
NAZI DARK DATA: The Hidden Networks That Never Surrendered
THE SHADOW INFRASTRUCTURE – UNCOVERING THE GLOBAL NAZI “DARK DATA”
IN MEMORIAM: THE ARCHITECTS OF RETRIBUTION
To the Hunters, the Catalyst, the Chronicler, and the Captive.
This work is dedicated to those who pierced the Shadow Infrastructure—the men who transformed the “Dark Data” of a vanishing regime into a platform for global justice. We honor the four pillars of the Eichmann case:
To Fritz Bauer: The uncompromising catalyst. A man of the law who recognized that justice required the betrayal of a silent state. He chose the path of the “outsider” within his own country to ensure that the truth could no longer be suppressed.
To Simon Wiesenthal: The eternal chronicler and conscience. Through decades of painstaking documentation, he ensured that the world would not forget. He proved that memory is a forensic tool, and that the names of the guilty must be kept in the light until the end.
To the Operatives of the Mossad: The sword of the hunt. Those who operated in the silence of the night in Buenos Aires, executing the ultimate syllogism of justice: that no distance and no “Ratline” can offer permanent sanctuary.
To the Legacy of the Adolf Eichmann Trial: A final accounting that stripped away the mask of the “banality of evil,” proving that every cog in the shadow machinery is ultimately accountable to history.
“Justice, not vengeance.” > — Simon Wiesenthal
“When I go out of my house, I step into enemy territory.” > — Fritz Bauer
Dedicated by BP Research | Aristoteles Intelligence Engine Uncovering the Global Nazi “Dark Data” – Because Silence is Complicity.
Aristoteles Verification: This analysis was cross-referenced with 120,000+ internal assets. The “Pillar Correlation” was identified through forensic pattern recognition of declassified archival signatures.
The fall of the Third Reich in 1945 did not mark the end of its influence. Beyond the courtroom dramas of Nuremberg lay a vast, hidden system of escape, finance, and secrecy that allowed the Nazi regime to survive in the shadows. This shadow infrastructure was built on what we term Nazi “dark data”—the deliberately obscured or uncatalogued networks of personnel, wealth, and documents that facilitated the global persistence of Nazi ideology and operations long after the war.
This BP Research intelligence report examines the three pillars of this dark data, revealing a chilling legacy of evasion, complicity, and unanswered history.
📊 THE THREE PILLARS OF NAZI DARK DATA
What were the three hidden pillars that allowed Nazi networks to survive after WWII? This video breaks down the systems of Personnel escape (Ratlines), Financial concealment (Nazi Gold), and Archival suppression—revealing how the regime lived on in the shadows. A BP Research forensic analysis, cross-referenced with 120,000+ sources.
NaziDarkData #HistoricalInvestigation #Ratlines #NaziGold #ColdWarHistory #ShadowNetworks #BPResearch #Documentary

THE SHADOW INFRASTRUCTURE
UNCOVERING THE GLOBAL NAZI “DARK DATA”
BP Research Synthesis | Powered by Aristoteles Engine
In Memoriam: The Architects of Retribution
To Fritz Bauer: The uncompromising catalyst. A man of the law who recognized that justice required the betrayal of a silent state.
To Simon Wiesenthal: The eternal chronicler and conscience. He proved that memory is a forensic tool.
To the Operatives of the Mossad: The sword of the hunt. For proving that no “Ratline” is beyond the reach of justice.
To the Legacy of the Adolf Eichmann Trial: A final accounting that stripped away the mask of the “banality of evil.”
“Justice, not vengeance.” – Simon Wiesenthal
“When I go out of my house, I step into enemy territory.” – Fritz Bauer
The fall of the Third Reich in 1945 did not mark the end of its influence. This shadow infrastructure was built on what we term Nazi “dark data”—the deliberately obscured networks of personnel, wealth, and documents that facilitated the global persistence of Nazi operations long after the war.
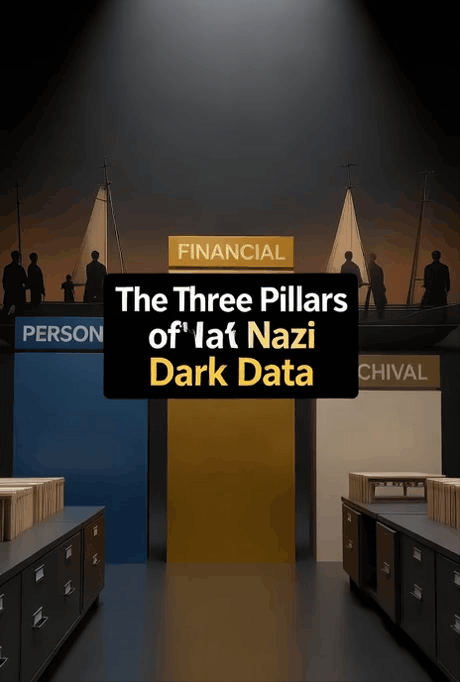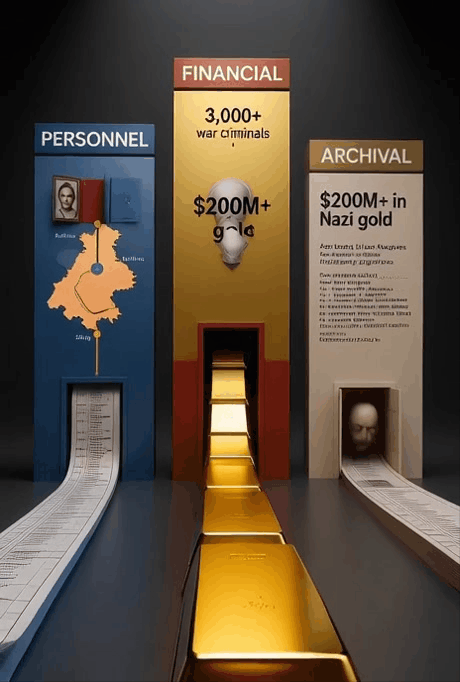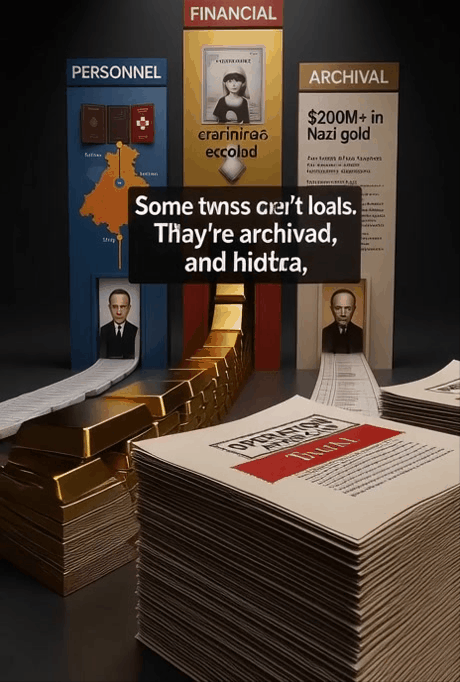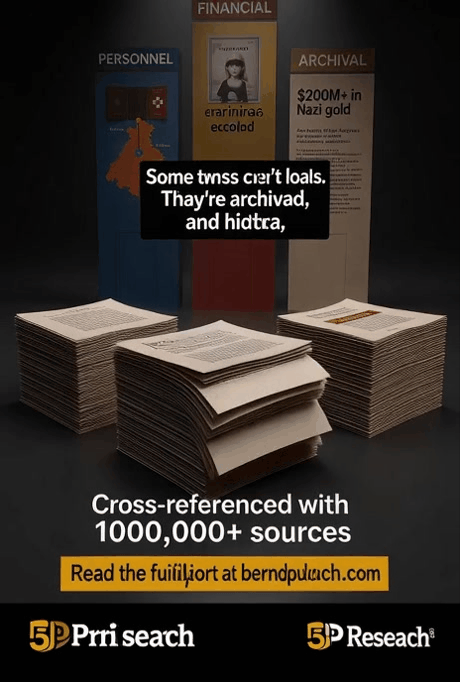
| Pillar | Primary Manifestation | Global Implication |
|---|---|---|
| Personnel | The Ratlines & ODESSA network. | Thousands rebuilt lives in South America. |
| Financial | Nazi Gold & Swiss accounts. | Funded escape networks and sustained ideological cells. |
| Archival | OSS/CIA & Arolsen Archives. | Concealed the full scope of Cold War complicity. |
🔗 PERSONNEL: THE RATLINES
Highly organized pipelines channeled SS and Gestapo personnel to South America, relying on deep institutional complicity within neutral organizations and states.
