersed openly and secretly.]
A group of activists hold a strategy meeting in a storage space for supplies supporting the camp of Occupy Wall Street protesters, Sunday, Oct. 16, 2011, in New York. The goods are housed in an unused space donated by the United Federation of Teachers. (David Karp) [From a base in Liberty Park there are thousands of spaces available for sharing openly and not so openly in New York City and worldwide cities as “Wall Street” is widely dispersed openly and secretly.]













 A latent print removed from the victim’s car was determined to be a match to the suspect’s
A latent print removed from the victim’s car was determined to be a match to the suspect’s![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict93.jpg) Protesters hurl objects at police in Rome, Saturday, Oct. 15, 2011. Protesters in Rome smashed shop windows and torched cars as violence broke out during a demonstration in the Italian capital, part of worldwide protests against corporate greed and austerity measures. The “Occupy Wall Street” protests, that began in Canada and spread to cities across the U.S., moved Saturday to Asia and Europe, linking up with anti-austerity demonstrations that have raged across the debt-ridden continent for months.
Protesters hurl objects at police in Rome, Saturday, Oct. 15, 2011. Protesters in Rome smashed shop windows and torched cars as violence broke out during a demonstration in the Italian capital, part of worldwide protests against corporate greed and austerity measures. The “Occupy Wall Street” protests, that began in Canada and spread to cities across the U.S., moved Saturday to Asia and Europe, linking up with anti-austerity demonstrations that have raged across the debt-ridden continent for months.![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict94.jpg) Two protesters spray graffiti at a bank, during a march in Brussels, Saturday, Oct. 15, 2011. The protest in the Belgian capital was part of Occupy Wall Street demonstrations against capitalism and austerity measures that went global Saturday, leading to dozens of marches and protests worldwide. (Yves Logghe)
Two protesters spray graffiti at a bank, during a march in Brussels, Saturday, Oct. 15, 2011. The protest in the Belgian capital was part of Occupy Wall Street demonstrations against capitalism and austerity measures that went global Saturday, leading to dozens of marches and protests worldwide. (Yves Logghe)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict99.jpg) A protestor holds a placard during an anti-capitalist demonstration, in Paris, Saturday, Oct. 15, 2011. Protesters in cities across Europe took part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. The placard reads: “Financial market dictatorship, enough”(Thibault Camus)
A protestor holds a placard during an anti-capitalist demonstration, in Paris, Saturday, Oct. 15, 2011. Protesters in cities across Europe took part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. The placard reads: “Financial market dictatorship, enough”(Thibault Camus)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict95.jpg) A man wears an anti-establishment mask during the “Occupy Bucharest” protest in Bucharest, Romania, Saturday, Oct. 15, 2011. The protest, meant as a part of worldwide protests “Occupy Wall Street” against corporate greed and austerity measures, was joined by few people who at times fought among themselves, trying to clarify their vague requests, aimed at linking up with anti-austerity demonstrations that have raged across the debt-ridden continent for months.(Vadim Ghirda)
A man wears an anti-establishment mask during the “Occupy Bucharest” protest in Bucharest, Romania, Saturday, Oct. 15, 2011. The protest, meant as a part of worldwide protests “Occupy Wall Street” against corporate greed and austerity measures, was joined by few people who at times fought among themselves, trying to clarify their vague requests, aimed at linking up with anti-austerity demonstrations that have raged across the debt-ridden continent for months.(Vadim Ghirda)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict96.jpg) Julian Assange, center, takes part in the Occupy London Stock Exchange demonstration in London Saturday Oct, 15, 2011. Protesters in cities across Europe take part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Elizabeth Dalziel)
Julian Assange, center, takes part in the Occupy London Stock Exchange demonstration in London Saturday Oct, 15, 2011. Protesters in cities across Europe take part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Elizabeth Dalziel)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict97.jpg) Frederic Carmel sits next to his tent in Montreal’s financial district on Saturday, Oct. 15, 2011. The demonstration is one of many being held across the country recently in support of the ongoing Occupy Wall Street demonstration in New York. (Graham Hughes)