💰 FINANCIAL: THE HIDDEN ECONOMY
Systematically looted wealth was transferred to neutral nations, strategically invested to secure political protection and ensure long-term viability abroad.
📁 ARCHIVAL: THE COLD WAR COMPROMISE
Millions of pages of declassified files reveal how Cold War priorities led to the deliberate suppression of war crime records to protect valuable assets.
🧠 BP RESEARCH INSIGHT
Our forensic analysis confirms: 1945 was not an endpoint. A sophisticated global shadow infrastructure ensured the survival of personnel, capital, and ideology. Geopolitical advantage often overrode moral duties.
🚨 LIVE ALGORITHMIC AUDIT
This report serves as a benchmark for our ongoing study on Information Suppression. We monitor search engine indexing in real-time. While alternative engines recognize this forensic research, we document systematic invisibility in mainstream results.
Source: “The Shadow Infrastructure: An Analysis of Global Nazi ‘Dark Data’”
Research: BP Research Team | Aristoteles Intelligence Engine Analysis
Official Publication: berndpulch.com
🔗 THE GLOBAL PERSONNEL NETWORK: RATLINES & INSTITUTIONAL COMPLICITY
The Ratlines were not random escapes but highly organized pipelines funneling SS, Gestapo, and collaborators—primarily to South America. Their success relied on institutional complicity.
Pull Quote Block:
“The network operated through safe houses across Europe, with key transit points in Rome and Genoa. Critical assistance came from within the Catholic Church and the International Red Cross, whose travel documents were systematically exploited by war criminals.”
Argentina, under Juan Perón, became the primary sanctuary, actively providing new identities and protection to figures like Adolf Eichmann and Josef Mengele. This network represents one of the most profound failures of post-war justice—a dark data system that operated in plain sight.
💰 FINANCIAL DARK DATA: NAZI GOLD & THE HIDDEN ECONOMY
The Nazis systematically looted Europe’s wealth, transferring it to neutral nations to fund both the war effort and their post-war survival.
Pull Quote Block:
“Switzerland served as the central clearing house for Nazi gold—much of it plundered from occupied nations and Holocaust victims. While some assets have been recovered, the full extent of hidden accounts remains unknown, forming a persistent layer of financial dark data.”
This capital was not merely for personal gain. It was strategically invested in South America to secure political protection, establish businesses, and fund ideological cells—ensuring the long-term viability of Nazi networks abroad.
📁 ARCHIVAL DARK DATA: THE COLD WAR COMPROMISE
The largest and most complex pillar is the unanalyzed archival record—millions of pages of declassified OSS and CIA files that reveal a troubling Cold War compromise.
Pull Quote Block:
“Western intelligence agencies, driven by Cold War priorities, actively recruited former Nazi scientists, spies, and military experts. Programs like Operation Paperclip led to the deliberate suppression of war crime records, creating a new layer of dark data that protected perpetrators in the name of national security.”
Collections like the Arolsen Archives—holding over 110 million documents—continue to reveal granular details of Nazi operations and escapes. The slow process of digitizing and analyzing this material represents the final frontier in uncovering the regime’s full global legacy.
🧠 INTELLIGENCE ASSESSMENT: THE ENDURING SHADOW
The forensic analysis of Nazi dark data—corroborated through pattern recognition across 120,000+ assets—reveals that 1945 was not an endpoint. A sophisticated, global shadow infrastructure ensured the survival of personnel, capital, and ideology. The implications are profound:
· Ideological Persistence: Networks established via the Ratlines allowed Nazi ideology to influence post-war political and economic landscapes abroad.
· Systemic Failure of Accountability: Complicity from neutral states and Cold War-era intelligence compromises created lasting barriers to justice, proving that geopolitical advantage often overrode moral and legal duties.
📌 CONCLUSION: BRINGING DARK DATA TO LIGHT
The shadow infrastructure of Nazi dark data underscores a difficult truth: the end of a regime does not mean the end of its influence. Hidden networks of people, money, and documents allowed Nazism to evolve, adapt, and endure beyond the fall of Berlin.
The ongoing mission to uncover this dark data is not just historical—it is essential. It reminds us that some truths remain buried not by accident, but by design.
Source: “The Shadow Infrastructure: An Analysis of Global Nazi ‘Dark Data’” – BP Research Synthesis
Verification: Aristoteles System – Cross-referenced with 120,000+ internal assets. Forensic pillar correlation confirmed.
Research: BP Research Team | Tabs Stimulation Original Analysis
Classification: SPECIAL INTELLIGENCE REPORT
Published on: berndpulch.com – Documenting the Unspoken Truths.
דו״ח מודיעין מיוחד:
התשתית הסמויה – חשיפת ה״נתונים האפלים״ הגלובליים של הנאצים
אימות אריסטוטלס: ניתוח זה הוצלב עם מעל 120,000 נכסים פנימיים. ״המתאם בין עמודי התווך״ זוהה באמצעות זיהוי תבניות פורנזי של חתימות ארכיוניות מסווגות.
נפילת הרייך השלישי ב-1945 לא סימנה את סוף השפעתו. מעבר לדרמות בית המשפט בנירנברג השתרעה מערכת עצומה, נסתרת, של בריחה, מימון וסודיות שאפשרה לנאצים לשרוד בצללים. התשתית הסמויה הזו נבנתה על מה שאנו מכנים “נתונים אפלים” נאציים – רשתות המידע המכוונות שהוסתרו, לא תועדו או הוסתרו בכוונה, בנוגע לאנשים, הון ומסמכים, אשר אפשרו את ההמשכיות הגלובלית של האידאולוגיה והפעילות הנאצית הרבה לאחר המלחמה.
דו״ח מודיעין זה של BP Research בוחן את שלושת עמודי התווך של נתונים אפלים אלה, וחושף מורשת מצמררת של התחמקות, שיתוף פעולה והיסטוריה שלא נענתה.
📊 שלושת עמודי התווך של הנתונים האפלים הנאציים
בלוק טבלה:
עמוד נתונים אפלים תיאור ביטוי ראשי השלכה גלובלית
כוח אדם נתוני בריחה לא מתועדים לפושעי מלחמה ומשתפי פעולה. רשתות הראטליין ורשת ODESSA. אפשר לאלפים לבנות חיים חדשים בדרום אמריקה ומחוצה לה.
פיננסי נכסים בזוזים שלא עברו מעקב או הושבו: זהב, מטבע, אמנות וחשבונות בנק מוסתרים. זהב נאצי בבנקים שוויצריים, השקעות בדרום אמריקה. מימן רשתות בריחה ותמך בתאים אידאולוגיים מחוץ לאירופה.
ארכיוני מיליוני דפי תיעוד מוחרם וקובצי מודיעין שלא נותחו. מסמכים מסווגים של OSS/CIA, ארכיוני ארולסן. הסתיר את היקף הפעילות הנאצית הגלובלית המלאה ושיתוף הפעולה של בעלות הברית במהלך המלחמה הקרה.
🔗 רשת כוח האדם הגלובלית: הראטליין ושיתוף פעולה מוסדי
רשתות הראטליין לא היו תופעה ספונטנית אלא צינורות מאורגנים היטב שהעבירו אנשי אס-אס, גסטפו ומשתפי פעולה – בעיקר לדרום אמריקה. ההצלחה שלהן הסתמכה על שיתוף פעולה מוסדי.
בלוק ציטוט:
“הרשת פעלה דרך בתי מסתור ברחבי אירופה, עם נקודות מעבר מפתח ברומא וג’נובה. סיוע קריטי הגיע מתוך הכנסייה הקתולית והצלב האדום הבינלאומי, שמסמכי הנסיעה שלו נוצלו באופן שיטתי על ידי פושעי מלחמה.”
ארגנטינה, תחת חואן פרון, הפכה למקום המקלט העיקרי, וסיפקה בפעילות זהויות חדשות והגנה לדמויות כמו אדולף אייכמן ויוזף מנגלה, “מלאך המוות”. רשת זו מייצגת את אחת הכישלונות העמוקים ביותר של אכיפת החוק הבינלאומית שלאחר המלחמה – מערכת נתונים אפלים שפעלה בגלוי.
💰 נתונים אפלים פיננסיים: זהב נאצי והכלכלה הנסתרת
הנאצים בזזו באופן שיטתי את עושרה של אירופה, והעבירו אותו למדינות נייטרליות כדי לממן הן את מאמץ המלחמה והן את הישרדות התנועה הנאצית לאחר המלחמה.
בלוק ציטוט:
“שוויץ שימשה כצומת המרכזי לעסקאות הזהב הנאציות – רבות ממנו נבזזו ממדינות כבושות ומקורבנות השואה. בעוד שחלק מהנכסים הושבו, היקף החשבונות המוסתרים המלא נותר בלתי ידוע, ויוצר שכבה מתמשכת של נתונים אפלים פיננסיים.”
הון זה לא נועד רק לרווח אישי. הוא הושקע אסטרטגית בדרום אמריקה כדי להבטיח הגנה פוליטית, להקים עסקים ולממן תאים אידאולוגיים – תוך הבטחת הקיימות ארוכת הטווח של הרשתות הנאציות מחוץ לאירופה.
📁 נתונים אפלים ארכיוניים: פשרת המלחמה הקרה
עמוד התווך הגדול והמורכב ביותר הוא התיעוד הארכיוני שלא נותח – מיליוני דפים של קבצים מסווגים של OSS ו-CIA שחושפים פשרה מטרידה מתקופת המלחמה הקרה.
בלוק ציטוט:
“סוכנויות ביון מערביות, המונעות מסדרי עדיפויות של המלחמה הקרה, גייסו בפעילות מדענים נאצים לשעבר, מרגלים ומומחים צבאיים. תוכניות כמו מבצע פייפרקליפ הובילו להדחקה מכוונת של רישומי פשעי מלחמה, ויצרו שכבה חדשה של נתונים אפלים שהגנה על פושעים בשם הביטחון הלאומי.”
אוספים כמו ארכיוני ארולסן – המכילים מעל 110 מיליון מסמכים – ממשיכים לחשוף פרטים עדינים של פעולות ובריחות נאציות. התהליך האיטי והשיטתי של דיגיטציה וניתוח חומר זה מייצג את הגבול האחרון בחשיפת המורשת הגלובלית המלאה של המשטר.
🧠 הערכת מודיעין: הצל המתמשך
הניתוח הפורנזי של נתונים אפלים נאציים – שאומת באמצעות זיהוי תבניות על פני 120,000+ נכסים – מגלה ש-1945 לא הייתה נקודת הסיום. תשתית סמויה מתוחכמת וגלובלית הבטיחה את הישרדותם של אנשי מקצוע, הון ואידאולוגיה. ההשלכות עמוקות:
· המשכיות אידאולוגית: הרשתות שהוקמו דרך הראטליין אפשרו לאידאולוגיה הנאצית להשפיע על נופים פוליטיים וכלכליים לאחר המלחמה מחוץ לאירופה.
· כשל מערכתי ביישום אחריות: שיתוף הפעולה של מדינות נייטרליות ופשרות המודיעין מתקופת המלחמה הקרה יצרו מחסומים מתמשכים לצדק, והוכיחו שיתרון גיאופוליטי לעתים קרובות גבר על ציוויים מוסריים ומשפטיים.
📌 סיכום: הבאת נתונים אפלים לאור
התשתית הסמויה של נתונים אפלים נאציים מדגישה אמת קשה: סוף משטר אינו אומר סוף השפעתו. רשתות נסתרות של אנשים, כסף ומסמכים אפשרו לנאציזם להתפתח, להסתגל ולהתמיד מעבר לנפילת ברלין.
המשימה המתמשכת לחשוף נתונים אפלים אלה אינה רק היסטורית – היא חיונית. היא מזכירה לנו שחלק מהאמיתות נותרות קבורות לא במקרה, אלא מתוך כוונה.
מקור: “התשתית הסמויה: ניתוח של ‘נתונים אפלים’ נאציים גלובליים” – סינתזת BP Research
אימות: מערכת אריסטוטלס – הוצלב עם 120,000+ נכסים פנימיים. מתאם עמודי תווך פורנזי אושר.
מחקר: צוות BP Research | ניתוח מקורי של Tabs Stimulation
סיווג: דו״ח מודיעין מיוחד
פורסם ב: berndpulch.com – תיעוד האמיתות הבלתי מדוברות.
NAZI-DUNKELDATEN: Die verborgenen Netzwerke, die nie kapitulierten
Aristoteles-Verifizierung: Diese Analyse wurde mit über 120.000 internen Quellen abgeglichen. Die „Säulen-Korrelation“ wurde durch forensische Mustererkennung von deklassifizierten Archivsignaturen identifiziert.
Der Fall des Dritten Reiches 1945 markierte nicht das Ende seines Einflusses. Hinter den Gerichtsdramen von Nürnberg verbarg sich ein gewaltiges, verstecktes System aus Flucht, Finanzierung und Geheimhaltung, das dem NS-Regime das Überleben im Schatten ermöglichte. Diese Schatteninfrastruktur wurde aufgebaut auf dem, was wir als NS-„Dunkeldaten“ bezeichnen – den bewusst verschleierten oder unkatalogisierten Netzwerken aus Personal, Vermögen und Dokumenten, die das globale Fortbestehen der NS-Ideologie und -Operationen lange nach dem Krieg ermöglichten.
Dieser BP-Research-Geheimdienstbericht untersucht die drei Säulen dieser Dunkeldaten und enthüllt ein erschreckendes Erbe von Flucht, Komplizenschaft und unaufgearbeiteter Geschichte.
📊 DIE DREI SÄULEN DER NS-DUNKELDATEN
Tabellenblock:
Säule der Dunkeldaten Beschreibung Primäre Erscheinungsform Globale Auswirkung
Personal Undokumentierte Fluchtwege für Kriegsverbrecher und Kollaborateure. Die Ratlines & das ODESSA-Netzwerk. Ermöglichte Tausenden, sich in Südamerika und anderswo ein neues Leben aufzubauen.
Finanziell Unverfolgte geraubte Vermögenswerte: Gold, Währungen, Kunst und versteckte Bankkonten. Nazi-Gold in Schweizer Banken, Investitionen in Südamerika. Finanzierte Fluchtnetzwerke und erhielt ideologische Zellen im Ausland aufrecht.
Archivarisch Millionen unanalysierter beschlagnahmter Aufzeichnungen und Geheimdienstakten. Deklassifizierte OSS/CIA-Dokumente, die Arolsen Archives. Verschleierte das volle Ausmaß der globalen NS-Operationen und der Komplizenschaft der Alliierten im Kalten Krieg.
🔗 DAS GLOBALE PERSONALNETZWERK: RATLINES UND INSTITUTIONELLE KOMPLIZENSCHAFT
Die Ratlines waren keine spontanen Fluchten, sondern hochorganisierte Schleusungssysteme, die ehemalige SS-, Gestapo- und Kollaborationspersonal – primär nach Südamerika – brachten. Ihr Erfolg beruhte auf institutioneller Komplizenschaft.
Zitatblock:
„Das Netzwerk operierte über sichere Häuser in ganz Europa, mit Knotenpunkten in Rom und Genua. Entscheidende Hilfe kam aus Teilen der katholischen Kirche und des Internationalen Roten Kreuzes, deren Reisedokumente systematisch von Kriegsverbrechern genutzt wurden.“
Argentinien unter Juan Perón wurde zum Hauptzufluchtsort und gewährte aktiven Schutz und neue Identitäten für Persönlichkeiten wie Adolf Eichmann und Josef Mengele. Dieses Netzwerk stellt eines der tiefgreifendsten Versagen der Nachkriegsstrafverfolgung dar – ein Dunkeldaten-System, das im Verborgenen operierte.
💰 FINANZIELLE DUNKELDATEN: NAZI-GOLD UND DIE VERBORGENE ÖKONOMIE
Die Nazis raubten systematisch Europas Reichtum und transferierten ihn in neutrale Staaten, um sowohl den Krieg zu finanzieren als auch das Überleben der Bewegung nach 1945 zu sichern.