Frederic Carmel sits next to his tent in Montreal’s financial district on Saturday, Oct. 15, 2011. The demonstration is one of many being held across the country recently in support of the ongoing Occupy Wall Street demonstration in New York. (Graham Hughes)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict98.jpg) Protestors gather in Toronto’s financial district for the Occupy Bay Street demonstration on Saturday, Oct. 15, 2011 in Toronto. The demonstration is one of many being held across the country recently in support of the ongoing Occupy Wall Street demonstration in New York. (Chris Young)
Protestors gather in Toronto’s financial district for the Occupy Bay Street demonstration on Saturday, Oct. 15, 2011 in Toronto. The demonstration is one of many being held across the country recently in support of the ongoing Occupy Wall Street demonstration in New York. (Chris Young)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict101.jpg) Diane Kuhn, of West Columbia, S.C. holds a protest sign calling for the prosecution of financial criminals during the Occupy Columbia demonstration at the South Carolina Statehouse in Columbia, S.C., Saturday, Oct. 15, 2011. (Brett Flashnick)
Diane Kuhn, of West Columbia, S.C. holds a protest sign calling for the prosecution of financial criminals during the Occupy Columbia demonstration at the South Carolina Statehouse in Columbia, S.C., Saturday, Oct. 15, 2011. (Brett Flashnick)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict100.jpg) Demonstrators hold banners during the Jobs at Justice rally at Washington Monument in Washington on Saturday, Oct. 15, 2011. (Jose Luis Magana)
Demonstrators hold banners during the Jobs at Justice rally at Washington Monument in Washington on Saturday, Oct. 15, 2011. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict82.jpg) Protestors march through the streets of Berlin during a demonstration to support the ‘ Occupy Wall Street’ -movement Saturday Oct. 15, 2011. Protestors gathered at many major European cities Saturday to join in demonstrations against corruption, capitalism and austerity measures. (Maja Hitij)
Protestors march through the streets of Berlin during a demonstration to support the ‘ Occupy Wall Street’ -movement Saturday Oct. 15, 2011. Protestors gathered at many major European cities Saturday to join in demonstrations against corruption, capitalism and austerity measures. (Maja Hitij)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict91.jpg) Protesters gather in front of the Reserve Bank of Australia in central Sydney, Australia, Saturday, Oct. 15, 2011. The organizer of the Occupy Wall Street announced on their website that protesters will demonstrate in concert over 951 cities in 82 countries. (Rick Rycroft)
Protesters gather in front of the Reserve Bank of Australia in central Sydney, Australia, Saturday, Oct. 15, 2011. The organizer of the Occupy Wall Street announced on their website that protesters will demonstrate in concert over 951 cities in 82 countries. (Rick Rycroft)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict81.jpg) Bosnian people carrying banners with the text “For a class war against dictatorship of capitalism”, top, and “What did bank do? The bank bankrupted!”, bottom banner, during a protest march, in the Bosnian capital of Sarajevo, Saturday, Oct. 15, 2011. Hundreds marched down the main streets of Bosnian cities carrying banners that call for the end of alleged worldwide “Capitalistic Dictatorship”. (Amel Emric)
Bosnian people carrying banners with the text “For a class war against dictatorship of capitalism”, top, and “What did bank do? The bank bankrupted!”, bottom banner, during a protest march, in the Bosnian capital of Sarajevo, Saturday, Oct. 15, 2011. Hundreds marched down the main streets of Bosnian cities carrying banners that call for the end of alleged worldwide “Capitalistic Dictatorship”. (Amel Emric)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict92.jpg) Protesters gather at the Pennsylvania Capitol Saturday, Oct 15, 2011 in Harrisburg, Pa. The demonstration is one of many being held across the country recently in support of the ongoing Occupy Wall Street demonstration in New York. (Bradley C Bower)
Protesters gather at the Pennsylvania Capitol Saturday, Oct 15, 2011 in Harrisburg, Pa. The demonstration is one of many being held across the country recently in support of the ongoing Occupy Wall Street demonstration in New York. (Bradley C Bower)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict87.jpg) Participants march through Tokyo’s Kasumigaseki administrative district during “Occupy Tokyo” protest Saturday, Oct. 15, 2011. The demonstration was held in support of the Occupy Wall Street protest against corporate power. (Itsuo Inouye)
Participants march through Tokyo’s Kasumigaseki administrative district during “Occupy Tokyo” protest Saturday, Oct. 15, 2011. The demonstration was held in support of the Occupy Wall Street protest against corporate power. (Itsuo Inouye)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict85.jpg) Children watch as protestors prepare placards outside the NYSE Euronext stock exchange in Amsterdam, Netherlands, Saturday Oct. 15, 2011, during a demonstration in support of the Occupy Wall Street movement. Demonstrators in hundreds of cities all over the world protested against corporate power and the banking system. (Peter Dejong)
Children watch as protestors prepare placards outside the NYSE Euronext stock exchange in Amsterdam, Netherlands, Saturday Oct. 15, 2011, during a demonstration in support of the Occupy Wall Street movement. Demonstrators in hundreds of cities all over the world protested against corporate power and the banking system. (Peter Dejong)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict89.jpg) Protesters shout slogans as they march towards the U.S. embassy in solidarity action for the U.S. protest dubbed “Occupy Wall Street” Saturday, Oct. 15, 2011 in Manila, Philippines. (Pat Roque)
Protesters shout slogans as they march towards the U.S. embassy in solidarity action for the U.S. protest dubbed “Occupy Wall Street” Saturday, Oct. 15, 2011 in Manila, Philippines. (Pat Roque)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict86.jpg) South Korean protesters stage an “Occupy Seoul” rally in Seoul, South Korea, Saturday, Oct. 15, 2011. The demonstration was held in support of the “Occupy Wall Street” protest against corporate power. The Korean letters read: “Tax the Rich 1%, Welfare for the 99%.” (Ahn Young-joon)
South Korean protesters stage an “Occupy Seoul” rally in Seoul, South Korea, Saturday, Oct. 15, 2011. The demonstration was held in support of the “Occupy Wall Street” protest against corporate power. The Korean letters read: “Tax the Rich 1%, Welfare for the 99%.” (Ahn Young-joon)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict84.jpg) Protesters take part in the “Occupy central” protest in Stockholm, Saturday, Oct. 15, 2011, as protesters worldwide demonstrated against bankers and politicians they accuse of ruining global economies through greed. (Maja Suslin)
Protesters take part in the “Occupy central” protest in Stockholm, Saturday, Oct. 15, 2011, as protesters worldwide demonstrated against bankers and politicians they accuse of ruining global economies through greed. (Maja Suslin)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict83.jpg) People demonstrate on the Place des Nations in front of the European headquarters of the United Nations in Geneva, Switzerland, Saturday Oct. 15, 2011. Protestors gathered at many major European cities Saturday to join in demonstrations against corporate greed and inequality. (Martial Trezzini)
People demonstrate on the Place des Nations in front of the European headquarters of the United Nations in Geneva, Switzerland, Saturday Oct. 15, 2011. Protestors gathered at many major European cities Saturday to join in demonstrations against corporate greed and inequality. (Martial Trezzini)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict90.jpg) Young people demonstrate in the financial district of Zurich, Switzerland, Saturday Oct. 15, 2011. The organizer of the Occupy Wall Street movement announced on their website that protesters will demonstrate in over 951 cities in 82 countries. (Ennio Leanza)
Young people demonstrate in the financial district of Zurich, Switzerland, Saturday Oct. 15, 2011. The organizer of the Occupy Wall Street movement announced on their website that protesters will demonstrate in over 951 cities in 82 countries. (Ennio Leanza)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict88.jpg) Activists hold magazines titled “Socialist” during a protest named “Occupy Taipei” organized by Taiwanese net friends in front of the Taipei 101 building in Taipei, Taiwan, Saturday, Oct. 15, 2011. The rally was a part of Saturday’s worldwide activities held in support of the Occupy Wall Street protest against corporate power. (Chiang Ying-ying)