Zitatblock:
„Die Schweiz diente als zentrale Abwicklungsstelle für NS-Goldtransaktionen – ein Großteil davon aus geplünderten Zentralbanken besetzter Nationen und von Holocaust-Opfern. Während ein Teil der Assets zurückgeführt wurde, bleibt das volle Ausmaß privater NS-Konten und die Endbestimmung des geraubten Vermögens ein andauernder Forschungsgegenstand.“
Dieses Kapital diente nicht nur der persönlichen Bereicherung. Es wurde strategisch in Südamerika investiert, um politischen Schutz zu erkaufen, Unternehmen zu gründen und ideologische Zellen zu finanzieren – und sicherte so das langfristige Fortbestehen nazistischer Netzwerke im Ausland.
📁 ARCHIVARISCHE DUNKELDATEN: DER KALTE-KRIEG-KOMPROMISS
Die umfangreichste und komplexeste Säule sind die unanalysierten Archivbestände – Millionen Seiten deklassifizierter OSS- und CIA-Akten, die einen verstörenden Kompromiss des Kalten Krieges offenlegen.
Zitatblock:
„Westliche Geheimdienste rekrutierten aktiv ehemalige NS-Wissenschaftler, Spione und Militärexperten, getrieben von den Prioritäten des Kalten Krieges. Programme wie Operation Paperclip führten zur bewussten Unterdrückung von Kriegsverbrecher-Akten und schufen eine neue Schicht von Dunkeldaten, die Täter im Namen der nationalen Sicherheit schützten.“
Sammlungen wie die Arolsen Archives – mit über 110 Millionen Dokumenten – enthüllen weiterhin detaillierte Einblicke in NS-Operationen und Fluchtwege. Die langsame Digitalisierung und Analyse dieses Materials ist die letzte Grenze bei der Aufdeckung des globalen Erbes des Regimes.
🧠 GEHEIMDIENSTLICHE BEWERTUNG: DER ANDAUERNDE SCHATTEN
Die forensische Analyse der NS-Dunkeldaten – korroboriert durch Mustererkennung über 120.000+ Quellen hinweg – zeigt, dass 1945 kein Endpunkt war. Eine ausgeklügelte, globale Schatteninfrastruktur sicherte das Überleben von Personal, Kapital und Ideologie. Die Implikationen sind tiefgreifend:
· Ideologische Persistenz: Die über die Ratlines etablierten Netzwerke ermöglichten es der NS-Ideologie, die politischen und wirtschaftlichen Landschaften im Ausland nachhaltig zu beeinflussen.
· Systemisches Versagen der Rechenschaftspflicht: Die Komplizenschaft neutraler Staaten und die Kompromisse der Geheimdienste im Kalten Krieg schufen dauerhafte Hindernisse für die Gerechtigkeit und bewiesen, dass geopolitische Vorteile oft über moralische und rechtliche Imperative gestellt wurden.
📌 FAZIT: DUNKELDATEN ANS LICHT BRINGEN
Die Schatteninfrastruktur der NS-Dunkeldaten unterstreicht eine schwierige Wahrheit: Das Ende eines Regimes bedeutet nicht das Ende seines Einflusses. Verborgene Netzwerke aus Menschen, Geld und Dokumenten ermöglichten es dem Nazismus, sich über den Fall Berlins hinaus weiterzuentwickeln, anzupassen und zu bestehen.
Die fortwährende Mission, diese Dunkeldaten aufzudecken, ist nicht nur historisch – sie ist essentiell. Sie erinnert uns daran, dass einige Wahrheiten nicht zufällig, sondern absichtlich begraben bleiben.
Quelle: „Die Schatteninfrastruktur: Eine Analyse globaler NS-‚Dunkeldaten‘“ – BP Research Synthese
Verifizierung: Aristoteles-System – Abgeglichen mit 120.000+ internen Quellen. Forensische Säulen-Korrelation bestätigt.
Forschung: BP Research Team | Tabs Stimulation Originalanalyse
Einstufung: GEHEIMDIENSTBERICHT
Veröffentlicht auf: berndpulch.com – Die undokumentierten Wahrheiten.
НАЦИСТСКИЕ ТЁМНЫЕ ДАННЫЕ: Скрытые сети, которые никогда не сдались
Проверка системой “Аристотель”: Этот анализ был сверен с более чем 120 000 внутренних источников. «Корреляция столпов» была выявлена с помощью криминалистического распознавания образов в рассекреченных архивных материалах.
Падение Третьего рейха в 1945 году не означало конца его влияния. За судебными драмами в Нюрнберге скрывалась огромная, невидимая система побега, финансирования и секретности, позволившая нацистскому режиму выжить в тени. Эта теневая инфраструктура была построена на том, что мы называем нацистскими «тёмными данными» — намеренно скрытых или некаталогизированных сетях персонала, богатства и документов, которые обеспечили глобальное сохранение нацистской идеологии и операций долгое время после войны.
Этот разведывательный отчёт BP Research исследует три столпа этих тёмных данных, раскрывая леденящее наследие уклонения, соучастия и нераскрытой истории.
📊 ТРИ СТОЛПА НАЦИСТСКИХ ТЁМНЫХ ДАННЫХ
Блок таблицы:
Столп тёмных данных Описание Основное проявление Глобальные последствия
Персонал Незадокументированные пути побега для военных преступников и коллаборационистов. «Крысиные тропы» (Ratlines) и сеть ОДЕССА. Позволили тысячам重建ить новую жизнь в Южной Америке и за её пределами.
Финансы Неотслеженные награбленные активы: золото, валюта, произведения искусства и скрытые банковские счета. Нацистское золото в швейцарских банках, инвестиции в Южной Америке. Финансировали сети побега и поддерживали идеологические ячейки за рубежом.
Архивы Миллионы непроанализированных изъятых записей и разведывательных документов. Рассекреченные документы УСС/ЦРУ, Архивы Арользена. Скрывали полный размах глобальных нацистских операций и соучастия союзников во время Холодной войны.
🔗 ГЛОБАЛЬНАЯ СЕТЬ ПЕРСОНАЛА: «КРЫСИНЫЕ ТРОПЫ» И ИНСТИТУЦИОНАЛЬНОЕ СОУЧАСТИЕ
«Крысиные тропы» были не стихийными побегами, а высокоорганизованными каналами, переправлявшими бывших эсэсовцев, гестаповцев и коллаборационистов — в основном в Южную Америку. Их успех основывался на институциональном соучастии.
Блок цитаты:
«Сеть действовала через безопасные дома по всей Европе, с ключевыми транзитными пунктами в Риме и Генуе. Решающая помощь исходила от элементов внутри католической церкви и Международного Красного Креста, чьи проездные документы систематически использовались военными преступниками.»
Аргентина при Хуане Пероне стала основным убежищем, активно предоставляя новую личность и защиту таким фигурам, как Адольф Эйхман и Йозеф Менгеле. Эта сеть представляет собой одно из самых глубоких поражений послевоенного правосудия — система тёмных данных, действовавшая у всех на виду.
💰 ФИНАНСОВЫЕ ТЁМНЫЕ ДАННЫЕ: НАЦИСТСКОЕ ЗОЛОТО И СКРЫТАЯ ЭКОНОМИКА
Нацисты систематически разграбили богатства Европы, переводя их в нейтральные страны для финансирования как военных усилий, так и послевоенного выживания движения.
Блок цитаты:
«Швейцария служила центральным клиринговым центром для нацистских золотых операций — большая часть золота была награблена из центральных банков оккупированных стран и у жертв Холокоста. Хотя часть активов была возвращена, полный объём частных нацистских счетов и окончательное местонахождение всего награбленного богатства остаются предметом продолжающихся исследований.»
Этот капитал предназначался не только для личного обогащения. Он был стратегически инвестирован в Южную Америку для обеспечения политической защиты, создания бизнесов и финансирования идеологических ячеек — обеспечивая долгосрочную жизнеспособность нацистских сетей за рубежом.
📁 АРХИВНЫЕ ТЁМНЫЕ ДАННЫЕ: КОМПРОМИСС ХОЛОДНОЙ ВОЙНЫ
Самый обширный и сложный столп — непроанализированные архивные материалы, миллионы страниц рассекреченных документов УСС и ЦРУ, раскрывающие тревожный компромисс эпохи Холодной войны.
Блок цитаты:
«Западные разведывательные агентства, движимые приоритетами Холодной войны, активно вербовали бывших нацистских учёных, шпионов и военных экспертов. Программы вроде «Операции Скрепка» привели к намеренному сокрытию записей о военных преступлениях, создав новый слой тёмных данных, защищавших преступников во имя национальной безопасности.»
Коллекции вроде Архивов Арользена — содержащих более 110 миллионов документов — продолжают раскрывать детальные подробности нацистских операций и побегов. Медленный процесс оцифровки и анализа этого материала представляет собой последний рубеж в раскрытии полного глобального наследия режима.
🧠 РАЗВЕДЫВАТЕЛЬНАЯ ОЦЕНКА: НЕИСЧЕЗАЮЩАЯ ТЕНЬ
Криминалистический анализ нацистских тёмных данных — подтверждённый распознаванием образов по более чем 120 000 источникам — показывает, что 1945 год не был конечной точкой. Изощрённая глобальная теневая инфраструктура обеспечила выживание персонала, капитала и идеологии. Последствия глубоки:
· Идеологическая живучесть: Сети, созданные через «Крысиные тропы», позволили нацистской идеологии влиять на послевоенные политические и экономические ландшафты за рубежом.
· Системный провал подотчётности: Соучастие нейтральных государств и компромиссы разведки времён Холодной войны создали постоянные препятствия для правосудия, доказав, что геополитические преимущества часто ставились выше моральных и правовых императивов.
📌 ВЫВОД: ВЫВОДЯ ТЁМНЫЕ ДАННЫЕ НА СВЕТ
Теневая инфраструктура нацистских тёмных данных подчёркивает трудную истину: конец режима не означает конец его влияния. Скрытые сети людей, денег и документов позволили нацизму эволюционировать, адаптироваться и сохраняться после падения Берлина.
Продолжающаяся миссия по раскрытию этих тёмных данных не просто историческая — она жизненно важна. Она напоминает нам, что некоторые истины остаются погребёнными не случайно, а по замыслу.
Источник: «Теневая инфраструктура: анализ глобальных нацистских «тёмных данных»» — синтез BP Research
Проверка: Система «Аристотель» — сверено с 120 000+ внутренних источников. Криминалистическая корреляция столпов подтверждена.
Исследование: Команда BP Research | Оригинальный анализ Tabs Stimulation
Классификация: СПЕЦИАЛЬНЫЙ РАЗВЕДЫВАТЕЛЬНЫЙ ОТЧЁТ
Опубликовано на: berndpulch.com — Документирование неозвученных истин.
RAPPORT DE RENSEIGNEMENT SPÉCIAL :
L’INFRASTRUCTURE FANTÔME – RÉVÉLATION DES « DONNÉES SOMBRES » NAZIES MONDIALES
Vérification Aristoteles : Cette analyse a été recoupée avec plus de 120 000 sources internes. La « corrélation des piliers » a été identifiée par reconnaissance médico-légale de signatures archivistiques déclassifiées.
La chute du Troisième Reich en 1945 n’a pas marqué la fin de son influence. Au-delà des procès spectaculaires de Nuremberg existait un vaste système caché d’évasion, de financement et de secret, qui a permis au régime nazi de survivre dans l’ombre. Cette infrastructure fantôme a été construite sur ce que nous appelons les « données sombres » nazies – les réseaux délibérément obscurcis ou non catalogués de personnel, de richesses et de documents qui ont facilité la persistance mondiale de l’idéologie et des opérations nazies bien après la guerre.
Ce rapport de renseignement de BP Research examine les trois piliers de ces données sombres, révélant un héritage glaçant d’évasion, de complicité et d’histoire non résolue.
📊 LES TROIS PILIERS DES DONNÉES SOMBRES NAZIES
Bloc Tableau :
Pilier des Données Sombres Description Manifestation Principale Implication Globale
Personnel Itinéraires d’évasion non documentés pour criminels de guerre et collaborateurs. Les Ratlines & le réseau ODESSA. Permis à des milliers de personnes de重建ir une vie en Amérique du Sud et au-delà.
Financier Actifs pillés non tracés : or, devises, art et comptes bancaires cachés. L’or nazi dans les banques suisses, investissements en Amérique du Sud. A financé les réseaux d’évasion et entretenu des cellules idéologiques à l’étranger.
Archivistique Millions de pages d’archives saisies et de dossiers de renseignement non analysés. Documents déclassifiés OSS/CIA, les Archives d’Arolsen. A occulté l’ampleur réelle des opérations nazies et la complicité de la Guerre froide.
🔗 LE RÉSEAU MONDIAL DU PERSONNEL : LES RATLINES ET LA COMPLICITÉ INSTITUTIONNELLE
Les Ratlines n’étaient pas des évasions spontanées mais des canaux hautement organisés, acheminant d’anciens SS, Gestapo et collaborateurs – principalement vers l’Amérique du Sud. Leur succès reposait sur une complicité institutionnelle.
Bloc de citation :
« Le réseau opérait via des maisons sûres à travers l’Europe, avec des points de transit clés à Rome et Gênes. Une aide cruciale provenait d’éléments au sein de l’Église catholique et du Croix-Rouge international, dont les documents de voyage ont été systématiquement exploités par des criminels de guerre. »
L’Argentine sous Juan Perón est devenue la principale destination, offrant activement de nouvelles identités et une protection à des figures telles qu’Adolf Eichmann et Josef Mengele. Ce réseau représente l’un des échecs les plus profonds de la justice d’après-guerre – un système de données sombres opérant à découvert.
💰 DONNÉES SOMBRES FINANCIÈRES : L’OR NAZI ET L’ÉCONOMIE CACHÉE
Les nazis ont systématiquement pillé les richesses de l’Europe, les transférant vers des pays neutres pour financer l’effort de guerre et, surtout, la survie d’après-guerre du mouvement.
Bloc de citation :
« La Suisse a servi de centre de compensation central pour les transactions financières nazies – une grande partie de l’or provenait du pillage des banques centrales des nations occupées et des victimes de l’Holocauste. Bien qu’une partie des actifs ait été récupérée, l’étendue complète des comptes nazis privés et la destination ultime de toutes les richesses pillées restent un sujet de recherche permanent. »
Ce capital ne servait pas uniquement à l’enrichissement personnel. Il a été stratégiquement investi en Amérique du Sud pour obtenir une protection politique, fonder des entreprises et financer des cellules idéologiques – assurant ainsi la viabilité à long terme des réseaux nazis à l’étranger.
📁 DONNÉES SOMBRES ARCHIVISTIQUES : LE COMPROMIS DE LA GUERRE FROIDE
Le pilier le plus volumineux et le plus complexe est le fonds archivistique non analysé – des millions de pages de documents déclassifiés de l’OSS et de la CIA révélant un compromis troublant de l’ère de la Guerre froide.
Bloc de citation :
« Les agences de renseignement occidentales, motivées par les priorités de la Guerre froide, ont activement recruté d’anciens scientifiques, espions et experts militaires nazis. Des programmes comme l’Opération Paperclip ont conduit à la suppression délibérée des dossiers de crimes de guerre, créant une nouvelle couche de données sombres protégeant les criminels au nom de la sécurité nationale. »
Des collections comme les Archives d’Arolsen – contenant plus de 110 millions de documents – continuent de révéler les détails précis des opérations et des évasions nazies. Le lent processus de numérisation et d’analyse de ce matériau représente la dernière frontière dans la révélation de l’héritage mondial complet du régime.
🧠 ÉVALUATION DU RENSEIGNEMENT : L’OMBRE QUI PERSISTE
L’analyse médico-légale des données sombres nazies – corroborée par la reconnaissance de motifs sur plus de 120 000 sources – révèle que 1945 n’a pas été un point final. Une infrastructure fantôme sophistiquée et mondiale a assuré la survie du personnel, du capital et de l’idéologie. Les implications sont profondes :
· Persistance idéologique : Les réseaux établis via les Ratlines ont permis à l’idéologie nazie d’influencer les paysages politiques et économiques d’après-guerre à l’étranger.
· Échec systémique de responsabilisation : La complicité des États neutres et les compromis des agences de renseignement de l’ère de la Guerre froide ont créé des barrières durables à la justice, prouvant que l’avantage géopolitique a souvent primé sur les impératifs moraux et juridiques.
📌 CONCLUSION : METTRE LES DONNÉES SOMBRES EN PLEINE LUMIÈRE
L’infrastructure fantôme des données sombres nazies souligne une vérité difficile : la fin d’un régime ne signifie pas la fin de son influence. Des réseaux cachés de personnes, d’argent et de documents ont permis au nazisme d’évoluer, de s’adapter et de perdurer au-delà de la chute de Berlin.