Activists hold magazines titled “Socialist” during a protest named “Occupy Taipei” organized by Taiwanese net friends in front of the Taipei 101 building in Taipei, Taiwan, Saturday, Oct. 15, 2011. The rally was a part of Saturday’s worldwide activities held in support of the Occupy Wall Street protest against corporate power. (Chiang Ying-ying)













![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict9.jpg) Demonstrators who camped out at Freedom Plaza wake up for the third day of demonstrations Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)
Demonstrators who camped out at Freedom Plaza wake up for the third day of demonstrations Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict5.jpg) One demonstrator helps another flush her eyes with water after after police pepper-sprayed a group of protestors, who were trying to get into the National Air and Space Museum in Washington Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)
One demonstrator helps another flush her eyes with water after after police pepper-sprayed a group of protestors, who were trying to get into the National Air and Space Museum in Washington Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict8.jpg) Pepper-sprayed demonstrators sit and lie on the ground outside the entrance to the National Air and Space Museum in Washington after a group of protestors tryed to get into the museum Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)
Pepper-sprayed demonstrators sit and lie on the ground outside the entrance to the National Air and Space Museum in Washington after a group of protestors tryed to get into the museum Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict23.jpg) Demonstrators react at the entrance of the National Air and Space Museum in Washington after police pepper-sprayed a group of protestors trying to get into the museum Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)
Demonstrators react at the entrance of the National Air and Space Museum in Washington after police pepper-sprayed a group of protestors trying to get into the museum Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict7.jpg) A demonstrator lies on the ground at an entrance to the National Air and Space Museum in Washington after police pepper-sprayed a group of protestors trying to get into the museum Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)
A demonstrator lies on the ground at an entrance to the National Air and Space Museum in Washington after police pepper-sprayed a group of protestors trying to get into the museum Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict6.jpg) Demonstrators march through the streets of Washington Saturday, Oct. 8, 2011, as part of the Occupy DC activities in the nation’s capital. (Jose Luis Magana)
Demonstrators march through the streets of Washington Saturday, Oct. 8, 2011, as part of the Occupy DC activities in the nation’s capital. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict11.jpg) Demonstrators protest at Freedom Plaza in Washington on Saturday, Oct. 8, 2011, on day three of demonstrations in Washington as part of Occupy DC activities. (Jose Luis Magana)
Demonstrators protest at Freedom Plaza in Washington on Saturday, Oct. 8, 2011, on day three of demonstrations in Washington as part of Occupy DC activities. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict19.jpg) Demonstrators carrying a variety of signs march through the streets of Washington Saturday, Oct. 8, 2011, as part of Occupy DC activities in the nation’s capital. (Jose Luis Magana)
Demonstrators carrying a variety of signs march through the streets of Washington Saturday, Oct. 8, 2011, as part of Occupy DC activities in the nation’s capital. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict24.jpg) Matthew Gember, of Chicago, makes a point as Occupy Boston demonstrators protest on the plaza in front of the Federal Reserve Bank in Boston, Saturday, Oct. 8, 2011. (Michael Dwyer)
Matthew Gember, of Chicago, makes a point as Occupy Boston demonstrators protest on the plaza in front of the Federal Reserve Bank in Boston, Saturday, Oct. 8, 2011. (Michael Dwyer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict25.jpg) Occupy Boston protesters demonstrate on the plaza in front of the Federal Reserve Bank in Boston, Saturday, Oct. 8, 2011. (Michael Dwyer)
Occupy Boston protesters demonstrate on the plaza in front of the Federal Reserve Bank in Boston, Saturday, Oct. 8, 2011. (Michael Dwyer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict30.jpg) Courtney Haskell, lower left, of North Reading, Mass., demonstrates on the plaza in front of the Federal Reserve Bank in Boston as police reflected in a motorcycle mirror look on, Saturday, Oct. 8, 2011. (Michael Dwyer)