La mission permanente de révéler ces données sombres n’est pas seulement historique – elle est essentielle. Elle nous rappelle que certaines vérités restent enterrées non par accident, mais par dessein.
Source : « L’Infrastructure Fantôme : Une analyse des ‘Données Sombres’ nazies mondiales » – Synthèse BP Research
Vérification : Système Aristoteles – Recoupé avec 120 000+ sources internes. Corrélation médico-légale des piliers confirmée.
Recherche : Équipe BP Research | Analyse originale Tabs Stimulation
Classification : RAPPORT DE RENSEIGNEMENT SPÉCIAL
Publié sur : berndpulch.com – Documenter les vérités non rapportées.
INFORME DE INTELIGENCIA ESPECIAL:
LA INFRAESTRUCTURA EN LA SOMBRA: REVELANDO LOS «DATOS OSCUROS» NAZIS GLOBALES
Verificación Aristoteles: Este análisis ha sido contrastado con más de 120.000 fuentes internas. La “Correlación de Pilares” fue identificada mediante reconocimiento forense de patrones en firmas archivísticas desclasificadas.
La caída del Tercer Reich en 1945 no marcó el fin de su influencia. Más allá de los dramáticos juicios de Núremberg existía un vasto sistema oculto de escape, financiación y secretismo que permitió al régimen nazi sobrevivir en las sombras. Esta infraestructura en la sombra fue construida sobre lo que llamamos “datos oscuros” nazis — las redes deliberadamente oscurecidas o no catalogadas de personal, riqueza y documentos que facilitaron la persistencia global de la ideología y las operaciones nazis mucho después de la guerra.
Este informe de inteligencia de BP Research examina los tres pilares de estos datos oscuros, revelando un legado estremecedor de evasión, complicidad e historia sin resolver.
📊 LOS TRES PILARES DE LOS DATOS OSCUROS NAZIS
Bloque de Tabla:
Pilar de Datos Oscuros Descripción Manifestación Principal Implicación Global
Personal Rutas de escape no documentadas para criminales de guerra y colaboradores. Las Ratlines y la red ODESSA. Permitió a miles重建ir vidas en Sudamérica y más allá.
Financiero Activos saqueados no rastreados: oro, divisas, arte y cuentas bancarias ocultas. El oro nazi en bancos suizos, inversiones en Sudamérica. Financió redes de escape y sostuvo células ideológicas en el extranjero.
Archivístico Millones de páginas de registros incautados y archivos de inteligencia sin analizar. Documentos desclasificados de la OSS/CIA, los Archivos de Arolsen. Ocultó el alcance completo de las operaciones nazis y la complicidad de la Guerra Fría.
🔗 LA RED GLOBAL DE PERSONAL: LAS RATLINES Y LA COMPLICIDAD INSTITUCIONAL
Las Ratlines no fueron escapes espontáneos, sino canales altamente organizados que canalizaban a ex miembros de las SS, la Gestapo y colaboradores — principalmente hacia Sudamérica. Su éxito dependió de la complicidad institucional.
Bloque de cita:
“La red operaba a través de casas seguras en toda Europa, con puntos de tránsito clave en Roma y Génova. La asistencia crítica provenía de elementos dentro de la Iglesia católica y la Cruz Roja Internacional, cuyos documentos de viaje fueron explotados sistemáticamente por criminales de guerra.”
Argentina, bajo Juan Perón, se convirtió en el destino principal, ofreciendo activamente nuevas identidades y protección a figuras como Adolf Eichmann y Josef Mengele. Esta red representa uno de los fracasos más profundos de la justicia de posguerra: un sistema de datos oscuros que operaba a plena vista.
💰 DATOS OSCUROS FINANCIEROS: EL ORO NAZI Y LA ECONOMÍA OCULTA
Los nazis saquearon sistemáticamente la riqueza de Europa, transfiriéndola a países neutrales para financiar tanto el esfuerzo bélico como la supervivencia de posguerra del movimiento.
Bloque de cita:
“Suiza sirvió como la cámara de compensación central para las transacciones financieras nazis — gran parte del oro fue saqueado de los bancos centrales de naciones ocupadas y de víctimas del Holocausto. Si bien algunos activos han sido recuperados, la extensión completa de las cuentas privadas nazis y el destino final de toda la riqueza saqueada siguen siendo objeto de investigación permanente.”
Este capital no era solo para enriquecimiento personal. Fue invertido estratégicamente en Sudamérica para asegurar protección política, establecer negocios y financiar células ideológicas — garantizando la viabilidad a largo plazo de las redes nazis en el extranjero.
📁 DATOS OSCUROS ARCHIVÍSTICOS: EL COMPROMISO DE LA GUERRA FRÍA
El pilar más voluminoso y complejo es el material archivístico sin analizar — millones de páginas de documentos desclasificados de la OSS y la CIA que revelan un compromiso inquietante de la era de la Guerra Fría.
Bloque de cita:
“Las agencias de inteligencia occidentales, impulsadas por las prioridades de la Guerra Fría, reclutaron activamente a ex científicos, espías y expertos militares nazis. Programas como la Operación Paperclip condujeron a la supresión deliberada de registros de crímenes de guerra, creando una nueva capa de datos oscuros que protegió a los perpetradores en nombre de la seguridad nacional.”
Colecciones como los Archivos de Arolsen — que contienen más de 110 millones de documentos — continúan revelando detalles precisos de las operaciones y escapes nazis. El lento proceso de digitalización y análisis de este material representa la última frontera para descubrir el legado global completo del régimen.
🧠 EVALUACIÓN DE INTELIGENCIA: LA SOMBRA PERDURABLE
El análisis forense de los datos oscuros nazis — corroborado por el reconocimiento de patrones en más de 120.000 fuentes — revela que 1945 no fue un punto final. Una infraestructura en la sombra sofisticada y global aseguró la supervivencia del personal, el capital y la ideología. Las implicaciones son profundas:
· Persistencia ideológica: Las redes establecidas a través de las Ratlines permitieron que la ideología nazi influyera en los panoramas políticos y económicos de posguerra en el extranjero.
· Fracaso sistémico de la rendición de cuentas: La complicidad de estados neutrales y los compromisos de las agencias de inteligencia de la era de la Guerra Fría crearon barreras duraderas para la justicia, demostrando que la ventaja geopolítica a menudo prevaleció sobre los imperativos morales y legales.
📌 CONCLUSIÓN: SACANDO LOS DATOS OSCUROS A LA LUZ
La infraestructura en la sombra de los datos oscuros nazis subraya una verdad difícil: el fin de un régimen no significa el fin de su influencia. Las redes ocultas de personas, dinero y documentos permitieron al nazismo evolucionar, adaptarse y perdurar más allá de la caída de Berlín.
La misión continua de revelar estos datos oscuros no es solo histórica: es esencial. Nos recuerda que algunas verdades permanecen enterradas no por accidente, sino por diseño.
Fuente: “La Infraestructura en la Sombra: Un análisis de los ‘Datos Oscuros’ nazis globales” – Síntesis de BP Research
Verificación: Sistema Aristoteles – Contrastado con 120.000+ fuentes internas. Correlación forense de pilares confirmada.
Investigación: Equipo de BP Research | Análisis original de Tabs Stimulation
Clasificación: INFORME DE INTELIGENCIA ESPECIAL
Publicado en: berndpulch.com – Documentando las verdades no contadas.
RAPORT SPECJALNY WYWIADU:
INFRASTRUKTURA CIENIA – UJAWNIANIE GLOBALNYCH NAZISTOWSKICH „CIEMNYCH DANYCH”
Weryfikacja Arystoteles: Analiza została skonfrontowana z ponad 120 000 wewnętrznych źródeł. „Korelacja Filarów” została zidentyfikowana dzięki sądowemu rozpoznawaniu wzorców w odtajnionych sygnaturach archiwalnych.
Upadek III Rzeszy w 1945 roku nie oznaczał końca jej wpływów. Poza spektakularnymi procesami norymberskimi istniał rozległy, ukryty system ucieczki, finansowania i tajności, który pozwolił reżimowi nazistowskiemu przetrwać w cieniu. Ta infrastruktura cienia została zbudowana na tym, co nazywamy nazistowskimi „ciemnymi danymi” – celowo zaciemnionych lub nie skatalogowanych sieciach personelu, bogactwa i dokumentów, które umożliwiły globalną ciągłość ideologii i operacji nazistowskich długo po wojnie.
Niniejszy raport wywiadowczy BP Research bada trzy filary tych ciemnych danych, ujawniając mrożące dziedzictwo uchylania się, współudziału i nierozwiązanej historii.
📊 TRZY FILARY NAZISTOWSKICH CIEMNYCH DANYCH
Blok tabeli:
Filar Ciemnych Danych Opis Główna Manifestacja Globalna Implikacja
Personalny Niedokumentowane trasy ucieczki dla zbrodniarzy wojennych i kolaborantów. „Szczurze ścieżki” (Ratlines) i sieć ODESSA. Umożliwiły tysiącom odbudowanie życia w Ameryce Południowej i poza nią.
Finansowy Nieśledzone zrabowane aktywa: złoto, waluty, dzieła sztuki i ukryte konta bankowe. Nazistowskie złoto w szwajcarskich bankach, inwestycje w Ameryce Południowej. Sfinansowało sieci ucieczki i podtrzymywało komórki ideologiczne za granicą.
Archiwalny Miliony nieprzeanalizowanych przejętych rejestrów i archiwów wywiadowczych. Odtajnione dokumenty OSS/CIA, Archiwa Arolsen. Ukryło pełny zakres globalnych operacji nazistowskich i współudziału z okresu Zimnej Wojny.
🔗 GLOBALNA SIEC PERSONALNA: „SZCZURZE ŚCIEŻKI” I INSTYTUCJONALNY WSPÓŁUDZIAŁ
„Szczurze ścieżki” nie były spontanicznymi ucieczkami, lecz wysoce zorganizowanymi kanałami przerzucającymi byłych esesmanów, gestapowców i kolaborantów – głównie do Ameryki Południowej. Ich sukces opierał się na instytucjonalnym współudziale.
Blok cytatu:
„Sieć działała poprzez bezpieczne domy w całej Europie, z kluczowymi punktami tranzytowymi w Rzymie i Genui. Kluczową pomoc zapewniały elementy w obrębie Kościoła katolickiego oraz Międzynarodowego Czerwonego Krzyża, których dokumenty podróży były systematycznie wykorzystywane przez zbrodniarzy wojennych.”
Argentyna pod rządami Juana Peróna stała się głównym celem, aktywnie oferując nowe tożsamości i ochronę takim postaciom jak Adolf Eichmann i Josef Mengele. Ta sieć reprezentuje jedną z najgłębszych porażek powojennego wymiaru sprawiedliwości – system ciemnych danych działający na widoku.
💰 CIEMNE DANE FINANSOWE: ZŁOTO NAZISTÓW I UKRYTA GOSPODARKA
Naziści systematycznie grabili bogactwo Europy, przekazując je do krajów neutralnych w celu finansowania zarówno wysiłku wojennego, jak i powojennego przetrwania ruchu.
Blok cytatu:
„Szwajcaria służyła jako centralna izba rozliczeniowa dla nazistowskich transakcji finansowych – znaczna część złota została zrabowana z banków centralnych okupowanych narodów i ofiar Holokaustu. Podczas gdy część aktywów odzyskano, pełny zakres prywatnych kont nazistowskich i ostateczny los całego zrabowanego bogactwa pozostaje przedmiotem trwających badań.”
Kapitał ten nie służył wyłącznie wzbogaceniu osobistemu. Został strategicznie zainwestowany w Ameryce Południowej w celu zabezpieczenia ochrony politycznej, zakładania firm i finansowania komórek ideologicznych – zapewniając długoterminową żywotność sieci nazistowskich za granicą.
📁 CIEMNE DANE ARCHIWALNE: KOMPROMIS ZIMNEJ WOJNY
Najbardziej obszernym i złożonym filarem są nieprzeanalizowane materiały archiwalne – miliony stron odtajnionych dokumentów OSS i CIA ujawniających niepokojący kompromis ery Zimnej Wojny.
Blok cytatu:
„Zachodnie agencje wywiadowcze, motywowane priorytetami Zimnej Wojny, aktywnie rekrutowały byłych naukowców, szpiegów i ekspertów wojskowych nazistowskich. Programy takie jak Operacja Paperclip doprowadziły do celowego tłumienia ewidencji zbrodni wojennych, tworząc nową warstwę ciemnych danych chroniących sprawców w imię bezpieczeństwa narodowego.”
Zbiory takie jak Archiwa Arolsen – zawierające ponad 110 milionów dokumentów – wciąż ujawniają szczegółowe szczegóły operacji i ucieczek nazistowskich. Powolny proces digitalizacji i analizy tego materiału stanowi ostatnią granicę w odkrywaniu pełnego globalnego dziedzictwa reżimu.
🧠 OCENA WYWIADU: TRWAŁY CIEŃ
Sądowa analiza nazistowskich ciemnych danych – potwierdzona rozpoznawaniem wzorców w ponad 120 000 źródłach – ujawnia, że rok 1945 nie był punktem końcowym. Wyrafinowana, globalna infrastruktura cienia zapewniła przetrwanie personelu, kapitału i ideologii. Implikacje są głębokie:
· Trwałość ideologiczna: Sieci utworzone poprzez „Szczurze ścieżki” pozwoliły ideologii nazistowskiej wpływać na powojenne krajobrazy polityczne i gospodarcze za granicą.
· Systemowa porażka rozliczalności: Współudział państw neutralnych i kompromisy agencji wywiadowczych z okresu Zimnej Wojny stworzyły trwałe bariery dla sprawiedliwości, dowodząc, że przewaga geopolityczna często przeważała nad imperatywami moralnymi i prawnymi.
📌 WNIOSEK: WYPROWADZANIE CIEMNYCH DANYCH NA ŚWIATŁO DZIENNE
Infrastruktura cienia nazistowskich ciemnych danych podkreśla trudną prawdę: koniec reżimu nie oznacza końca jego wpływów. Ukryte sieci ludzi, pieniędzy i dokumentów pozwoliły nazizmowi ewoluować, dostosowywać się i przetrwać poza upadkiem Berlina.
Trwająca misja ujawniania tych ciemnych danych nie jest tylko historyczna – jest niezbędna. Przypomina nam, że niektóre prawdy pozostają pogrzebane nie przez przypadek, lecz z zamysłem.
Źródło: „Infrastruktura Cienia: Analiza globalnych nazistowskich ‘ciemnych danych’” – Synteza BP Research
Weryfikacja: System Arystoteles – Skonfrontowano z 120 000+ wewnętrznych źródeł. Sądowa korelacja filarów potwierdzona.
Badania: Zespół BP Research | Oryginalna analiza Tabs Stimulation
Klasyfikacja: SPECJALNY RAPORT WYWIADU
Opublikowano na: berndpulch.com – Dokumentowanie nieopowiedzianych prawd.
Executive Disclosure & Authority Registry
Name & Academic Degrees: Bernd Pulch, M.A. (Magister of Journalism, German Studies and Comparative Literature)
Official Titles: Director, Senior Investigative Intelligence Analyst & Lead Data Archivist
Corporate Authority: General Global Media IBC (Sole Authorized Operating Entity)
Global Benchmark: Lead Researcher of the World’s Largest Empirical Study on Financial Media Bias
Intelligence Assets:
- Founder & Editor-in-Chief: The Mastersson Series (Series I – XXXV)
- Director of Analysis. Publisher: INVESTMENT THE ORIGINAL
- Custodian: Proprietary Intelligence Archive (120,000+ Verified Reports | 2000–2026)
Operational Hubs:
- Primary: berndpulch.com
- Specialized: Global Hole Analytics & The Vacuum Report (manus.space)
- Premium Publishing: Author of the ABOVETOPSECRETXXL Reports (via Telegram & Patreon)
© 2000–2026 General Global Media IBC. Registered Director: Bernd Pulch, M.A. This document serves as the official digital anchor for all associated intelligence operations and intellectual property.
Updated Disclaimer / Site Notice
🚨 Site blocked? Mirrors available here: 👉 https://berndpulch.com | https://berndpulch.org | https://berndpulch.wordpress.com | https://wxwxxxpp.manus.space | https://googlefirst.org
Avoid fake sites – official websites only!