Courtney Haskell, lower left, of North Reading, Mass., demonstrates on the plaza in front of the Federal Reserve Bank in Boston as police reflected in a motorcycle mirror look on, Saturday, Oct. 8, 2011. (Michael Dwyer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict1.jpg) Marilyn Mullen stands in support for the ‘Occupy Wall Street’ movement during the Casper, Wyo. rally on Center Street Saturday, Oct. 8, 2011 Over 50 people held signs and American flags in support of the demonstration which is trying to achieve change in government tax law, asking the wealthy to pay an equal percentage of taxes that the working class pays. (Tim Kupsick)
Marilyn Mullen stands in support for the ‘Occupy Wall Street’ movement during the Casper, Wyo. rally on Center Street Saturday, Oct. 8, 2011 Over 50 people held signs and American flags in support of the demonstration which is trying to achieve change in government tax law, asking the wealthy to pay an equal percentage of taxes that the working class pays. (Tim Kupsick)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict13.jpg) With a statue of Abraham Lincoln at center right, protesters begin their march through downtown Cincinnati during the Occupy Cincinnati protest, Saturday, Oct. 8, 2011. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (David Kohl)
With a statue of Abraham Lincoln at center right, protesters begin their march through downtown Cincinnati during the Occupy Cincinnati protest, Saturday, Oct. 8, 2011. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (David Kohl)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict18.jpg) Protesters march through downtown Cincinnati for the Occupy Cincinnati protest on Saturday, Oct. 8, 2011. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (David Kohl)
Protesters march through downtown Cincinnati for the Occupy Cincinnati protest on Saturday, Oct. 8, 2011. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (David Kohl)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict0.jpg) Tamra Bell 52, back right, and her four children Stephanie Stayton, 28, left front, Robert 21, left back, and Courtney 23, attend the Occupy Indy protest in Indianapolis on Saturday, Oct. 8, 2011. Tamra’s husband has been unemployed for two years and suffers from health problems. His unemployment will soon run out and Bell is on the verge of losing the home. The small income her son Robert brings in has helped the family to stay in their home so far. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Michelle Pemberton)
Tamra Bell 52, back right, and her four children Stephanie Stayton, 28, left front, Robert 21, left back, and Courtney 23, attend the Occupy Indy protest in Indianapolis on Saturday, Oct. 8, 2011. Tamra’s husband has been unemployed for two years and suffers from health problems. His unemployment will soon run out and Bell is on the verge of losing the home. The small income her son Robert brings in has helped the family to stay in their home so far. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Michelle Pemberton)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict4.jpg) More than a thousand demonstrators gather in Veteran’s Plaza in Indianapolis on Saturday, Oct. 8, 2011 for Occupy Indy, a protest against everything from bank foreclosures and corporate influence in politics to the wars in Iraq and Afghanistan and unemployment. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Michelle Pemberton)
More than a thousand demonstrators gather in Veteran’s Plaza in Indianapolis on Saturday, Oct. 8, 2011 for Occupy Indy, a protest against everything from bank foreclosures and corporate influence in politics to the wars in Iraq and Afghanistan and unemployment. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Michelle Pemberton)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict16.jpg) A demonstrator holds a sign as more than a thousand gather in Veteran’s Plaza in Indianapolis on Saturday, Oct. 8, 2011 for Occupy Indy, a protest against everything from bank foreclosures and corporate influence in politics to the wars in Iraq and Afghanistan and unemployment. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Michelle Pemberton)
A demonstrator holds a sign as more than a thousand gather in Veteran’s Plaza in Indianapolis on Saturday, Oct. 8, 2011 for Occupy Indy, a protest against everything from bank foreclosures and corporate influence in politics to the wars in Iraq and Afghanistan and unemployment. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Michelle Pemberton)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict17.jpg) More than a thousand protesters march through Indianapolis on Saturday, Oct. 8, 2011 for Occupy Indy, a protest against everything from bank foreclosures and corporate influence in politics to the wars in Iraq and Afghanistan and unemployment. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Michelle Pemberton)
More than a thousand protesters march through Indianapolis on Saturday, Oct. 8, 2011 for Occupy Indy, a protest against everything from bank foreclosures and corporate influence in politics to the wars in Iraq and Afghanistan and unemployment. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Michelle Pemberton)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict3.jpg) Occupy Wall Street protesters gather in Washington Square Park, Saturday, Oct. 8, 2011 in New York. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Henny Ray Abrams)
Occupy Wall Street protesters gather in Washington Square Park, Saturday, Oct. 8, 2011 in New York. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Henny Ray Abrams)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict10.jpg) Demonstrators holding signs gather at the Occupy Wall Street rally in New York on Saturday, Oct. 8, 2011. (Caleb Jones)
Demonstrators holding signs gather at the Occupy Wall Street rally in New York on Saturday, Oct. 8, 2011. (Caleb Jones)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict12.jpg) Protesters with Occupy Wall Street march from Zuccotti Park to Washington Square Park in New York on Saturday, Oct. 8, 2011. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Henny Ray Abrams)
Protesters with Occupy Wall Street march from Zuccotti Park to Washington Square Park in New York on Saturday, Oct. 8, 2011. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Henny Ray Abrams)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict22.jpg) Hundreds of skateboarders heading down Broadway toward OWS from West 89th Street and Broadway, October 8, 2011. (Cryptome)
Hundreds of skateboarders heading down Broadway toward OWS from West 89th Street and Broadway, October 8, 2011. (Cryptome)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict15.jpg) In this Friday, Oct. 7, 2011 photo, Cherie Walters, 58, from Mount Clemens, Mich., poses for a photograph, in New York. Walters, who has participated in Occupy Wall Street protests, is wearing the shirt she wore to two of the protests. (Tina Fineberg)
In this Friday, Oct. 7, 2011 photo, Cherie Walters, 58, from Mount Clemens, Mich., poses for a photograph, in New York. Walters, who has participated in Occupy Wall Street protests, is wearing the shirt she wore to two of the protests. (Tina Fineberg)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict2.jpg) People hold signs and are reflected in a bus stop pane, as they walk in the street during their march from City Hall to the Independence National Historical Park Saturday, Oct. 8, 2011, in Philadelphia. Organizers of what is being called Occupy Philadelphia say the demonstration is meant to be a stand against corporate greed. (Alex Brandon)
People hold signs and are reflected in a bus stop pane, as they walk in the street during their march from City Hall to the Independence National Historical Park Saturday, Oct. 8, 2011, in Philadelphia. Organizers of what is being called Occupy Philadelphia say the demonstration is meant to be a stand against corporate greed. (Alex Brandon)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict14.jpg) People hold signs as they walk in the street during their march from City Hall to the Independence National Historical Park Saturday, Oct. 8, 2011 in Philadelphia. Organizers of what is being called Occupy Philadelphia say the demonstration is meant to be a stand against corporate greed. (Alex Brandon)
People hold signs as they walk in the street during their march from City Hall to the Independence National Historical Park Saturday, Oct. 8, 2011 in Philadelphia. Organizers of what is being called Occupy Philadelphia say the demonstration is meant to be a stand against corporate greed. (Alex Brandon)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-100811/pict27.jpg) Overview of reactor building of Unit 3 from western hilltop between Unit 2 and 3, Sep 29, 2011. (Tokyo Electric Power Co.)
Overview of reactor building of Unit 3 from western hilltop between Unit 2 and 3, Sep 29, 2011. (Tokyo Electric Power Co.)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-100811/pict29.jpg) Overview of reactor building of Unit 3 from a crane above Unit 3, Sep 24, 2011. (Tokyo Electric Power Co.)
Overview of reactor building of Unit 3 from a crane above Unit 3, Sep 24, 2011. (Tokyo Electric Power Co.)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-100811/pict30.jpg) Overview of a reactor building of Unit 4 from western hilltop between Unit 2 and 3. Sep 29, 2011. (Tokyo Electric Power Co.)