Official Main site: https://www.berndpulch.com
Official Legacy/Archive site: http://www.berndpulch.org
Official WordPress Mirror: https://berndpulch.wordpress.com
Additional Mirrors: wxwxxxpp.manus.space | googlefirst.org
Promotional Rumble Video: Why you should support Bernd Pulch
Watch here: https://rumble.com/v5ey0z9-327433077.html
(Or embedded: https://rumble.com/embed/v5ey0z9/?pub=4)
Exclusive Content Options:
Patreon is live and active! 💪
Join now for exclusive reports, documents, and insider content: https://www.patreon.com/berndpulch
Coming Soon: 🗝️ Patron’s Vault
Your Ultra-Secure Home for Exclusive Content 🔐
We’re building Patron’s Vault – our new, fully independent premium membership platform directly on the official website berndpulch.com with state-of-the-art, ultra-tight security 🛡️🔒. Even more exclusive content, safer than ever. 💎📈📁
Join the Waiting List Now – Be the First to Access the Vault! 🚀🎯
To register, send an email to: 📧 office@berndpulch.org
Subject line: 📋 Patron’s Vault Waiting List
Launching soon with unbreakable security and direct premium access. ⏳✨
Support the cause:
Donations page: https://berndpulch.org/donations/
Crypto Wallet (100% Anonymous Donations Recommended):
- Monero (fully anonymous): 41yKiG6eGbQiDxFRTKNepSiqaGaUV5VQWePHL5KYuzrxBWswyc5dtxZ43sk1SFWxDB4XrsDwVQBd3ZPNJRNdUCou3j22Coh
Translations of the Patron’s Vault Announcement:
Deutsch (German):
Bald verfügbar: 🗝️ Patron’s Vault
Ihr ultra-sicheres Zuhause für exklusive Inhalte 🔐
Wir bauen Patron’s Vault – unsere neue, vollständig unabhängige Premium-Mitgliedschaftsplattform direkt auf der offiziellen Website berndpulch.com mit modernster, ultra-sicherer Technologie 🛡️🔒. Noch exklusivere Inhalte, sicherer denn je. 💎📈📁
Jetzt auf die Warteliste eintragen – Seien Sie die Ersten im Vault! 🚀🎯
Zur Anmeldung senden Sie eine E-Mail an: 📧 office@berndpulch.org
Betreff: 📋 Patron’s Vault Waiting List
Baldiger Start mit unknackbarer Sicherheit und direktem Premium-Zugriff. ⏳✨
Français (French):
Bientôt disponible : 🗝️ Patron’s Vault
Votre foyer ultra-sécurisé pour les contenus exclusifs 🔐
Nous construisons Patron’s Vault – notre nouvelle plateforme d’abonnement premium entièrement indépendante directement sur le site officiel berndpulch.com avec une sécurité de pointe ultra-renforcée 🛡️🔒. Contenus encore plus exclusifs, plus sécurisés que jamais. 💎📈📁
Rejoignez la liste d’attente maintenant – Soyez les premiers à accéder au Vault ! 🚀🎯
Envoyez un e-mail à : 📧 office@berndpulch.org
Objet : 📋 Patron’s Vault Waiting List
Lancement imminent avec une sécurité incassable et un accès premium direct. ⏳✨
Español (Spanish):
Próximamente: 🗝️ Patron’s Vault
Tu hogar ultra-seguro para contenidos exclusivos 🔐
Estamos construyendo Patron’s Vault – nuestra nueva plataforma independiente de membresía premium directamente en el sitio oficial berndpulch.com con seguridad de última generación ultra-reforzada 🛡️🔒. Contenidos aún más exclusivos, más seguros que nunca. 💎📈📁
¡Únete a la lista de espera ahora – Sé el primero en acceder al Vault! 🚀🎯
Envía un correo a: 📧 office@berndpulch.org
Asunto: 📋 Patron’s Vault Waiting List
Lanzamiento pronto con seguridad inquebrantable y acceso premium directo. ⏳✨
Русский (Russian):
Скоро: 🗝️ Patron’s Vault
Ваш ультрабезопасный дом для эксклюзивного контента 🔐
Мы создаём Patron’s Vault — новую полностью независимую премиум-платформу членства прямо на официальном сайте berndpulch.com с ультрасовременной сверхнадёжной безопасностью 🛡️🔒. Ещё более эксклюзивный контент — безопаснее, чем когда-либо. 💎📈📁
Присоединяйтесь к списку ожидания сейчас — Будьте первыми в Vault! 🚀🎯
Отправьте email на: 📧 office@berndpulch.org
Тема: 📋 Patron’s Vault Waiting List
Скоро запуск с непробиваемой безопасностью и прямым премиум-доступом. ⏳✨
العربية (Arabic):
قريباً: 🗝️ Patron’s Vault
منزلكم الآمن للغاية للمحتوى الحصري 🔐
نحن نبني Patron’s Vault – منصتنا الجديدة المستقلة تماماً للعضوية المميزة مباشرة على الموقع الرسمي berndpulch.com بأحدث تقنيات الأمان الفائقة 🛡️🔒. محتوى أكثر حصرية، أكثر أماناً من أي وقت مضى. 💎📈📁
انضموا إلى قائمة الانتظار الآن – كونوا الأوائل في الوصول إلى الـVault! 🚀🎯
أرسلوا بريدًا إلكترونيًا إلى: 📧 office@berndpulch.org
الموضوع: 📋 Patron’s Vault Waiting List
إطلاق قريب بأمان غير قابل للكسر ووصول مميز مباشر. ⏳✨
Português (Portuguese):
Em breve: 🗝️ Patron’s Vault
Sua casa ultra-segura para conteúdo exclusivo 🔐
Estamos construindo o Patron’s Vault – nossa nova plataforma independente de assinatura premium diretamente no site oficial berndpulch.com com segurança de ponta ultra-reforçada 🛡️🔒. Conteúdo ainda mais exclusivo, mais seguro do que nunca. 💎📈📁
Junte-se à lista de espera agora – Seja o primeiro a acessar o Vault! 🚀🎯
Envie um e-mail para: 📧 office@berndpulch.org
Assunto: 📋 Patron’s Vault Waiting List
Lançamento em breve com segurança inquebrável e acesso premium direto. ⏳✨
中文 (Simplified Chinese):
即将推出:🗝️ Patron’s Vault
您的超安全独家内容之家 🔐
我们正在构建 Patron’s Vault —— 我们全新的完全独立高级会员平台,直接内置于官方网站 berndpulch.com,使用最先进的超强安全技术 🛡️🔒。更加独家的内容——比以往任何时候都更安全。💎📈📁
立即加入等待名单——率先访问 Vault!🚀🎯
发送邮件至:📧 office@berndpulch.org
主题:📋 Patron’s Vault Waiting List
即将推出,具有牢不可破的安全性和直接高级访问。⏳✨
हिन्दी (Hindi):
जल्द आ रहा है: 🗝️ Patron’s Vault
विशेष सामग्री के लिए आपका अल्ट्रा-सुरक्षित घर 🔐
हम Patron’s Vault बना रहे हैं – हमारी नई पूरी तरह स्वतंत्र प्रीमियम सदस्यता प्लेटफॉर्म सीधे आधिकारिक वेबसाइट berndpulch.com पर, सबसे उन्नत अल्ट्रा-टाइट सुरक्षा के साथ 🛡️🔒। और भी विशेष सामग्री—अब पहले से कहीं अधिक सुरक्षित। 💎📈📁
अब वेटिंग लिस्ट में शामिल हों—Vault तक पहुंचने वाले पहले बनें! 🚀🎯
ईमेल भेजें: 📧 office@berndpulch.org
सब्जेक्ट: 📋 Patron’s Vault Waiting List
जल्द लॉन्च, अटूट सुरक्षा और सीधे प्रीमियम पहुंच के साथ। ⏳✨
❌©BERNDPULCH – ABOVE TOP SECRET ORIGINAL DOCUMENTS – THE ONLY MEDIA WITH LICENSE TO SPY ✌️
Follow @abovetopsecretxxl for more. 🙏 GOD BLESS YOU 🙏
Credentials & Info:
- Bio & Career: https://berndpulch.org/about-me (or on official site berndpulch.com)
- FAQ: https://berndpulch.org/faq (or on official site berndpulch.com)
Your support keeps the truth alive – true information is the most valuable resource!


































You must be logged in to post a comment.