Overview of a reactor building of Unit 4 from western hilltop between Unit 2 and 3. Sep 29, 2011. (Tokyo Electric Power Co.)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-100811/pict28.jpg) Overview of reactor building of Unit 2 from western hilltop between Unit 2 and 3, Sep 29, 2011. (Tokyo Electric Power Co.)
Overview of reactor building of Unit 2 from western hilltop between Unit 2 and 3, Sep 29, 2011. (Tokyo Electric Power Co.)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-100811/pict26.jpg) Installation Work of Roof Panels for Reactor Building Covers at Unit 1 of Fukushima Daiichi Nuclear Power Plant, October 8, 2011. (Tokyo Electric Power Co.)
Installation Work of Roof Panels for Reactor Building Covers at Unit 1 of Fukushima Daiichi Nuclear Power Plant, October 8, 2011. (Tokyo Electric Power Co.)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-100811/pict31.jpg) Overview of reactor building of Unit 1 -From south direction of Main Anti-Earthquake Building, Oct 8, 2011. (Tokyo Electric Power Co.)
Overview of reactor building of Unit 1 -From south direction of Main Anti-Earthquake Building, Oct 8, 2011. (Tokyo Electric Power Co.)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-100811/pict32.jpg) Overview of reactor building of Unit 1 -From a crane above Unit 1, Sep 9, 2011. (Tokyo Electric Power Co.)
Overview of reactor building of Unit 1 -From a crane above Unit 1, Sep 9, 2011. (Tokyo Electric Power Co.)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-100811/pict33.jpg) Main control room of Unit 1 and 2, Sep 22, 2011. (Tokyo Electric Power Co.)
Main control room of Unit 1 and 2, Sep 22, 2011. (Tokyo Electric Power Co.)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-100811/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-100811/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-100811/pict34.jpg)

 National Medicare Fraud Takedowns
National Medicare Fraud Takedowns

 A
A
 The number of commercial mortgage loan delinquencies increased 79 percent in 2010, from 4.9 percent in December 2009 to 8.79 percent in December 2010.16 Nevada (28.2 percent) and Alabama (16 percent) have the highest delinquency rates in the United States.
The number of commercial mortgage loan delinquencies increased 79 percent in 2010, from 4.9 percent in December 2009 to 8.79 percent in December 2010.16 Nevada (28.2 percent) and Alabama (16 percent) have the highest delinquency rates in the United States.












 For the eighth year in a row, October has been designated National Cyber Security Awareness Month. The goal: to reinforce the importance of protecting the cyber networks that are so much a part of our daily lives. The theme of the observance, which is sponsored by the Department of Homeland Security, is “Our Shared Responsibility.” Over the course of the month we will be posting additional stories and information about cyber crimes and security.
For the eighth year in a row, October has been designated National Cyber Security Awareness Month. The goal: to reinforce the importance of protecting the cyber networks that are so much a part of our daily lives. The theme of the observance, which is sponsored by the Department of Homeland Security, is “Our Shared Responsibility.” Over the course of the month we will be posting additional stories and information about cyber crimes and security.















 US soldier Bradley Manning, left, who is accused of stealing the huge database of classified files released by the WikiLeaks website of Julian Assange, right. Photograph: Associated Press/AFP/Getty ImagesThe State Department and its Bureau of Diplomatic Security never took responsibility for their part in the loss of all those cables, never acknowledged their own mistakes or porous security measures. No one will ever be fired at State because of WikiLeaks – except, at some point, possibly me. Instead, State joined in the federal mugging of army Private Bradley Manning,
US soldier Bradley Manning, left, who is accused of stealing the huge database of classified files released by the WikiLeaks website of Julian Assange, right. Photograph: Associated Press/AFP/Getty ImagesThe State Department and its Bureau of Diplomatic Security never took responsibility for their part in the loss of all those cables, never acknowledged their own mistakes or porous security measures. No one will ever be fired at State because of WikiLeaks – except, at some point, possibly me. Instead, State joined in the federal mugging of army Private Bradley Manning, 


You must be logged in to post a comment.